
by Contributed | May 1, 2023 | Technology
This article is contributed. See the original author and article here.
By Marina Khidekel, Chief Content Officer at Thrive Global
Throughout our time spent at home during the pandemic, many of us picked up new rituals and habits that helped us stay positive, grounded, and optimistic. We learned new skills, revisited childhood passions, and started incorporating little activities that became staples in our everyday routines. In fact, many of them are continuing to boost our happiness and well-being.
We asked our Thrive community to share with us the pandemic habits and rituals that are now staples in their routines. Which of these will you implement into your routine?
Five-minute journaling
“I have tried journaling in the past and it never stuck, mainly because I do not consider myself a writer and would judge myself for journaling what I classified as ‘mundane thoughts.’ The five-minute journal was such a nice shift from traditional journaling. It’s quick and easy, allowing me to set an intention for the day with some added reflection at night.”
—Julie Bronsteatter, personal and executive coach, Chicago, IL
Taking evening walks
“During the pandemic, my husband and I took our dog on long walks in the evening. It was a relief to get out of the house and feel the sunshine on our faces. It created space for us to talk to each other about what was happening and how we felt. We found that we took more time to notice the sunset in the evening, sometimes having a cocktail on the patio while watching the world go by. In the chaos of what was happening, it gave us time to ground ourselves individually and as a couple. We still take our evening walks and remember to focus on the positive, staying grounded in who we are and the decisions that we make.”
—Anne McAuley Lopez, content writer, Chandler, AZ
Baking bread from scratch
“I learned to bake bread from scratch during the pandemic. While I love to cook, baking bread always terrified me. It seemed like too daunting a challenge. I decided to face my fear and give it a whirl. While it is not something I do daily, it is definitely still something that I do very regularly. I find that the process is meditative, and the smell of fresh baked bread is such a reward for the work that goes into it!”
—Cindy J., executive search and human resources consultant, Boston, MA
Replacing phone calls with video
“I used to stay in touch with distant relatives and friends via phone calls, texts, and emails, but now that I have the rhythm and the technology in place, I enjoy turning on the video function to connect. It’s added a great dimension to our conversations and the ‘getting ready’ bit is now a nice part of the process. Even the older generation has come on board and enjoys the video calls!”
—Marta Rzeszowska Chavent, management and change consultant, France
Home cooking
“During the lockdowns, I planned and prepared most of my meals, and cooking was therapeutic. I would play an audiobook whilst cooking and was finally able to read two books a month. Another bonus: It was easier to practice intermittent fasting where I’d eat at 2:00 p.m. and stop before 7:00 p.m. This routine gave me structure and saved so much time. Now that we can go out, I still do this at least five days a week, as it makes me feel calm, disciplined, and enriched.”
—Georgina Chang, communication coach and mentor, Singapore
Setting intentions
“One new technique that I picked up during the pandemic that continues to be a positive change for me is setting intentions for every part of my day. This technique is called Segment Intending. I divide the day into three segments, such as personal, work, and family. Each segment has two things that I want or need to accomplish for that day. The intentions I set are always positive. That way, even if some unforeseen and unpleasant circumstances happen, I still train my mind to see the positive in that moment of interaction. It also helps divide your day into manageable segments.”
—Armida Markarova, leadership development and employee engagement, Chicago, IL
Doing at-home workouts
“Since I could not go to my regular gym during the pandemic, I bought an elliptical to be able to do a bit of exercise indoors in winter, as I struggle with seasonal affective disorder. I am a big fan of electronic dance music, so to start off my day in a better mood, I use the elliptical for twenty minutes and I play videos of recorded EDM sets, which I think helped with my endorphins and mentally reminded me of an activity that I would soon get to do again. I still do this on days where I don’t go to the gym!”
—Duane Taylor, technical account manager, Washington, D.C.
Spending time outside
“During the pandemic, I increased my outdoor exercise routine — rain, snow, or shine. I began walking on empty country roads for 90 minutes every day. While some days the snow was in my face, I found it invigorating. I just had to walk and my body did the rest. The ritual encompassed simplicity and serenity at the same time. This improved my mood and it’s still a staple in my routine.”
—Cathy Connally, managing partner, Toronto, ON, Canada
Daily free writing
“Every evening, I set a timer and free-write for three minutes. I write anything that needs to come out of my mind and onto the page. It’s been eye-opening, recording the gratitude, the small wins, the creative ideas, and the connection parts of the day that normally I’d overlook or not make the time and space to see. I force myself to write for three minutes and typically the goodness comes out in the last 30 seconds!”
—Lisa Pezik, business strategist and content expert, Ontario, Canada
Checking in with loved ones
“I missed my family and friends, but we have found ways to reassure each other of our love. I stay connected with them through video chats, phone calls, and text messages. I reach out to friends when I am having a bad day, and regularly check in to see how they are doing.”
—Sara Leandro, health coach, Berlin
For more actionable tips and inspiration on strengthening resilience and improving well-being at work and beyond, visit ThriveGlobal.com

Marina Khidekel, Chief Content Officer at Thrive Global
Marina leads strategy, ideation and execution of Thrive Global content company-wide, including cross-platform brand partnership campaigns, editorial tentpoles and partnerships, and the voice of the Thrive app. In her role, she helps people tell their personal stories of going from surviving to thriving, brings Thrive’s audience actionable, science-backed tips for reducing stress and improving their physical and mental well-being, and shares those insights on panels, at conferences, and in national outlets like NBC’s TODAY. Previously, Marina held senior editorial roles at Women’s Health, Cosmopolitan, and Glamour, where she edited award-winning health and mental health features and spearheaded the campaigns and partnerships around them.
|
by Contributed | Apr 29, 2023 | Technology
This article is contributed. See the original author and article here.

This session is part of Build AI Powered Solutions with Azure OpenAI Service series, learn more and register for the events here: Build AI powered apps with Azure OpenAI Service. Make sure to complete the Cloud Skills Challenge we have for this series: https://aka.ms/AI-Powered-Content-Manager-Challenge
Our Use case Project – Content Manager Mobile App (Register Here)
What is this session about?
