by Scott Muniz | Sep 11, 2020 | Uncategorized
This article is contributed. See the original author and article here.
This week, we bring you more Excel knowledge from MVPs Chandoo, Jan Karel Pieterse, and Jeff Lenning.
Power Query Tutorial – What is it, How to use, Full examples, Tips & Tricks
Chandoo shares a tutorial on Power Query in Excel, including examples and tips & tricks.
Enabling Drag And Drop Between Two Listboxes On A VBA Userform
Jan Karel Pieterse walks through a few lines of VBA code to enable drag and drop between two listboxes on a userform.
Dynamic Arrays (part 1, 2, and 3)
Jeff Lenning provides an overview of dynamic arrays in Excel in this three-part blog series.
Find this useful? Click Like below.
Want to know more about a specific Excel topic? Leave us a comment.
by Scott Muniz | Sep 11, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
Hello World!
With so many Azure customers relying on native Azure network security tools to secure their networks and applications, it is clear that there is a demand for more information on this topic. We are here to deliver just that. My team is dedicated to helping customers deploy and get the most out of Azure Network Security services, and we will be using Tech Community to amplify our voices.
What are the Azure Network Security services?
Azure network security is a set of native services meant to secure cloud and hybrid networks using the Zero Trust approach. To narrow it down, the primary tools we will cover here are Azure Firewall and Firewall Manager, Azure DDoS Protection, and Azure WAF. Yes, we’re aware that WAF deals with Application Security and not as much Network Security, but we’re bringing the concepts together. Web applications are delivered over networks, right?
Naturally while we are concentrating on these core services, that does not mean others will not be discussed. Quite the opposite, in fact. Building a secure Azure network can involve a vast array of resources. Expect attention to also be paid to Azure Bastion, Network Watcher, NSGs, as well as core networking components ranging from Route Tables to Virtual WAN.
Here’s a quick introduction to our primary tools for those that are unfamiliar:
Azure Firewall
Azure Firewall is the Azure-native PaaS firewall. Not to be confused with NSGs or resource firewalls on other PaaS services, Azure Firewall is built to be a centrally deployed and managed service that handles all the traffic from your regional deployments. Being a PaaS service, it auto-scales to accommodate increasingly demanding workloads, and it can be managed using the tools and methods you are already using to deploy and manage other resources – CLI, API, ARM, or whichever combination of abbreviations suits you best.
Azure Firewall is meant to perform all the same functions as most Network Virtual Appliances (NVAs), including segmenting east-west traffic within your VNets and controlling inbound and outbound traffic. Learn more in the docs.
Azure Firewall Manager
Firewall Manager is a service that serves a growing number of purposes. First, it allows for easy management of multiple Azure Firewalls. By abstracting the Firewall Policy away from each individual Firewall, you can use Firewall Manager to assign a central set of policies to one or many Firewalls across the globe. Additionally, Firewall Manager can be used to manage security services in Azure VWAN Hubs, which can either be more Azure Firewalls or third-party services such as Zscaler and iboss.
Read the docs to get the full story on Firewall Manager.
Azure WAF
Azure Web Application Firewall, as the name implies, is a firewall specifically meant to inspect web application traffic. Azure WAF can be attached to Application Gateway, Front Door, or CDN. There are some differences based on which service WAF is attached to, but the major function is the same – WAF analyzes decrypted traffic to match every request against its rules. These rules can consist of managed rulesets that look for common attacks found in the OWASP Top 10, bot protection rulesets that can block known malicious bot traffic, and custom rules that can look for various combinations of patterns.
To learn more, read some more docs.
Azure DDoS Protection Standard
Every resource that lives in an Azure data center benefits from the inbuilt platform-level DDoS Protection. Our DDoS Protection infrastructure is in place to ensure the availability of each Azure region, and this protection is inherited by every Azure service. For customers that need to ensure that their workloads are protected against every attack, DDoS Protection Standard is available to tune the protection mechanisms to each individual workload. Along with Standard comes several other features, which include cost protection for resources that auto-scale during an attack, high-priority support during attacks, and some great logging to feed to your SOC.
This is the final time in this post that docs will be read.
