by Contributed | Apr 15, 2024 | Technology
This article is contributed. See the original author and article here.
With more than 800,000 organizations depending on Microsoft Entra to navigate the constantly evolving identity and network access threat landscape, the need for increased transparency regarding product updates — particularly changes you may need to take action on — is critical.
Today, I’m thrilled to announce the public preview of What’s New in Microsoft Entra. This new hub in the Microsoft Entra admin center offers you a centralized view of our roadmap and change announcements across the Microsoft Entra identity and network access portfolio. In this article, I’ll show you how admins can get the most from what’s new to stay informed about Entra product updates and actionable insights.
Discover what’s new in the Microsoft Entra admin center
Because you’ll want visibility to product updates often, we’ve added what’s new to the top section of the Microsoft Entra admin center navigation pane.
 Figure 1: What’s new is available from the top of the navigation pane in the Microsoft Entra admin center.
Figure 1: What’s new is available from the top of the navigation pane in the Microsoft Entra admin center.
What’s new is not available in Azure portal, so we encourage you to migrate to the Microsoft Entra admin center if you haven’t already. It’s a great way to manage and gain cohesive visibility across all the identity and network access solutions.
Overview of what’s new functionality
What’s new offers a consolidated view of Microsoft Entra product updates categorized as Roadmap and Change announcements. The Roadmap tab includes public previews and recent general availability releases, while Change announcements detail modifications to existing features.
Highlights tab
To make your life easier, the Highlights tab summarizes important product launches and impactful changes.
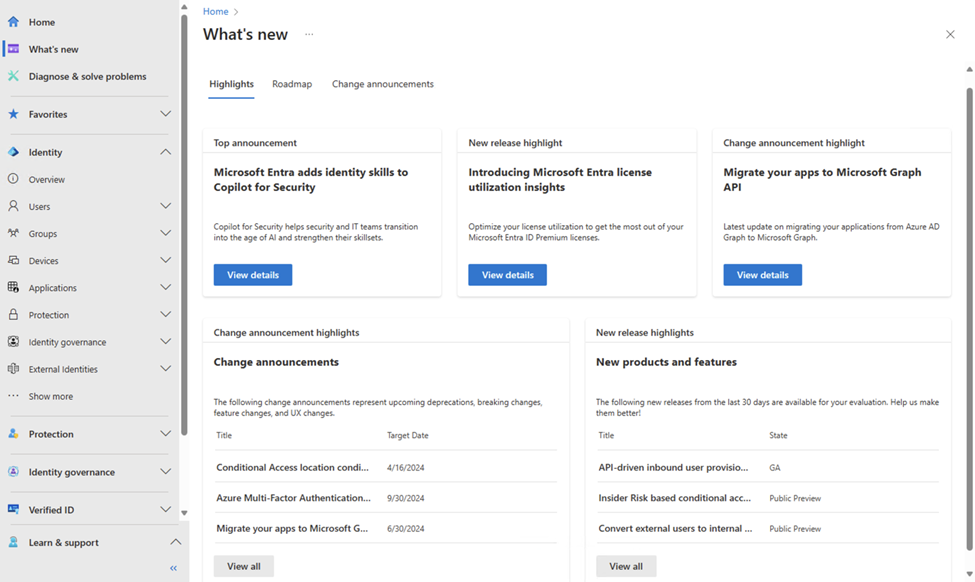 Figure 2: The highlights tab of what’s new is a quick overview of key product launches and impactful changes.
Figure 2: The highlights tab of what’s new is a quick overview of key product launches and impactful changes.
Clicking through the items on the highlights tab allows you to get details and links to documentation to configure policies.