When the marketing submits the content, they want to use as part of the marketing strategy they are normally using a traditional system of sending emails back and forth with documents of the content. We want to automate this process to make it easier for the Marketing Manager to have a summary of the content, the original content and review it to either approve/reject the content that will be posted on the company’s social media accounts.
Who is it aimed at?
This session is aimed at anyone who wants to learn how to build AI powered apps and wants to learn more about Azure OpenAI
Solution Considerations before development
Before you build an application, you should have some thought and break down what you want to do before building. This process is often called “Solution Architecting“. While we will not be taking a lot of time doing this, I would like to introduce you to the basics of it.
Watch On Demand – Coming Soon
Speakers:
Hadeel Shubair
Hadeel is a Regional Cloud Advocate and Data Analytics Engineer for Microsoft, Middle East/Africa region. She holds a Master’s degree in Data Analytics and is passionate about learning and sharing her knowledge on tech topics including Data Analytics, AI, & ML. Before joining Microsoft, Hadeel held several appointments and roles including Google Women in Tech scholar through which she delivered several sessions to the community to motivate and empower young talents. Hadeel also served as part of the Data & Communications team overlooking the organization of the World Government Summit. On the other side, while at University, Hadeel chaired the Women in Engineering club, and was the Chief Editor of the Engineering Newsletter. As a Cloud Advocate for the Microsoft Reactor, Hadeel’s main goal is to take you on a journey to understand & learn more about Data and AI concepts and applications. She’s passionate about technology, education, & growing the Data & AI community across the region.
Someleze Diko
Someleze is a young individual that is passionate about upskilling people from different communities using the different technologies at his disposal through being involved with initiatives that upskill and empower people. Today, he is an M365 and Power Platform Cloud Advocate at Microsoft focusing on upskilling students and communities through the Microsoft Power Platform. Before becoming a Cloud Advocate, Someleze was a Gold Microsoft Learn Student Ambassador in which he worked closely with other ambassadors to learn, upskill and empower students in different communities through hosting sessions that cover different Microsoft Technologies. He also served as a United Nations Peace Ambassador alongside his team from Artpeace.
by Contributed | Apr 29, 2023 | Technology
This article is contributed. See the original author and article here.
As you may have heard; Windows LAPS feature is released to Public Preview in the last week of April. It has support for two main scenarios for backing up local administrator password such as storing passwords in Azure AD and Windows Server AD. It also has interoperability with legacy LAPS solution. This article on the other hand; will focus on native cloud deployment for Windows 10/11 clients that does not have legacy LAPS client installed, managed through Intune and either Hybrid Azure AD Joined or Azure AD Joined.
In this blog post, I’ll walk you through basic policy configuration and core Windows LAPS functionalities such as accessing local administrator passwords from different consoles and manually triggering password rotation.
Pre-requisites for enabling Windows LAPS may change in the future, so it is always a good idea to check online documentation first; but the tasks we will cover in this post are as follows:
- Enabling local administrator password feature on tenant level
- Creating a Windows LAPS Policy
- Monitoring policy application
- Accessing local administrator passwords that are backed up
- Rotating local administrator passwords manually
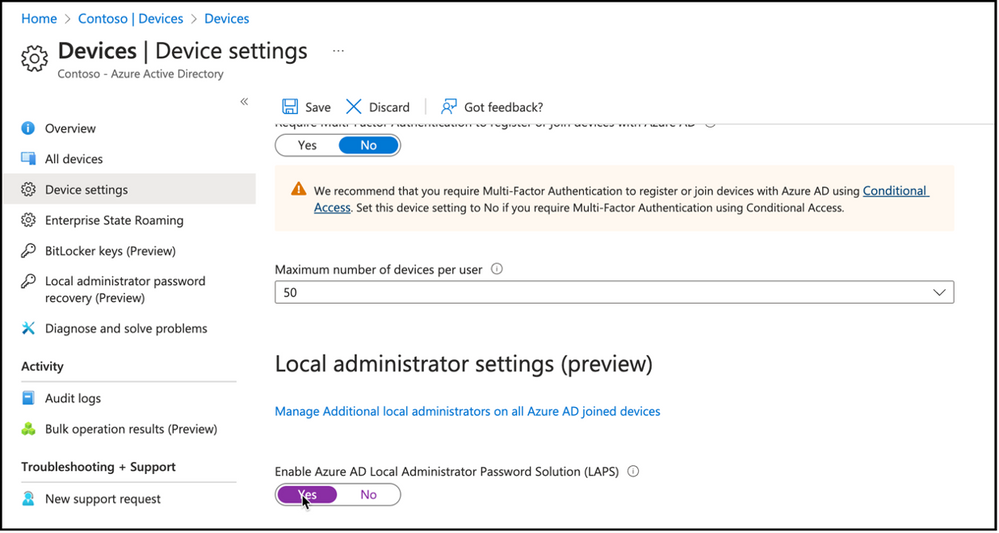
Enable Azure AD Local Administrator Password Feature
Enabling Local administrator password settings in tenant level can be done in Azure AD portal, Devices node, Device settings view. Option to enable Azure AD Local Administrator Password Solution (LAPS) will be available for configuration.
 Snippet from Azure Active Directory Devices Node, Device Settings View
Snippet from Azure Active Directory Devices Node, Device Settings View
After enabling feature on the tenant level, we can proceed with policy creation.
Creating Local Admin Password Policy
Local Admin Password Solution policies can be configured from Endpoint Security Node, Account Protection view. Clicking on “Create Policy” button will present policy creation wizard.
