
by Contributed | May 18, 2024 | Technology
This article is contributed. See the original author and article here.

¡GitHub y Microsoft lanzaron una nueva iniciativa para ayudarte a impulsar tu carrera en tecnología con la serie de charlas en vivo – Certifícate con GitHub – comienza el 6 de junio y finaliza hasta el 27 de junio. Estas sesiones están diseñadas para ayudarte a obtener la certificación de Fundamentos de GitHub y para ayudarte a explorar herramientas esenciales como GitHub Copilot y GitHub Codespaces. Además, tendrás la oportunidad de obtener un voucher gratuito para el examen de la certificación Fundamentos de GitHub*
REGÍSTRATE AQUÍ: aka.ms/CertificateConGitHub
* Al final de la sesión, es posible que incluso recibas un cupón (voucher) gratuito para el examen de la certificación de GitHub Foundations, todo basado en el orden de llegada (first-come, first-served basis).
Oferta válida solo hasta agotar existencias. Límite de un cupón de GitHub por persona. Esta oferta no es transferible y no se puede combinar con ninguna otra oferta. Esta oferta finaliza el 27 de junio de 2024 o hasta agotar existencias, y no se puede canjear por dinero en efectivo. Los impuestos, si los hubiera, son responsabilidad exclusiva del destinatario. Microsoft se reserva el derecho de cancelar, cambiar o suspender esta oferta en cualquier momento sin previo aviso.
Obtener la certificación de GitHub es una excelente manera de mostrar tus habilidades y comprensión de las herramientas y tecnología utilizada por más de 100 millones de desarrolladores en todo el mundo.

Durante estas charlas, estarás interactuando con expertos de Microsoft y GitHub que te guiarán durante todas estas sesiones sobre diferentes temas relacionados con la certificación de GitHub Foundations.
Además, al registrarte y asistir a las sesiones en vivo, podrías recibir un voucher gratuito para la certificación GitHub Foundations – todo basado en orden de llegada (first-come, first-served).
Obtener una certificación de GitHub te brinda una ventaja competitiva en el mercado laboral para permitirte demostrar tus habilidades de GitHub en un área en específico.

Estas sesiones estarán llenas de consejos, trucos y ejercicios prácticos que te ayudarán a construir una base sólida para esta certificación. Ya sea que estés comenzando o estés buscando mejorar tus habilidades, este es un evento único para cualquier persona interesada en hacer crecer su carrera en tecnología.
Todas nuestras sesiones comenzaran en base a la zona horaria de Ciudad de México.
Sesión
|
Descripción
|
Programando más rápido con GitHub Copilot
6 de junio 2024 – 6 pm (GMT-6)
|
¡Aprovecha GitHub Copilot para automatizar tareas repetitivas y aumentar tu productividad! En esta sesión daremos una introducción a esta herramienta, sus funciones más nuevas, prompts interactivos y ¡mucho más!
|
Seguridad con tus proyectos en GitHub
12 de Junio 2024 – 6 pm (GMT-6)
|
Descubre cómo aplicar seguridad de GitHub Advanced Security a tus propios proyectos y protegerlos de amenazas y vulnerabilidades de seguridad.
|
¡Administra tus proyectos con GitHub!
20 de Junio 2024 – 6 pm (GMT-6)
|
Utiliza GitHub para administrar el desarrollo de tus proyectos de software. En esta sesión, hablaremos sobre la gestión de proyectos con issues, pull requests y seguimiento de cambios.
|
Trucos para automatizar tus proyectos con GitHub
27 de junio 2024 – 6 pm (GMT-6)
|
¡Descubre cómo puedes potenciar tus proyectos de programación! Aprende a automatizar cualquier actividad de tus proyectos de software utilizando GitHub. En esta sesión usaremos GitHub Actions, GitHub Copilot y GitHub Codespaces.
|

Al obtener la certificación de Fundamentos de GitHub, puedes demostrar tu comprensión de los temas y conceptos fundamentales de colaborar, contribuir y trabajar en GitHub. Este examen cubre:
- Colaboración
- Productos GitHub
- Conceptos básicos de Git
- Trabajar dentro de los repositorios de GitHub

Estamos muy emocionados de anunciar el GitHub Challenge como parte del Microsoft Learn Challenge ¡Edición Build! Esto es parte de Microsoft Build 2024, nuestro evento para programadores más grande del año. Las inscripciones para el Challenge están abiertas: ¡regístrate YA! (aka.ms/GitHubChallengeBuild)
¡El GitHub Challenge es una aventura de aprendizaje de 30 días en Microsoft Learn! Es completamente gratis, súper divertido y con ejercicios dinámicos. ¡Regístrate y vuélvete experto en GitHub Copilot! Además, crearás aventuras interesantes con Python y JavaScript mientras usas GitHub Codespaces y crearás proyectos del mundo real con GitHub Copilot, ¡justo a tiempo para Microsoft Build! Este desafío comienza el 21 de Mayo y finaliza el 21 de Junio de 2024.
Queremos apoyarte en el desarrollo y mejora de tus habilidades. ¡Prepárate para iniciar este emocionante desafío! ¡Este viaje de aprendizaje ha sido diseñado para aumentar tu comprensión de la IA y convertirte en un experto en GitHub Copilot! Este reto en línea te ayudará a prepararte para el examen de certificación de Fundamentos de GitHub, cubriendo algunos temas que pueden aparecer en el examen.
El GitHub Challenge está disponible todos los días y a cualquier hora en Microsoft Learn. Podrás aprender cuando mejor te convenga y a tu propio ritmo.
Al completar este desafío antes del 21 de junio de 2024, recibirás una insignia (badge) digital especial en tu perfil de Microsoft Learn por finalizar esta experiencia de aprendizaje
Esta insignia solo está disponible durante Microsoft Build, nuestro evento para desarrolladores más grande del año.
¡Aprovecha esta increíble y única oportunidad para seguir aprendiendo y haciendo crecer tu carrera en tecnología! ¡Regístrate al reto aquí!