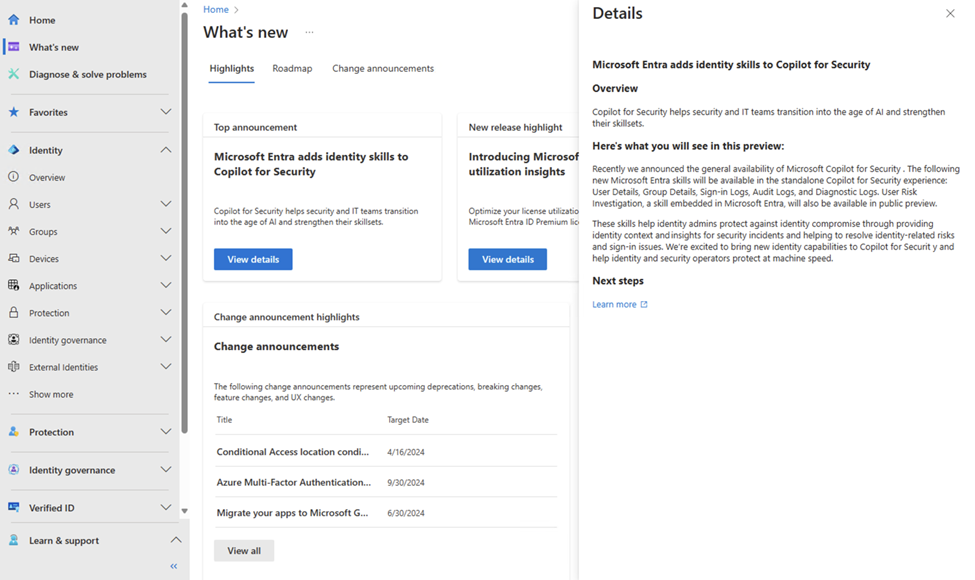 Figure 3: Click View details to learn more about an announcement.
Figure 3: Click View details to learn more about an announcement.
Roadmap tab
The Roadmap tab allows you to explore the specifics of public previews and recent general availability releases.
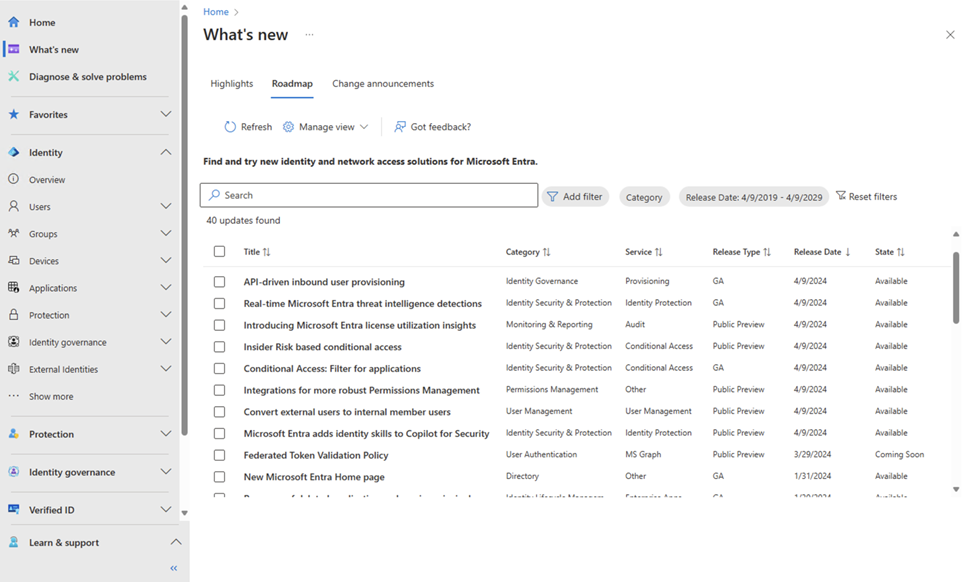 Figure 4: The Roadmap tab lists the current public preview and recent general availability releases.
Figure 4: The Roadmap tab lists the current public preview and recent general availability releases.
To know more, you can click on a title for details of that release. Click ‘Learn more’ to open the related documentation.
