Our Latest News
Use intelligence to transform routing of service delivery requests
Any call center that uses unified routing to manage and assign incoming support requests is going to notice gains in efficiency. The core routing capabilities in Dynamics 365 Customer Service use skill matching and priority to help determine assignments. However,...
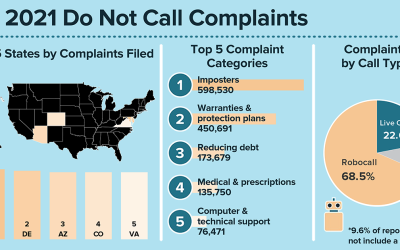
What are people reporting at DoNotCall.gov?
In the past 18 years of the National Do Not Call Registry, those of you signed up for the registry (244 million phone numbers right now) have reported millions upon millions of unwanted sales calls over the years. Here’s a quick look at what you’ve reported this year...
The 5-Minute Recap: Everything new with Security, Compliance, and Identity on Microsoft Learn
Welcome to our new monthly blog series featuring the latest Security, Compliance, and Identity content updates on Microsoft Learn! This is our first post, and we’re highlighting recently released updates, including a new learning path we launched during Cybersecurity...
Donate safely this Giving Tuesday
Giving Tuesday is a great time to show your gratitude by donating to help others. But you don’t want to give money to a fake charity or scammer (any day of the week). Before you donate this Giving Tuesday ― and anytime you’re asked to give to charity: Research the...
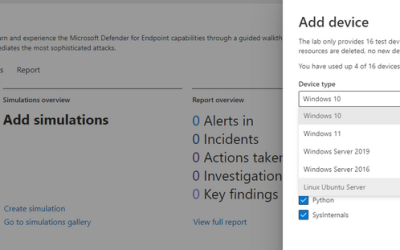
Evaluation Lab: Expanded OS support & Atomic Red Team simulations
Microsoft Defender for Endpoint’s Evaluation Lab is an environment that allows security teams to seamlessly test their defense against threats. We are excited to share that the Evaluation Lab now supports adding Windows 11, Windows Server 2016, and Linux devices. In...
The most important customer experience metrics (that you’re not tracking yet)
Marketing professionals go to great lengths to understand customers. Detailed personas are written to identify the motivations, interests, and buying patterns of prospects and customers. But all too often, these personasand their resulting customer journeysare...
Reminder for Critical Infrastructure to Stay Vigilant Against Threats During Holidays and Weekends
As Americans prepare to hit the highways and airports this Thanksgiving holiday, CISA and the Federal Bureau of Investigation (FBI) are reminding critical infrastructure partners that malicious cyber actors aren’t making the same holiday plans as you. Recent history...
How to spot and avoid common health scams
As a caregiver for a family member with special health needs, you know that shopping, making meals, or just regularly spending time with someone who can’t get out much can profoundly improve their quality of life. But being a caregiver is stressful, and scammers know...
Vulnerability Summary for the Week of November 15, 2021
adobe -- after_effects Adobe After Effects version 18.4.1 (and earlier) is affected by a Null pointer dereference vulnerability when parsing a specially crafted file. An unauthenticated attacker could leverage this vulnerability to achieve an application...
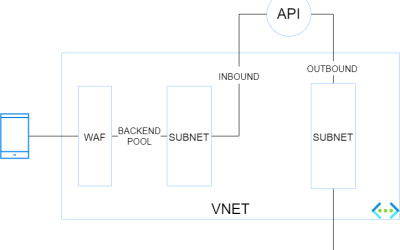
10 shades of public API hosting on Azure
APIs are everywhere and there are many ways to host them in Azure! Let us see what are the different possibilities with the pros & cons of each. I am not going to discuss the bits and bytes about each possibility. The purpose of this post is to give you a rough...
Extracting SAP data using OData – Part 2 – All About Parameters
Before implementing data extraction from SAP systems please always verify your licensing agreement. OData services have become one the most powerful interfaces in SAP systems. In the last episode, we’ve built a simple pipeline that extracts business information...
Updated: APT Exploitation of ManageEngine ADSelfService Plus Vulnerability
The Federal Bureau of Investigation (FBI), CISA, and Coast Guard Cyber Command (CGCYBER) have updated the Joint Cybersecurity Advisory (CSA) published on September 16, 2021, which details the active exploitation of an authentication bypass vulnerability...




Recent Comments