by Contributed | Sep 25, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
The most read paths on LEARN has gotten an update. Check out the new paths here and some description on what each path contains:
Azure Fundamentals part 1: Describe core Azure concepts
- Understand the benefits of cloud computing in Azure and how it can save you time and money
- Explain cloud concepts such as high availability, scalability, elasticity, agility, and disaster recovery
- Describe core Azure architecture components such as subscriptions, management groups, resources and resource groups
- Summarize geographic distribution concepts such as Azure regions, region pairs, and availability zones
Azure Fundamentals part 2: Describe core Azure services
- Understand the breadth of services available in Azure including compute, network, storage, and database
- Identify virtualization services such as Azure Virtual Machines, Azure Container Instances, Azure Kubernetes Service, and Windows Virtual Desktop
- Compare Azure’s database services such as Azure Cosmos DB, Azure SQL, Azure Database for MySQL, Azure Database for PostgreSQL, and Azure’s big data and analysis services
- Examine Azure networking resources such as Virtual Networks, VPN Gateways, and Azure ExpressRoute
- Summarize Azure storage services such Azure Blob Storage, Azure Disk Storage, and Azure File Storage
Azure Fundamentals part 3: Describe core solutions and management tools on Azure
- Choose the correct Azure Artificial Intelligence service to address different kinds of business challenges.
- Choose the best software development process tools and services for a given business scenario.
- Choose the correct cloud monitoring service to address different kinds of business challenges.
- Choose the correct Azure management tool to address different kinds of technical needs and challenges.
- Choose the right serverless computing technology for your business scenario.
- Choose the best Azure IoT service for a given business scenario.
Azure Fundamentals part 4: Describe general security and network security features
-
Having a good security strategy is essential in today’s digital world. Every application and service, whether on-premises or in the cloud, needs to be designed with security in mind. Security needs to happen at the application level, at the data level, and at the network level.
Learn about the various Azure services you can use to help ensure that your cloud resources are safe, secure, and trusted.
Azure Fundamentals part 5: Describe identity, governance, privacy, and compliance features
-
With the rise of remote work, bring your own device (BYOD), mobile applications, and cloud applications, the primary security boundary has shifted from firewalls and physical access controls to identity.
Understanding who is using your systems and what they have permission to do are critical to keeping your data safe from attackers. To stay organized, manage costs, and meet your compliance goals, you need a good cloud governance strategy.
Learn how Azure can help you secure access to cloud resources, what it means to build a cloud governance strategy, and how Azure adheres to common regulatory and compliance standards.
Azure Fundamentals part 6: Describe Azure cost management and service level agreements
-
Migration to the cloud presents new ways to think about your IT expenses. The cloud also removes the burden of supporting IT infrastructure.
As you move to the cloud, you might ask:
- How much will it cost?
- What guarantees does Azure provide around uptime and connectivity?
- How do preview services impact my production applications?
Learn about the factors that influence cost, tools you can use to help estimate and manage your cloud spend, and how Azure’s service-level agreements (SLAs) can impact your application design decisions.
by Contributed | Sep 25, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
The most read paths on LEARN has gotten an update. Check out the new paths here and some description on what each path contains:
Azure Fundamentals part 1: Describe core Azure concepts
- Understand the benefits of cloud computing in Azure and how it can save you time and money
- Explain cloud concepts such as high availability, scalability, elasticity, agility, and disaster recovery
- Describe core Azure architecture components such as subscriptions, management groups, resources and resource groups
- Summarize geographic distribution concepts such as Azure regions, region pairs, and availability zones
Azure Fundamentals part 2: Describe core Azure services
- Understand the breadth of services available in Azure including compute, network, storage, and database
- Identify virtualization services such as Azure Virtual Machines, Azure Container Instances, Azure Kubernetes Service, and Windows Virtual Desktop
- Compare Azure’s database services such as Azure Cosmos DB, Azure SQL, Azure Database for MySQL, Azure Database for PostgreSQL, and Azure’s big data and analysis services
- Examine Azure networking resources such as Virtual Networks, VPN Gateways, and Azure ExpressRoute
- Summarize Azure storage services such Azure Blob Storage, Azure Disk Storage, and Azure File Storage
Azure Fundamentals part 3: Describe core solutions and management tools on Azure
- Choose the correct Azure Artificial Intelligence service to address different kinds of business challenges.
