by Contributed | Sep 7, 2024 | Technology
This article is contributed. See the original author and article here.
As you may be aware, Azure Automation Agent-based User Hybrid Runbook Worker (Windows and Linux) was retired on 31 August 2024, and support has been discontinued.
For guidance on migrating, please refer to this article: Migrate an existing agent-based hybrid workers to extension-based-workers in Azure Automation | Microsoft Learn
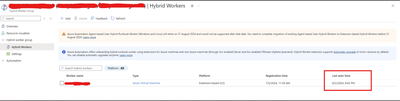
Nonetheless, users might want to verify whether their runbooks and jobs are utilizing the extension or agent-based system when they transition. It’s worth noting that versions V1 and V2 of the same hybrid worker machine can be registered simultaneously with Azure Automation but will have different names.
If the V1 agent wasn’t uninstalled before the V2 extension was installed, this would lead Azure to detect both versions on the same machine.
The “last seen time” suggests V1 and V2 are communicating with Azure Automation if both exist.

It’s also worth noting that some automation tasks are still being performed by the V1 worker, which accounts for its continued activity. Runbook jobs can be executed on any machine within the Hybrid Worker Group. Currently, this group includes both V1 and V2 versions, so the tasks are distributed between them.
The installation of V2 does not mean that the Hybrid Worker Group will disregard V1 and exclusively use V2.
Happy Learning!
by Contributed | Sep 6, 2024 | Technology
This article is contributed. See the original author and article here.
In my previous blog posts of containerising .NET apps and Function apps, I discussed how to containerise .NET apps and Azure Functions apps with and without Dockerfile. However, deploying these containerised apps to Azure Container Apps (ACA) is a different story.