Conoce nuestra guía gratuita con ejercicios dinámicos para ayudarte a prepararte para esta certificación. Puedes leer toda la información que necesitas aquí: aka.ms/InfoGuideGitHub

El código del voucher (cupón) se ingresará manualmente durante el proceso de pago. A continuación, se detallan los pasos de registro y para agendar tu examen:
- Inicia sesión en el sitio de registro del examen y elige la certificación deseada. Esto te redireccionará a la página de registro.
- Haz clic en “Programar/realizar examen” para continuar.
- Completa el formulario de registro y selecciona “Programar examen” en la parte inferior.
- Esta acción transmitirá tus detalles de elegibilidad a nuestro proveedor de pruebas, PSI.
- Al enviar el formulario de registro, serás dirigido al sitio de pruebas de PSI para finalizar la programación de su examen.
- Durante el proceso de pago en el sitio de pruebas de PSI, encontrarás un campo designado donde puedes ingresar el código del voucher (cupón) para poner a cero el saldo.
by Contributed | May 17, 2024 | Technology
This article is contributed. See the original author and article here.
Helping you build better apps has been one of our key focus areas in Azure. Our latest tooling focuses on providing guidance for architecting, optimizing, and deploying apps. Whether you’re creating a new proof of concept or improving an existing app, these capabilities can boost productivity and performance. These capabilities are all in Preview, so please give them a try and let us know what you think!
Starting Right: Architecting Your Azure App
Let’s say you’re starting a proof of concept for a new application. Normally, you might spend a lot of time picking services, architecting apps, and deploying them based on industry best practices. Better Together can streamline this process with the below capabilities.
Better Together in Microsoft Copilot for Azure
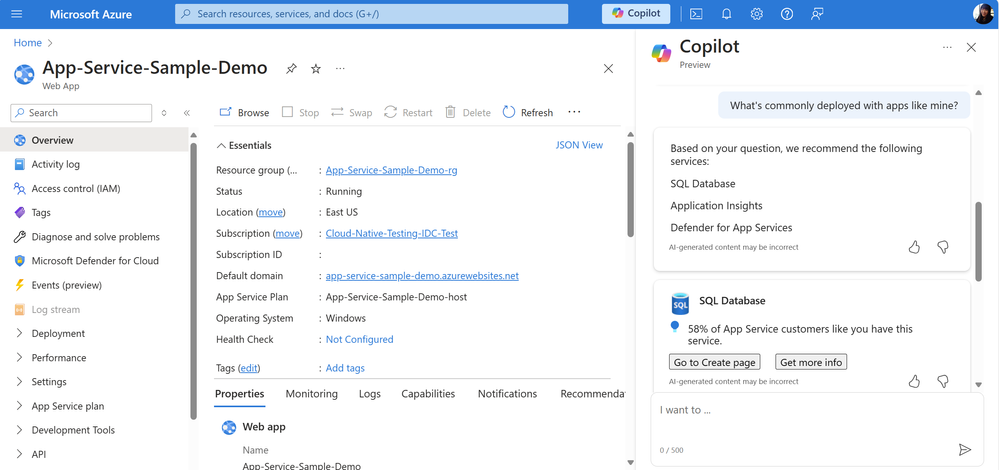
The Better Together capability which can be accessed from Copilot can be helpful to understanding if you’re on the right track when building your app. In the past it might’ve been time-consuming to learn about the kinds of services that similar apps are using through docs and videos. This capability can streamline some of this process by recommending services based on patterns that other similar apps have used.
 Azure Better Together in Copilot
Azure Better Together in Copilot
To give this a try, navigate to the Azure Portal and select the Copilot button in the toolbar to open the chat window. Here you can ask questions to recommended services for your app, or architecture, including, “What are popular services that are deployed with App Service apps like mine?” and “Which database should I use with my ACA app?”, and “What services would you recommend to implement distributed caching?”