- Choose the best software development process tools and services for a given business scenario.
- Choose the correct cloud monitoring service to address different kinds of business challenges.
- Choose the correct Azure management tool to address different kinds of technical needs and challenges.
- Choose the right serverless computing technology for your business scenario.
- Choose the best Azure IoT service for a given business scenario.
Azure Fundamentals part 4: Describe general security and network security features
-
Having a good security strategy is essential in today’s digital world. Every application and service, whether on-premises or in the cloud, needs to be designed with security in mind. Security needs to happen at the application level, at the data level, and at the network level.
Learn about the various Azure services you can use to help ensure that your cloud resources are safe, secure, and trusted.
Azure Fundamentals part 5: Describe identity, governance, privacy, and compliance features
-
With the rise of remote work, bring your own device (BYOD), mobile applications, and cloud applications, the primary security boundary has shifted from firewalls and physical access controls to identity.
Understanding who is using your systems and what they have permission to do are critical to keeping your data safe from attackers. To stay organized, manage costs, and meet your compliance goals, you need a good cloud governance strategy.
Learn how Azure can help you secure access to cloud resources, what it means to build a cloud governance strategy, and how Azure adheres to common regulatory and compliance standards.
Azure Fundamentals part 6: Describe Azure cost management and service level agreements
-
Migration to the cloud presents new ways to think about your IT expenses. The cloud also removes the burden of supporting IT infrastructure.
As you move to the cloud, you might ask:
- How much will it cost?
- What guarantees does Azure provide around uptime and connectivity?
- How do preview services impact my production applications?
Learn about the factors that influence cost, tools you can use to help estimate and manage your cloud spend, and how Azure’s service-level agreements (SLAs) can impact your application design decisions.
by Contributed | Sep 25, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
Hyperscale cloud technologies have become a common platform for modernization and lift-and-shift of On-Premise customers due to cost efficiencies, scalability and resiliency, Complex workloads like SAS have very particular workload characteristics and requirements that need to be understood and rationalized prior to deciding whether to move to the cloud or not, the maturity of compute and storage however has made this easier than in the past, allowing for Microsoft Azure to become a consideration for hosting such demanding workloads.
The attached whitepaper describes guidelines for deploying SAS 9.4 Grid technologies on Azure using the Lustre parallel clustered filesystem in a cost effective, performant and scalable manner.
The work is a collaboration between Donovan White and myself from Microsoft and Renier Dryer from CrunchYard.
Open the whitepaper with the link below.
by Contributed | Sep 25, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
Azure App Services supports an interesting feature called Manage Identity from Azure Active Directory.
This allows your App Services to easily connect to Azure Resources such as Azure KeyVault, Azure Storage, Azure SQL . The complete list of resources that support this feature are available in the following document:
Azure Services that support managed identities – Azure AD | Microsoft Docs
You could refer to our documentation for more details on this feature here.
MSI-Validator helps you troubleshoot issues with Managed Identity for Azure App Services.
The link to download this tool is available in the attachments section of the blog.
Installation Steps:
- Download the zip file from the attachments.
Current version – v1.0.0.0
- Extract it to the local folder.