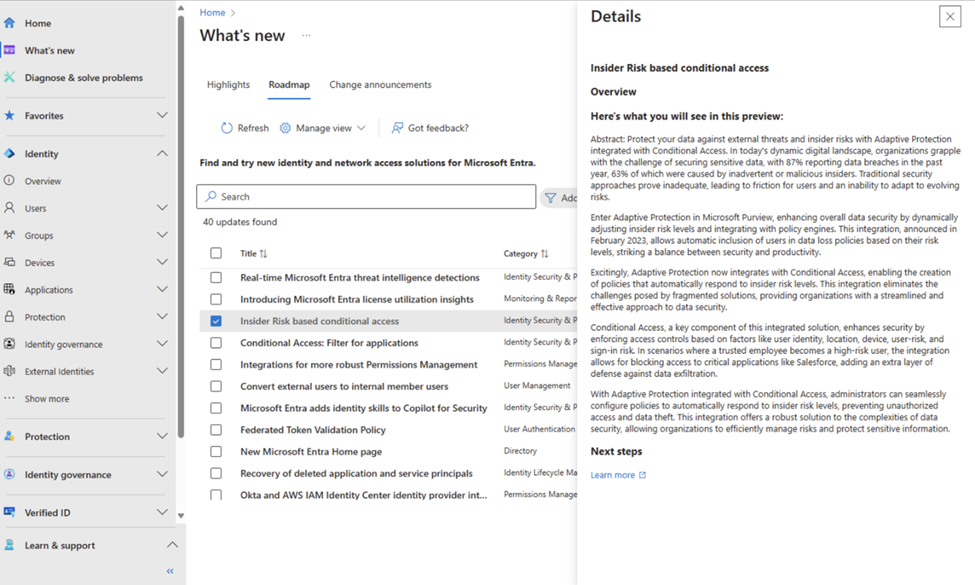 Figure 5: Learn more about an announcement by clicking its title.
Figure 5: Learn more about an announcement by clicking its title.
Change Announcements tab
Change announcements include upcoming breaking changes, deprecations, retirements, UX changes and features becoming Microsoft-managed.
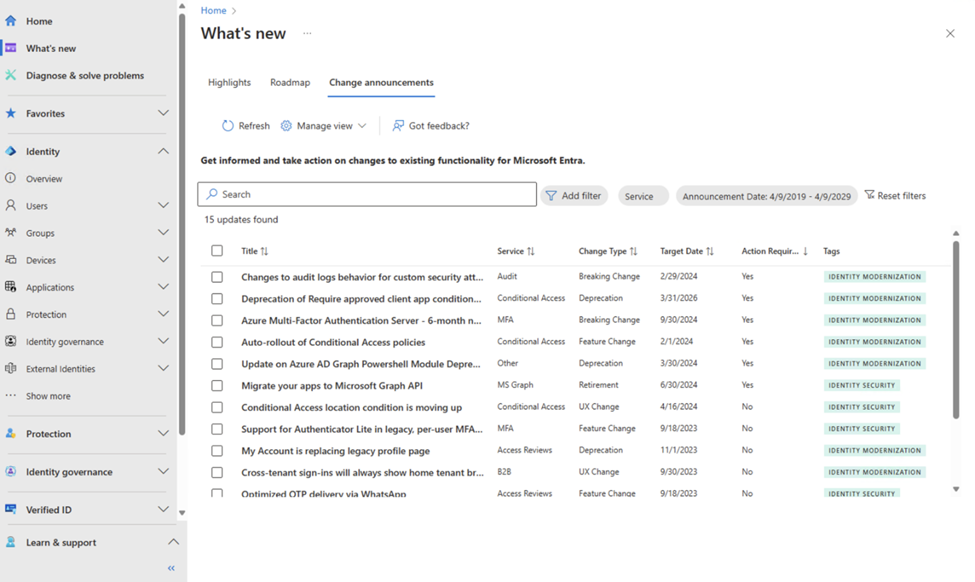 Figure 6: Change announcements tab displays changes to the existing features.
Figure 6: Change announcements tab displays changes to the existing features.
You can customize your view according to your preferences, by sorting or by applying filters to prepare a change implementation plan.
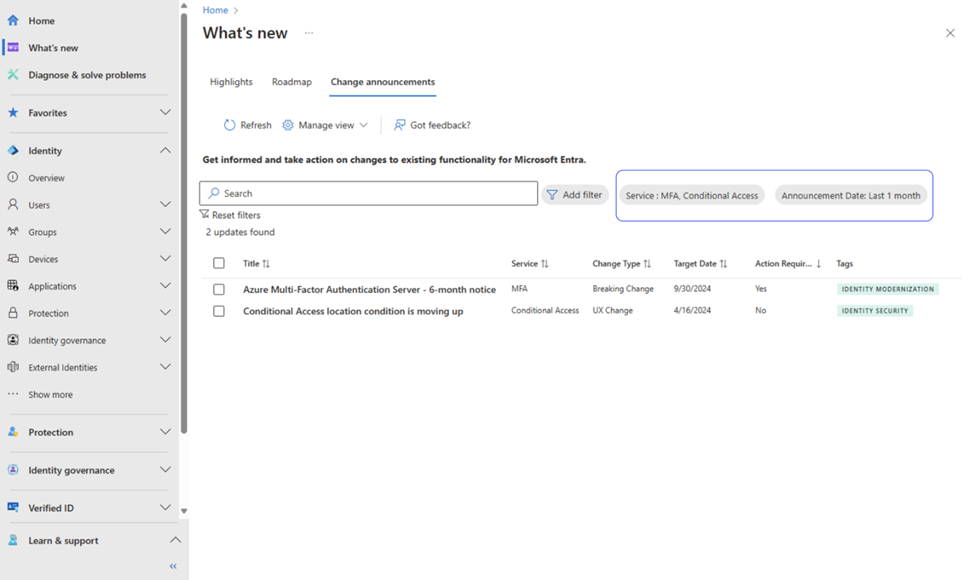 Figure 7: Apply filters, sort by columns to create a customized view.
Figure 7: Apply filters, sort by columns to create a customized view.
What’s next?
We’ll continue to extend this transparency into Entra product updates and look forward to elevating your experience to new heights. We would love to hear your feedback on this new capability, as well as what would be most useful to you. Explore what’s new in Microsoft Entra now.
Best regards,
Shobhit Sahay
Learn more about Microsoft identity:

by Contributed | Apr 14, 2024 | Technology
This article is contributed. See the original author and article here.
Unleashing Your Potential with Cloud Ready Skills
Are you a student or professional looking to enhance your technical skills?

Are you looking to kickstart your employability & take part in some friendly rivalry against other students?
Register for the University AI Cloud Challenge 2024 for your Microsoft Professional certification in AI whilst competing with other university students to gain top spot on our leaderboard and win prizes!
What: University Cloud Challenge ’24 UK & Spain AI Edition
Where: Online any student from UK or Spain based University or College
When: Live Webinar kick off session 2pm GMT 15th of April 2024 (available on demand after the 15th)
How: Register now: https://aka.ms/UCC24-AI
Register now to gain access to:
FREE access to live kick off webinar session
FREE practice assessment
FREE exam for the Microsoft Azure AI Fundamentals certification (AI-900)
Note: Exams to be taken between 15th April and 14th of May 2024

Help your university win the University AI Cloud Challenge!
Join the University AI Cloud Challenge 2024 and unlock your potential with cloud-ready skills. Gain a Microsoft Professional certification in AI, compete with students across the UK and Spain, and win exciting prizes. Register now to access our live webinar, free practice assessment, and free AI-900 exam. Help your university top our leaderboard and become the 2024 Student Learning Champion. Register, learn, and certify at no cost. Start your cloud journey today.
The race is on to find the 2024 champion Student Learning Campions for UK and Spain. Students Register, learn and certify at no cost!
University Leaderboard: You can view the current leaderboard here: (coming soon, after the first live webinar)
Scoring
Your university will score points for your activity. Points will be awarded as follows:
- Student Registration 1 point
- Student attends webinar 10 points
- Student access Microsoft Learn 10 points
- Student completed AI-900 exam – actual exam score converted to points (out of 1000)
Prizes
The University AI Cloud Challenge 2024 award will be presented to the university which scores the highest total score for all of their students that compete.
A box of Microsoft branded ‘swag’ will also be issued to the top 3 scoring universities.
Please review the terms and conditions here.
by Contributed | Apr 12, 2024 | Technology
This article is contributed. See the original author and article here.
Our goal is to support our customers’ needs, wherever they might be. To this end, we’re introducing the Surface API Management Service, aimed at simplifying how you access information about your devices, coverage and insights.
 Extend Surface Management Portal
Extend Surface Management Portal
This service builds on the familiar Surface Management Portal, enabling IT admins to directly access Microsoft coverage and entitlement information for their devices via API endpoints. It’s a practical enhancement for those already using the portal, designed to make device management more straightforward.
The service at a glance
The Surface API Management Service is an API management system that allows you to gain access to APIs that provide you with information about your devices.
These APIs serve as a direct conduit for customers seeking to streamline their asset management processes. By seamlessly connecting to the API, IT admins gain immediate access to critical device and warranty information, essential for effective asset oversight. Tailored specifically for Surface customers, this integration offers a hassle-free solution, eliminating the need for convoluted data acquisition methods. Now, with the simple integration of this API, customers can quickly retrieve pertinent details, empowering organizations to make informed decisions and optimize their asset management strategies.