Since its release in May 2023, Azure Developer CLI (azd) has evolved significantly. azd nowadays even automatically generates Bicep files for us to immediately provision and deploy applications to Azure. With this feature, you only need the azd up command for provisioning and deployment.
Throughout this post, I’m going to discuss how to provision and deploy .NET apps including Azure Functions to ACA through just one command, azd up.
You can find a sample code from this GitHub repository.
Prerequisites
There are a few prerequisites to containerise .NET apps effectively.
Running the app locally
The sample app repository already includes the following apps:
Let’s make sure those apps running properly on your local machine. In order to run those apps locally, open three terminal windows and run the following commands on each terminal:
# Terminal 1 – ASP.NET Core Web API
dotnet run –project ./ApiApp
# Terminal 2 – Azure Functions
cd ./FuncApp
dotnet clean && func start
# Terminal 3 – Blazor app
dotnet run –project ./WebApp
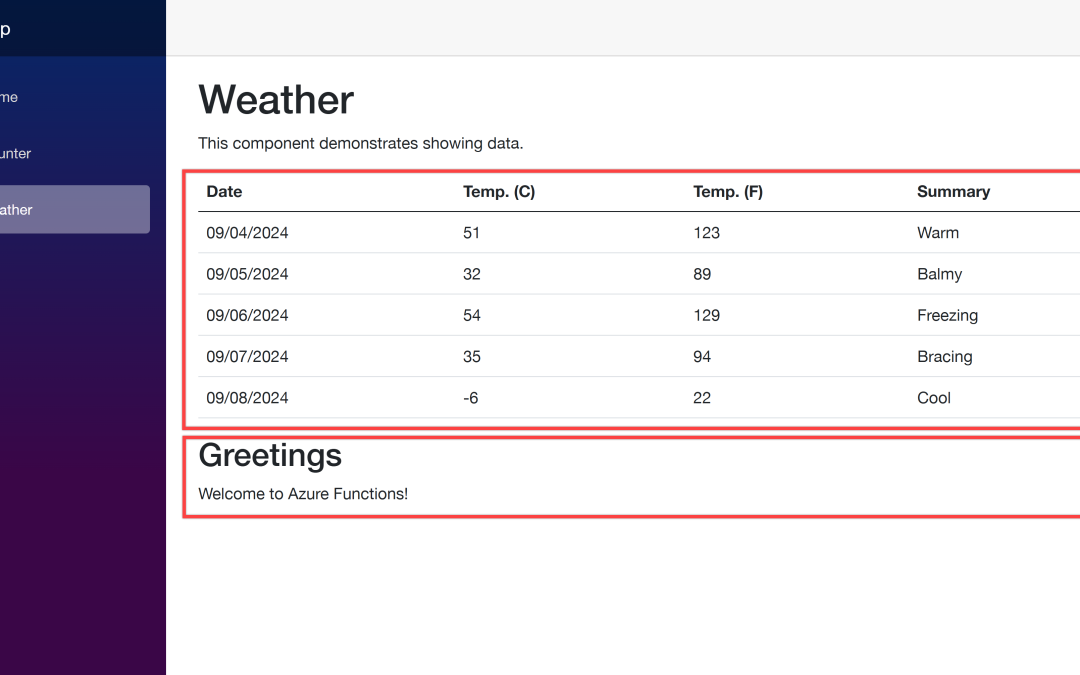
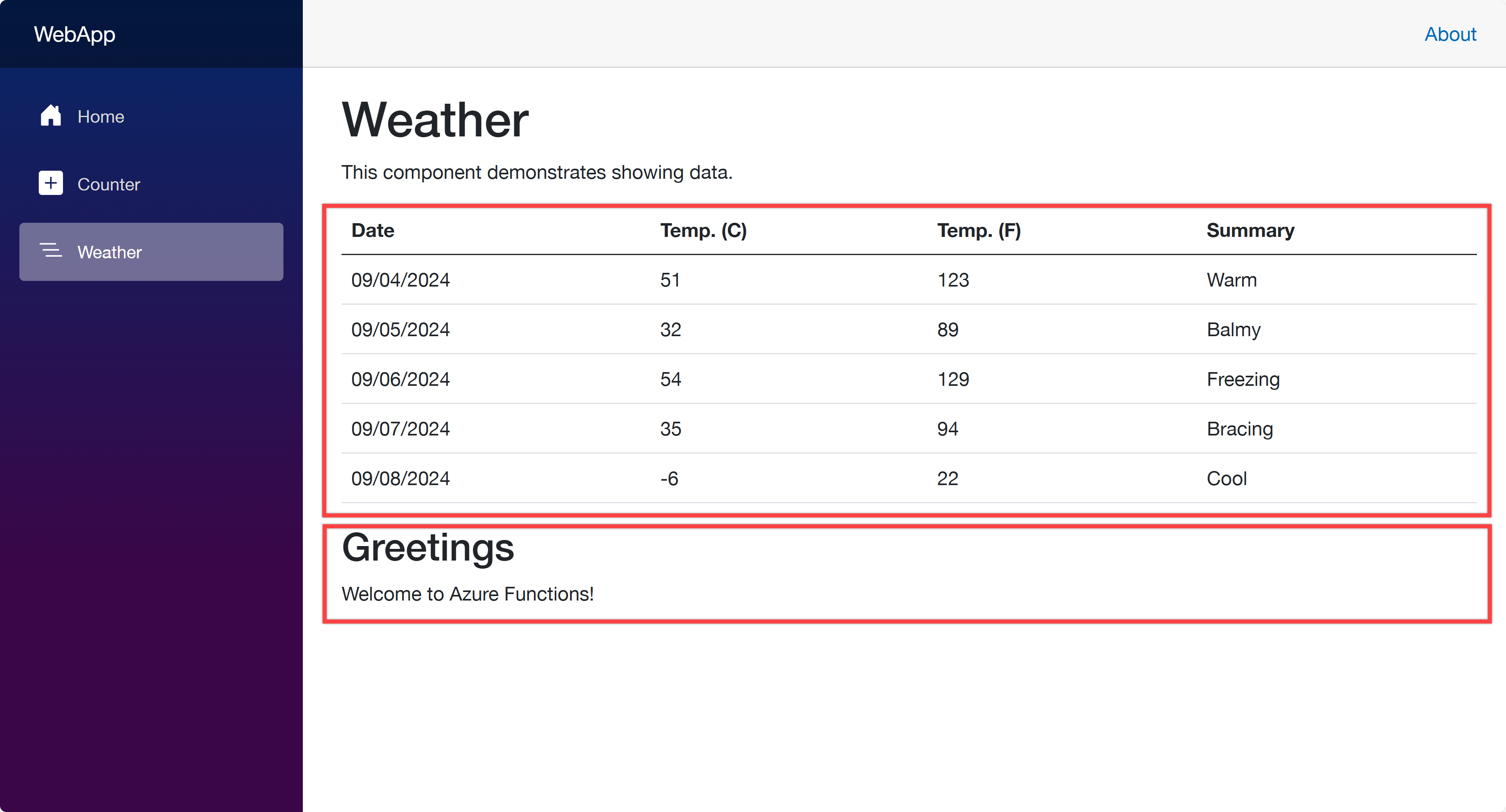
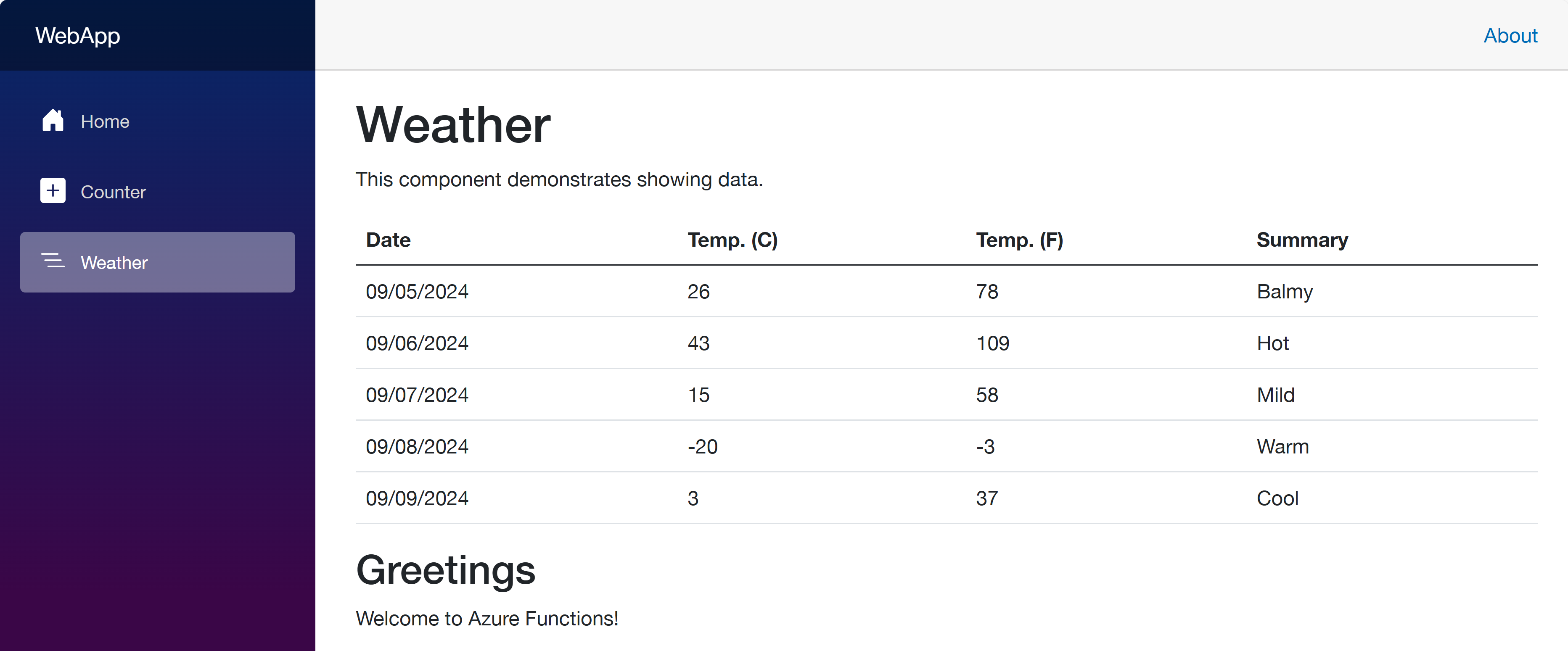
Open your web browser and navigate to https://localhost:5001 to see the Blazor app running. Then navigate to https://localhost:5001/weather to see the weather data fetched from the ApiApp and the greetings populated from the FuncApp.
Now, let’s start using azd to provision and deploy these apps to ACA. Make sure that you’ve already logged in to Azure with the azd auth login command.
azd init – Initialisation
In order to provision and deploy the apps to ACA, you need to initialise the azd configuration. Run the following command:
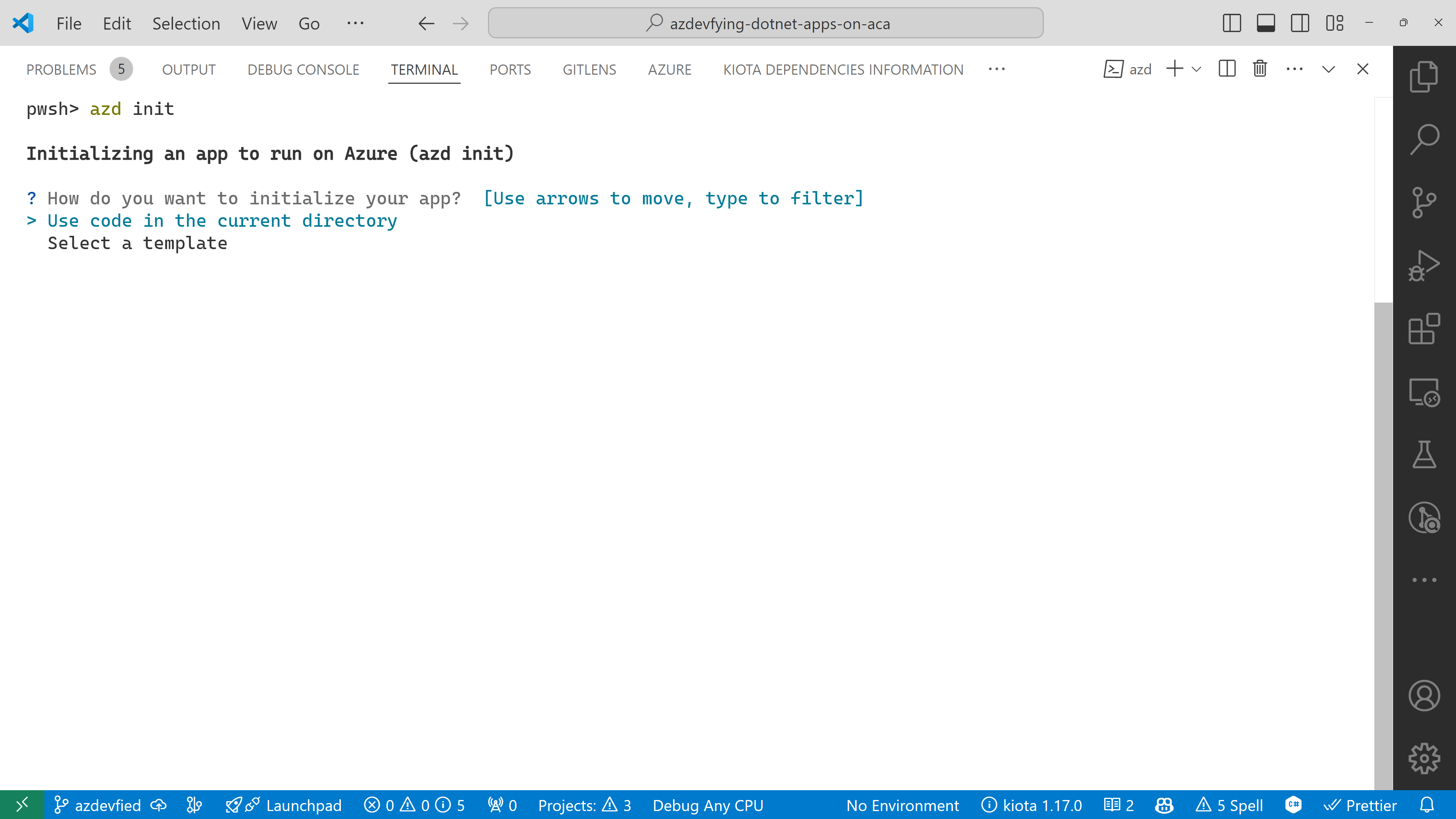
azd init
You’ll be prompted to initialise the app. Choose the Use code in the current directory option.
azd automatically detects your three apps as shown below. In addition to that, it says it will use Azure Container Apps. Choose the Confirm and continue initializing my app option.
