by Contributed | Aug 30, 2022 | Technology
This article is contributed. See the original author and article here.
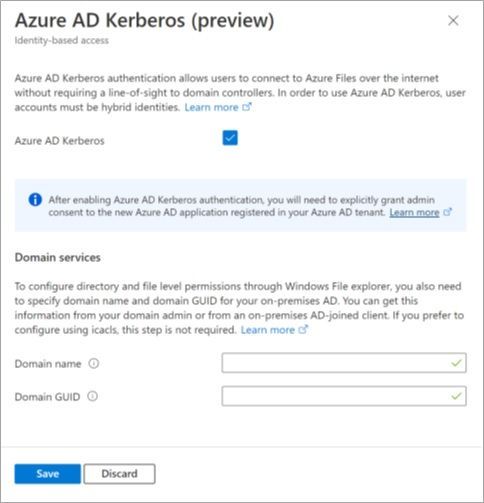
We are excited to announce Azure Files integration with Azure Active Directory (Azure AD) Kerberos for hybrid identities. With this release, identities in Azure AD can mount and access Azure file shares without the need for line-of-sight to an Active Directory domain controller.
Until now, Azure Files supported identity-based authentication over Server Message Block (SMB) through two types of Domain Services: on-premises Active Directory Domain Services (AD DS) and Azure Active Directory Domain Services (Azure AD DS). On-premises AD DS requires clients to have line-of-sight to the domain controller, while Azure AD DS requires deploying domain services onto Azure AD and domain joining to Azure AD DS. Azure AD Kerberos is a new addition to these identity-based authentication methods. Azure AD Kerberos allows Azure AD to issue Kerberos service tickets over HTTPS for service applications in Azure AD. This removes the need to setup and manage another domain service, while also removing the line-of-sight requirement to the domain controller when authenticating with Azure Files. For this experience, the clients connecting to Azure Files need to be Azure AD-joined clients (or hybrid Azure AD-joined), and the user identities must be hybrid identities, managed in Active Directory.
This experience builds on what we previously announced for FSLogix profiles support. Now, the experience is much simpler, and the use cases are no longer limited to Azure Virtual Desktop user profiles.

To learn more and get started, visit our documentation page.

by Contributed | Aug 29, 2022 | Technology
This article is contributed. See the original author and article here.
Microsoft partners like Audioburst, Fivetran, Skkynet, and YData Labs deliver transact-capable offers, which allow you to purchase directly from Azure Marketplace. Learn about these offers below:
 |
Audioburst – Audio Content Analysis: Audioburst’s enhanced content analysis tools extract actionable data points, enhance search and discovery, improve recommendations, and provide monetization opportunities using NLP and AI on Azure. |
 |
Fivetran Data Pipelines: Fivetran automatically ingests and centralizes your data from hundreds of data sources using over 180 data connectors. Fivetran data pipelines support a variety of data warehouses, including Microsoft Azure Synapse Analytics, Azure Blog Storage, Azure Databricks, and Snowflake.
|
 |
Skkynet DataHub: With the Skkynet DataHub, you can integrate live IoT processes using standard protocols, including OPC, MQTT, and Modbus, as well as connect SCADA systems, Azure Data Lake, and more for real-time OT/IT integration and remote data access.
|
 |
YData – Accelerate Development and Increase ROI of Your AI Solutions: YData helps data science teams collaborate, build great training data sets, and exponentially accelerate AI and ML projects while preserving security, privacy, and data fidelity without leaving Azure.
|

by Contributed | Aug 29, 2022 | Business, Microsoft 365, Technology
This article is contributed. See the original author and article here.
With Microsoft Teams Phone, we have been unabashed in our belief that the future of calling is built on VoIP calling that delivers rich voice and video experiences across organizational boundaries. Teams Phone VoIP calling capabilities are complemented by an enterprise-grade PSTN service that provides customers with the ultimate flexibility in how they communicate and collaborate.
The post Discover how Microsoft Teams Phone keeps 12 million PSTN users connected appeared first on Microsoft 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
by Contributed | Aug 26, 2022 | Technology
This article is contributed. See the original author and article here.
Introduction
Transport Layer Security (TLS) provides server authentication and channel defenses (encryption and integrity verification) for communication between two applications such as a web browser and a web server. Optionally, TLS can provide client authentication, too.
Most TLS connections today use X.509 certificates, and core to certificates are root Certificate Authority (CA) certificates. For a client to successfully establish a secure connection to a server using TLS, the client system must trust the CA that issued the server’s certificate. The word ‘trust’ in this scenario means the client has the CA’s root certificate installed in the client system.
Later this year, we will update the root CA certificates used by all Azure services, including the database services such as Azure SQL Database, Cosmos DB, Azure Database for PostgreSQL, and Azure Database for MySQL.
This root certificate change might have implications for you as an Azure database user.
What is Changing?
Azure is changing the set of root certificates used by Azure services. Right now, almost all Azure services use one root CA certificate for TLS:
- Baltimore CyberTrust Root
By the end of the calendar year 2022, Azure services will chain up to one of the following CAs:
- DigiCert Global Root G2
- DigiCert Global Root CA
- Baltimore CyberTrust Root
- D-TRUST Root Class 3 CA 2
- Microsoft RSA Root Certificate Authority 2017
- Microsoft ECC Root Certificate Authority 2017
What’s the Impact?
Most Azure database users will see no impact because the new set of root CA certificates are commonly installed on systems including mobile devices. Their client code will continue to make secure connections to back-end databases on Azure.
The potential issue is if developers design their code in a way that restricts which root CA certs are valid and trusted. This is called Certificate Pinning. You could have, for example, a dozen roots on a device, but your application only trusts one specific root. So, in your code, you explicitly check for that certificate when making a TLS connection. This is usually performed by checking the thumbprint of the certificate in your code.
At the time of its invention, pinning seemed like a good idea, but it has since fallen out of favor as it leads to fragility. You can read one point of view from DigiCert at Stop Certificate Pinning | DigiCert.com.
A more concrete example is if your code pins the Baltimore CyberTrust Root CA certificate, but Cosmos DB uses the DigiCert Global Root CA certificate, then the client will not connect to Cosmos DB. If your code is C/C++ Windows code, another way to mimic certificate pinning is to use Certificate Trust Lists (CTL).
You can learn more about the certificates we will use at Azure TLS Certificate Changes | Microsoft Docs and the Cosmos DB specific post is at Upcoming changes to Azure Cosmos DB TLS certificates – Azure Cosmos DB Blog.
What You Need to Do
Review all your code that interacts with Azure services, including our PaaS database products and make sure TLS connections do not limit which root CA certificates are valid. For Windows C/C++ code, make sure there is no use of CTLs.
Installing Root CA Certificates
You probably won’t need to add the new root CA certificates to your clients, but if you do, here is how to do it on Ubuntu Linux Installing a root CA certificate in the trust store | Ubuntu and how to use Global Policy on Windows to deploy certificates to your enterprise Distribute Certificates to Client Computers by Using Group Policy | Microsoft Docs or manually How to install Windows 10/11 root certificates. Some applications might have their own root CA store and not rely on the operating system, however.
SQL Server IaaS is not Affected
Note that SQL Server running in a Windows or Linux Virtual Machine is not affected by this change because you can configure any certificate and root used by the database server within the operating system. You cannot do this when using PaaS Azure databases because certificates are handled by Azure.
Summary
Most people will see no issues at all with this update. Just perform a little due diligence on your client-side code to make sure it is not restricting CA certs.
Thanks to Ashutosh Korde for his review of this post.

