by Scott Muniz | Sep 8, 2020 | Uncategorized
This article is contributed. See the original author and article here.
With the September 2020 cumulative update for Windows 10, we introduced changes that help improve the security of devices that scan Windows Server Update Services (WSUS) for their updates. This post will describe those changes and offer basic recommendations to help you better secure the devices in you organization.
Secure by default
First, beginning with the September 2020 cumulative update, HTTP-based intranet servers will be secure by default. To ensure that your devices remain inherently secure, we are no longer allowing HTTP-based intranet servers to leverage user proxy by default to detect updates. If you have a WSUS environment not secured with TLS protocol/HTTPS and a device requires a proxy in order to successfully connect to intranet WSUS Servers—and that proxy is only configured for users (not devices)—then your software update scans against WSUS will start to fail after your device successfully takes the September 2020 cumulative update.
Recommendations for greater security
To help ensure the security of your WSUS infrastructure, Microsoft recommends using the TLS/SSL protocol between your devices and your WSUS servers. The Microsoft Update system (including WSUS) relies on two types of content: update payloads and update metadata. Update payloads are the data files that contain the software update components that make up the update. Update metadata is all the information that the Microsoft Update system needs to know about the updates, including which updates are available, which devices each update can be applied to, and where to retrieve the payloads for each update. Both types of content are crucial and they both need to be protected to help keep your computers secure and up to date.
Update payloads are protected against modification by multiple means, including digital signature checks and cryptographic hash verifications. HTTPS provides a proper chain of custody which the client uses to prove the data is trusted.
When a device receives updates directly from Microsoft Update, that device receives update metadata directly from Microsoft servers. This metadata is always transmitted via HTTPS to prevent tampering. When you use WSUS or Configuration Manager to manage your organization’s updates, the update metadata travels from Microsoft servers to your devices via a chain of connections. Each one of these connections needs to be protected against malicious attacks.
Your WSUS server connects with Windows Update servers and receives update metadata. This connection always uses HTTPS, and the HTTPS security features guard the metadata against tampering. If you have multiple WSUS servers arranged in a hierarchy, the downstream servers receive metadata from the upstream servers. Here, you have a choice: you can use HTTP or HTTPS for these metadata connections. Using HTTP; however, can be very dangerous as it breaks the chain of trust and can leave you vulnerable to attack. Using HTTPS enables the WSUS server to prove that it trusts the metadata it receives from the upstream WSUS server.
In order to maintain the chain of trust and prevent attacks on your client computers, you must ensure that all metadata connections within your organizations – the connections between upstream and downstream WSUS servers, and the connections between the WSUS servers and your client computers – are defended against attacks. To do so, we highly recommend that you configure your WSUS network to protect these connections using HTTPS. To learn more, see Michael Cureton’s post Security best practices for Windows Server Update Services (WSUS).
Even with HTTPS configured, it is still very important that you utilize a system-based proxy rather than a user-based proxy if a proxy is needed. When using a user-based proxy, a user, even one without elevated privileges, could intercept and manipulate the data being exchanged between the update client and the update server.
Recommendations for those who absolutely need user proxy
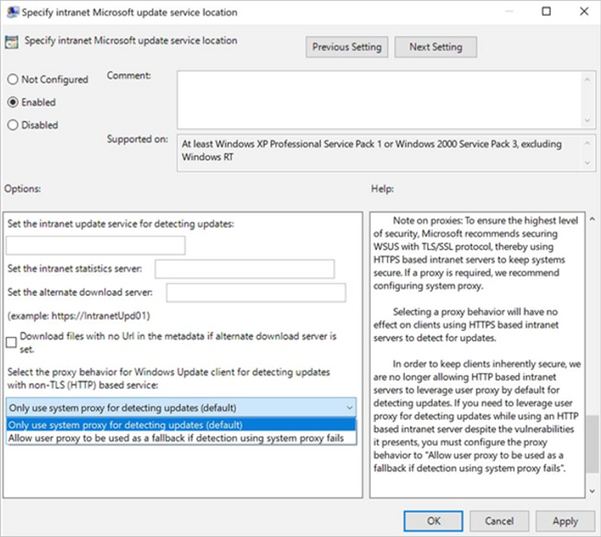
If you do need to leverage a user-based proxy to detect updates while using an HTTP-based intranet server, despite the vulnerabilities it presents, make sure to configure the proxy behavior to “Allow user proxy to be used as a fallback if detection using system proxy fails.”
Group Policy path: Windows Components>Windows Update>Specify intranet Microsoft update service location
Configuration Service Provider path: Update/ SetProxyBehaviorForUpdateDetection
Next steps
If you are an IT administrator who currently manages an HTTP-configured WSUS environment and relies on user-based proxy for client scans, please consider taking one of the following actions as soon as possible. If none of these actions are taken your devices will stop successfully scanning for software updates after the September 2020 security update.
Options to ensure that devices in your environment can continue to successfully scan for updates:
- Secure your WSUS environment with TLS/SSL protocol (configure servers with HTTPS).
- Set up system-based proxy for detecting updates if needed.

by Scott Muniz | Sep 8, 2020 | Uncategorized
This article is contributed. See the original author and article here.
With the September 2020 cumulative update for Windows 10, we introduced changes that help improve the security of devices that scan Windows Server Update Services (WSUS) for their updates. This post will describe those changes, outline the actions you need to take to ensure your devices continue to scan for updates, and offer basic recommendations to help you better secure the devices in you organization.
Secure by default
First, beginning with the September 2020 cumulative update, HTTP-based intranet servers will be secure by default. To ensure that your devices remain inherently secure, we are no longer allowing HTTP-based intranet servers to leverage user proxy by default to detect updates. If you have a WSUS environment not secured with TLS protocol/HTTPS and a device requires a proxy in order to successfully connect to intranet WSUS Servers—and that proxy is only configured for users (not devices)—then your software update scans against WSUS will start to fail after your device successfully takes the September 2020 cumulative update.
Recommendations for greater security
To help ensure the security of your WSUS infrastructure, Microsoft recommends using the TLS/SSL protocol between your devices and your WSUS servers. The Microsoft Update system (including WSUS) relies on two types of content: update payloads and update metadata. Update payloads are the data files that contain the software update components that make up the update. Update metadata is all the information that the Microsoft Update system needs to know about the updates, including which updates are available, which devices each update can be applied to, and where to retrieve the payloads for each update. Both types of content are crucial and they both need to be protected to help keep your computers secure and up to date.
Update payloads are protected against modification by multiple means, including digital signature checks and cryptographic hash verifications. HTTPS provides a proper chain of custody which the client uses to prove the data is trusted.
When a device receives updates directly from Microsoft Update, that device receives update metadata directly from Microsoft servers. This metadata is always transmitted via HTTPS to prevent tampering. When you use WSUS or Configuration Manager to manage your organization’s updates, the update metadata travels from Microsoft servers to your devices via a chain of connections. Each one of these connections needs to be protected against malicious attacks.
Your WSUS server connects with Windows Update servers and receives update metadata. This connection always uses HTTPS, and the HTTPS security features guard the metadata against tampering. If you have multiple WSUS servers arranged in a hierarchy, the downstream servers receive metadata from the upstream servers. Here, you have a choice: you can use HTTP or HTTPS for these metadata connections. Using HTTP; however, can be very dangerous as it breaks the chain of trust and can leave you vulnerable to attack. Using HTTPS enables the WSUS server to prove that it trusts the metadata it receives from the upstream WSUS server.
In order to maintain the chain of trust and prevent attacks on your client computers, you must ensure that all metadata connections within your organizations – the connections between upstream and downstream WSUS servers, and the connections between the WSUS servers and your client computers – are defended against attacks. To do so, we highly recommend that you configure your WSUS network to protect these connections using HTTPS. To learn more, see Michael Cureton’s post Security best practices for Windows Server Update Services (WSUS).
Even with HTTPS configured, it is still very important that you utilize a system-based proxy rather than a user-based proxy if a proxy is needed. When using a user-based proxy, a user, even one without elevated privileges, could intercept and manipulate the data being exchanged between the update client and the update server.