Our first launch experience will allow current Surface Management Portal users to get their Microsoft coverage and entitlement information for their devices directly through API endpoints. Through our portal you can also see more of the performance and usage of the APIs across the globe with Surface API Management Service Reports.
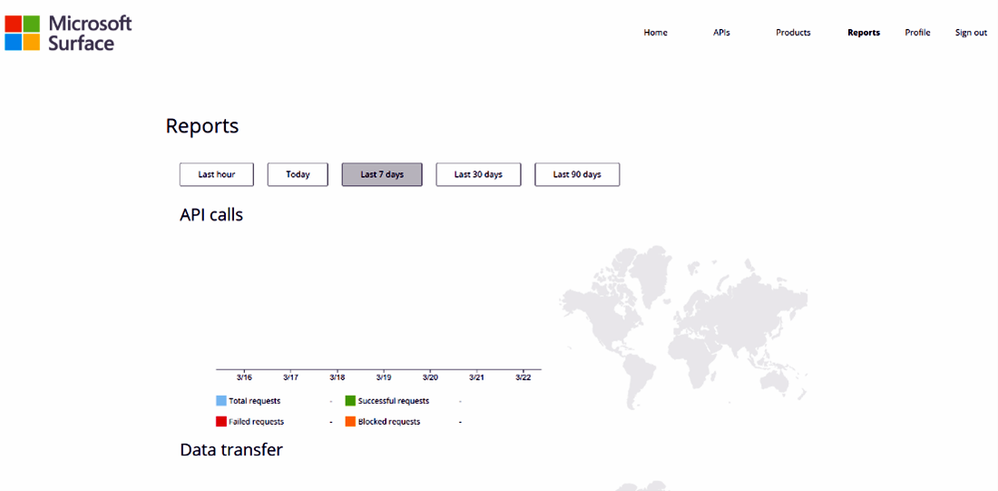
Get access to Surface API Management Services
To access, you need an active Surface Management Portal Account and a completed customer validation check. (If you have access to create service requests within Surface Management Portal you have been approved.)
Email request to surfaceapimanagement@microsoft.com:
Subject: “Requesting Access to Surface API Management Service”
Include the following info:
- Company Name
- Tenant ID
- Tenant primary domain (e.g. contoso.onmicrosoft.com)
- Application (client) ID*
- Estimated quantity of Intune-registered Surface devices in your organization
|
Get started
To get started with using the APIs, see the Readme on GitHub.
by Contributed | Apr 12, 2024 | Technology
This article is contributed. See the original author and article here.
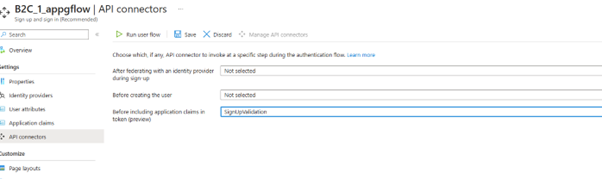
I was recently working with a customer who is using Azure AD B2C API Connector to enrich tokens with claims from external sources. They are using Azure Function App as the external source. As this setup demands, they exposed Azure Function App over public IP to work with B2C. But due to enterprise security restriction policy they must remove public endpoint from Function App and use private endpoints to VNET.
They thought of 2 options to expose the Function App securely over internet – using Azure API Management instance to a virtual network – external mode APIM in external mode or using Azure Application Gateway. But in both the cases B2C auth process errors out after adding the API Connector in the user flow:

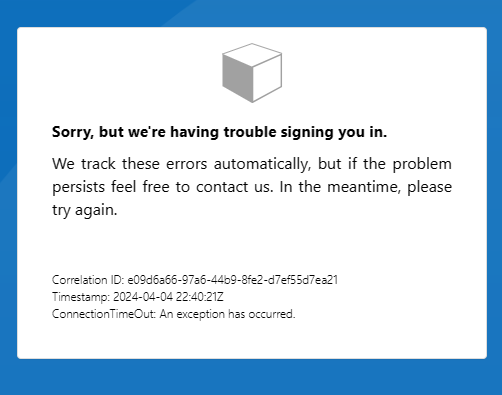
Initially I investigated on the error messages collected at the B2C, and APIM or Azure Application Gateway end. But later realized the main source of problem lies somewhere else. It is the ASP.NET Core framework used in building the Function App.