- Drag and drop “msi-validator.exe” to the Kudu console of the App Service (https://<webapp-name>.scm.azurewebsites.net)

Commands:
- To Get an Access Token :
msi-validator get-token -r <resource>
Valid Arguments for resource = keyvault, storage, sql
Sample:
msi-validator get-token -r keyvault
msi-validator get-token -r storage
msi-validator get-token -r sql
- To Test the connection
msi-validator test-connection -r <resource> -e <endpoint>
Valid Arguments for resource = keyvault, storage, sql
Sample:
msi-validator test-connection -r "keyvault" -e "https://<keyvault-name>.vault.azure.net/secrets/<secret-key>"
msi-validator.exe test-connection -r storage -e https://<storage-name>.blob.core.windows.net/webapp/<container-name>/<blob-path>
msi-validator.exe test-connection -r sql -e "Data Source=<server-name>.database.windows.net;Initial Catalog=<database-name>;"
Troubleshooting:
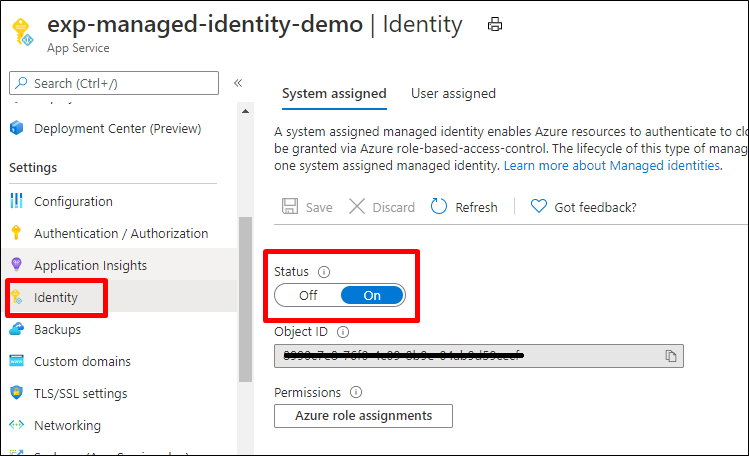
- From the Identity Blade of the App Service, ensure that Managed Identity is turned on.
- Navigate to Kudu Console (https://<webapp-name>.scm.azurewebsites.net) > Environment Section and search for MSI (Ctrl + F)
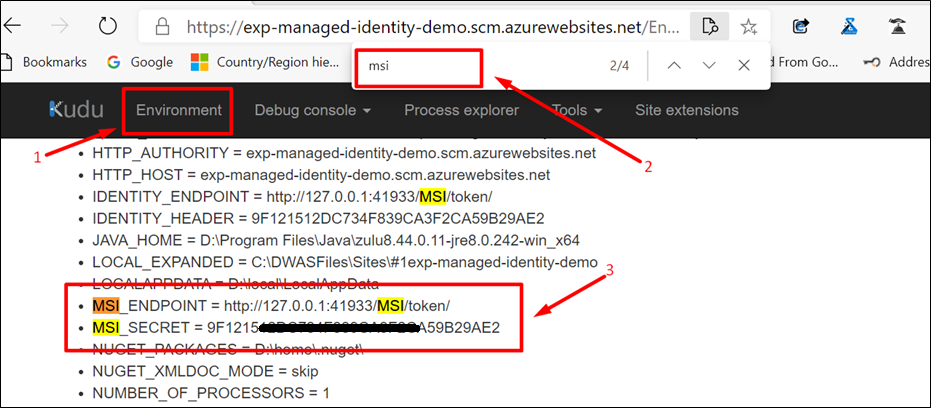
The Environmental Variables “MSI_ENDPOINT” and “MSI_SECRET” would have been set automatically.
- Run the command “msi-validator get-token -r <resource>” and check if a token is being returned.
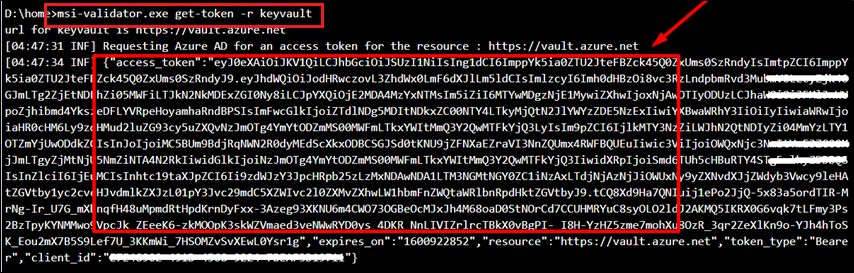
An access token should be returned.
