This article is contributed. See the original author and article here.
Hi Everyone!
After speaking with a few of our customers, we realized that some were not familiar or aware of their ability to leverage suggested and saved queries inside of Cloud App Security. In this blog, we will show you what we consider our top five use cases for custom queries!
But before we get into this great feature, below is how to navigate to it–
When you get to the Dashboard, click on Investigate and then Activity Log. At the top left, you will see “Select a Query.”
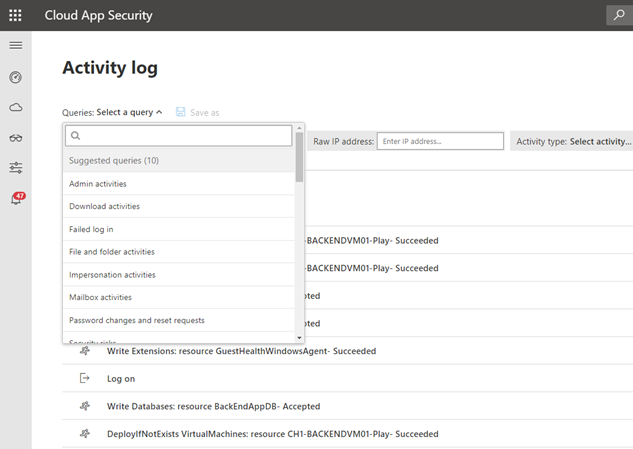
Out of the box, users are given 10 built-in suggested queries they can start using immediately: Cloud App Security discovered app filters and queries. These queries include admin activities, failed logins, file and folder activities, password changes and quite a few more! Our customers use these queries as a starting point and customize them depending on their use cases. Aside from this immediate benefit, you can also create your own saved queries based on your typical investigations or customized environment.
Below, we have compiled a short list of use cases we have seen our customers use for custom queries that may help you as well.
Use Case #1: Someone has added an external account with a personal email to our Teams tenant, which goes against company policy, and we need to know who and when it was done.
Filters Needed:
- Activity Type equals “Create User”
- User name does not equal “On-Prem Directory Synchronization”
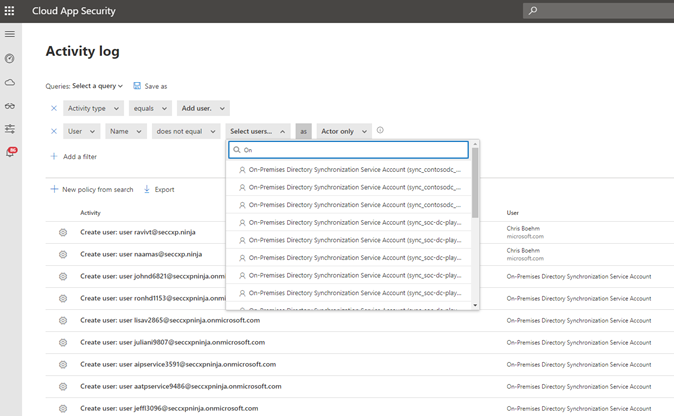
Note: Ensure you run this query in your environment and exclude any accounts that may be a part of this process. We needed to exclude users associated with On-Prem Directory Synchronization and you may too
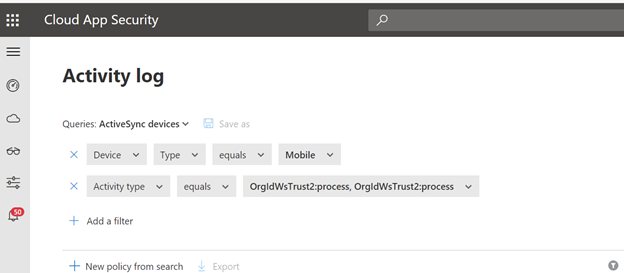
Use Case #2: We want to block the use of ActiveSync to push users to leverage updated authentication methods. Prior to denying the use of ActiveSync, we need to see who may be using it today and communicate before deprecation.
Filters Needed:
- Device Type equals Mobile
- Activity Type equals ”Log on: OrgIdWsTrust2:process” and “Failed Log On: OrgIdWsTrust2:process”
Note: OrgIdWsTrust:process is an activity type that surfaces ActiveSync data
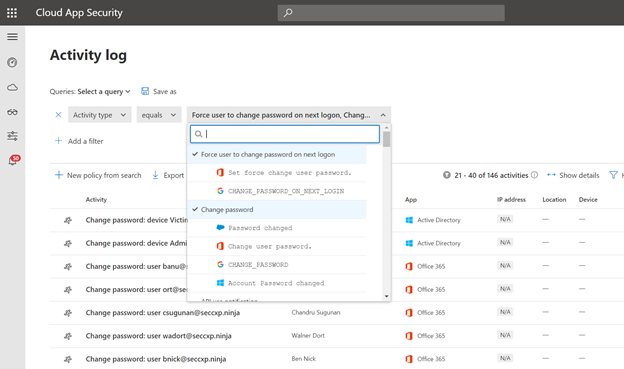
Use Case #3: We recently had a user that was potentially compromised, we forced them to reset their password but we want to ensure that they have completed this as directed.