Recommendations for those who absolutely need user proxy
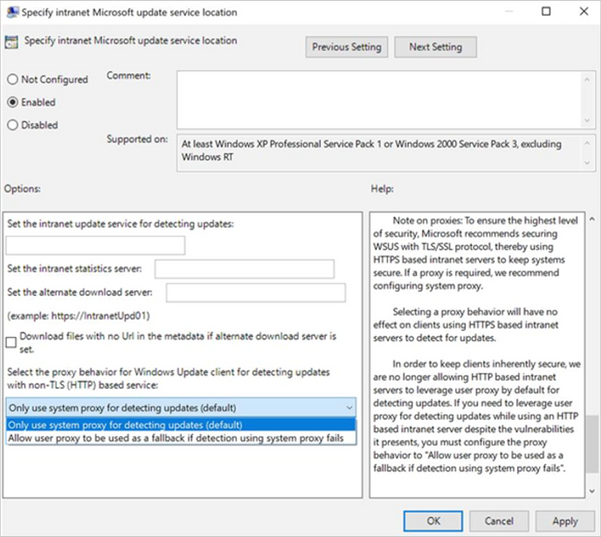
If you do need to leverage a user-based proxy to detect updates while using an HTTP-based intranet server, despite the vulnerabilities it presents, make sure to configure the proxy behavior to “Allow user proxy to be used as a fallback if detection using system proxy fails.”
Group Policy path: Windows Components>Windows Update>Specify intranet Microsoft update service location
Configuration Service Provider path: Update/ SetProxyBehaviorForUpdateDetection

Next steps
If you are an IT administrator who currently manages an HTTP-configured WSUS environment and relies on user-based proxy for client scans, please consider taking one of the following actions as soon as possible. If none of these actions are taken your devices will stop successfully scanning for software updates after the September 2020 security update.
Options to ensure that devices in your environment can continue to successfully scan for updates:
- Secure your WSUS environment with TLS/SSL protocol (configure servers with HTTPS).
- Set up system-based proxy for detecting updates if needed.

by Scott Muniz | Sep 8, 2020 | Uncategorized
This article is contributed. See the original author and article here.
 Voices of #HealthcareCloud is a new webinar series focused on how Healthcare is seeing positive business and clinical outcomes with cloud technology.
Voices of #HealthcareCloud is a new webinar series focused on how Healthcare is seeing positive business and clinical outcomes with cloud technology.
We will be bringing new and creative solutions to you at least once a month so we hope you tune in live or catch the on-demand series after the session is completed.
For the upcoming session on September 15 at 10a PST, we’ll talk about how to leverage the power of the Microsoft cloud to break down functional boundaries and improve cross functional collaboration. Learn how to set up and run multi-disciplinary huddles using the power of Microsoft Teams.
We’ll look to cover the building blocks and touch on some potential use cases including
- Tiered huddles
- Care coordination
- Situational awareness
- Discharge planning
To download the invite, click here.
To join the event, click here.

by Scott Muniz | Sep 8, 2020 | Uncategorized
This article is contributed. See the original author and article here.
 This month, we have THREE wallpaper options for you!
This month, we have THREE wallpaper options for you!
Hello, world!
It’s me again, with your monthly digital swag!
This month, we are celebrating #SkillUpSeptember and will be sharing resources for everyone from the person who is brand new to coding all the way up to the seasoned pro!
So, to get your month and learning adventure started right, here are THREE new wallpapers / Teams backgrounds for you. Choose your favorite out of blue, purple, and orange (or switch between all three, we won’t judge ;))!
What do you plan on learning this month? Post in the comments below and we will help you find the best place to get started :party_popper:
Down the wallpapers / Teams backgrounds here ⬇
by Scott Muniz | Sep 8, 2020 | Uncategorized
This article is contributed. See the original author and article here.
By: Caroline Lee & Sebastien Molendijk
Update on where to find our Power Automate templates: we will post all of our templates on GitHub (https://github.com/microsoft/Microsoft-Cloud-App-Security/tree/master/Playbooks) including instructions on how to import the templates into your Power Automate instance. Comment below with any questions!