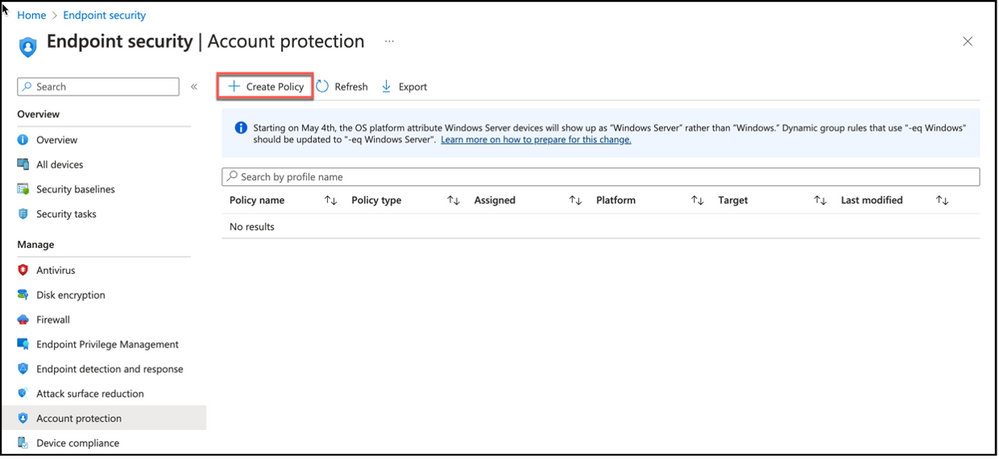 Snippet from Endpoint Security, Account Protection View
Snippet from Endpoint Security, Account Protection View
First option will be selecting platform for the policy, and the second option will be policy type itself. As you notice, there are different account protection policy options such as Local User Group Membership or Account Protection as well as Local Admin Password Solution (Windows LAPS). Selecting Local admin password solution (Windows LAPS) from profile list will start policy creation wizard.
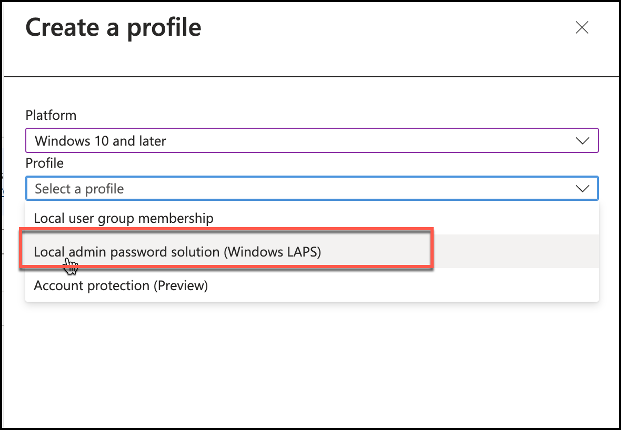 Snippet from Endpoint Security, Account Protection Node, Policy Creation View
Snippet from Endpoint Security, Account Protection Node, Policy Creation View
As always, first step is naming policy as well as giving a description.
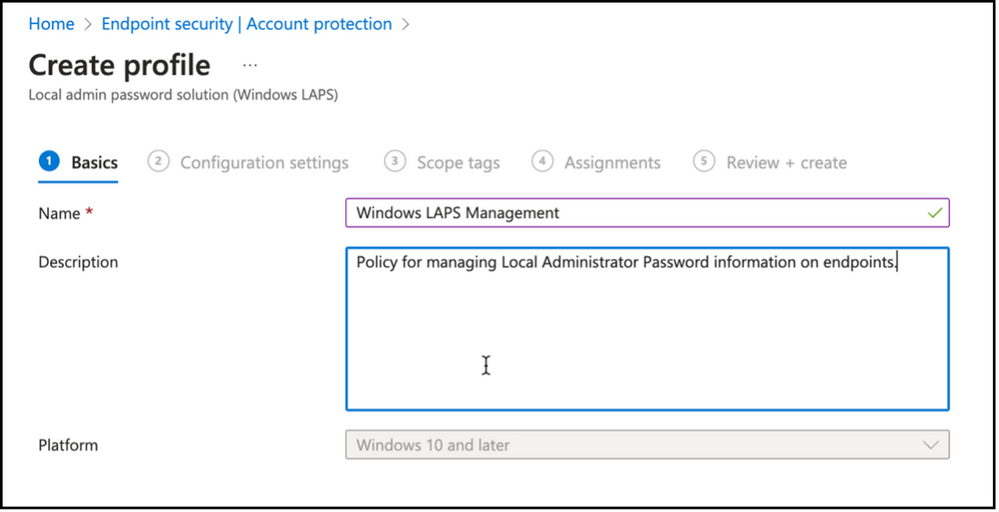 Snippet from Policy Creation – Naming Account Protection Policy
Snippet from Policy Creation – Naming Account Protection Policy
Next step is building the policy itself. As you see there are several options regarding Administrator account, password options as well as the directory to backup the local administrator password. Let’s take a deeper look at these options and prepare our Windows LAPS policy.
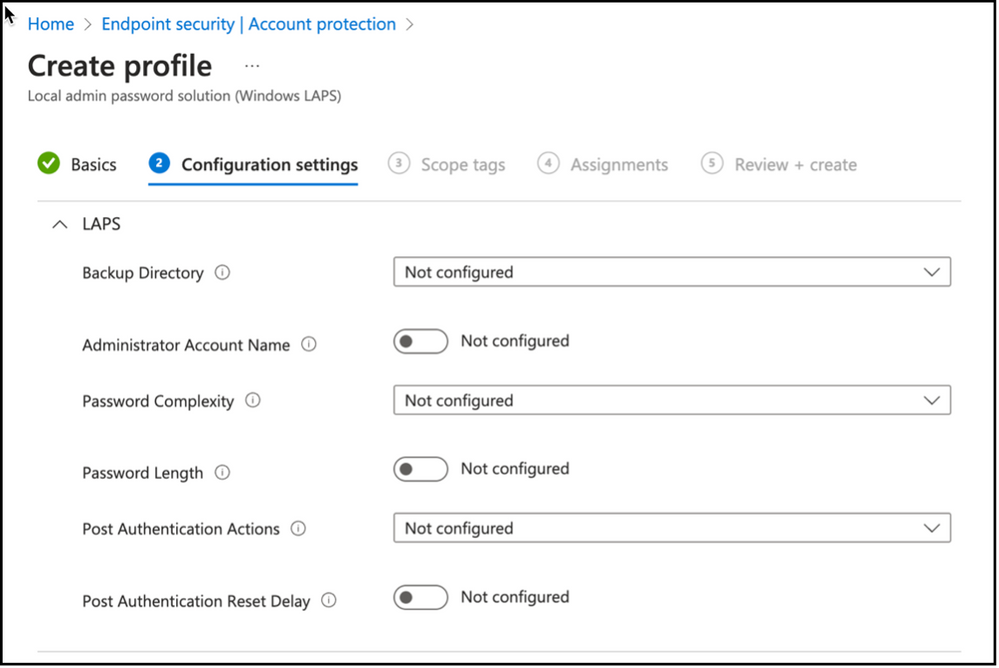 Snippet from Policy Creation, Configuration Settings View
Snippet from Policy Creation, Configuration Settings View
Backup Directory:
First setting in creating Windows LAPS policy is defining the directory service that will be used to backup the local admin password on the endpoints. It is possible to use Windows Server Active Directory or Azure Active Directory as a means to store local admin passwords. You can also use “Disabled” option to remove existing configuration.