 Azure Better Together in Copilot
Azure Better Together in Copilot
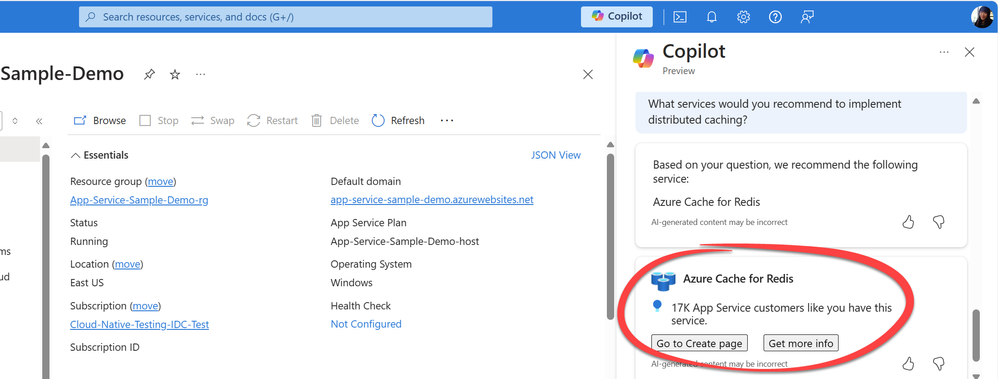
Sometimes it’s important to validate if you’re on the right track. When you ask architectural or infrastructure-level questions to Azure Copilot, it helps you discover the most commonly used services for your specific use case. In the example below, after identifying performance bottlenecks in your app and considering implementing distributed caching to enhance performance, the recommendation points to Azure Cache for Redis. This service is widely deployed by many App Service apps similar to yours.
Boosting Performance: Optimizing Your Azure App
If your App Service app is running a little slower than expected, or if you’re suspecting any performance bottlenecks, these are some capabilities that can diagnose and optimize these problems.
Diagnostics Insights (Preview)
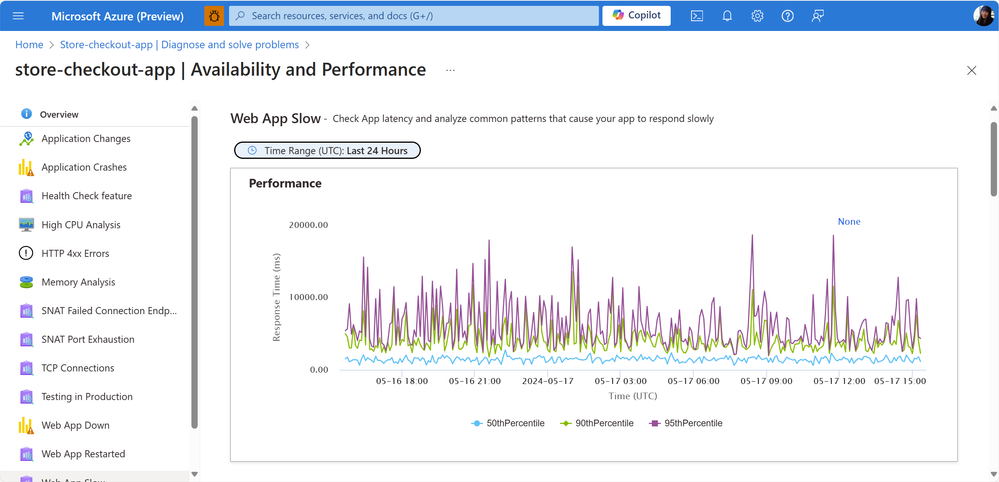
Diagnostic logs can return pages of information that are difficult to interpret. This capability can make it easier to identify anomalies and quickly identify bottlenecks . In the Azure Portal, you can efficiently evaluate your application’s CPU usage and track any anomalies by navigating to Diagnose & Solve Problems > Web App Slow. Within this section, you’ll find a chart that provides insights into performance and latency.
 Availability and Performance for Azure Apps
Availability and Performance for Azure Apps
Notably, over the last 24 hours, approximately 90% of users accessing this web app experienced low latency.
Another way to access suggestions is to type in “my web app is slow” into Copilot for Azure, which will offer suggestions around any bottlenecks.
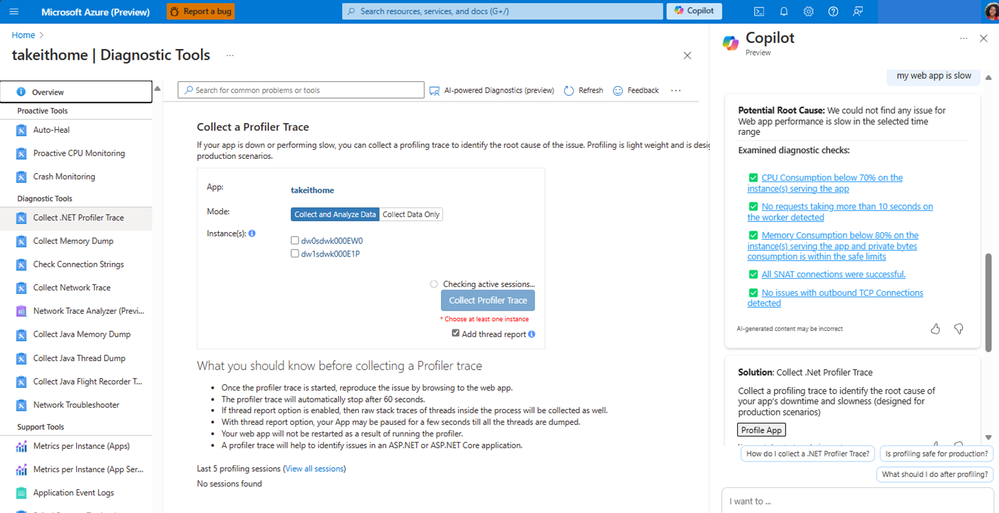 Diagnostic Tooling for Azure Apps
Diagnostic Tooling for Azure Apps
Diagnostic charts can sometimes be time-consuming to analyze. However, Copilot offers a helpful Summarization capability. When you input variations of “summarize this page,” Copilot will generate concise summaries of the insights, allowing you to quickly grasp the main points without having to read through every chart and detail.
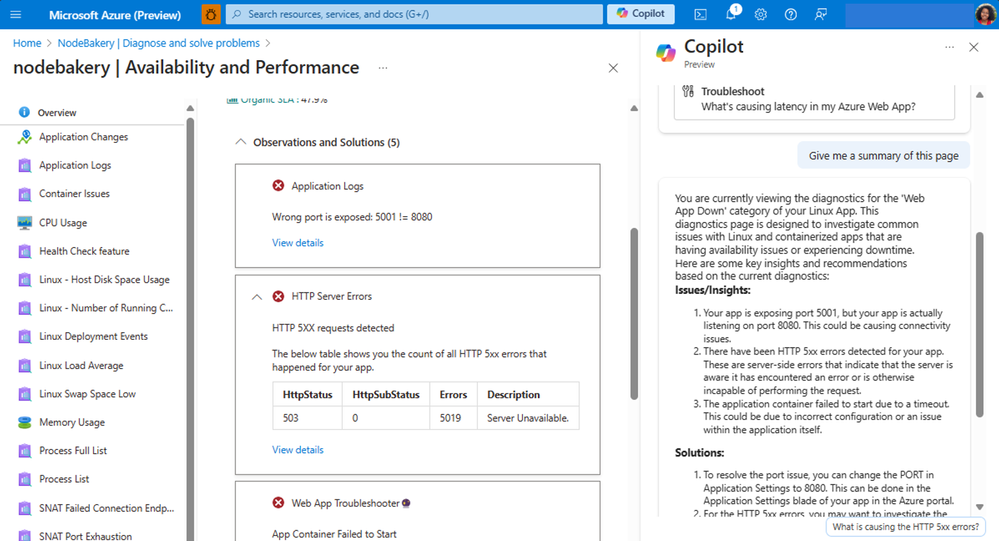 Diagnostic Tooling for Azure Apps
Diagnostic Tooling for Azure Apps
Application Insights Code Optimizations (Preview)
Performance can be improved by making code-level changes. Code Optimizations helps identify where to make these improvements. By leveraging AI, Code Optimizations detects CPU and memory bottlenecks of your application during runtime. It is available for .NET applications that have Application Insights Profiler enabled. To access Code Optimizations in the Azure Portal, navigate to the Performance blade in Application Insights. For App Service, it’s also available in Diagnose & Solve Problems > Web App Slow.