by Contributed | Aug 26, 2022 | Technology
This article is contributed. See the original author and article here.
This is the next segment of our blog series highlighting Microsoft Learn Student Ambassadors who achieved the Gold milestone and have recently graduated from university. Each blog in the series features a different student and highlights their accomplishments, their experience with the Student Ambassador community, and what they’re up to now.
Today we meet Arsalan Khattak who is from Pakistan and recently graduated from the National University of Modern Languages – Islamabad with a bachelor’s degree in computer science.

Responses have been edited for clarity and length.
When you joined the Student Ambassador community in 2019, did you have specific goals you wanted to reach, such as a particular skill or quality?
The goal I had in my mind was to be a part of a community, connect with like-minded people, and help others by sharing my knowledge. I wanted to make an impact through my blogs, videos, and sessions. As a Student Ambassador, I believe I achieved what was possible. In 2021 alone, I impacted around 1500+ people with just my live streams for the GitHub Education Twitch Channel.

Arsalan’s livestream set-up
I also helped many students learn how to code. Also, I used to be too shy to give a public speech or even walk in front of many people. I believed that being in a community would be a great way to overcome my fear and get out of my comfort zone, and it has been a success.
What were the accomplishments that you’re the proudest of and why?
As a Student Ambassador, one of my visible and prominent contributions was speaking at a Microsoft Reactor virtual event about Visual Studio Code, where I went through the VS Code structure and taught how to customize it according to your needs, including setting up themes, extensions, customizing title, etc.
I helped a couple of Alpha Ambassadors with their efforts to be promoted to Beta level. I helped them with how to give good presentations and gave them tips on how to engage and present to their audiences as well as some good resources to get technical information and knowledge.
I am the founding member of MLSA Islamabad, one of the leading communities in Pakistan. MLSA Islamabad hosted some very successful events, such as Digital Design Roadshow, and I secured partnerships with international communities and companies like Telenor.
What are you doing now that you’ve graduated?
Currently, I am employed at Major League Hacking working in their Fellowship Department as a Program Associate where I help students learn market-required skills and stay updated with technologies. My long-term goal is to make my community focused on web technologies.
If you could redo your time as a Student Ambassador, is there anything you would have done differently?
There isn’t much that I would have done differently, but one thing is that I would have spent more time on soft skills, that is, time management, project management, etc. I believe I spent quite a lot of time focusing on technical skills but didn’t give much attention to my soft skills which actually hold an equal amount of importance in one’s career as tech skills do.
If you were to describe the community to a student who is interested in joining, what would you say about it to convince him or her to join?
A community is a group of like-minded people that come together to solve a shared struggle and problem. The problem could be something technical like helping juniors to level up their skills, or completely nontechnical helping kids to learn skating. Being in a community helps you grow and learn faster as you have like-minded people to help you solve problems, and you can also do a lot of networking and expand your connections. For example, when you join the Students Ambassador community, you get access to thousands of other Ambassadors all around the globe who have expertise in different domains.
What advice would you give to new Student Ambassadors?
My only advice to them is to get the most out of the community and network as much as possible. I have noticed some folks focusing just on the swags, which should not be the motivation to join a community. Everyone loves swag, including me, but treat it as an extra perk. The motivation should be expanding your network and connecting with industry experts and like-minded people.
What is your motto in life, your guiding principle?
My motto is to learn, build and open source. I help others learn technologies to build things with them and open source them. I do this by creating video content on my YouTube and Instagram accounts.

Planning content for a YouTube Video
What is one random fact about you that few people are aware of?
I can wiggle my ears.
Good luck to you in all your endeavors, Arsalan!
Readers, you can find Arsalan on YouTube, LinkedIn, and Twitter.


Recent Comments