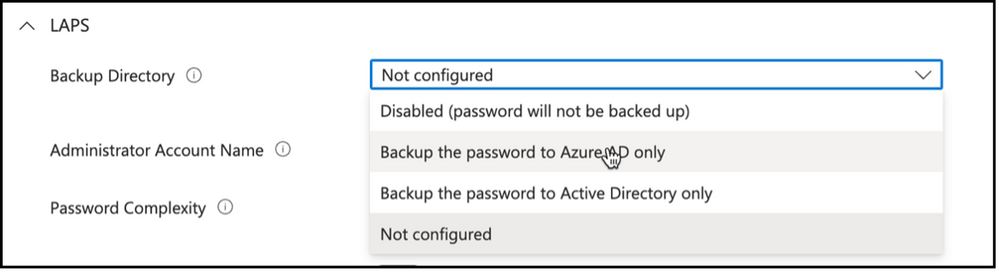 Snippet from Policy Creation, Backup Directory Options
Snippet from Policy Creation, Backup Directory Options
There will be additional settings depending on the backup directory selected. Some of these will include Active Directory specific settings such as “AD Encrypted Password History Size”, “AD Password Encryption Principal” and “AD Password Encryption Enabled” if backup to Active Directory is selected.
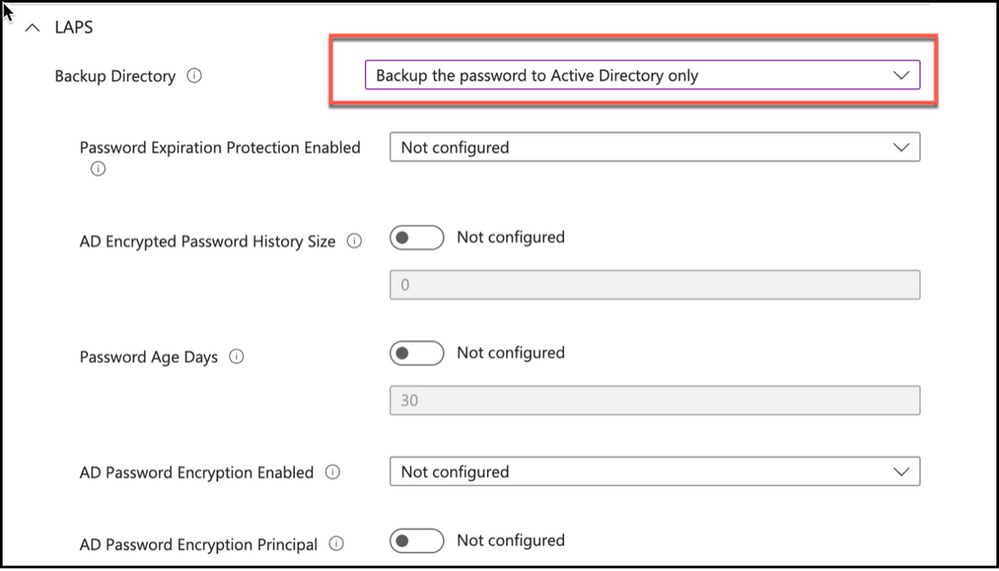 Snippet from Policy Creation, Backup Directory Setting – Active Directory only
Snippet from Policy Creation, Backup Directory Setting – Active Directory only
Only additional setting to configure will be Password Age Days when Azure AD selected as the directory service for backing up the local administrator password. Password Age Days option defaults to 30 days unless it is configured and it is possible to configure this option between 7 days & 365 days while backing up to Azure AD, and 1 day & 365 days while backing up to Active Directory.
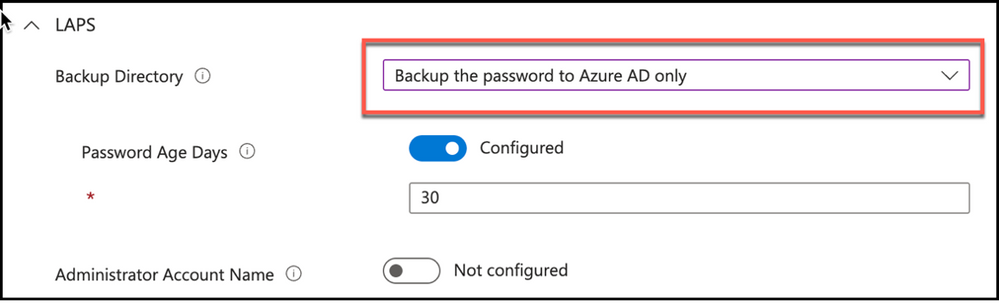 Snippet from Policy Creation, Backup Directory Setting – Azure AD
Snippet from Policy Creation, Backup Directory Setting – Azure AD
Administrator Account Name: Another setting to configure is the Administrator account name to manage. Policy will use Built-In Administrator SID if not configured. Renaming built-in administrator account will not impact SID monitoring, so you can configure this option to define, if there is another local administrator account present on the endpoint to manage its password.