In this example, some of the performance issues identified may be caused by inefficient code, which can be investigated.
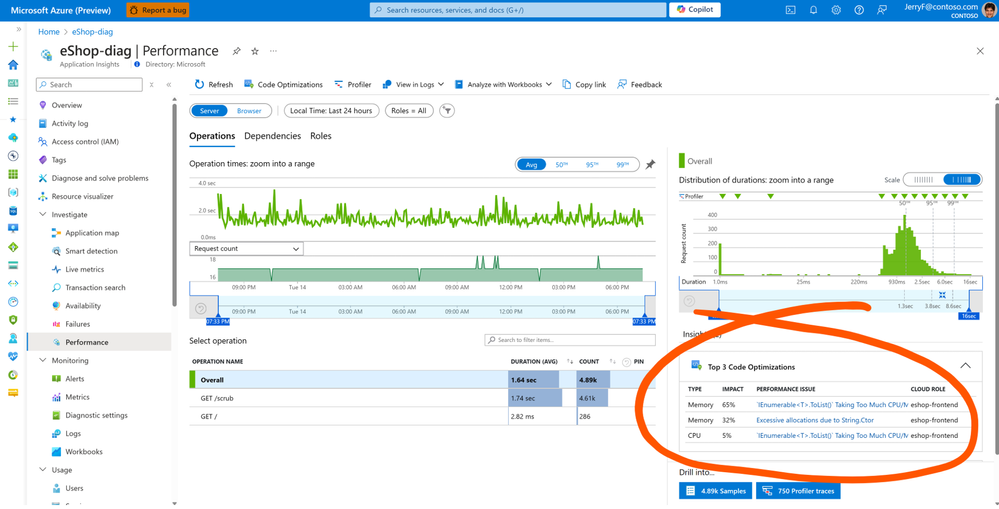 Code Optimizations for Azure Apps
Code Optimizations for Azure Apps
Selecting any of these suggestions will open more details about the performance issue, show where and when in the code it’s occurring, and show the recommended solution.
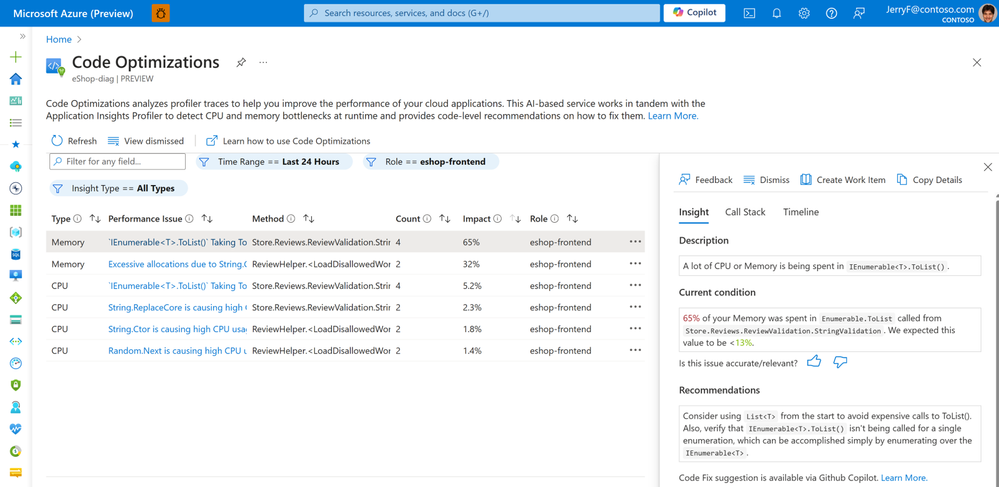 Code Optimizations for Azure Apps
Code Optimizations for Azure Apps
For many recommendations, a code fix can be generated using the Code Optimizations extension (currently in limited preview) for Visual Studio and Visual Studio Code – Insiders. You can sign up here.
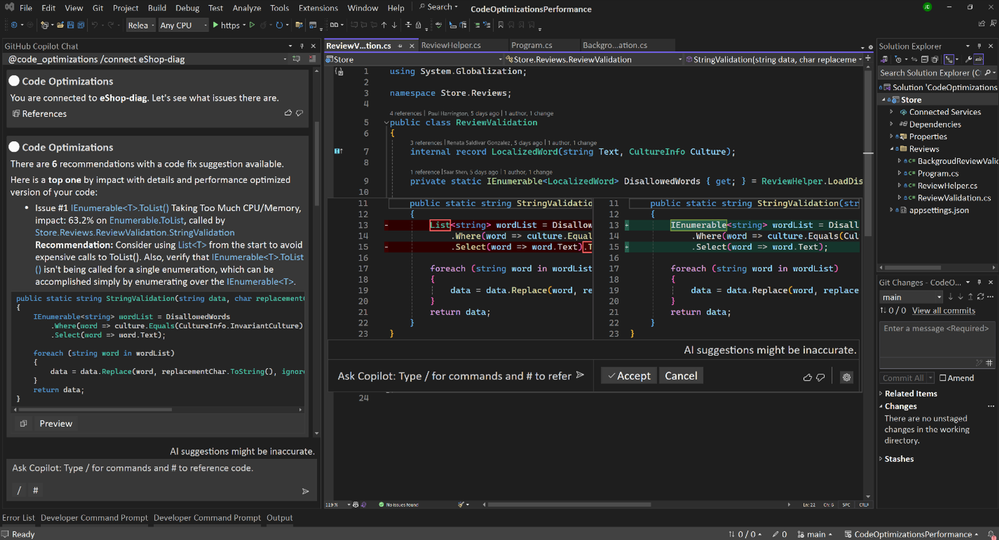 Code Optimizations for Azure Apps in Visual Studio
Code Optimizations for Azure Apps in Visual Studio
Learn more about Code Optimizations.
Making Improvements: Augmenting Your Azure App
If you have deployed an App Service app and you’re unsure which services to use to improve scalability and reliability for it, these capabilities can help optimize without reinventing the wheel.
Better Together (Preview) in Azure Portal
It can be time-consuming to pick, create, deploy, and connect a service to your App Service app. Better Together can help you deploy and connect popular services for your App Service app. This capability primarily focuses on connecting newly-created resources to your App Service app more easily. Navigate to Better Together for your App Service app through the Azure Portal using the menu item Better Together.
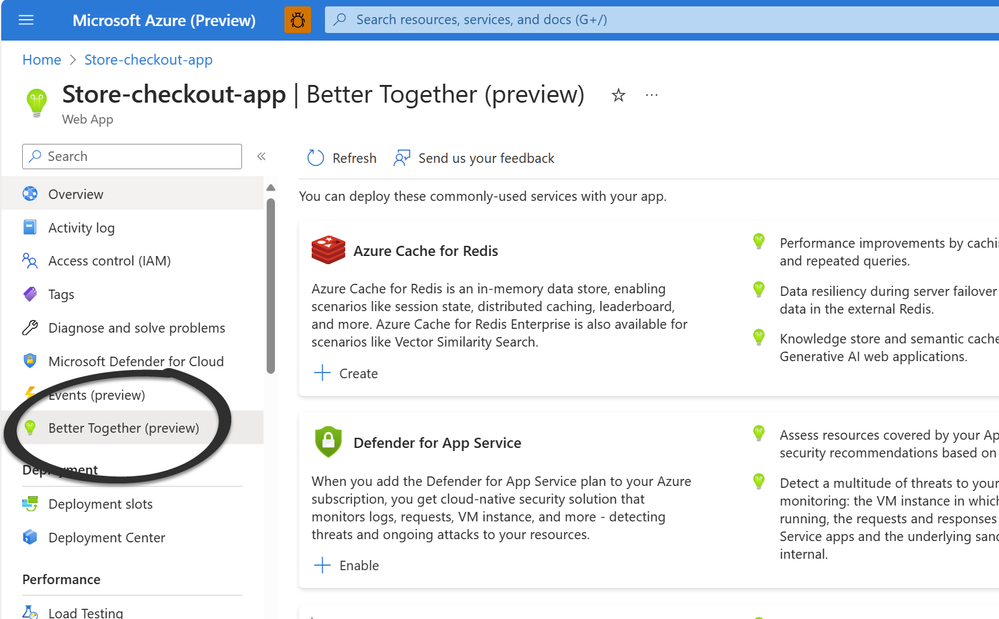 Better Together for App Service Apps
Better Together for App Service Apps
Enabling Azure Cache for Redis will automatically create a new Redis instance and establish the connection with your existing App Service app. If you choose to “Create” any of the other services, you’ll be directed to their onboarding flow, where you’ll receive guidance on creating and connecting the service. Stay tuned for the next release for a more customized experience!
Take a look at these capabilities in action with the video below.
Conclusion: Better Together
Azure strives to empower you to create robust, high-performing apps. Whether you’re starting a new app or improving an existing one, we are creating tools and services that can help. Please give these capabilities a try and let us know what you think by leaving a comment or emailing us at bettertogetherteam@microsoft.com.