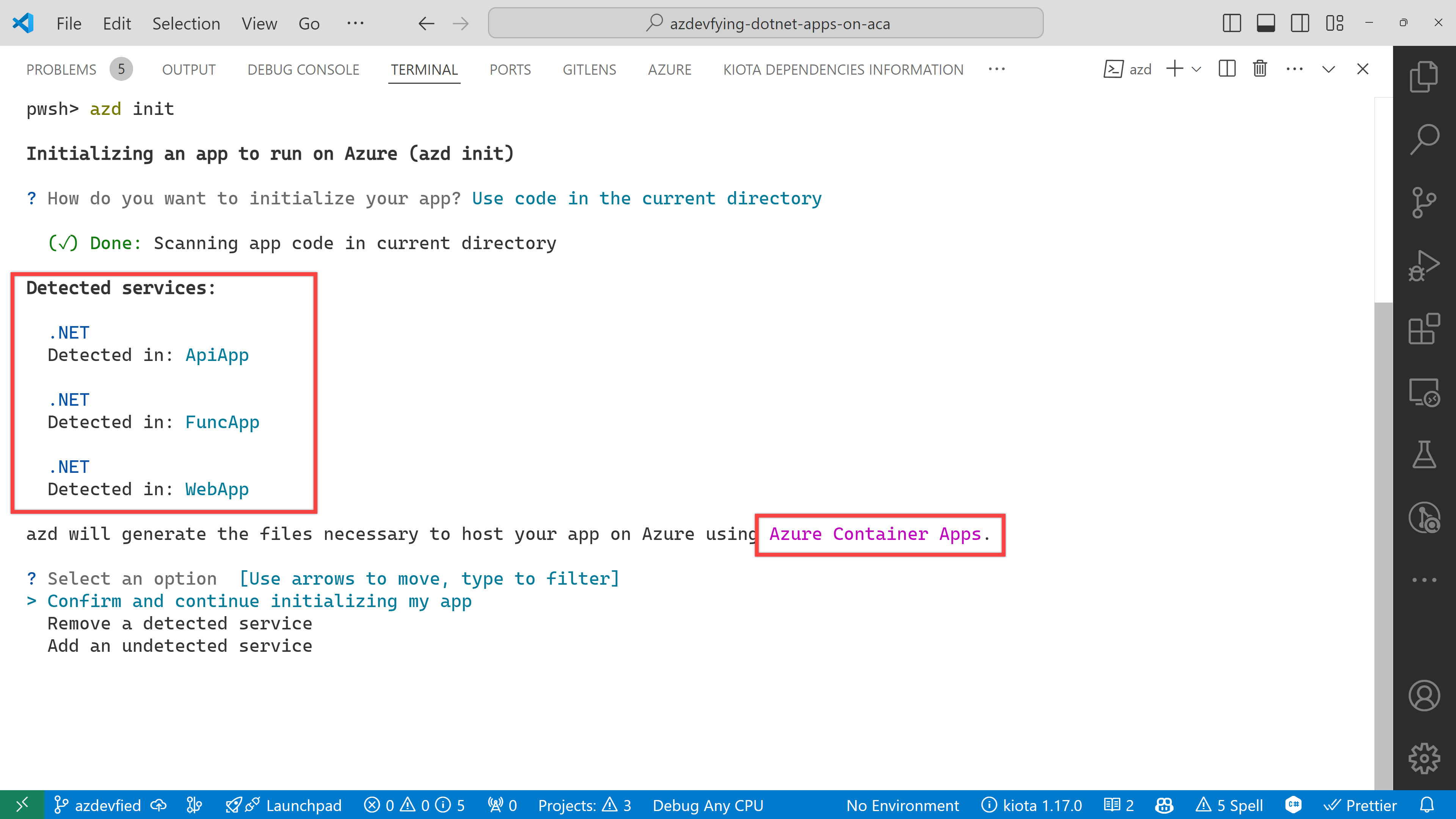
The function app asks the target port number. Enter 80.
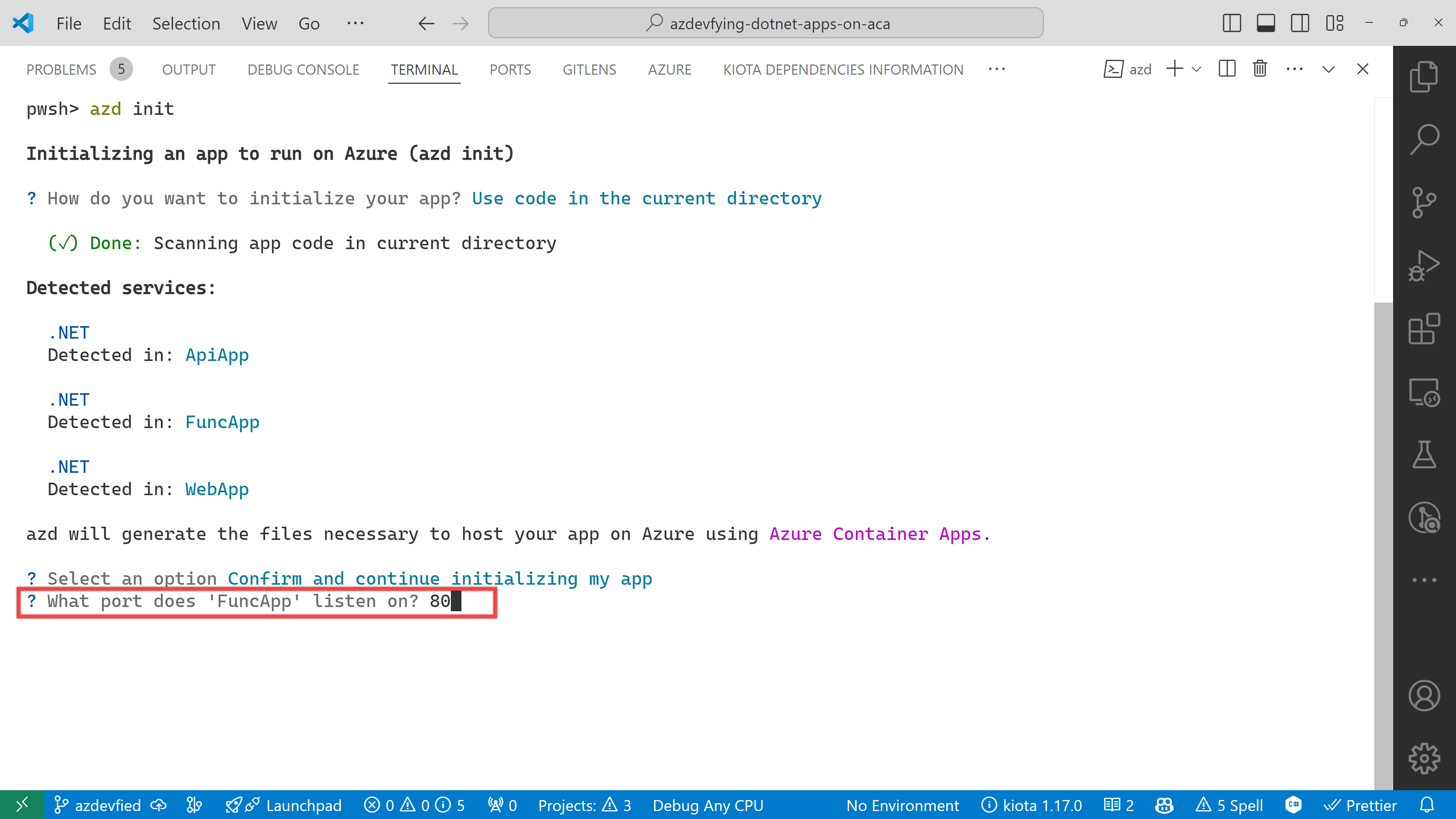
And finally, it asks the environment name. Enter any name you want. I just entered aca0906 for now.