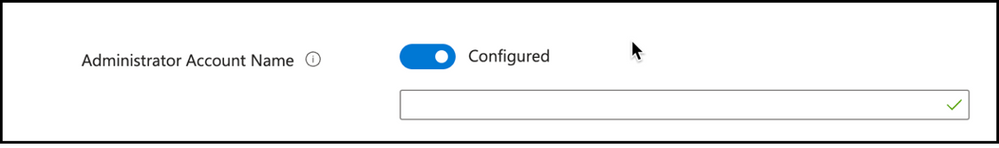 Snippet from Policy Creation, Administrator Account Name Setting
Snippet from Policy Creation, Administrator Account Name Setting
Password Complexity: Next setting that will require our attention will be Password Complexity. This is where we define how complex local administrator passwords will be on the endpoints. As you can see there are different options to use Large letters, small letters, numbers and special characters in the local administrator password.
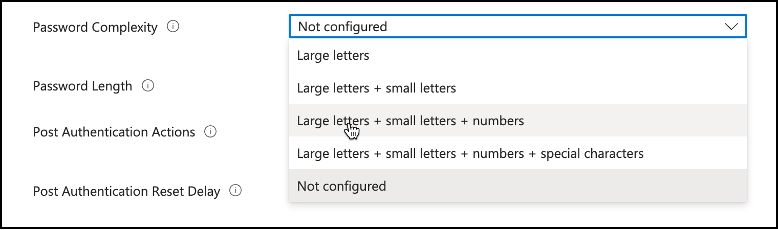 Snippet from Policy Creation, Password Complexity Options
Snippet from Policy Creation, Password Complexity Options
Password Length: Another important item to configure is the password length setting which will define the length of local administrator password created based on the complexity requirements defined earlier. It defaults to 14 characters unless defined, and has a minimum of 8 and maximum of 64 character limitation.
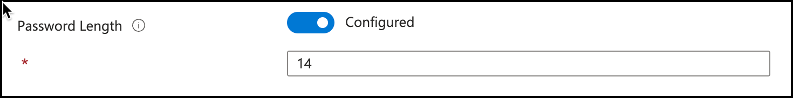 Snippet from Policy Creation, Password Length Setting
Snippet from Policy Creation, Password Length Setting
Post Authentication Actions: Post Authentication Actions will define what will happen to the password, user or device after logging on with the stored local admin credentials. Password will be reset at a minimum, managed account will be logged off or device will be rebooted after the expiry of grace period to make sure password rotation took place. Fort his configuration I will define my policy to reset the password and logoff the managed account upon expiry of the grace period.
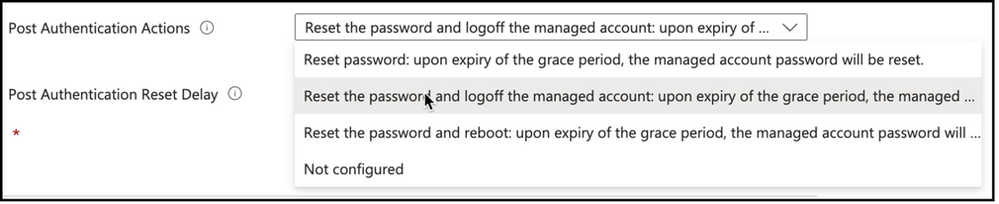 Snippet from Policy Creation, Post Authentication Actions Setting
Snippet from Policy Creation, Post Authentication Actions Setting
Post Authentication Reset Delay: Post authentication reset delay value will define the time in hours to execute the actions following authenticating with the managed identity as defined earlier. This setting defaults to 24 hours if not configured; and can be set between 0 (disables post authentication actions) and 24 hours.
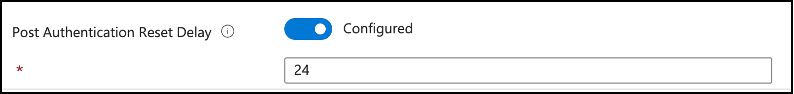 Snippet from Policy Creation, Post Authentication Reset Delay Settings
Snippet from Policy Creation, Post Authentication Reset Delay Settings
Just like all the other device configurations that can be deployed by intune, next step in the policy wizard would be assigning a set of devices for policy application. In my environment i’ve used built in All devices group.
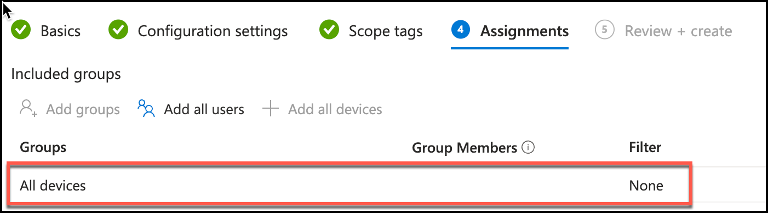 Snippet from Policy Creation, Group Assignment
Snippet from Policy Creation, Group Assignment
Monitoring Policy Application
It is possible to monitor Windows LAPS policy application via Intune just like any other policy. One way would be pivoting from policy itself. It is possible to view check-in status per logged on user in the policy details.
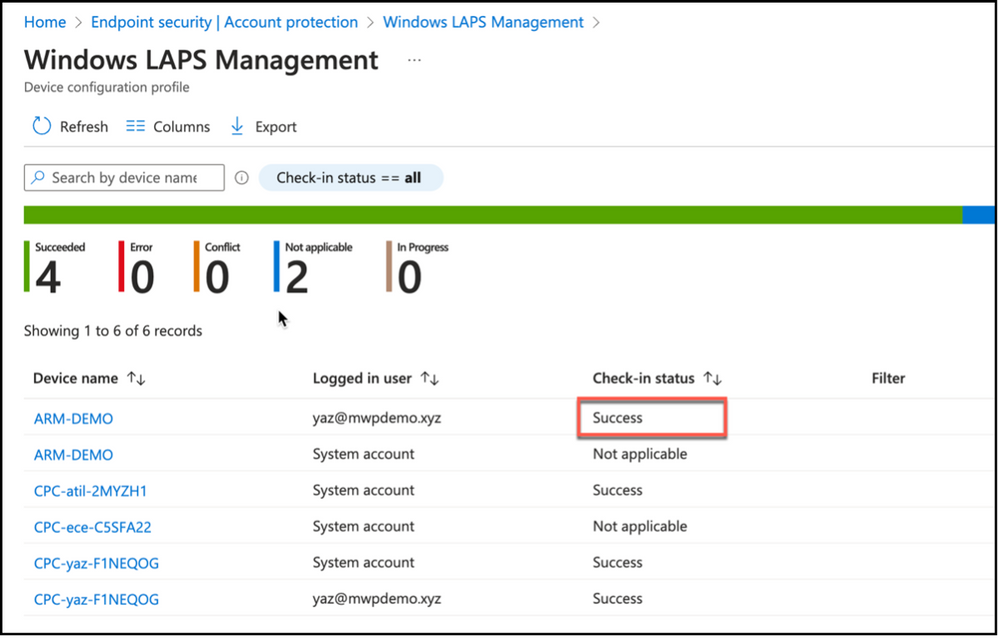 Snippet from Windows LAPS Policy Properties, Check-In Status
Snippet from Windows LAPS Policy Properties, Check-In Status
It is also possible to pivot from a device; checking device configuration view from device properties and validating the policy application to the endpoint.