Filters Needed:
- Activity Type equals “Force User to change password on next logon” and “Change password
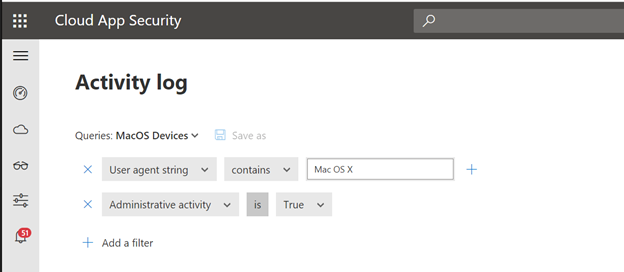
Use Case #4: All of our administrators are given Windows laptops, we would like to see if any administrative activities have been conducted using a Mac.
Filters Needed:
- User Agent String contains “MAC OS X”
- Administrative Activity is “True”
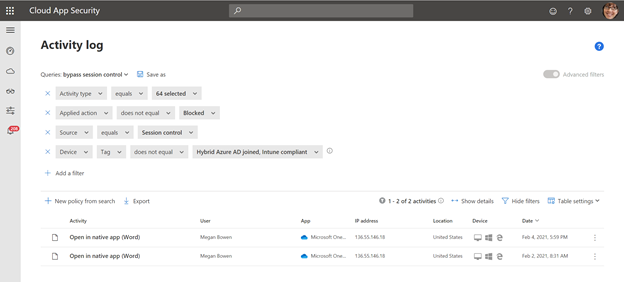
Use Case #5: As an administrator, I want to see all file downloads that were not blocked via session controls from an unmanaged device.
Filters Needed:
- Activity type equals “Download File”
- Applied Action does not equal “Blocked”
- Source equals “Session Control”
- Device Tag does not equal “Hybrid Azure Ad joined, Intune Compliant”
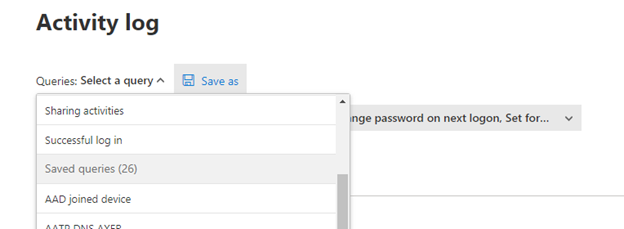
For ease of use, all queries can be saved and can be accessed later under “Saved queries,” this will reduce the time and resources needed to reproduce the filters.
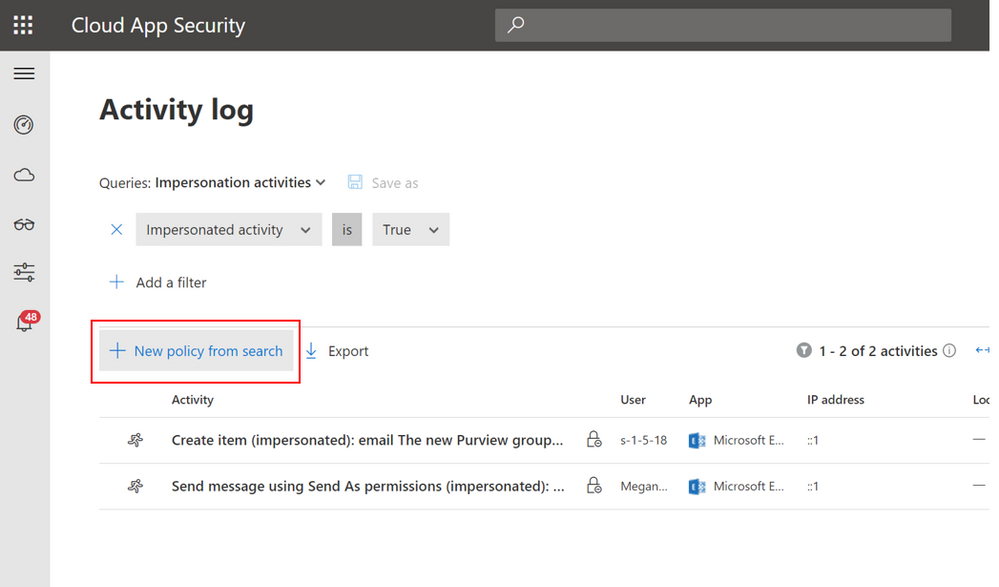
Lastly, we wanted to point out that each of these queries can be turned into a policy in just a few clicks. Once your conditions have been perfected and all appropriate environment tweaks are made, you can select “New Policy from search” that will redirect you to the policy page. All filters and conditions will be automatically listed and all you have left is some naming, alerting details and after actions to complete your policy.
We hope you found this article helpful and ask that you drop us a comment and let us know what custom policies you are using today!
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments