
by Contributed | Oct 12, 2022 | Business, Hybrid Work, Ignite, Microsoft 365, Technology, Work Trend Index
This article is contributed. See the original author and article here.
Empowering today’s digitally connected, distributed workforce requires the right culture and the right technology. At Microsoft Ignite, we’re sharing new innovations across Microsoft 365, Microsoft Teams, and Microsoft Viva to help everyone thrive.
The post Microsoft 365 at Ignite—Re-energize your workforce in the office, at home, and everywhere in between appeared first on Microsoft 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.

by Contributed | Oct 12, 2022 | Business, Microsoft 365, Technology
This article is contributed. See the original author and article here.
Today at Microsoft Ignite, we’re proud to launch Microsoft Syntex. Microsoft Syntex is Content AI integrated in the flow of work. It puts people at the center, with content seamlessly integrated into collaboration and workflows, turning content from a cost into an advantage.
The post Welcome to Microsoft Syntex—Content AI integrated in the flow of work appeared first on Microsoft 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.

by Contributed | Oct 12, 2022 | Business, Hybrid Work, Microsoft 365, Technology
This article is contributed. See the original author and article here.
I’m thrilled to announce new consumer tools in Microsoft 365, Microsoft Edge, and Bing designed to help all of us ignite our imagination and express ourselves. Everything begins with an idea but getting started and capturing your individuality isn’t always easy. For anyone who is trying to create, we aimed to solve a few key challenges with creating and sharing content.
The post New tools from Microsoft 365, Edge, and Bing bridge the gap between productivity and creativity appeared first on Microsoft 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
by Contributed | Oct 11, 2022 | Technology
This article is contributed. See the original author and article here.
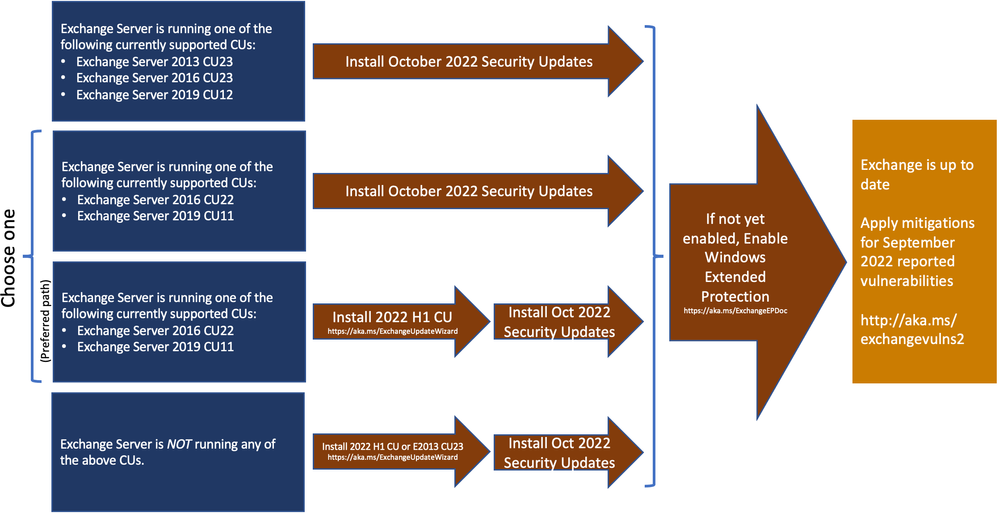
Microsoft has released Security Updates (SUs) for vulnerabilities found in:
- Exchange Server 2013
- Exchange Server 2016
- Exchange Server 2019
SUs are available in a self-extracting auto-elevating .exe package, as well as the original update packages (.msp files), which can be downloaded from the Microsoft Update Catalog.
The October 2022 SUs are available for the following specific versions of Exchange Server:
The SUs address vulnerabilities responsibly reported to Microsoft by security partners and found through Microsoft’s internal processes. Our recommendation is to immediately install these updates to protect your environment.
These vulnerabilities affect Exchange Server. Exchange Online customers are already protected from the vulnerabilities addressed in these SUs and do not need to take any action other than updating any Exchange servers in their environment.
NOTE The October 2022 SUs do not contain fixes for the zero-day vulnerabilities reported publicly on September 29, 2022 (CVE-2022-41040 and CVE-2022-41082). Please see this blog post to apply mitigations for those vulnerabilities. We will release updates for CVE-2022-41040 and CVE-2022-41082 when they are ready.
Also note that we have re-released some CVEs published in August 2022, to highlight the resolution of known issue. More details about specific CVEs can be found in the Security Update Guide (filter on Exchange Server under Product Family).
Enable Windows Extended Protection
Starting with the August 2022 SUs, Exchange Server supports the Windows Extended Protection (EP) feature, which can help you protect your environments from authentication relay or “man in the middle” (MitM) attacks. If you have not yet enabled EP in your environment, please install the October SUs which address a known issue in Exchange EP support (see below). Then, review the information in the Manual Enablement of Extended Protection section of our August announcement for more details.
Customers who have already installed the August 2022 SUs and have enabled EP do not need to re-run the EP script after installing the October SUs.
Update installation
The following update paths are available:

Known issues with this release
We are not aware of any known issues with this release.
Issues resolved by this release
- In Exchange 2013, Exchange 2016, and Exchange 2019 various Outlook and compliance-related monitoring probes show as Failed once EP is enabled.
FAQs
My organization is in Hybrid mode with Exchange Online. Do I need to do anything?
Exchange Online is already protected, but the October 2022 SUs need to be installed on your Exchange servers, even if they are used only for management purposes. You do not need to re-run the Hybrid Configuration Wizard after installing these updates.
Do I need to install the updates on ‘Exchange Management Tools only’ workstations?
Servers and workstations running only the Management tools role (no Exchange services) do not need these updates.
This post might receive future updates; they will be listed here (if available).
The Exchange Server Team
by Contributed | Oct 10, 2022 | Technology
This article is contributed. See the original author and article here.
During Cybersecurity Awareness Month, it’s important to focus not only on the dangers of data breaches but also on how to build with products like Microsoft Power Platform and Dataverse—products that are designed to help keep your organization’s data protected. Use the resources on Microsoft Learn to explore ways to support security in your organization, whether you’re a traditional solution architect, a business user, or an IT pro. April Dunnam, Power Platform Cloud Advocate, notes that anyone building a low-code solution should have a security-first mindset. She explains, “Your solution will be better designed, and then it’s going to be long-standing.”
Dataverse and Microsoft Power Platform—better together
Dataverse is a critical and foundational component of Microsoft Power Platform. It’s what the platform runs on, and it’s secure by design. You can configure many layers of security in Dataverse. As April points out, “You can use the [Microsoft Power Platform] admin center to define different data loss prevention policies to determine which connectors you can and can’t use, all the way down to a really granular level.” She recommends checking out the new managed environments that apply to both Microsoft Power Platform and Dataverse, which make it easier to manage some of the out-of-the box security features. For every solution, you can configure additional security capabilities. For more information, go to the Microsoft Learn module Create and manage environments in Dataverse.
As part of your cybersecurity strategy, April also recommends setting up a Center of Excellence and using the toolkit, because, as she observes, “[It] augments the capabilities of Microsoft Power Platform and fosters an internal community who can think ahead and put together best practices to enable secure low-code solutions.” To learn more, explore the Microsoft Learn module Get started with Microsoft Power Platform Center of Excellence.
April is all for using Microsoft Power Platform tools “right out of the box” for building security solutions. She observes, “These intuitive, user-friendly tools guide us through making sure that the applications and solutions we build are secure. So, with just a little bit of work and a little bit of reading some of the Microsoft Learn material to get a good understanding, you’re ready to come up to speed on making sure that the solutions that you build are secure.” For details, check out the Microsoft Learn module Introduction to Microsoft Power Platform security and governance.
Use a collection to discover more security content
April encourages the use of Microsoft Learn resources, saying, “Learning paths and modules are so helpful for getting a basic understanding of security to help you set your department up for success. Later, you can transition to more advanced content as you strategize for your organization in a role like solution architect.” April recommends the Cybersecurity Awareness – Microsoft Power Platform collection, which offers a basic understanding of Dataverse security capabilities. Plus, it explores fundamental Microsoft Power Platform security concepts.
Earn a Microsoft Certification
People who follow April know that she’s a passionate Microsoft Power Platform advocate with many certifications. She observes, “People are always asking me, ‘What should I do next on my path?’” April has a couple of recommendations for validating your skills by earning an industry-recognized Microsoft Certification. She says, “If you’re building some secure applications for your team, then look into earning a Microsoft Certified: Power Platform Functional Consultant Associate certification. [Pass Exam PL-200.] If you’re at a senior level, doing things like deploying scalable applications and managing security across the environment for an organization, then explore earning a Microsoft Certified: Power Platform Solution Architect Expert certification. [Pass Exam-PL-600 and a prerequisite.]”
Keep learning with April Dunnam
Now that you’ve gotten some key tips on how to handle security issues, it’s time to dive deep into Microsoft Power Platform and Dataverse on April Dunnam’s YouTube channel. Watch for her upcoming video “Why SharePoint Experts are using Dataverse”, and be sure to check out her show—The Low Code Revolution—to build apps efficiently and expand your skill set.


Recent Comments