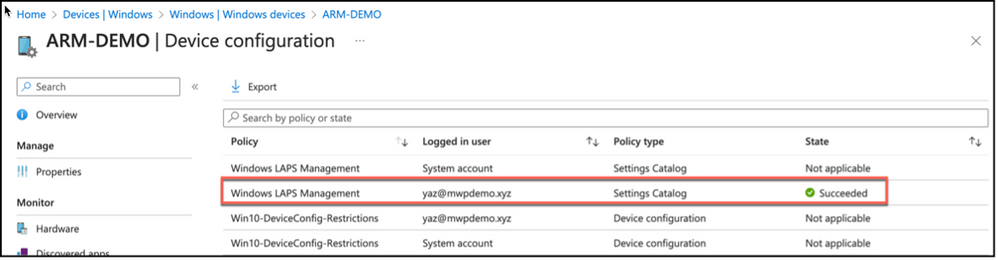 Snippet from Device Properties, Device Configuration View
Snippet from Device Properties, Device Configuration View
When drilled through the device configuration applied, we can see per-setting level status as well. You may see the settings are successfully applied to our device in the following snippet.
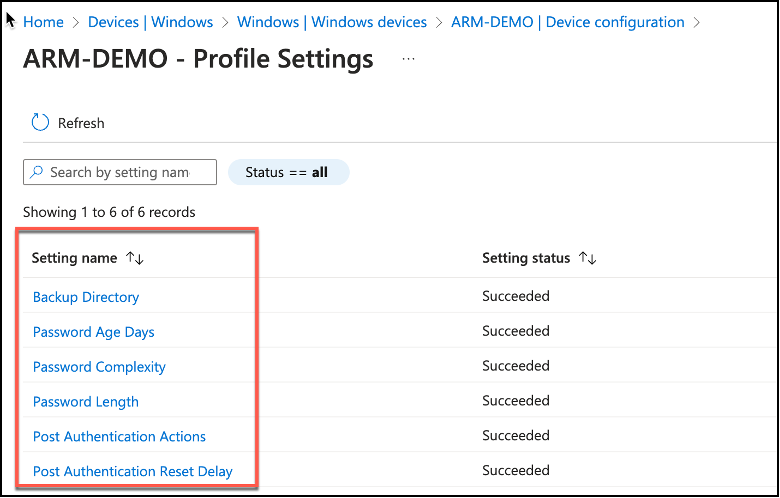 Snippet from Device Configuration, Profile Settings View
Snippet from Device Configuration, Profile Settings View
Accessing Local Admin Passwords
Once the policy is applied on the endpoint, Windows LAPS will create a random local administrator password for the managed credential in the endpoint and will store this as an attribute that is accessible through either Azure AD, or Microsoft Intune. On the other hand, there are some requirements for accessing the local admin password.
Someone who needs to view local admin passwords should be granted with the following rights in Azure AD as stated in the RBAC document here.
- microsoft.directory/deviceLocalCredentials/password/read
- microsoft.directory/deviceLocalCredentials/standard/read
An admin / operator user who has correct rights / roles assigned, can access to the local admin password recovery view either following Azure Local administrator password recovery view within Devices Node, ins Azure Active Directory console, or they can use “local admin password” view inside device properties within Microsoft Intune.
For Azure Active Directory, admin / operator can drill on the properties of the endpoint that its local administrator password is looked for; click on Local administrator password recovery link from the left hand side menu. This will bring information about the local administrator password such as when the last password rotation was and when the next password rotation will be, as well as an option to Show local administrator password.
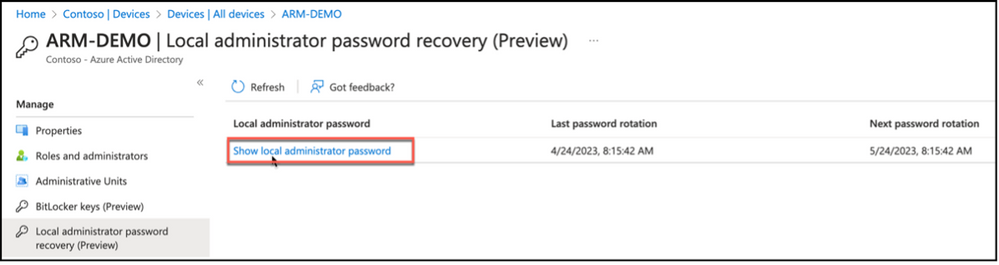 Snippet from Azure Active Directory, Device Properties, Local Administrator Password Recovery View
Snippet from Azure Active Directory, Device Properties, Local Administrator Password Recovery View
When clicked on Show local administrator password task, a window will pop-up from the right side of the screen and will Show details about the managed identity such as Account name, SID information, password rotation details as well as local admin password hidden in asterisk with a “Show” button.
