Our Latest News
CISA Issues ED 22-02 Directing Federal Agencies to Mitigate Apache Log4j Vulnerabilities
Official websites use .govA .gov website belongs to an official government organization in the United States. Secure .gov websites use HTTPS A lock () or https:// means you've safely connected to the .gov website. Share sensitive information only on official, secure...
VMware Releases Security Advisory
VMware has released a security advisory to address a vulnerability in Workspace ONE UEM console. An attacker could exploit this vulnerability to obtain sensitive information.CISA encourages users and administrators to review VMware Security Advisory...
NSA and CISA Release Final Part IV of Guidance on Securing 5G Cloud Infrastructures
CISA has announced the joint National Security Agency (NSA) and CISA publication of the final of a four-part series, Security Guidance for 5G Cloud Infrastructures. Part IV: Ensure Integrity of Cloud Infrastructure focuses on platform integrity,...
Look beyond the award when you hire a lawyer
If you suddenly need to hire a lawyer, you might start searching online. When you do, you’re likely to see lawyers and law firms with fancy-looking seals and badges on their websites claiming they’re among the best in their field. Before you move forward, know that...
End user email notifications are now customizable!
Attack Simulation Training is an intelligent phish risk reduction tool that measures behavior change and automates the deployment of an integrated security awareness training program across an organization. It is available with Microsoft 365 E5 or Microsoft...
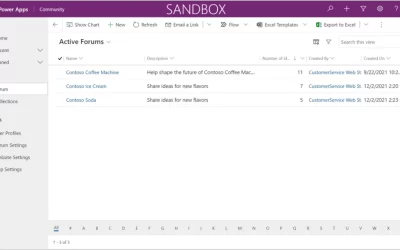
Engage with customers in Dynamics 365 Customer Service Community Preview
Organizations have an increasing need to interact with their customers to solicit feedback on products and services, building customer trust with process transparency. Dynamics 365 Customer Service has launched two capabilities in preview to enable organizations to...
CISA Adds Two Known Exploited Vulnerabilities to Catalog
CISA has added two new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence that threat actors are actively exploiting the vulnerabilities listed in the table below. These types of vulnerabilities are a frequent attack vector for malicious...
Advanced resource sets in Azure Purview
At-scale data processing systems typically store a single table in storage as multiple files. In the Azure Purview data catalog, this concept is represented by using resource sets; a resource set is a single object in the catalog that represents many assets in...
Achieving personalized engagement in Business to Business organizations
The business-to-business (B2B) landscape looks drastically different than it used to, thanks to digital acceleration that has reached every corner of our lives. Today's B2B buyers, accustomed to fast, frictionless, and personalized experiences in their everyday lives,...
’Tis the season for student loan scam calls
If you have a federal student loan, you probably already know that the Coronavirus emergency relief program that has paused your payments is ending. Repayments will begin again after January 31, 2022. Scammers know it, too, and are looking for ways to take advantage:...
Immediate Steps to Strengthen Critical Infrastructure against Potential Cyberattacks
In light of persistent and ongoing cyber threats, CISA urges critical infrastructure owners and operators to take immediate steps to strengthen their computer network defenses against potential cyberattacks. CISA has released CISA Insights: Preparing For and...
Adobe Releases Security Updates for Multiple Products
Adobe has released security updates to address vulnerabilities in multiple Adobe products. An attacker could exploit some of these vulnerabilities to take control of an affected system. CISA encourages users and administrators to review Adobe’s Security...




Recent Comments