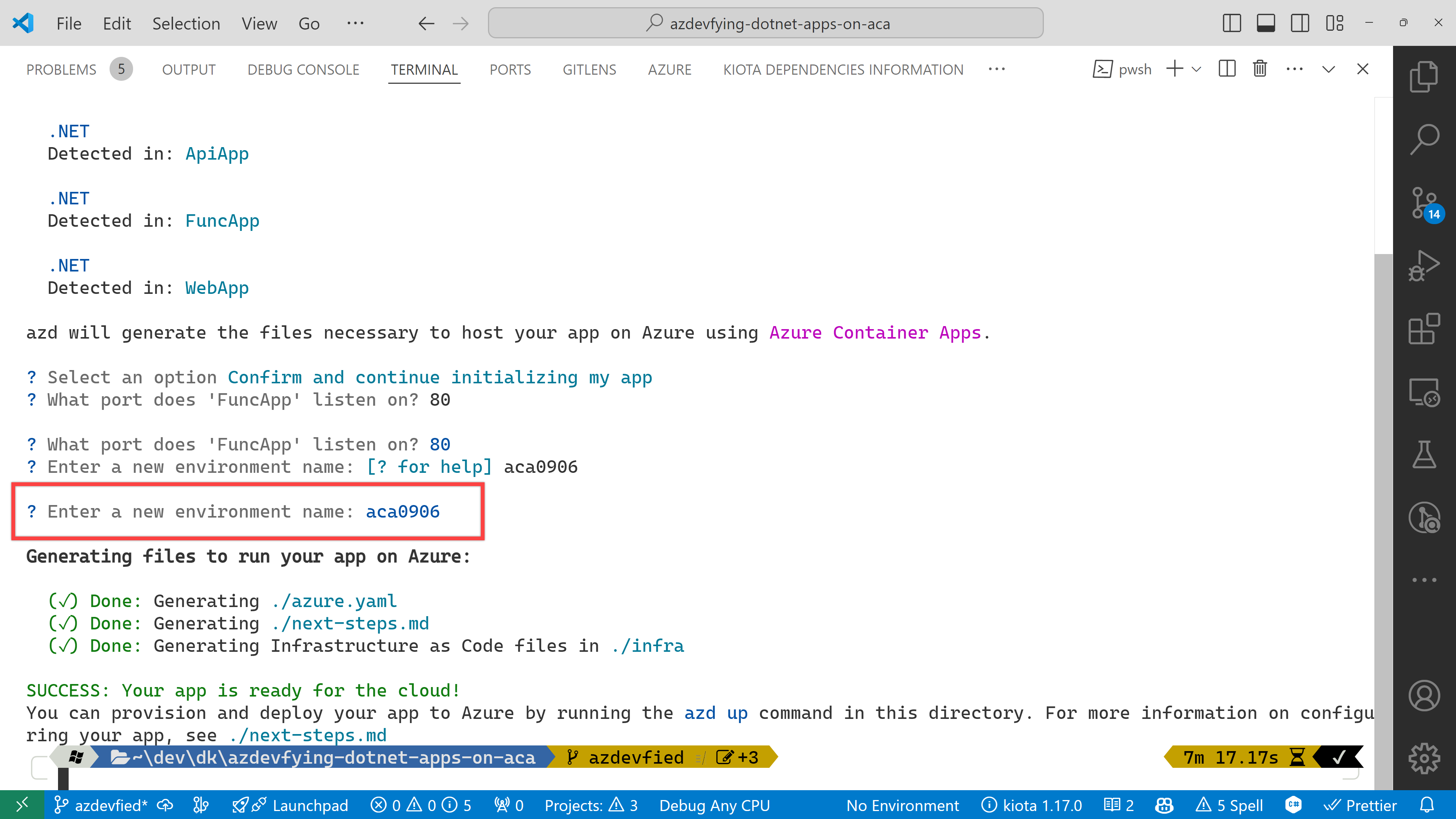
Now, you’ve got two directories and two files generated:
.azure directory
infra directory
next-steps.md file
azure.yaml file
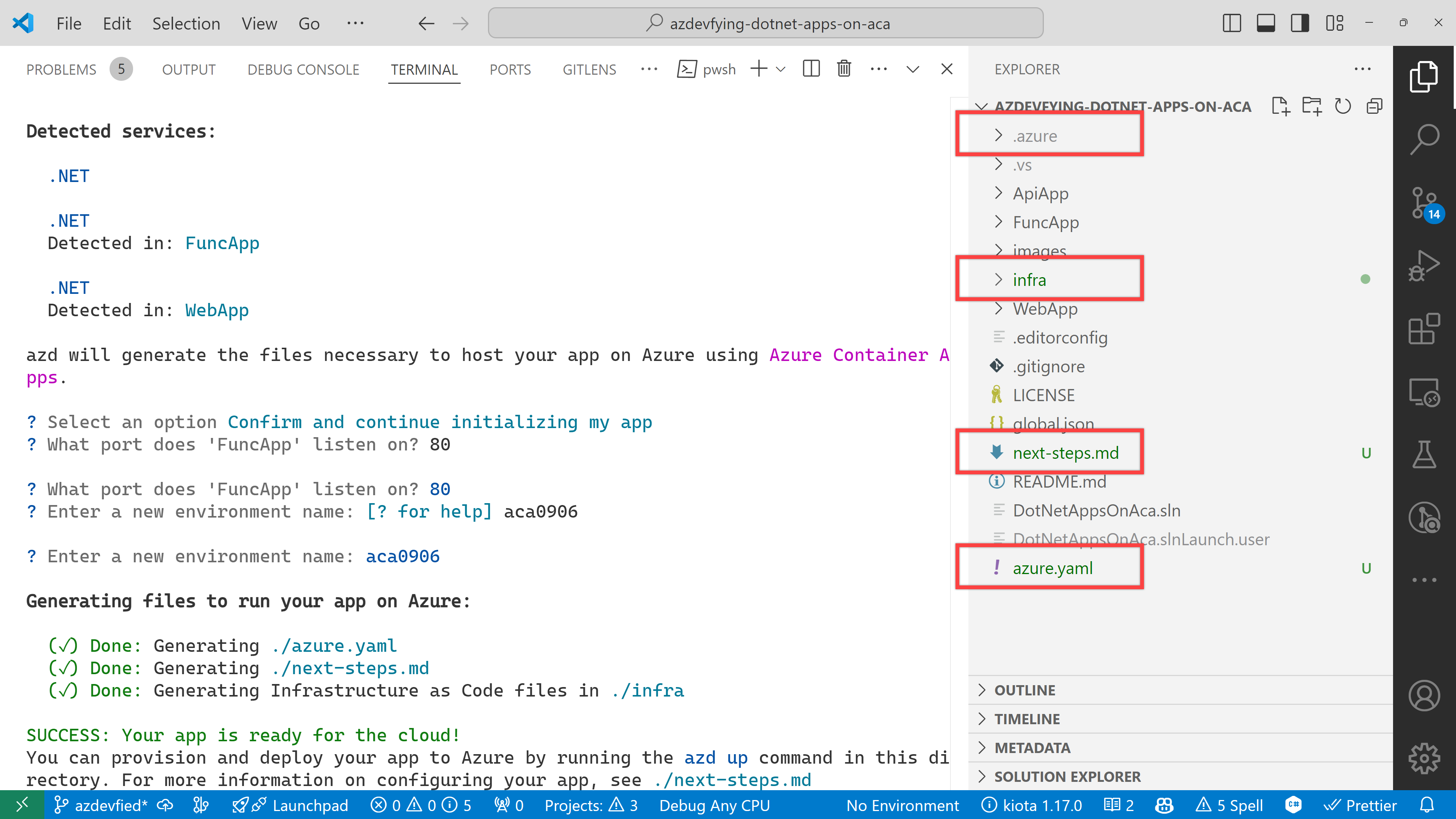
Under the infra directory, there are bunch of Bicep files automatically generated through azd init.
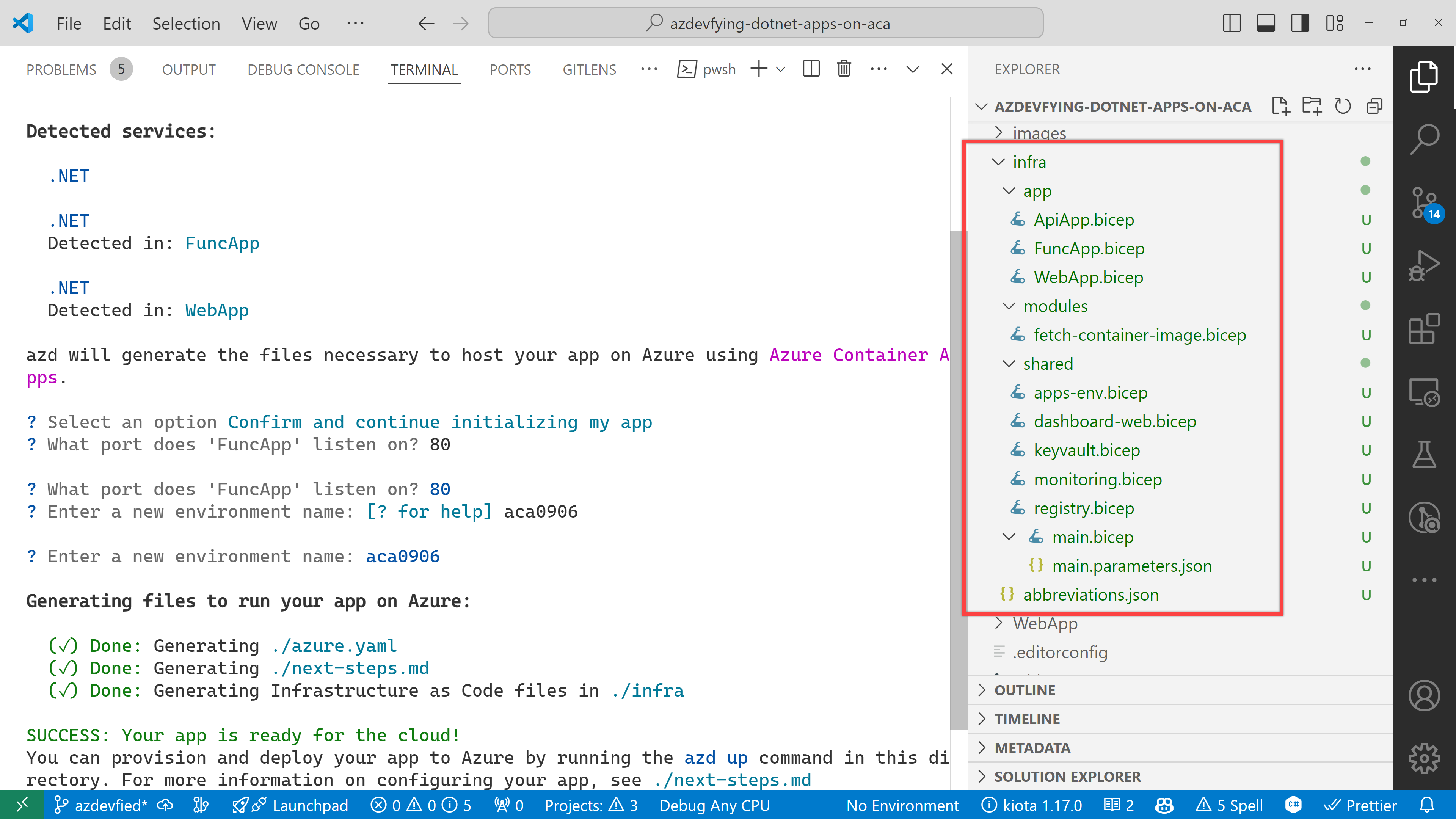
As a result of running the command, azd init, you don’t have to write all necessary Bicep files. Instead, it generates them for you, which significantly reduces the time for infrastructure provisioning. Now, you’re ready to provision and deploy your apps to ACA. Let’s move on.