GitHub Repository
There has been such an appetite among our customers for useful technical content that we decided to create a GitHub repo just for Azure network security. Find it at Aka.ms/AzNetSec. You will find a combination of scripts, Policies, KQL queries, ARM templates, Azure Monitor Workbooks, and other odds and ends. Our goal is to make everything as useful as possible to take the guess work out of using our tools.
We encourage contributions from the community, so if you have something you think may be useful to others, don’t hesitate to fork and send us a pull request. Even if you don’t wish to contribute, please leave us feedback and suggestions for new content to create; we strive for continuous improvement. If you have suggestions or feedback regarding specific product features, please use Azure User Voice. Yes, we do monitor it and use the feedback when planning features.
Tech Community Plans
This has been a quick introductory post to share this team’s focus and areas of interest. We have lots of ideas for things to share in the future based on our experience with customers, but we also want to listen to the feedback we receive here. If there is something you would like to know more about, please leave a comment here or post about it in the Network Security conversations space.
by Scott Muniz | Sep 11, 2020 | Uncategorized
This article is contributed. See the original author and article here.
Microsoft needs your help creating our learning and exam content. To facilitate this, we’ve created the SME Profile database where you can provide us with information about your skills and abilities. With the SME Profile database program, we can connect with SMEs who are passionate about Microsoft’s training and credentialing efforts. Through the program, participants can take part in exam and learning development activities such as courseware authoring, exam item writing, acting as technical reviewers, and participating in research. Perhaps the best benefit is getting special invites to participate in beta exams. SMEs in the database receive a special beta exam discount code that, while limited to a set number of seats, is only provided to that group. Being a member has its privileges.
Here are the basic steps:
- The SME Profile database is hosted as an engagement under the Microsoft Collaborate developer program. Joining requires a Microsoft account and registration to the developer site, so you’ll need to make sure you have an account.
- Join the Worldwide Learning SME Profile engagement on Microsoft Collaborate and complete your profile survey.
That’s it! OK, there are a few more steps required, but this is the basic gist. For step-by-step instructions (and lots of screen captures), download the attached PDF called Joining the SME Profile engagement on Microsoft Collaborate.
Many people on Microsoft’s Worldwide Learning team use the database to search for SMEs who can assist with content development—from creating courses to reviewing them to writing exam content to reviewing items and setting the passing score (really!)—and participating in research designed to define the direction we head as a learning organization. As an active participant in the SME Profile database program, you can have a say in what we teach, how we evaluate skills, and the future of our program. Not too shabby. But, I suspect that the reason you’ll join is because those in our SME database get a unique code to participate in beta exams (one that is not posted here), increasing the likelihood of getting a seat in that beta exam that you really want to take. Join today!
Joining the SME Profile engagement on Microsoft Collaborate_v2.pdf
by Scott Muniz | Sep 11, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
Special thanks to “Clive Watson” and “Ofer Shezaf” that collaborating with me on this blog post.
Due to the COVID-19 crisis, the usage of Office 365 has increased which introduces new security monitoring challenges for SOC teams. Increase usage means that the service should be more focal for defenders.
Over the past few mounts I have been working with my customers, on approaches to onboard Office 365 and related services into Azure Sentinel and the benefit of built-in solutions that a Cloud based Security Information and Event Management (SIEM) and Security Orchestration, Automation and Response (SOAR) bring, such as these use cases.
This blog post is built as a checklist and covers the following topics:
- Required data sources for Office 365 and related workloads
- Onboarding of data sources
- Visualizing data
- Using of out of the box Analytics Rules templates
- Hunting with Azure Sentinel
- Integration of 3rd party Threat Intelligence (TI)
- Data enrichment capabilities
- Automation with SOAR capabilities
- Integration with Ticketing Systems
- Integration with 3rd party SIEMs
Required data sources for Office 365 and related workloads
Choosing the right telemetry for Office 365 and related workloads depends on the enterprise’s security model. For instance, if an enterprise which follow the Zero Trust approach from Microsoft would focus on different telemetry than an enterprise with a classical security approach.
The following data sources should be the minimum onboarded to monitor Office 365:
In addition, the sources below are optional as they depend on additional licenses. Azure Sentinel can benefit from these expert systems and it is recommended to onboard if licensed or consider adding these to aid with detection and use cases.