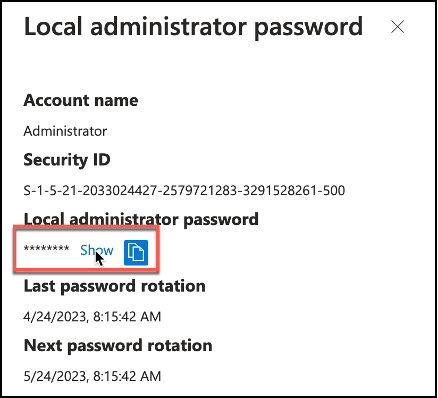 Snippet from Azure Active Directory, Local Administrator Password Retrieval
Snippet from Azure Active Directory, Local Administrator Password Retrieval
Clicking on Show button will reveal the current local administrator password for the endpoint. Admin / Operator user can then use Copy button to copy the local administrator password to clipboard and use it to do the tasks that require administrator privileges.
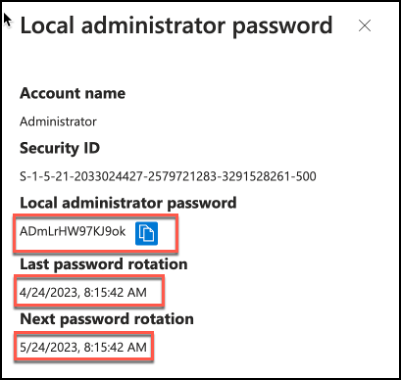 Snippet from Azure Active Directory, Local Administrator Password Retrieval
Snippet from Azure Active Directory, Local Administrator Password Retrieval
Once the password is used to authentication to the target system, actions defined in post authentication actions policy setting will be executed after a time period defined in post authentication actions delay policy setting. These actions may include rotating password, logging off the managed identity or rebooting the device.
It is also possible to manually trigger local administrator password rotation. Task for Windows LAPS password rotation can be found in the actions menu item for the given endpoint.
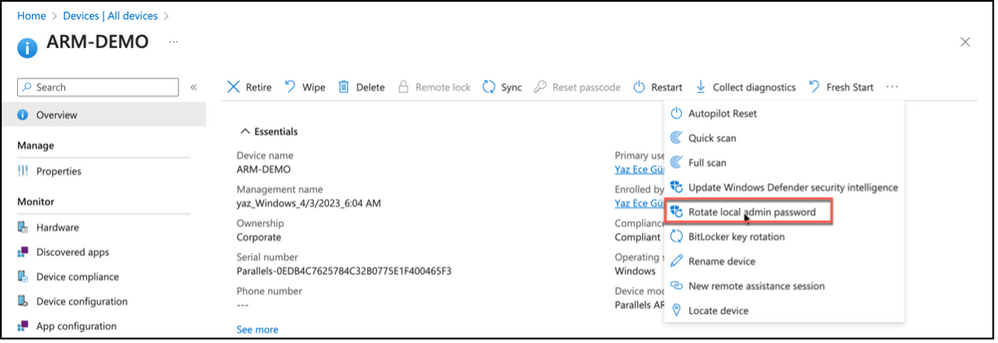 Snippet from Microsoft Intune Device Properties, Rotate Local Administrator Password Task
Snippet from Microsoft Intune Device Properties, Rotate Local Administrator Password Task
Once clicked, admin / operator user will get a confirmation message stating that old password will no longer be applicable and a new password will be generated after rebooting the device.
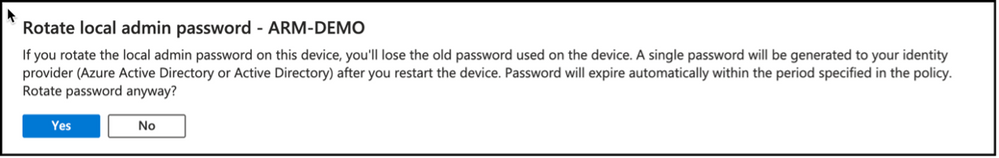 Snippet from Microsoft Intune, Local Administrator Password Rotation Confirmation
Snippet from Microsoft Intune, Local Administrator Password Rotation Confirmation
It is also possible to access local administrator password via Microsoft Intune device properties. Let’s check how and confirm that password for local administrator has changed with rotate local admin password task.
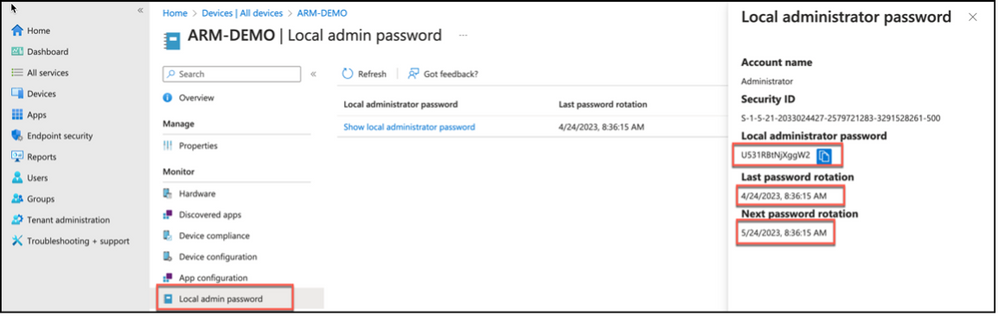 Snippet from Microsoft Intune, Local Administrator Password Rotation
Snippet from Microsoft Intune, Local Administrator Password Rotation
Device properties for a given device has an option for Local admin password. Which has the information about last rotation time for local administrator password, next rotation time for local administration password as well as Show local administrator password task just like the one in Azure Active Directory. Clicking on Show local administrator password task will reveal a similar pop-up from right hand side, that is usable to copy the existing local administrator password for the device.
Wrap Up:
Windows LAPS feature is released to Public Preview while this post is written. It has native support for cloud scenarios such as Hybrid Azure AD Joined devices and Azure AD Joined devices as well as interoperability with legacy LAPS solution. Customers may use Intune to create and deploy Windows LAPS policies and may utilize Azure AD or Microsoft Intune portals to view local administrator password for a given device. It is also possible to utilize Graph API to do certain tasks which can be a subject of another post.
by Contributed | Apr 28, 2023 | Technology
This article is contributed. See the original author and article here.