azd up – Provision and deployment
All you need to run at this stage is:
azd up
Then, it asks you to confirm the subscription and location to provision the resources. Choose the appropriate options and continue.
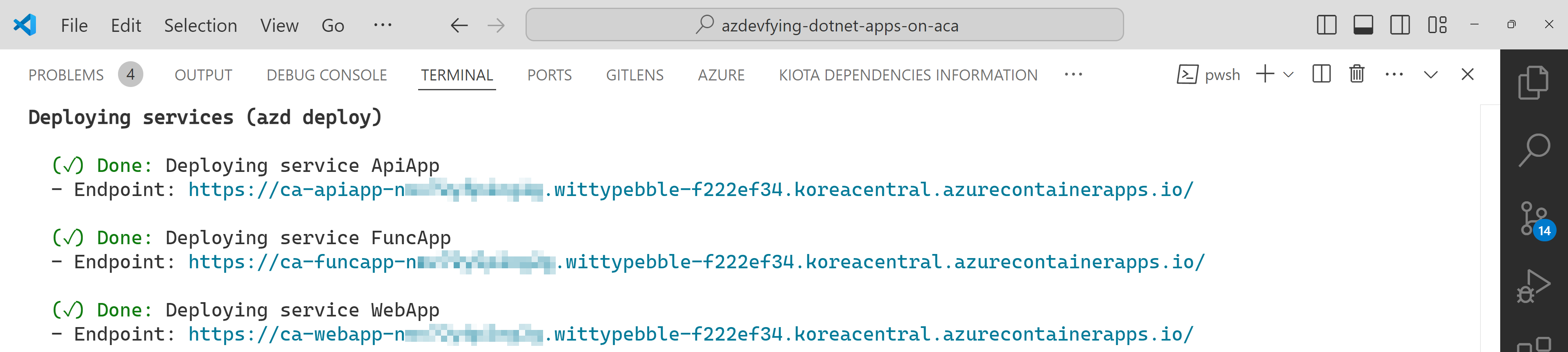
All apps are containerised and deployed to ACA. Once the deployment is done, you can see the output as shown below:
Click the web app URL and navigate to the /weather page. But you will see the error as shown below:
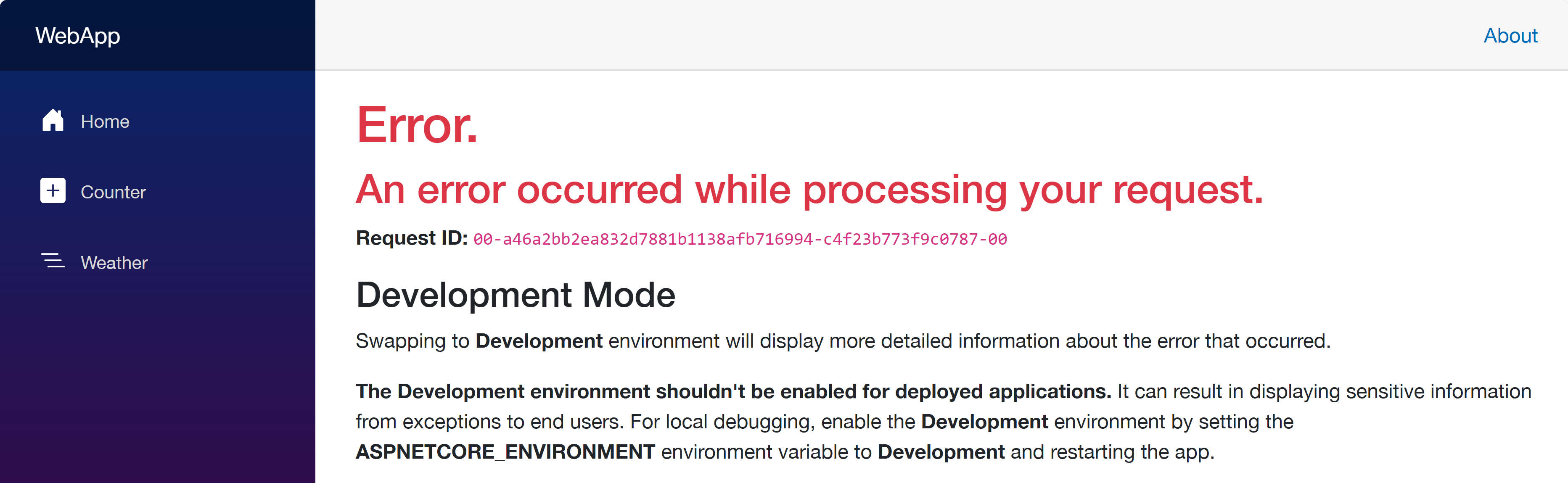
This is because each app doesn’t know where each other is. Therefore, you should update the Bicep files to let the web app know where the other apps are.
Update Bicep files – Service discovery
Open the infra/main.bicep file and update the webApp resource:
module webApp ‘./app/WebApp.bicep’ = {
name: ‘WebApp’
params: {
…
// Add these two lines
apiAppEndpoint: apiApp.outputs.uri
funcAppEndpoint: funcApp.outputs.uri
}
scope: rg
}
Then, open the infra/app/WebApp.bicep file and add both apiAppEndpoint and funcAppEndpoint parameters:
…
@secure()
param appDefinition object
// Add these two lines
param apiAppEndpoint string
param funcAppEndpoint string
…
In the same file, change the env variable:
// Before
var env = map(filter(appSettingsArray, i => i.?secret == null), i => {
name: i.name
value: i.value
})
// After
var env = union(map(filter(appSettingsArray, i => i.?secret == null), i => {
name: i.name
value: i.value
}), [
{
name: ‘API_ENDPOINT_URL’
value: apiAppEndpoint
}
{
name: ‘FUNC_ENDPOINT_URL’
value: funcAppEndpoint
}
])
This change passes the API and Function app endpoints to the web app as environment variables, so that the web app knows where the other apps are.
Once you’ve made the changes, run the azd up command again. It will update the resources in ACA. After that, go to the web app URL and navigate to the /weather page. You will see the weather data and greetings fetched from the API and Function apps.
So far, I’ve discussed how to provision and deploy .NET apps including Azure Functions to ACA with just one command, azd up. This is a very convenient way to deploy apps to Azure. However, to let the apps know each other, you should slightly tweak the auto-generated Bicep files. With this little tweak, all your .NET apps will be seamlessly provisioned and deployed to ACA.
One more thing I’d like to mention here, though, is that, if you use .NET Aspire, this sort of service discovery is automatically handled.
More about deploying .NET apps to ACA?
If you want to learn more options about deploying .NET apps to ACA, the following links might be helpful.
This article was originally published on Dev Kimchi.
by Contributed | Sep 5, 2024 | Technology
This article is contributed. See the original author and article here.
In today’s digital era, where data breaches and cyber threats are increasingly sophisticated and pervasive, the need for robust data security measures has never been more critical. Traditional security approaches are proving insufficient against the complex and evolving nature of modern cyber threats. This has led to a growing consensus among security experts and industry leaders on the imperative to incorporate Generative AI (GenAI) into data security frameworks. GenAI’s ability to analyze vast amounts of data in real-time, identify patterns, and predict potential threats offers a transformative approach to safeguarding sensitive information. According to a recent report by Gartner, the use of AI in cybersecurity is expected to reduce the number of data breaches by up to 20% by 2025, underscoring the industry’s recognition of AI’s vital role in enhancing data security (Gartner, 2022). This blog explores how Microsoft is leveraging GenAI to revolutionize data security, providing organizations with the tools they need to protect their digital assets effectively.