- Azure Activity Directory Identity Protection alerts
- Office 365 Advanced Threat Protection and Threat Investigation and Response alerts
- Microsoft Cloud App Security alerts
Lastly, the following data sources are optional and would unlock more value by correlating different data sources using SIEM and SOAR capabilities.
- Logs from Domain Controllers and Azure Advanced Threat Protection alerts
- Telemetry from client devices
- Logs and alerts from Proxies and Firewalls
- 3rd Party Threat Intelligence feeds
Onboarding of data sources
Azure Sentinel comes with a several built-in and custom connectors to onboard Office 365 and related workloads.
GIFT Demonstration – Enable the Office 365 data connector:
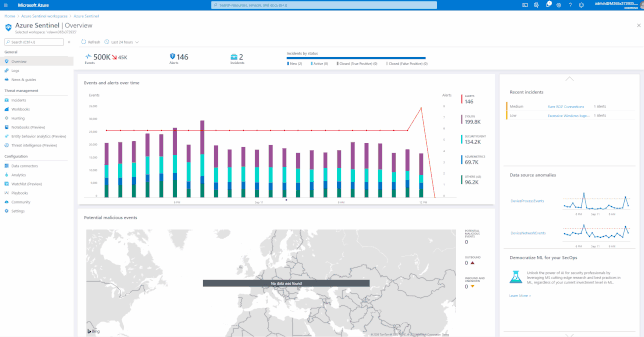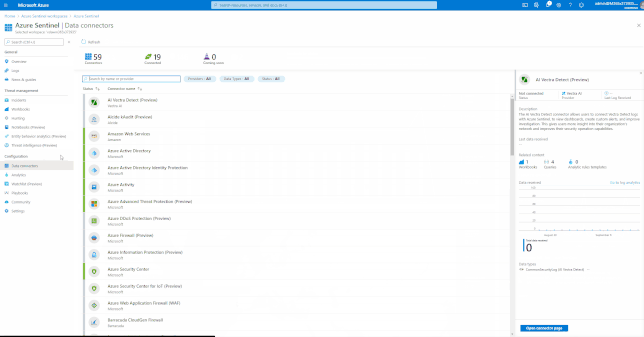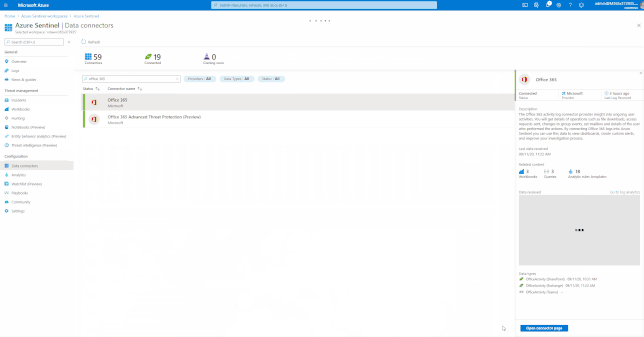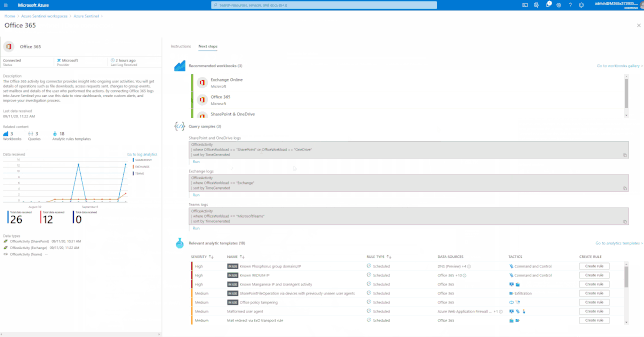
For a full list, please see, the Azure Sentinel Grand List.