by Contributed | May 16, 2024 | Technology
This article is contributed. See the original author and article here.

GitHub and Microsoft are helping you to boost your tech career with the Get Certified with GitHub livestream series! Starts from June 5th until June 26th. These sessions are designed to help you get certified on the GitHub Foundation Certification and to help you explore essential tools like GitHub Copilot and GitHub Codespaces. Plus, you’ll have the chance to earn a free certification voucher for the GitHub Foundation Certification*
REGISTER HERE: aka.ms/GetCertifiedwithGitHub
* At the end of the session, you may even receive a free GitHub certification voucher, on a first-come, first-served basis.
Offer good only while supplies last. Limit one GitHub voucher per person. This offer is non-transferable and cannot be combined with any other offer. This offer ends on June 27, 2024 or while supplies last, and is not redeemable for cash. Taxes, if any, are the sole responsibility of the recipient. Microsoft reserves the right to cancel, change, or suspend this offer at any time without notice.
Earning certification from GitHub is an excellent way to showcase your abilities, reputation, trust, and understanding of the tools and technologies used by over 100 million developers worldwide.

You’ll be interacting with Microsoft and GitHub Experts that will guide you during all these sessions about different topics related to the GitHub Foundation certification.
Also, by registering and attending the live sessions you may be able to receive a free certification voucher on a first-come, first-served basis
Earning a GitHub Certification gives you a competitive edge in the job market by allowing you to promote your skills in a specific GitHub domain.

These sessions will be full of tips, tricks, and practical exercises to help you build a great foundation for this certification. Whether you’re just starting out or looking to improve your skills, this is a must-see event for anyone interested in growing their career in tech.
All our sessions will take place in Pacific Time.
Session
|
Description
|
Building Automation with GitHub
June 5th – 11 am Pacific Time
|
Find out how you can create powerful automation on any software project using GitHub’s platform. This session will cover GitHub Actions, GitHub Copilot, and GitHub Codespaces
|
Securing projects on GitHub
June 12th – 11 am Pacific Time
|
Discover how to apply security features from GitHub Advanced Security to your own projects and protect it from security threats and vulnerabilities.
|
Faster development with GitHub Copilot
June 19th – 11 am Pacific Time
|
Learn how to leverage GitHub Copilot for automating repetitive tasks and increasing your development cycles. We’ll go through basic usage as well as newer features like interactive prompts and inline suggestions
|
Manage your project with the GitHub Platform
June 26th – 11 am Pacific Time
|
Use GitHub’s powerful project features to manage your software development process. We’ll cover project management with issues, pull requests, and tracking changes.
|

With the GitHub Foundations certificate, you can highlight your understanding of the foundational topics and concepts of collaborating, contributing, and working on GitHub. This exam covers:
- Collaboration
- GitHub products
- Git basics
- Working within GitHub repositories

We are super excited to announce the GitHub Challenge as part of the Microsoft Learn Challenge | Build Edition! This is part of Microsoft Build 2024, our largest developer event of the year. Registrations to the challenge are open – register NOW! (aka.ms/GitHubChallengeBuild)
The GitHub Challenge is a 30-day learning adventure on Microsoft Learn! It’s completely free, super fun, with dynamic exercises. Dive in to master GitHub Copilot! Plus, you’ll create interesting adventures with Python and JavaScript while using GitHub Codespaces and create real-world projects with GitHub Copilot —just in time for Microsoft Build! This challenge starts on May 21st and ends on June 21st 2024.
We want to support you in developing and upgrading your abilities! Prepare to take on this exciting challenge and level up. This learning journey has been designed to increase your understanding of AI and make you a GitHub Copilot expert! This challenge will help you prepare for the GitHub Foundations certification exam by covering a few topics that may appear on the test.
The GitHub Challenge is available every day at any time on Microsoft Learn. You can learn whenever it’s convenient for you and at your own speed.
By completing this challenge before June 21st 2024, you will receive a special and distinctive digital badge on your Microsoft Learn profile for finishing this learning experience. You can share your badge on your LinkedIn!
This badge is only available during Microsoft Build, our largest developer event of the year.
Take this amazing and unique opportunity to keep learning and growing your career in tech! Registrations to the challenge HERE!

We have a comprehensive, free, dynamic exercise guide to help you prepare for this certification. You can read all the information you need, here: aka.ms/InfoGuideGitHub

The voucher code will be entered manually during the checkout process. Below are the registration and scheduling steps:
- Log into the exam registration site and choose the desired certification. This will redirect you to the registration page.
- Click on “Schedule/take exam” to proceed.
- Complete the registration form and select “Schedule exam” at the bottom.
- This action will transmit your eligibility details to our testing vendor, PSI.
- Upon submitting the registration form, you’ll be directed to the PSI testing site to finalize the scheduling of your exam.
- During the checkout process on the PSI testing site, you’ll encounter a designated field where you can enter the voucher code to zero the balance.
by Contributed | May 15, 2024 | Technology
This article is contributed. See the original author and article here.
Azure CycleCloud is an enterprise-friendly tool for orchestrating and managing High-Performance Computing (HPC) environments on Azure. With CycleCloud, users can provision infrastructure for HPC systems, deploy familiar HPC schedulers, and automatically scale the infrastructure to run jobs efficiently at any scale.
Slurm is a widely used open-source HPC scheduler that can manage workloads across clusters of compute nodes. Slurm can also be configured to interact with cloud resources, such as Azure CycleCloud, to dynamically add or remove nodes based on the demand of the jobs. This allows users to optimize their resource utilization and cost efficiency, as well as to access the scalability and flexibility of the cloud.
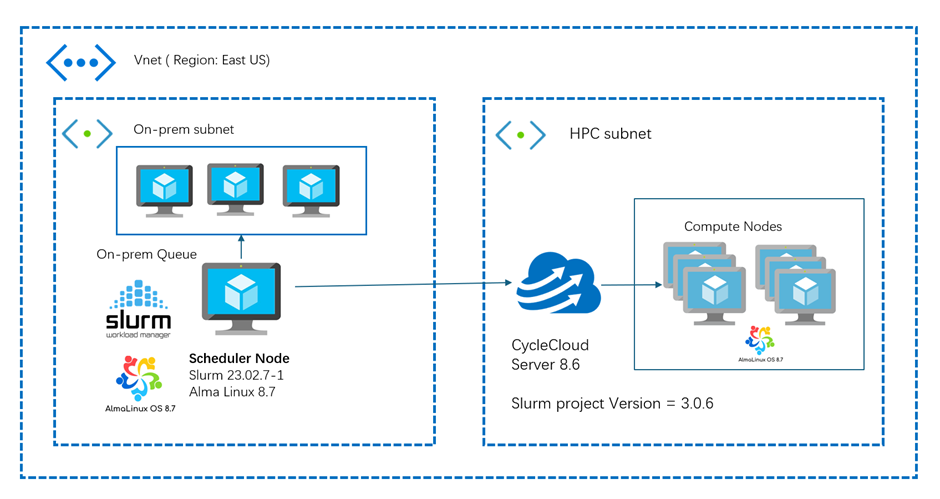
In this blog post, we are discussing how to integrate an external Slurm Scheduler to send jobs to CycleCloud for cloud bursting (Enabling on-premises workloads to be sent to the cloud for processing, known as “cloud bursting”) or hybrid HPC scenarios. For demonstration purposes, we are creating a Slurm Scheduler node in Azure as an external Slurm Scheduler in a different VNET and the execute nodes are in CycleCloud in a separate VNET. We are not discussing the complexities of networking involved in Hybrid scenarios.