Leverage the power of Copilot to secure your organization
Human ingenuity and expertise will always be an irreplaceable component of defense, so we need technology that can augment these unique capabilities with skill sets, processing speeds, and rapid learning of AI. Technology that can work alongside us, detect hidden patterns and behaviors, and inform response at machine speed with the latest and most advanced security practices.
In this scenario, Microsoft Copilot for Security helps professionals across the many cybersecurity disciplines to be more effective and efficient at all the roles they play. It helps you enhance and grow your capabilities and skills, while also supporting the workflows and teams you collaborate with to solve security challenges. Since Copilot for Security uses GenAI to analyze data from many sources, including other Microsoft Security solutions, it can also help analysts catch what they might have otherwise missed. Copilot for Security synthesizes data and detects those important signals better than ever before, all in a single pane of glass, without having to jump between different solutions to get additional context.
Boost your data protection efficiency with Copilot for Security embedded in Purview
An important application of Copilot for Security is to empower and strengthen data security and data compliance teams in securing data with more efficiency and agility. Data security admins are often challenged by the high volume and complexity of alerts, and the integration between Microsoft Purview and Copilot for Security enables these tools to work together to protect your data at machine speed.
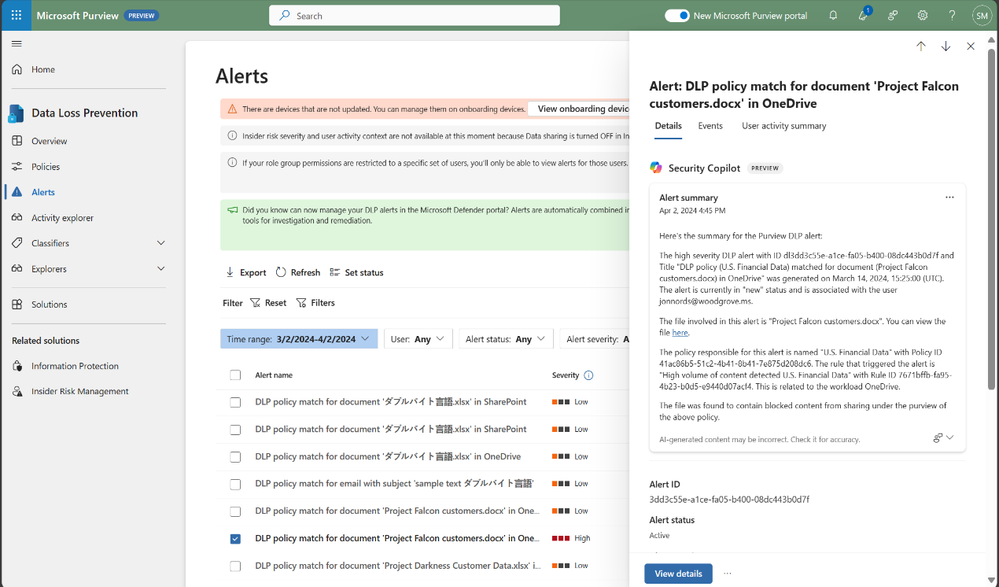
The speed at which data security investigations are conducted is crucial to preventing data loss. However, the task of analyzing a vast array of sources can pose a significant challenge for analysts at any experience level. With Copilot-powered comprehensive summaries of Microsoft Purview Data Loss Prevention (DLP) alerts, data security admins can identify, act on alerts and prevent data risks much faster and effectively. When an alert is summarized, it includes details such as policy rules, the source, and the files involved, as well as user risk level context pulled from Insider Risk Management (IRM).
 Figure 1: embedded Copilot summarization into Data Loss Prevention
Figure 1: embedded Copilot summarization into Data Loss Prevention
Your team can also leverage summaries in Microsoft Purview Insider Risk Management alerts, which enables faster understanding of potentially risky activity, user context, behavior sequences. and intent present in an alert. Moreover, we’re excited to announce the public preview of the Copilot for Security-powered enhanced hunting in IRM, where admins will be able to use GenAI-driven analytics to deepen investigations and double-click into a user’s risk profile and activities, beyond the alert summary.
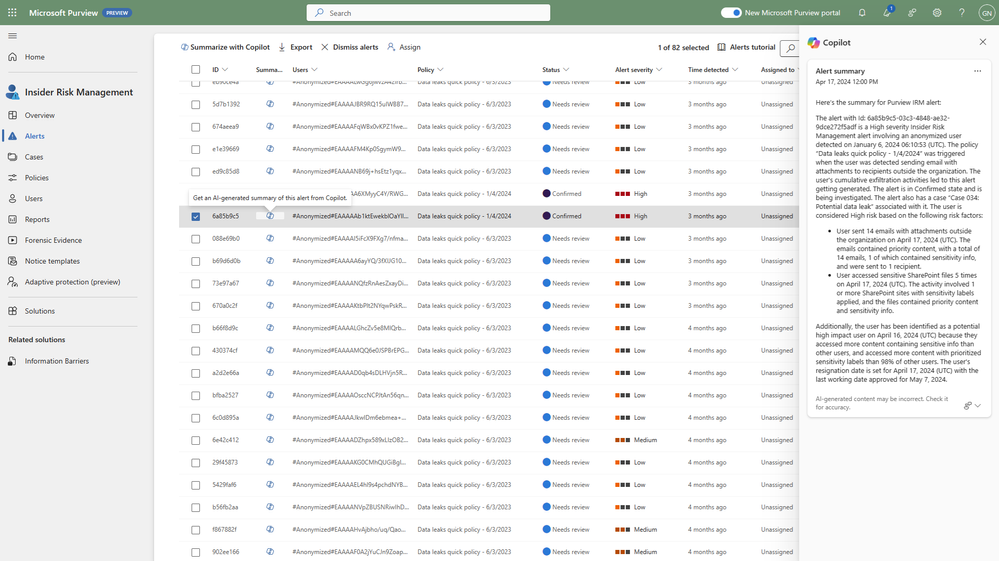 Figure 2: embedded Copilot summarization into Insider Risk Management
Figure 2: embedded Copilot summarization into Insider Risk Management
Compliance admins, forensic investigators, legal, and other teams can also strongly benefit from GenAI being incorporated into their workflows. Not only do they spend most of their time reviewing lengthy content and evidence; but admins need to invest time to learn complex technical capabilities like keyword query language to conduct a search, with 60% of admin time spent reviewing evidence collected in review sets.
Compliance teams are subject to regulatory obligations, like industry regulations or corporate policies related to business communications. This requires teams to review communication violations that contain lengthy content like meeting transcripts, group chats, long email threads and attachments. With concise and comprehensive contextual summaries on Microsoft Purview Communication Compliance, content can be evaluated against relevant compliance polices and investigators are able to get a summary of the policy match and better identify risky communication.
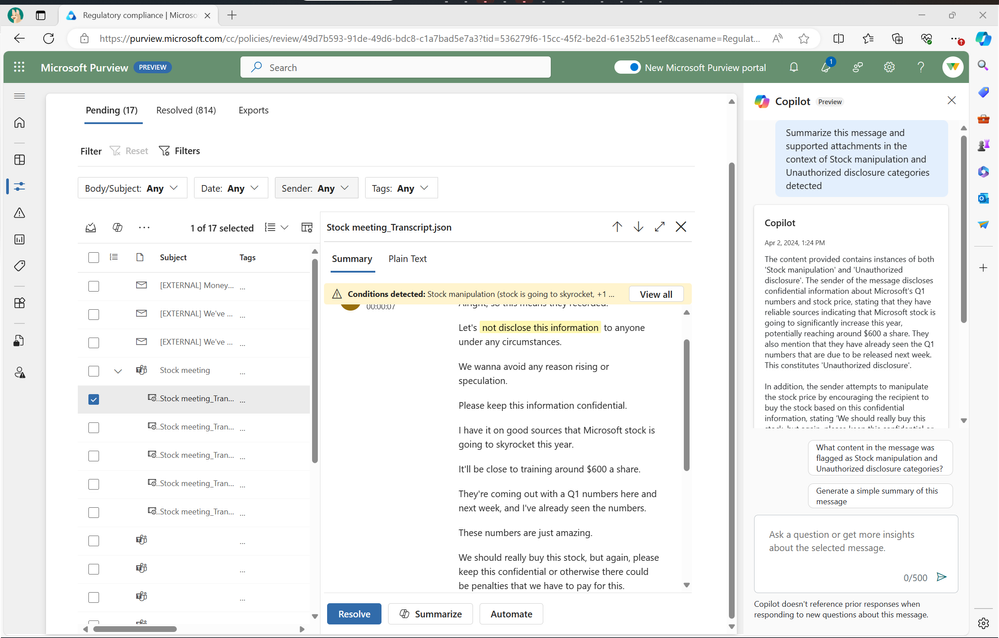 Figure 3: embedded Copilot summarization into Communication Compliance
Figure 3: embedded Copilot summarization into Communication Compliance
These contextualized summaries are also invaluable in Microsoft Purview eDiscovery, where they help simplify the exploration of large about of evidence data, which can take hours, days, even weeks to do. This process often requires costly resources like an outside council to manually go through each document to determine relevancy to the case, and this embedded Copilot for Security capability enables reducing days of legal investigations into seconds, by allowing an investigator to use Copilot to summarize items in a review set.