Otherwise, it indicates that MSI service has issues reaching out to Azure Active Directory to fetch a token.
Things to check :
- Does the App Service have regional VNet Integration / is the App in ASE?
Are there any User Defined Routes on the subnet to which the App Service is integrated ?
If Yes , is the device to which the traffic is force tunneled, blocking any Azure Active Directory Dependency ?
- Do you still face the issue if Managed Identity is disabled and enabled again ?
- Run the command “msi-validator test-connection -r <resource> -e “<endpoint>” ” and check if data is returned from the resource or inspect the error message..
KeyVault:
From the below error message, we see that the App Service doesn’t have necessary permissions to access the KeyVault. 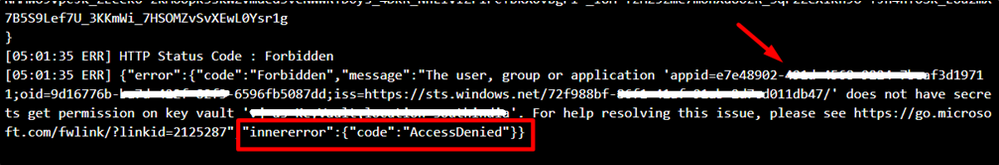
Resolution:
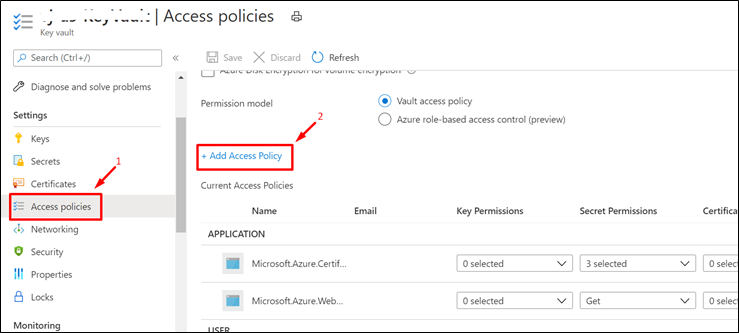
- Navigate to the Access Policies Blade of KeyVault from the Azure Portal.
- Click on “+ Add Access Policy“
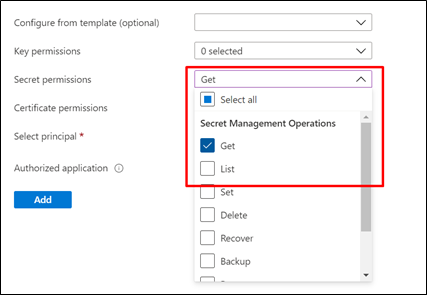
- Provide the necessary permission.
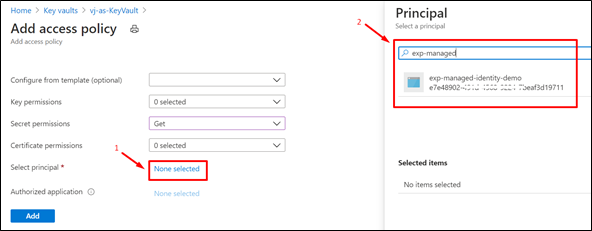
-
Choose the Service Principal (name of the App Service)
Storage:
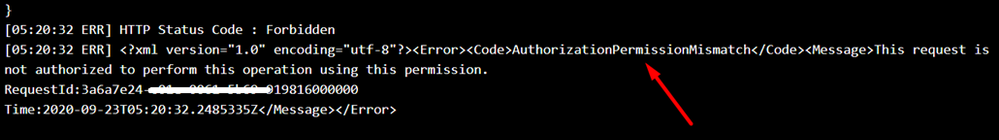
Resolution :
Navigate to the Access Control IAM) > Add Role assignment and choose the necessary storage related permission. The roles should be configured as per your application’s use case.