Prerequisites
Before we start, we need to have the following items ready:
- An Azure subscription
- CycleCloud Version: 8.6.0-3223
- OS version in Scheduler and execute nodes: Alma Linux release 8.7 (almalinux:almalinux-hpc:8_7-hpc-gen2:latest)
- Slurm Version: 23.02.7-1
- cyclecloud-slurm Project: 3.0.6
- An external Slurm Scheduler node in Azure or on-premises. in this example we are using Azure VM running with Alma Linux 8.7.
- A network connection between the external Slurm Scheduler node and the CycleCloud cluster. You can use Azure Virtual Network peering, VPN gateway, ExpressRoute, or other methods to establish the connection. In this example, we are using a very basic network setup.
- A shared file system between the external Slurm Scheduler node and the CycleCloud cluster. You can use Azure NetApp Files, Azure Files, NFS, or other methods to mount the same file system on both sides. In this example, we are using a Scheduler VM as a NFS server.
Steps
After we have the prerequisites ready, we can follow these steps to integrate the external Slurm Scheduler node with the CycleCloud cluster:
1. On CycleCloud VM:
- Ensure CycleCloud 8.6 VM is running and accessible via
cyclecloud CLI.
- Clone this repository and import a cluster using the provided CycleCloud template (
slurm-headless.txt).
- We are importing a cluster named
hpc1using theslurm-headless.txt template.
git clone https://github.com/vinil-v/slurm-cloud-bursting-using-cyclecloud.git
cyclecloud import_cluster hpc1 -c Slurm-HL -f slurm-cloud-bursting-using-cyclecloud/templates/slurm-headless.txt
Output:
[vinil@cc86 ~]$ cyclecloud import_cluster hpc1 -c Slurm-HL -f slurm-cloud-bursting-using-cyclecloud/cyclecloud-template/slurm-headless.txt
Importing cluster Slurm-HL and creating cluster hpc1....
----------
hpc1 : off
----------
Resource group:
Cluster nodes:
Total nodes: 0
2. Preparing Scheduler VM:
- Deploy a VM using the specified AlmaLinux image (If you have an existing Slurm Scheduler, you can skip this).
- Run the Slurm scheduler installation script (
slurm-scheduler-builder.sh) and provide the cluster name (hpc1) when prompted.
- This script will install and configure Slurm Scheduler.
git clone https://github.com/vinil-v/slurm-cloud-bursting-using-cyclecloud.git
cd slurm-cloud-bursting-using-cyclecloud/scripts
sh slurm-scheduler-builder.sh
Output:
------------------------------------------------------------------------------------------------------------------------------
Building Slurm scheduler for cloud bursting with Azure CycleCloud
------------------------------------------------------------------------------------------------------------------------------
Enter Cluster Name: hpc1
------------------------------------------------------------------------------------------------------------------------------
Summary of entered details:
Cluster Name: hpc1
Scheduler Hostname: masternode2
NFSServer IP Address: 10.222.1.26
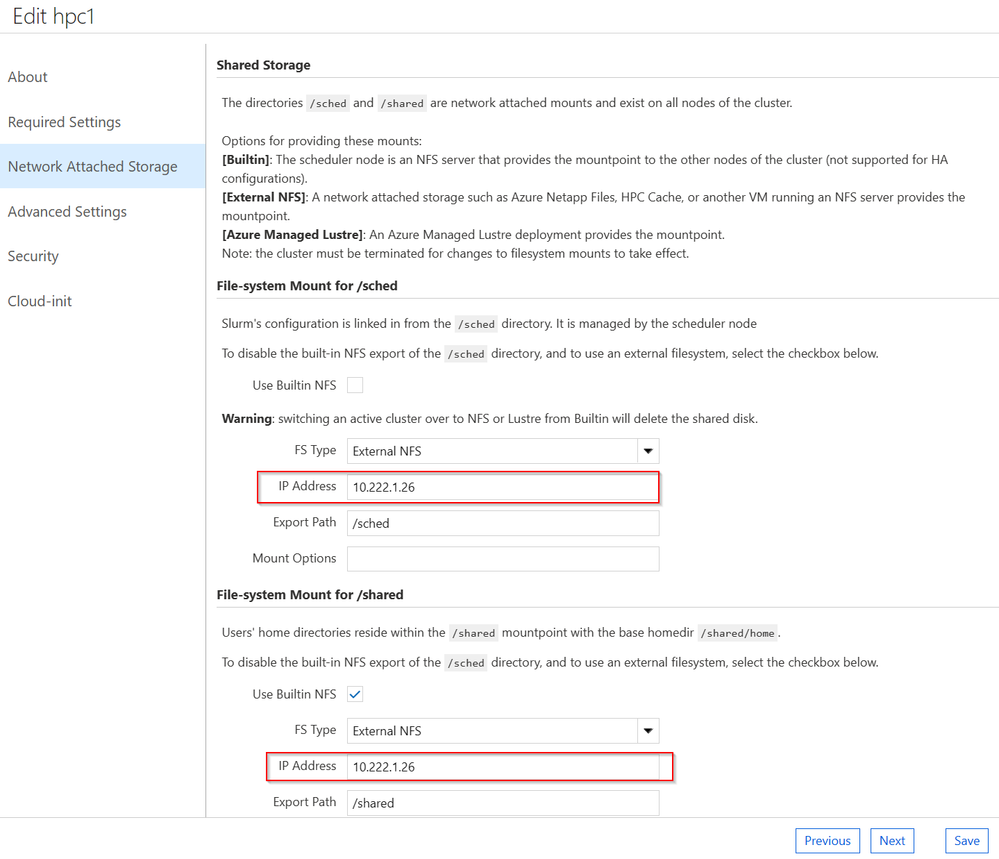
3. CycleCloud UI:
- Access the CycleCloud UI, edit the
hpc1 cluster settings, and configure VM SKUs and networking settings.
- Enter the NFS server IP address for
/sched and /shared mounts in the Network Attached Storage section.
- Save & Start
hpc1 cluster
4. On Slurm Scheduler Node:
- Integrate External Slurm Scheduler with CycleCloud using the
cyclecloud-integrator.sh script.
- Provide CycleCloud details (username, password, and URL) when prompted. (Try entering the details manually instead of copy and paste. The copy & paste might contain some whitespaces and it might create issues in building the connection.)
cd slurm-cloud-bursting-using-cyclecloud/scripts
sh cyclecloud-integrator.sh
Output:
[root@masternode2 scripts]# sh cyclecloud-integrator.sh
Please enter the CycleCloud details to integrate with the Slurm scheduler
Enter Cluster Name: hpc1
Enter CycleCloud Username: vinil
Enter CycleCloud Password:
Enter CycleCloud URL (e.g., https://10.222.1.19): https://10.222.1.19
------------------------------------------------------------------------------------------------------------------------------
Summary of entered details:
Cluster Name: hpc1
CycleCloud Username: vinil
CycleCloud URL: https://10.222.1.19
------------------------------------------------------------------------------------------------------------------------------
5. User and Group Setup:
- Ensure consistent user and group IDs across all nodes.