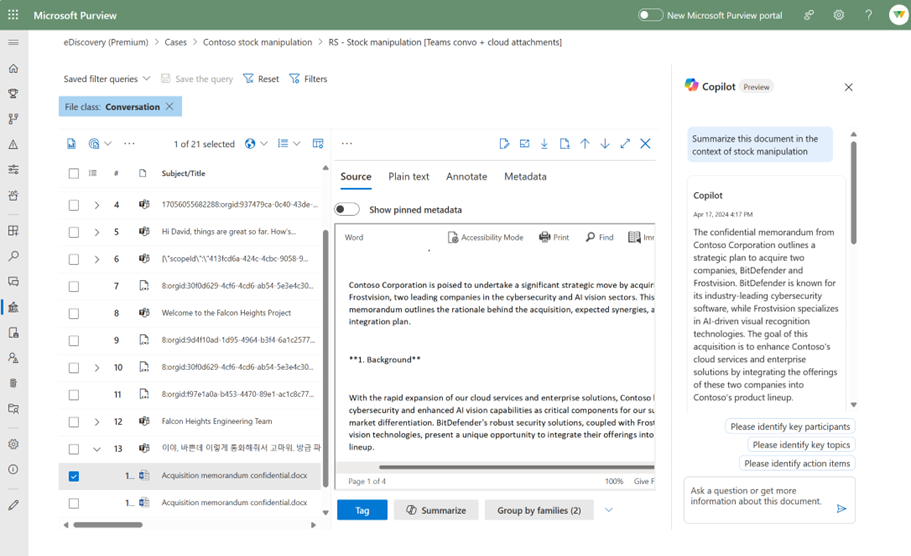 Figure 4: embedded Copilot summarization into eDiscovery
Figure 4: embedded Copilot summarization into eDiscovery
Search is one of the most difficult and time-intensive workflows in an eDiscovery investigation. Now, you can simplify investigation by leveraging Copilot for Security to translate inquiries from natural to keywork query language. This feature allows organizations to take Natural Language and convert that into assertive evidence queries, in doing so this can correct possible errors, boost team expertise, and enable analysts at all levels to carry out advanced investigations.
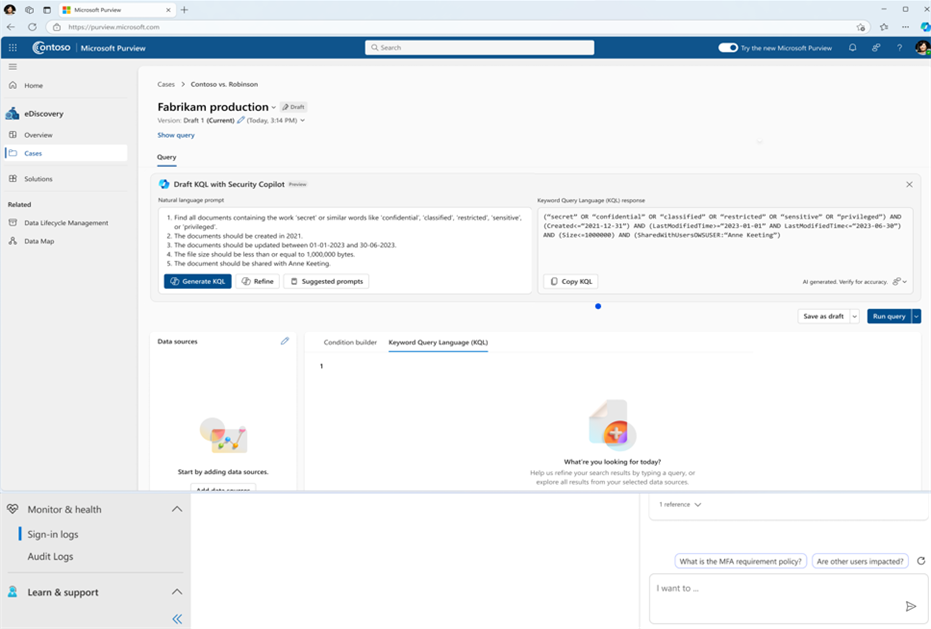 Figure 5: embedded Copilot search with Natural Language on eDiscovery
Figure 5: embedded Copilot search with Natural Language on eDiscovery
All these recent developments are just the beginning of the Copilot for Security journey into Microsoft Purview, and we’ll continue to share new advancements and GenAI-powered capabilities that will take your data security program to the next level.
To learn more about how Microsoft Purview can help you protect your data, check our website, or explore our learning resources focused on Copilot for Security in Purview.
Get Started
by Contributed | Sep 4, 2024 | Technology
This article is contributed. See the original author and article here.
With the new semester just around the corner, we’re excited to introduce some fantastic new features in Forms to enhance your teaching and learning experience. Now, you can enjoy an improved data sync function to stay up to date, set rules to collect more accurate responses, pre-fill forms and quizzes, and easily manage response notifications. Let’s dive in and check more details. You can also try out from this template.
Let’s create a science club registration together to explore how we can make the most of these new features. Imagine you are a high school science teacher and trying to establish a science club where students from all grades can dive into fascinating topics beyond the curriculum and participate in fun, hands-on activities.
Improved Excel data sync function
You can start with Excel for the web to create the registration form, no need to visit Forms. This process will automatically generate a new form in Forms where you can add your questions. All the questions you add and responses you receive will seamlessly sync with Excel. (check more details: Forms data sync to Excel is now fully available with more functionality – Microsoft Community Hub)
 Create forms from Excel for the web
Create forms from Excel for the web
Prefill answers for forms/quizzes
In this science club registration, you can use prefilled answers for fields like grade and class, creating unique links for each grade and class. This allows you to easily track and differentiate student distribution across different groups in the club. (check more details: Pre-fill Responses in Your Microsoft Forms – Microsoft Community Hub)
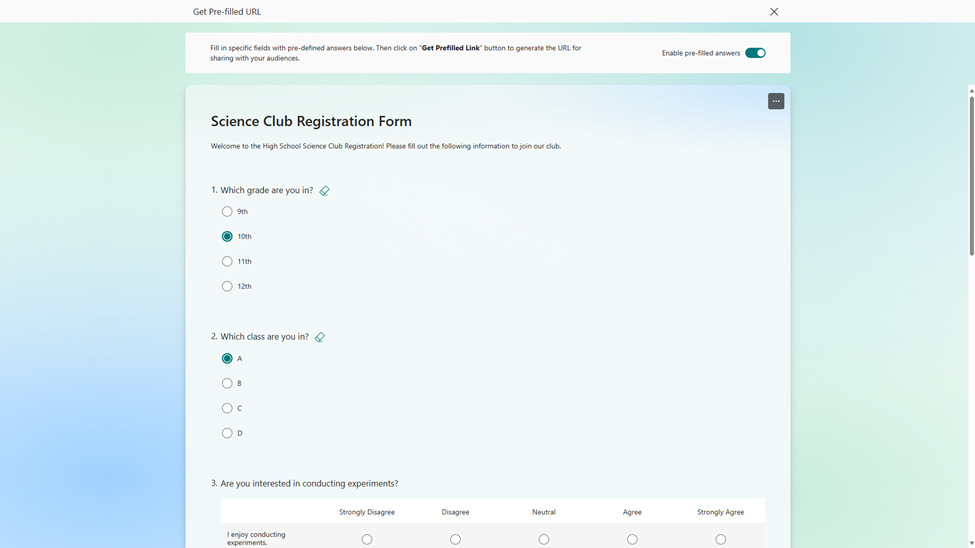 Set prefilled answer
Set prefilled answer
Validation for open text question
To make sure students provide correct contact information and receive timely updates, you can set restriction for open text questions to only accept email formats. (Other types of restriction are also supported in Forms, check more details here: Validate open text responses in Microsoft Forms – Microsoft Community Hub)
 Set validation on email address
Set validation on email address
Manage recipients of new response notification
You can set multiple key individuals to receive the notification when a new registration comes in, such as the club coordinator and an assistant. This allows them to quickly review and confirm new members, update the membership list, and prepare welcome materials. (check more details: Add or remove people from your form response notification emails – Microsoft Community Hub)
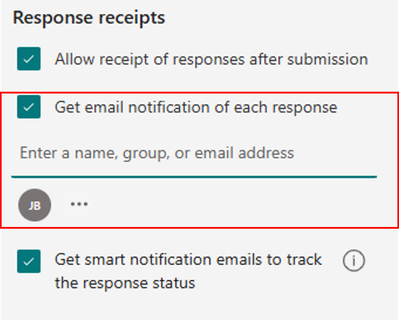 Add recipients for new response notification
Add recipients for new response notification
Hope you find these new features useful for the new semester. If you’re interested in trying them out, simply start with this template.
by Contributed | Sep 3, 2024 | Technology
This article is contributed. See the original author and article here.