We need to modify default FowardedHeaders middleware settings. Otherwise, it will ignore the X-Forwarded headers being sent by APIM or Application Gateway because it isn’t in the list of KnownProxies and KnownNetworks. Please see the following links to understand the concept better:
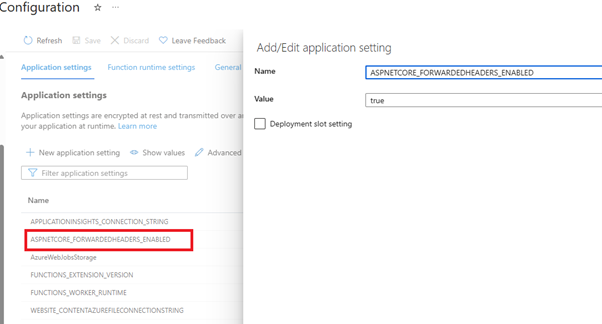
So, I did the following changes:
1. Added ASPNETCORE_FORWARDEDHEADERS_ENABLED application setting to my Function App Configuration:
2. Added a Startup.cs file in my function app code.
using System.Collections.Generic;
using Microsoft.AspNetCore.Builder;
using Microsoft.Azure.Functions.Extensions.DependencyInjection;
using Microsoft.Extensions.DependencyInjection;
[assembly: FunctionsStartup(typeof(TestAPIFunctionApp.Startup))]
namespace TestAPIFunctionApp
{
public class Startup : FunctionsStartup
{
public override void Configure(IFunctionsHostBuilder builder)
{
builder.Services.Configure(options =>
{
options.ForwardedHeaders = Microsoft.AspNetCore.HttpOverrides.ForwardedHeaders.XForwardedFor | Microsoft.AspNetCore.HttpOverrides.ForwardedHeaders.XForwardedProto | Microsoft.AspNetCore.HttpOverrides.ForwardedHeaders.XForwardedHost;
options.KnownNetworks.Clear();
options.KnownProxies.Clear();
// Put your front door, application gateway, APIM, b2clogin FQDN here and any other hosts that will send headers you want respected
options.AllowedHosts = new List() { “.azurewebsites.net”, “.b2clogin.com”, “.azure-api.net”};
});
}
}
}
That solves our problem. We can now see the “augmented claims”:
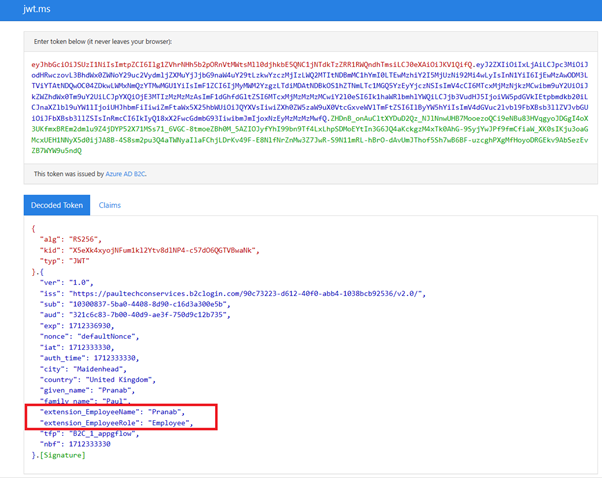
by Contributed | Apr 11, 2024 | Technology
This article is contributed. See the original author and article here.
We are excited to announce the general availability (GA) of Elastic Jobs for Azure SQL Databases.
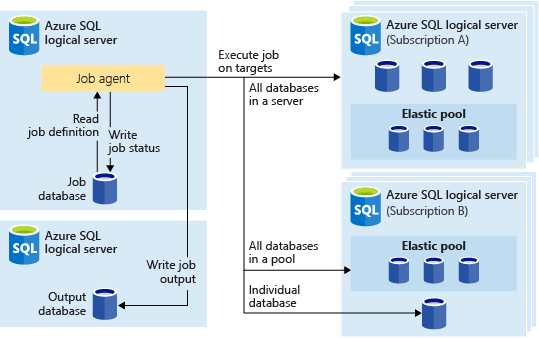
Elastic Jobs is a fully integrated Azure SQL database service that allows you to automate and manage administrative tasks across multiple SQL databases in a secure, scalable way. It can run one or more T-SQL job scripts in parallel using Azure portal, PowerShell, REST, or T-SQL APIs. Jobs can be run on a schedule or on-demand, targeting any tier of Azure SQL Database. Job target can include all databases in a server, in an elastic pool, across multiple servers and even databases across different subscriptions and geo regions on Azure. Servers and pools are dynamically enumerated at runtime, so jobs run against all databases that exist in the target group at the time of execution.

