Our Latest News
CISA Has Added One Known Exploited Vulnerability to Catalog
CISA has added one new vulnerability to it's Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. These types of vulnerabilities are a frequent attack vector for malicious cyber actors and pose significant risk to the federal enterprise....
Do you have slow workbooks due to size bloat? Give us a try at speeding up.
Hey Folks - Do you have slow workbooks due to size bloat? If so, then I am super excited to unveil Excel Performance team’s new capability to detect and remove unwanted size bloat and speed up such workbooks. At Excel, customer focus is at the core of what we do;...
CISA and NSA Publish Joint Cybersecurity Advisory on Control System Defense
CISA and the National Security Agency (NSA) have published a joint cybersecurity advisory about control system defense for operational technology (OT) and industrial control systems (ICSs). Control System Defense: Know the Opponent is intended to provide critical...
ISC Releases Security Advisories for Multiple Versions of BIND 9
The Internet Systems Consortium (ISC) has released security advisories that address vulnerabilities affecting multiple versions of the ISC’s Berkeley Internet Name Domain (BIND) 9. A remote attacker could exploit these vulnerabilities to potentially cause...
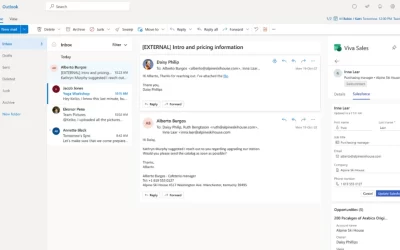
Announcing the general availability of Viva Sales, an intelligent selling experience in Microsoft 365 and Teams
Today we’re announcing the general availability of Microsoft Viva Sales on October 3, the first Viva application designed to improve the employee experience for a specific role: sellers. Viva Sales brings together a seller’s customer relationship...
Empower and energize employees with Microsoft Viva
Today, we’re announcing the expansion of Microsoft Viva with new apps and services that help companies address the three business imperatives from our latest Work Trend Index Pulse Report, to empower and energize employees to do meaningful work in an uncertain...
CISA Releases Three Industrial Control Systems Advisories
Official websites use .govA .gov website belongs to an official government organization in the United States. Secure .gov websites use HTTPS A lock () or https:// means you've safely connected to the .gov website. Share sensitive information only on official, secure...
Spot impersonator scams and share what you know
ARM Deployment considerations for Azure Data Factory
Some of the main goals for adopting DevOps culture in our organization are the reduction of failures in new deployments, be able to update our solutions frequently, improving deployments time, among others. Implementing DevOps processes into your Team requires trust...
Transforming customer experiences with connected sales and marketing
In the customer experience (CX) game, the last best experience sets the bar for the next. Businesses that are successful at meeting and exceeding their customers' expectations are hearing glowing testimonials like:"This brand makes valuable information directly...
How companies manipulate you online – and what the FTC is doing to protect you
Automating complex tax scenarios with enhanced Tax Calculation capabilities
Financial management is in the midst of a transformative moment. The global operating environment of business today is increasingly complex and prone to turbulence from numerous sources. New business models are disrupting the status quo and challenging the idea of how...



Recent Comments