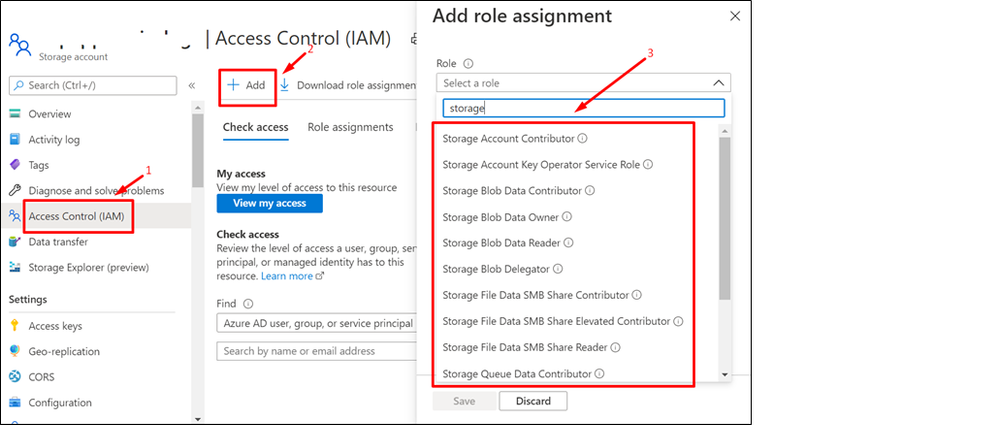
SQL:
The application could fail while connecting to Azure SQL using MSI with the error message: “Unable to connect to SQL. Exception : Login failed for user ‘<token-identified principal>’“
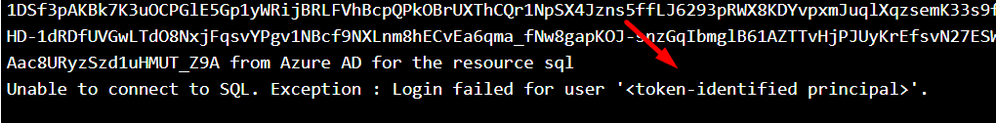
Resolution:
If you want, you can add the identity to an Azure AD group, then grant SQL Database access to the Azure AD group instead of the identity. For example, the following commands add the managed identity from the previous step to a new group called myAzureSQLDBAccessGroup:
groupid=$(az ad group create --display-name myAzureSQLDBAccessGroup --mail-nickname myAzureSQLDBAccessGroup --query objectId --output tsv)
msiobjectid=$(az webapp identity show --resource-group myResourceGroup --name <app-name> --query principalId --output tsv)
az ad group member add --group $groupid --member-id $msiobjectid
az ad group member list -g $groupid
In the Cloud Shell, sign in to SQL Database by using the SQLCMD command. Replace <server-name> with your server name, <db-name> with the database name your app uses, and <aad-user-name> and <aad-password> with your Azure AD user’s credentials.
sqlcmd -S <server-name>.database.windows.net -d <db-name> -U <aad-user-name> -P "<aad-password>" -G -l 30
In the SQL prompt for the database you want, run the following commands to grant the permissions your app needs. For example,
CREATE USER [<identity-name>] FROM EXTERNAL PROVIDER;
ALTER ROLE db_datareader ADD MEMBER [<identity-name>];
ALTER ROLE db_datawriter ADD MEMBER [<identity-name>];
ALTER ROLE db_ddladmin ADD MEMBER [<identity-name>];
GO
<identity-name> is the name of the managed identity in Azure AD. If the identity is system-assigned, the name always the same as the name of your App Service app. To grant permissions for an Azure AD group, use the group’s display name instead (for example, myAzureSQLDBAccessGroup).
Type EXIT to return to the Cloud Shell prompt.