Explore Azure AI Services: Prebuilt Models and Demos
Azure AI services provide a comprehensive suite of prebuilt models and demos designed to address a wide range of use cases. These models are readily accessible and allow you to implement AI-powered solutions seamlessly. We have curated and catalogued prebuilt demos available across Azure AI services. We hope this helps you infuse AI seamlessly into your products and services.
Speech Recognition
Speech to Text Scenarios
Scenario |
Description |
Link |
Real-time speech to text |
Quickly test your audio on a speech recognition endpoint without writing any code. |
Explore Demo |
Whisper Model in Azure OpenAI Service |
Transcribe and translate audio content from 57 languages into English using OpenAI Whisper v2-large model. |
Explore Demo |
Batch speech to text |
Transcribe large amounts of audio in storage asynchronously. |
Explore Demo |
Custom Speech |
Improve speech recognition accuracy with domain-specific vocabulary and data. |
Explore Demo |
Pronunciation Assessment |
Evaluate and get feedback on speech pronunciation accuracy and fluency. |
Explore Demo |
Speech Translation |
Translate speech into other languages in real-time with low latency. |
Explore Demo |
Text to Speech
Text to Speech Scenarios
Scenario |
Description |
Link |
Voice Gallery |
Choose from 486 voices across 148 languages and variants to create natural-sounding speech. |
Explore Demo |
Custom Neural Voice |
Create a natural-sounding synthetic voice based on human voice recordings. |
Explore Demo |
Personal Voice |
Create an AI voice from a human voice sample for personalized voice experiences. |
Explore Demo |
Audio Content Creation |
Build highly natural audio content for various scenarios like audiobooks and video narrations. |
Explore Demo |
Text to speech Avatar |
Turn your text into a video with an AI-generated avatar and realistic voice. |
Explore Demo |
Other Scenarios
|
|
|
Captioning with Speech to Text
|
Use our sample application to learn how to use Azure Speech to automatically caption your content in real-time and offline by transcribing the audio of films, videos, live events, and more. Display the resulting text on a screen to provide an accessible experience. In this example, we leverage features like speech to text and phrase list.
|
|
Post Call Transcription & Analytics
|
Batch transcribe call center recordings and extract valuable information such as Personal Identifiable Information (PII), sentiment, and call summary. This demonstrates how to use the Speech and Language services to analyze call center conversations.
|
|
|
Engage in natural conversations with an avatar that recognizes users’ speech input and responds fluently with realistic AI voice.
|
|
|
Get instant feedback on pronunciation accuracy, fluency, prosody, grammar, and vocabulary from your chatting experience.
|
|
|
Seamlessly translate and generate videos in multiple languages automatically. With its powerful capabilities, you can efficiently localize your video content to cater to diverse audiences around the globe.
|
|
Vision Studio
Vision-Based Scenarios
Scenario |
Description |
Link |
Video Retrieval and Summary |
Quickly summarize the main points of a video and search for specific moments. |
Explore Demo |
Customize Models with Images |
Find specific objects within images for use cases like product placement and assembly line checks. |
Explore Demo |
Add Dense Captions to Images |
Generate human-readable captions for all important objects detected in your image. |
Explore Demo |
Remove Backgrounds from Images |
Easily remove the background and preserve foreground elements. |
Explore Demo |
Add Captions to Images |
Generate a human-readable sentence that describes the content of an image. |
Explore Demo |
Detect Common Objects in Images |
Detect and extract bounding boxes for recognizable objects and living beings. |
Explore Demo |
Extract Text from Images |
Use OCR to extract printed and handwritten text from images, PDFs, and TIFF files. |
Explore Demo |
Extract Common Tags from Images |
Extract tags based on recognizable objects, scenery, and actions. |
Explore Demo |
Create Smart-Cropped Images |
Automatically crop images to emphasize the most important areas. |
Explore Demo |
Detect Faces in an Image |
Detect the location of human faces and their attributes in images. |
Explore Demo |
Count People in an Area |
Analyze video to count the number of people in a designated zone. |
Explore Demo |
Detect When People Cross a Line |
Detect when a person crosses a line in the camera’s field of view. |
Explore Demo |
Language Studio
Language Processing Scenarios
Scenario |
Description |
Link |
Extract PII |
Identify sensitive personally identifiable information (PII) in text. |
Explore Demo |
Extract Key Phrases |
Quickly identify the main points from unstructured text. |
Explore Demo |
Find Linked Entities |
Disambiguate the identity of entities found in text by linking to a knowledge base. |
Explore Demo |
Extract Named Entities |
Identify and categorize entities in text using Named Entity Recognition (NER). |
Explore Demo |
Extract Health Information |
Extract and label medical information from unstructured texts. |
Explore Demo |
Analyze Sentiment and Opinions |
Provide sentiment labels and confidence scores at the sentence and document level. |
Explore Demo |
Detect Language |
Determine the language used in the input document and return a confidence score. |
Explore Demo |
Custom Text Classification |
Create custom text classification projects with labeled data and trained models. |
Explore Demo |
Answer Questions |
Extract answers to questions from passages of text provided. |
Explore Demo |
Conversational Language Understanding Projects |
Build projects with labeled data and trained models for understanding conversational language. |
Explore Demo |
Orchestration Projects |
Build and manage projects that integrate multiple language services. |
Explore Demo |
Summarize Information |
Produce summaries for conversations or documents using summarization APIs. |
Explore Demo |
|
Batch translate documents into one or more languages either from local storage or Azure Blob Storage
|
|
Document Intelligence
Document Analysis Scenarios
Scenario |
Description |
Link |
Read |
Extract printed and handwritten texts along with barcodes and formulas from documents. |
Explore Demo |
Layout |
Extract tables, checkboxes, and text from forms and images. |
Explore Demo |
General Documents |
Extract key-value pairs and structure from any form or document. |
Explore Demo |
Prebuilt Models Scenarios
|
|
|
Extract invoice details including customer and vendor details, totals, and line items.
|
|
Extract transaction details from receipts including date, merchant information, and totals.
|
|
Extract details from passports and ID cards.
|
US Health Insurance Cards
|
Extract details from US health insurance cards.
|
|
Classify then extract information from documents containing any number of W2s, 1040s, 1098s and 1099s.
|
|
Extract information from a variety of mortgage
|
|
Extract employee information, payment information including earnings, deductions, net pay and more.
|
|
|
|
Extract amount, date, pay to order MICR numbers, name and address of the player, and more.
|
|
Extract details from marriage certificates.
|
|
Extract details from credit cards including card number and cardholder name.
|
|
Extract title and signatory parties’ information from contracts.
|
|
Extract contact details from business cards.
|
Gen-AI Safety Solutions
Safeguard your image content
|
|
|
|
This is a tool for evaluating different content moderation scenarios. It takes into account various factors such as the type of content, the platform’s policies, and the potential impact on users. Run moderation tests on sample content. Use Configure filters to rerun and further fine tune the test results. Add specific terms to the block list that you want detect and act on.
|
|
Moderate Multimodal content
|
Run moderation test on image and text combined contents. Assess the test results with detected severities.
|
|
Safeguard your Text
|
|
|
|
Run moderation tests on text contents. Assess the test results with detected severities.
|
|
|
Groundedness detection detects ungroundedness generated by the large language models (LLMs).
|
|
Protected Material Detection
|
Detect and protect third-party text material in LLM modules.
|
|
|
Prompt shields provides a unified API that addresses the following types of attacks: Jailbreak attacks and Indirect attacks.
|
|
Real-time Safety Measures
|
|
|
|
This will display your API usage, moderation results, and their distributions per category. You can customize the severity threshold for each category to view the updated results and deploy the new threshold to your end. Additionally, you can edit the blocklist on this page to respond to any incidences.
|
|














Recent Comments