IT/DevOps personnel need access to database and system metadata so that they can keep critical database systems healthy, performing to expectations and secure. Microsoft Purview DevOps policies, a subset of Microsoft Purview access policies, are specifically designed to provide IT/DevOps personnel with the access they need so that they perform their crucial job, while at the same time helping reduce the insider threat.
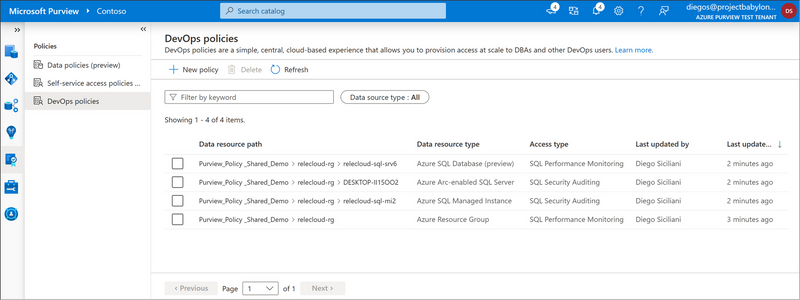
Microsoft Purview DevOps policies is a central, cloud-based experience. This is what the experience looks like:
 Figure 1: Screenshot of DevOps policies
Figure 1: Screenshot of DevOps policies
In prior blogs, we announced the launch into General Availability (GA) of Microsoft Purview DevOps policies, first for SQL Server 2022, and subsequently for Azure SQL Database. Today, we are pleased to introduce the expansion of permissions related to role “SQL Performance Monitor”. This is one of two roles that can be provisioned as part of the Microsoft Purview DevOps policies.
Up to this point, this role gave a user (or group) access to hundreds to DMVs/DMFs. These DMVs/DMFs allow the user to review system parameters, identify performance bottlenecks, currently running queries, blocking issues, memory usage, file and index usage, active user connections, internal tasks, procedure execution stats and use of the Query Store, among others.
With the expansion, Microsoft Purview can now be used to grant access to all the typical commands that a persona tasked with performance monitoring and analysis requires. The additional permission assignments enable the user (or group) that is assigned role SQL Performance Monitor to see data from most catalog views, which contain information about user objects and configurations. Furthermore, the user will now be able to run several DBCC commands that are used for system analysis and can even create and change Extended Event-sessions for system tracing for deeper analysis.
This capability will be rolled-out to all Azure regions that support Azure SQL and Microsoft Purview over the next few weeks.
Role definition detail
The following table lists the actions that are now part of the role definition for SQL Performance Monitor. The first four (in blue) were already part of the role and the ones that follow were recently added.
Microsoft Purview policy role definition
|
Data source specific actions
|
|
|
SQL Performance Monitor
|
Microsoft.Sql/Sqlservers/Connect
|
|
Microsoft.Sql/Sqlservers/Databases/Connect
|
|
Microsoft.Sql/Sqlservers/Databases/SystemViewsAndFunctions/DatabasePerformanceState/Rows/Select
|
|
Microsoft.Sql/Sqlservers/SystemViewsAndFunctions/ServerPerformanceState/Rows/Select
|
|
Microsoft.Sql/Sqlservers/Databases/SystemViewsAndFunctions/DatabaseGeneralMetadata/Rows/Select
|
|
Microsoft.Sql/Sqlservers/SystemViewsAndFunctions/ServerGeneralMetadata/Rows/Select
|
|
Microsoft.Sql/Sqlservers/Databases/DBCCs/ViewDatabasePerformanceState/Execute
|
|
Microsoft.Sql/Sqlservers/DBCCs/ViewServerPerformanceState/Execute
|
|
Microsoft.Sql/Sqlservers/Databases/ExtendedEventSessions/Create
|
|
Microsoft.Sql/Sqlservers/Databases/ExtendedEventSessions/Options/Alter
|
|
Microsoft.Sql/Sqlservers/Databases/ExtendedEventSessions/Events/Add
|
|
Microsoft.Sql/Sqlservers/Databases/ExtendedEventSessions/Events/Drop
|
|
Microsoft.Sql/Sqlservers/Databases/ExtendedEventSessions/State/Enable
|
|
Microsoft.Sql/Sqlservers/Databases/ExtendedEventSessions/State/Disable
|
|
Microsoft.Sql/Sqlservers/Databases/ExtendedEventSessions/Drop
|
|
Microsoft.Sql/Sqlservers/Databases/ExtendedEventSessions/Target/Add
|
|
Microsoft.Sql/Sqlservers/Databases/ExtendedEventSessions/Target/Drop
|
|
Microsoft.Sql/Sqlservers/ExtendedEventSessions/Create
|
|
Microsoft.Sql/Sqlservers/ExtendedEventSessions/Options/Alter
|
|
Microsoft.Sql/Sqlservers/ExtendedEventSessions/Events/Add
|
|
Microsoft.Sql/Sqlservers/ExtendedEventSessions/Events/Drop
|
|
Microsoft.Sql/Sqlservers/ExtendedEventSessions/State/Enable
|
|
Microsoft.Sql/Sqlservers/ExtendedEventSessions/State/Disable
|
|
Microsoft.Sql/Sqlservers/ExtendedEventSessions/Drop
|
|
Microsoft.Sql/Sqlservers/ExtendedEventSessions/Target/Add
|
|
Microsoft.Sql/Sqlservers/ExtendedEventSessions/Target/Drop
|
Conclusion
With that, we expect the SQL Performance Monitor role to cover all the typical scenarios where you need to provision access for dedicated support personnel to Azure SQL or SQL Server 2022 (Azure Arc-enabled), all from a simple, central and scalable experience.
Of course. we are always interested in which other scenarios you would like to see enabled via Microsoft Purview.
Recommended next steps
- DevOps policies for Azure SQL MI (Private Preview): Click here to test-drive this new experience at no additional charge. Note, your Microsoft Purview account and Azure SQL MI will be allow-listed after you enroll.
- DevOps policies for Azure SQL Database (GA) and SQL Server 2022 (GA):


Recent Comments