Welcome back to the Automation in Cloud App Security series with Sebastien & Caroline. For those of you who are reading for the first time, this series covers advanced scenarios for our Microsoft Cloud App Security (MCAS) users; providing Power Automate flows to solve the most common customer asks the Customer Experience team sees today.
Go check out our first blog to see how we auto-remediated information protection alerts https://aka.ms/MCAS/Auto-Blog. In today’s post, we will be covering how to use Power Automate in Cloud App Security to dismiss Infrequent Country alerts.
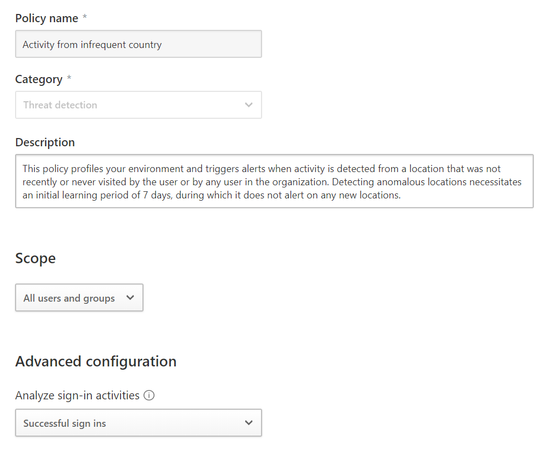
The Infrequent Country Alert in Cloud App Security is a popular detection for many companies. The alert triggers when there is sign-in activity outside of normal user locations. For example, imagine you have an employee who normally works out of the New York corporate office but then you see there is a sign-in activity for that person from China, you probably want to investigate this type of alert. In MCAS, you can tune the policy by scoping it to specific users, groups and by the type of sign in activity (see below template).

Activity from infrequent country template in MCAS
We’ve also recently published an anomaly detection alerts investigation guide to aid administrators in distinguishing true positives vs. benign true positives vs. false positives. But what about when employees go on vacation? Or are travelling outside of the country for work? How do you manage the volume of alerts especially for large enterprises?
We have developed a new flow in Power Automate to answer these questions. (Note: You will be able to select the template within the Power Automate gallery by searching for “Microsoft Cloud App Security.”) If you haven’t configured a Power Automate Flow in MCAS before, check out these steps in our documentation. So, how does this flow work? Essentially, when an infrequent country alert gets triggered, we’ll send it to Power Automate. In the flow, it will look at a couple of different details:
- The user profile (job title, department, email address, etc.)
- If the user has an out of office (OOO) message enabled
- Any groups the user is a part of
Based off these details, we can set conditions to auto-resolve the alert or request further investigation. The logic will be: If the user has an OOO message, then resolve the alert. You could also add more conditions around the user groups. For example, if you have a user who is part of a sensitive group such as Security Administrators, you could add logic to say if the user has no OOO message and is in the Security Admin group, then you may want to investigate the alert.
As folks start to take leave for vacation or staycation, this flow could help to save time in the alert investigation as admins will be able to focus on the most critical activities and lessen the sheer volume of alerts seen in MCAS. Keep an eye out for our next post and comment below if there are any other topics you’d like us to cover!
by Scott Muniz | Sep 8, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
Microsoft Learn offers several different fundamentals training and certifications for Azure—Azure Fundamentals, Azure Data Fundamentals, and Azure AI Fundamentals. Choose the ones that work for you. Use these foundational certifications as a starting point to explore more training for Azure technologies and to chart your path forward. If you’re looking to advance your career or to jump-start a new one, the message is the same: establish your foundations.
Azure opens a world of possibilities for you in this cloud-based, digital era. Let’s explore a few of them and how they can fit with your plans for growing your skills and expertise.
How you can use Azure to grow your career
Azure offers an ever-expanding set of cloud services that can help companies meet business challenges. It offers the freedom to build, manage, and deploy applications on a massive global network using an organization’s favorite tools and frameworks. This opens up many opportunities for IT professionals, depending on their talents and interests.