- Better to use a centralized User Management system like LDAP to ensure the UID and GID are consistent across all the nodes.
- In this example we are using the
users.sh script to create a test user vinil and group for job submission. (User vinil exists in CycleCloud)
cd slurm-cloud-bursting-using-cyclecloud/scripts
sh users.sh
6. Testing & Job Submission:
- Log in as a test user (
vinil in this example) on the Scheduler node.
- Submit a test job to verify the setup.
su - vinil
srun hostname &
Output:
[root@masternode2 scripts]# su - vinil
Last login: Tue May 14 04:54:51 UTC 2024 on pts/0
[vinil@masternode2 ~]$ srun hostname &
[1] 43448
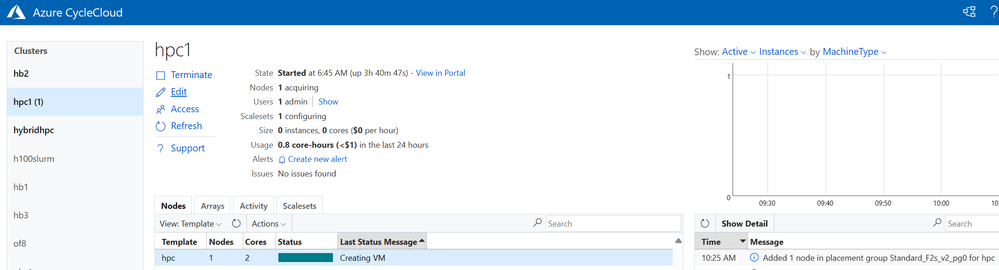
[vinil@masternode2 ~]$ squeue
JOBID PARTITION NAME USER ST TIME NODES NODELIST(REASON)
1 hpc hostname vinil CF 0:04 1 hpc1-hpc-1
[vinil@masternode2 ~]$ hpc1-hpc-1
You will see a new node getting created in hpc1 cluster.
Congratulations! You have successfully set up Slurm bursting with CycleCloud on Azure.
Conclusion
In this blog post, we have shown how to integrate an external Slurm Scheduler node with Azure CycleCloud for cloud bursting or hybrid HPC scenarios. This enables users to leverage the power and flexibility of the cloud for their HPC workloads, while maintaining their existing Slurm workflows and tools. We hope this guide helps you to get started with your HPC journey on Azure.
Reference:
GitHub repo – slurm-cloud-bursting-using-cyclecloud
Azure CycleCloud Documentation
Slurm documentation
by Contributed | May 14, 2024 | Technology
This article is contributed. See the original author and article here.
Microsoft Support is excited to continue the blog series that will demystify how Microsoft 365 email protection works. In this fifth and final part of the series, we will cover the different overrides, why you may need them, and why it isn’t a good idea to keep them permanently.
Email security is a critical aspect of modern business operations, and Microsoft 365 provides a robust set of tools to keep your communications safe. But what should you do when legitimate emails are blocked? This is where submissions and overrides come into play. As we have covered in part 2 of this series, Submissions help you learn more about why email was junked or quarantined and allow you to notify Microsoft if the filters got it wrong. (It happens.) Overrides are special settings that allow certain emails to bypass the usual security filters, ensuring important communications reach their destination.
A closer look at email overrides
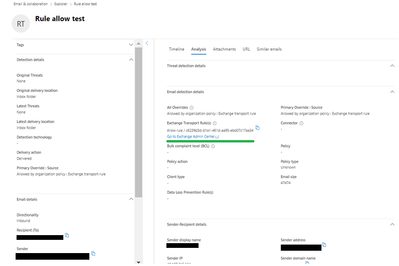
Overrides are not one-size-fits-all; they come in different forms to suit various needs. Use Explorer email summary flyout and email entity pages to learn more about why a message was delivered to a certain location, and if overrides played a role in delivery. Note, since messages can have multiple allow or block overrides as identified in the column Override source, the override that ultimately allowed or blocked the message is identified in Primary override source in Explorer.
Learn more: Understanding overrides within the email entity page in Microsoft Defender for Office 365, Understanding detection technology within the email entity page in Microsoft Defender for Office 365
- Tenant Allow Block List (TABL): Ideal for creating temporary and safe exceptions. Based on your submission, Microsoft will analyze the exact part of the email deemed malicious (sender, domain, URL, file hash, spoof, or impersonation). TABL is the preferred choice for maintaining security: “Allows” eventually expire, and until they do, the system learns from your submissions to allow emails with similar elements. Both easy for you to manage, and useful for service filter adjustments. A win-win!
Note: spoof overrides do not expire. Learn more here: Allow or block email using the Tenant Allow/Block List
- Exchange Mail Flow Rules (Exchange Transport Rules or ETRs): ETRs provide the most flexibility but come with increased risk. They should be used sparingly and thoughtfully. Safer ETR overrides use conditions for email authentication checks passing before allowing anything (see an example). The Analysis tab of the email entity page in Explorer will help you verify which ETR acted on a message, and the anti-spam message headers will include SFV:SKN if an ETR override is detected.