Where can you use Elastic Jobs?
Any database administration or management job that can be scripted with a T-SQL script is a good candidate for elastic jobs. Some of these example scenarios include:
- Automate management tasks like deploy schema changes, index rebuilding, performance/telemetry data collection etc.
- Configure jobs like query execution, collecting results across a collection of databases on a recurring basis.
- Aggregate and collect data for processing and reporting.
- Data movement, ETL processing to extract/process/insert data between tables in a database.
- .. to name a few.
What are some significant capabilities of Elastic Jobs?
Elastic Jobs makes it easy and secure to manage large number of SQL databases across Aure. Some significant security and management capabilities of Elastic Jobs include:
- Microsoft Entra ID (formerly Azure Active Directory) support for central administration of authentication and permissions
- Service-managed Private Link support to securely connect to target databases.
- Integration with Azure Alerts for job execution status notification.
- Easily scale Job Agent’s tier to connect to hundreds of target databases concurrently across Azure.
- Dynamic enumeration target databases in target servers and elastic pools
- Jobs can be composed of multiple steps to customize the execution sequence.
- All functionalities can be accessed through portal, PowerShell, T-SQL and REST APIs
How do you setup and use Elastic Jobs?
Setting up and using elastic jobs is simple as described here.
- Job Agent and Job database creation
Job Agent and associated Job database creation experience in portal is similar to a SQL database creation. As part of job agent creation, its service tier can be chosen, and a user assigned managed identity can be added for Entra authentication. Once the job agent is created, its portal page allows easy access to all its capabilities.
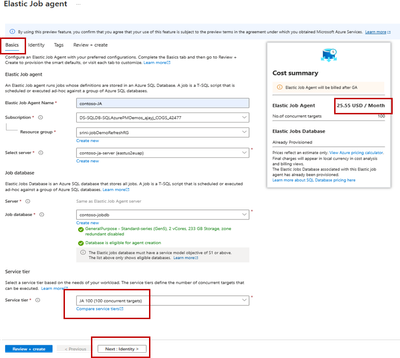
- Defining Jobs, their target groups and monitoring them through job agent’s portal page.
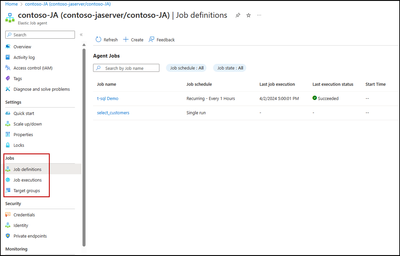
Jobs and job steps can be defined, edited and executed through portal page. These jobs can also be scheduled to run at regular intervals and their execution can be monitored.
- Advanced security functionalities, alert notification and scaling are also easily accessed through Job Agent’s portal page.
Job agents Entra ID can be changed and private links to target databases established easily through portal page. Azure Alerts can be defined for getting alert notification on job executions status. Scaling the job agent’s compute tier to enable it to connect to hundreds of target databases concurrently is also easy through portal page links.
Steps described above for creating, configuring, and managing elastic jobs also be accomplished through using PowerShell, REST and T-SQL APIs.
Pricing
Billing for Job agents will start at GA time, April 11th, 2024. Billing cards in the Azure portal page will show estimated cost based on the provisioned job agent tier.
*Billing for the job agents in national clouds are expected to start a little later, depending on the billing pipeline deployment in those regions.
Regional availability
The Elastic Jobs is available in all the regions that Azure SQL Database is available.
Resources
To get started, access the Elastic Database Jobs in our documentation and follow through with the tutorials.
Figure 1: What’s new is available from the top of the navigation pane in the Microsoft Entra admin center.
Figure 2: The highlights tab of what’s new is a quick overview of key product launches and impactful changes.
Figure 3: Click View details to learn more about an announcement.
Figure 4: The Roadmap tab lists the current public preview and recent general availability releases.
Figure 5: Learn more about an announcement by clicking its title.
Figure 6: Change announcements tab displays changes to the existing features.
Figure 7: Apply filters, sort by columns to create a customized view.


Recent Comments