The back-end services of managed identities also maintains a token cache that updates the token for a target resource only when it expires. If you make a mistake configuring your SQL Database permissions and try to modify the permissions after trying to get a token with your app, you don’t actually get a new token with the updated permissions until the cached token expires.
Modify connection string
Remember that the same changes you made in Web.config or appsettings.json works with the managed identity, so the only thing to do is to remove the existing connection string in App Service, which Visual Studio created deploying your app the first time. Use the following command, but replace <app-name> with the name of your app.
az webapp config connection-string delete --resource-group myResourceGroup --name <app-name> --setting-names MyDbConnection
You could refer to our official documentation regarding this at Tutorial: Access data with managed identity – Azure App Service | Microsoft Docs

by Contributed | Sep 25, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
Well Microsoft Ignite 2020 is over and while our step counters may not have captured as many steps as last year… but it doesn’t mean that there wasn’t a plethora of Azure news shared. Here are the headlines we are covering this week: The IT Professional’s role in the Responsible use of AI, Azure Automanage for VMs, Move resources to another region with Azure Resource Mover, New Windows Virtual Desktop Capabilities, Hybrid Cloud announcements surrounding Azure Arc and Azure Stack as well as the Microsoft Learn module of the week.
The IT Professional’s Role in the Responsible use of Artificial Intelligence
Artificial Intelligence, like Operations, is in everything these days. From the way we work – to the way we go about our daily lives – AI enables us to make quicker, smarter decisions on what our next steps should be. But that also raises the question of ethics and more specifically the ethical use and management of AI.
An example of responsible AI utilization came in the form of the newly announced spatial analysis capability in the Computer Vision Azure Cognitive Service. Its advanced AI models aggregate insights from multiple cameras to count the number of people in the room, measure the distance between individuals, and monitor wait and dwell times. Organizations can now apply this technology to use their space in a safe, optimal way.
I also had the opportunity to sit down with members of the Microsoft Ethics & Society team to discuss the IT Professional’s role in responsible adoption of Artificial Intelligence as well as share the corresponding resources made available.
Azure Automanage for virtual machines
Newly announced service, Azure Automanage reduces the OpEx burden for VMs further by automating day-to-day operational requirements in areas such as security, anti-malware, compliance, disaster recovery, etc. Through its virtual machine best practices capability, select services are discovered, onboarded, and configured across the entire lifecycle of both dev/test and production VMs. You can add VMs individually or do so at scale safe in the knowledge that if your VMs deviate from best practices, Azure Automanage will detect and automatically correct it.
Azure Resource Mover: Move resources across regions from resource groups
Resource Mover helps you to move Azure resources between Azure regions. You might move resources to different Azure regions to: Align to a region launch, Align for services/features, Respond to business developments, Align for proximity, Meet data requirements, Respond to deployment requirements, and Respond to decommissioning.
New Windows Virtual Desktop Capabilities Announced
To help customers continue to accelerate this move to secure remote work with Windows Virtual Desktop, Microsoft has announced several new capabilities that make it even easier to deploy, secure, and scale your virtual desktop deployments. These new capabilities will be available in public preview by the end of the calendar year 2020. These capabilities include:
- Microsoft Endpoint Manager support for Windows 10 multisession will provide IT admins with the ability to manage and secure virtual desktops the same way as physical devices.
- New integration with Azure Monitor, providing customers with a workbook that captures all the relevant monitoring insights and provides rich visualizations to identify and troubleshoot issues quickly. This is an important consideration for customers looking to monitor and troubleshoot easily while deploying virtual desktops at scale.
- The ability to add application layers from the Azure portal, helping customers onboard applications quickly — with a few clicks, you can now deploy and publish applications for your employees.
MS Learn Module of the Week

This Microsoft Learn module provides an introductory overview of various hybrid-cloud technologies and how you can connect an on-premises environment to Azure in a way that works best for your organization.
Let us know in the comments below if there are any news items you would like to see covered in next week show. Az Update streams live every Friday so be sure to catch the next episode and join us in the live chat.




Recent Comments