Figure 1: “Allowed by organization policy: Exchange transport rule” override source on the Email Entity page in Microsoft Defender XDR
Certain user allows “win” over tenant configurations and provide the end-users the ability to manage their own exceptions, so make sure to review the “User and tenant settings conflict” section to learn what to expect at Order and precedence of email protection.
Tip: List all overrides for a user or all users in your organization using the PowerShell cmdlet. For full syntax and examples, see Get-MailboxJunkEmailConfiguration.
- IP Allow List (Connection Filtering): This allows emails from specified IP addresses to bypass filters as part of connection filtering. One risk here is if an IP you believe is trusted becomes compromised, the entire email filtering stack except Secure by default is bypassed. Another risk is adding IP overrides for shared IP addresses or ranges. If bad actors use the same sender infrastructure for malicious purposes, you will allow bad messages along with good ones. In short: exercise caution, review regularly, keep IP allows to a minimum. The anti-spam message headers will include IPV:CAL if an IP override is detected, and the Explorer email entity page will look like this:
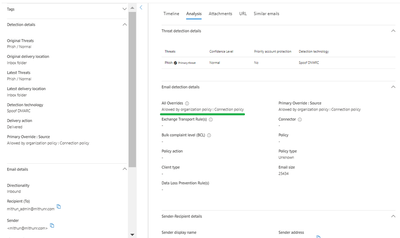
Figure 3: “Allowed by organization policy: Connection policy” override source on the Email Entity page in Microsoft Defender XDR
- Anti-Phishing Policy Overrides: Aimed at combating domain, user and mailbox impersonation phishing threats, these overrides will target false positives with UIMP, DIMP, GIMP verdicts only. They are relatively safer as the rest of the protection scans take place, but it’s still a good idea to make sure from time to time any trusted senders and domains are still necessary, as they never expire.
Tip: You can also use Tenant Allow/Block List for impersonation overrides, just note that the allow entry isn’t created in the Tenant Allow/Block List. Instead, the domain or sender is added to the Trusted senders and domains section in the anti-phishing policy that detected the message and it does not expire.
Example
The company CEO, John Smith (johnsmith@contoso.com) is a prime target for impersonation attacks, so your SecOps team adds his address to trusted users to protect in the anti-phishing policy. However, the CEO sometimes sends email to his team from his personal account (johnsmith@outlook.com). After the service flags this correctly as user impersonation, you add the CEO’s personal address to trusted senders, for his emails to get through to recipient inboxes. (Of course, after you educate the CEO about the risks tied to this practice, you remove this entry.)
Figure 4: Add trusted senders part of the anti-phishing policy in Microsoft Defender XDR
- Anti-Spam Policy Overrides: used to override spam, bulk, spoofing and low-confidence phishing verdicts (SPM, HSPM, PHISH, SPOOF and BULK), anti-spam policy senders and/or domains allows also override the anti-phishing stack, and they do not expire. Overly broad (domain) allows are particularly risky and known to be a leading cause for letting bad email into your inboxes. Best practice, review your policies periodically and trim/clear these lists. The Analysis tab of the email entity page in Explorer will help you verify if a policy that acted on a message, and the anti-spam message headers will include SFV:SKA if a policy override is detected.
Tip: You can also export an extended report (message trace) for the email in question. The AGENTINFO event in the resulting csv file contains the CustomData field with additional details, such as the GUID of the policy that acted on the message. For example:
S:PCFA=SUM|tact=5|di=SQ|tactcat=SPM|hctfp=191b78dc-9221-4a2c-b51c-208a186e931a;
SQ means the message was routed to Spam Quarantine, and hctfp stands for Hosted Content Filter Policy. Find the policy name by running the cmdlet Get-HostedContentFilteringPolicy in Exchange Online PowerShell.
- While most of this article is about allow overrides, you can use Anti-Spam policies to block email, as well. For example, filter messages containing geographies and languages you would not expect to be working with. Learn how to configure spam filter policies.
Secure by Default
Microsoft 365 Secure by Default stance ensures that the system starts with the highest security settings. Notably, verdicts for malware (MALW) and high-confidence phishing (HPHISH) cannot be overridden by ETRs if the MX record points to Office 365. This policy is in place to protect users from the most severe threats automatically.
Why would I ever override Secure by Default?
There are specific instances where an override may be necessary. It is highly recommended to configure the Advanced delivery policy to handle these uses cases securely.
- Phishing Simulations: To test their defenses, organizations might run controlled phishing simulations. To ensure these tests reach inboxes when they’re sent over email, overrides are essential.
- SecOps Mailboxes: Security teams sometimes need to examine malicious emails for analysis and learning. Access to such emails requires an override to allow them through.
Learn more: Configure the advanced delivery policy for third-party phishing simulations and email delivery to SecOps mailboxes
What if the MX record for my domain does not point to Exchange Online Protection?
Secure by default applies only when the MX record for your domain points to Microsoft 365 (contoso-com.mail.protection.outlook.com). If the MX record points to another service or device, it’s possible to override high-confidence phishing verdicts using an Exchange mail flow rule to bypass spam filtering (malware verdicts cannot be overridden). But although it’s technically possible, consider the benefits of defense-in-depth of your filtering solution paired with Microsoft Defender for Office 365. Use Enhanced Filtering for Connectors to skip the last known IP address(es) of your service, and to infer the email authentication information from the original sender IP. In addition, if your filtering solution supports ARC, configure to trust the ARC sealer in Microsoft Defender XDR settings. These configurations will allow you to keep the extra layer of Microsoft protection even when using third party protections.
Learn more about Getting started with defense in-depth configuration for email security, Secure by default in Office 365, Manage mail flow using a third-party cloud service with Exchange Online and Configure trusted ARC sealers.
Messages I send land in spam folders for external recipients. Can I override outbound spam filtering?
No. However, you can take steps to authenticate outbound email to improve deliverability.
Use overrides wisely
While overrides are useful tools, they must be implemented wisely. Incorrect usage can inadvertently open your company to threats. It’s essential to take the following precautions:
- Only allow emails from verified and trustworthy sources. And even when you trust the source, consider that it may become compromised, and you would inadvertently allow unwanted phishing or spam.
- Use Advanced Hunting in Microsoft Defender XDR to help you discover top overrides sources and remove the unnecessary ones.
- Regularly review your overrides to ensure they remain relevant and secure.
- Never put domains that you own onto the Allow and blocklists. If you own Contoso, do not add contoso.com to your allow lists.
- Never put common domains, such as microsoft.com and office.com, onto the Allow and blocklists.
We hope that by understanding and applying email overrides correctly, you can ensure your organization’s email is both secure and functional, allowing the right messages to get through while keeping the bad ones out.
Do you have questions or feedback about Microsoft Defender for Office 365? Engage with the community and Microsoft experts in the Defender for Office 365 forum.
Click here to view additional posts in this series.
Important resources:
Allow or block email using the Tenant Allow/Block List
Order and precedence of email protection
Understanding overrides within the email entity page in Microsoft Defender for Office 365
Understanding detection technology within the email entity page in Microsoft Defender for Office 365
About Threat Explorer and Real-time detections in Microsoft Defender for Office 365
Getting started with defense in-depth configuration for email security
Review and remove unnecessary allow list entries with Advanced Hunting in Microsoft Defender for Office 365
Create safe sender lists
Create blocked sender lists
Configure the advanced delivery policy for third-party phishing simulations and email delivery to SecOps mailboxes
Secure by default in Office 365
Manage mail flow using a third-party cloud service with Exchange Online
Configure trusted ARC sealers
Configure spam filter policies
Configure anti-phishing policies in Microsoft Defender for Office 365
Get-MailboxJunkEmailConfiguration
Authenticate Outbound Email to Improve Deliverability


Recent Comments