If you’re a developer, you can get your work done faster, take your skills to the next level, and imagine and build tomorrow’s applications.
If you’re an IT administrator, Azure cloud infrastructure helps you simplify management, reduce costs, rapidly adjust to changing business demands, and enhance security.
If you’re a data specialist, Azure can help you unlock the potential of data. Azure enables rapid growth and innovation with a portfolio of secure, enterprise grade database services that support open-source database engines.
If you’re an artificial intelligence (AI) specialist, Azure offers your application an edge over the competition. Just imagine what you can build—an app that translates speech in real time as you’re speaking or an app that helps you identify parts of a motor in a mixed-reality training. The possibilities are endless.
Get the Azure training that fits your background and interests
Interested in Azure, and want to learn more? Use our training offerings to explore the fundamentals of the cloud platform, foundational database concepts in Azure, and the basics of Azure AI.
Use Azure fundamentals training to learn the essentials of Azure—architectural components and core Azure services and solutions, plus management tools, compliance, security, and data protection. Learn how to get the best of Azure by growing your skills on cloud computing concepts, models, and services, including public, private, and hybrid cloud. In this training, explore cloud concepts, such as high availability, scalability, elasticity, agility, fault tolerance, and disaster recovery, and get strategies for transitioning to the cloud. To help you start this foundational training, we’ve curated the Azure Fundamentals collection on Microsoft Learn.
Use Azure database training to learn the fundamentals of database concepts in a cloud environment, get basic skilling in cloud data services, and build your foundational knowledge of cloud data services within Azure. Learn core data concepts, such as relational, nonrelational, big data, analytics, and roles, plus tasks and responsibilities in the world of data. To start this foundational training, check out the Azure Data Fundamentals collection on Microsoft Learn we’ve curated for you.
Use Azure AI training to explore how Azure provides easy-to-use services to help you get started with building AI solutions. Learn about many areas of AI, including machine learning, which is at the core of AI, and how many modern applications and services depend on predictive machine learning models. Explore computer vision, an area of AI in which software systems are designed to perceive the world visually, though cameras, images, and video. Plus, get the details on natural language processing (NLP), which supports applications that can see, hear, speak with, and understand users, and conversational AI, which deals with dialogs between AI agents and human users. We’ve curated the Azure AI Fundamentals collection on Microsoft Learn to help you start this foundational training.
Choose the right certification for you
Combine your training with a certification that announces your proficiency to the world. A comprehensive path forward for your Azure learning might begin with the foundations of cloud services and could be followed with core data concepts, after which it might move to common machine learning and AI workloads.
If you’re a system administrator, developer, or data and AI professional just starting out with Azure or the cloud, consider the Azure Fundamentals certification. This validates your basic knowledge of cloud services and how those services are provided with Azure. It can also help to prepare you for other Azure certifications, but it’s not a prerequisite for any of them.
Looking to grow your cloud database expertise? If you’re a developer or a data and AI pro—or even if you’re just beginning to work with data in the cloud—the new Azure Data Fundamentals certification can help you prove your knowledge of core data concepts and how they’re implemented using Azure data services.
If you’re getting started in the AI world, consider the Azure AI Fundamentals certification. Use this certification to demonstrate your knowledge of common AI and machine learning workloads and how to implement them on Azure. You don’t need to be a technical professional to take this exam. General programming knowledge will help, but data science or software engineering experience isn’t required.
Although not part of the Azure portfolio, the Power Platform Fundamentals certification can help data analysts and Azure developers validate their understanding of core Microsoft Power Platform capabilities, including Power Apps and Power BI.
Time to start mastering the basics!
It’s time to start growing your skills and building your reputation as an Azure expert. Go to Microsoft Learn, and explore the fundamentals training and related certifications: Azure Fundamentals. . . checked? Azure Data Fundamentals . . . checked? Azure AI Fundamentals. . . checked? Excellent. You’re on the path to getting the recognition that you deserve.
Related posts
Understanding Microsoft Azure certifications
Finding the right Microsoft Azure certification for you






Recent Comments