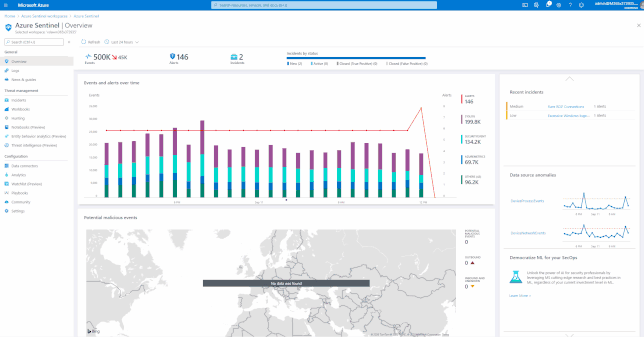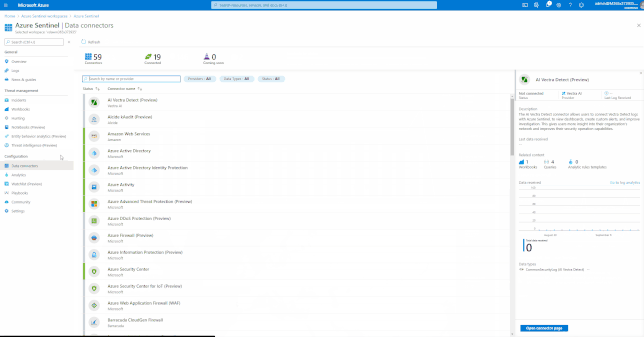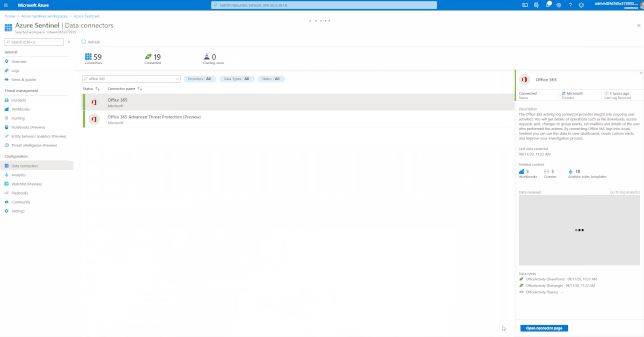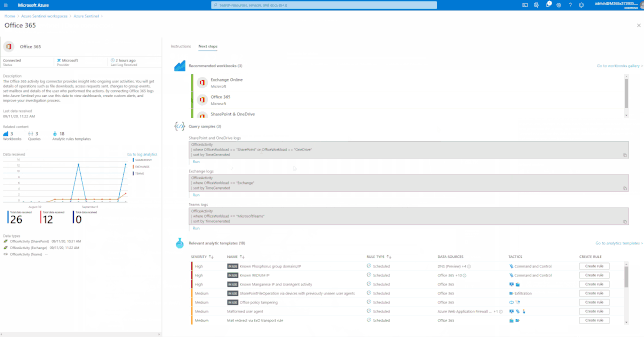
Visualizing data
Azure Sentinel has many built-in workbooks that provide extensive reporting capabilities analyzing your connected data sources to let you quickly and easily deep dive into the data generated by those services. The built-in workbooks can be changed and customized as needed. The Workbooks are provided by Microsoft, our data connector partners and the community.
These built-in Workbooks are available in Azure Sentinel for Office 365 and related workloads.
For more information and instructions on how to use Azure Sentinel Workbooks, please see:
Visualize your data using Azure Monitor Workbooks in Azure Sentinel | Microsoft Docs
In case you prefer to use Power BI for analytics and visualization:
Import Azure Monitor log data into PowerBI:
https://docs.microsoft.com/en-us/azure/azure-monitor/platform/powerbi
GIFT Demonstration – How to enable and use the Office 365 Workbook:
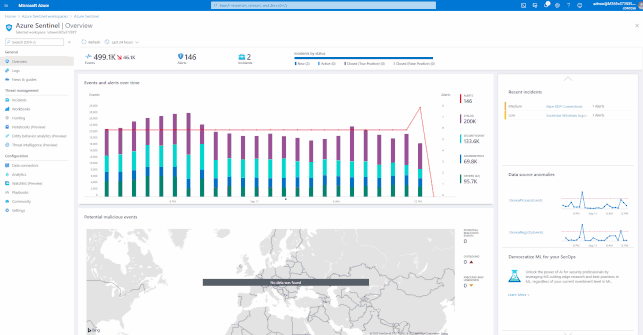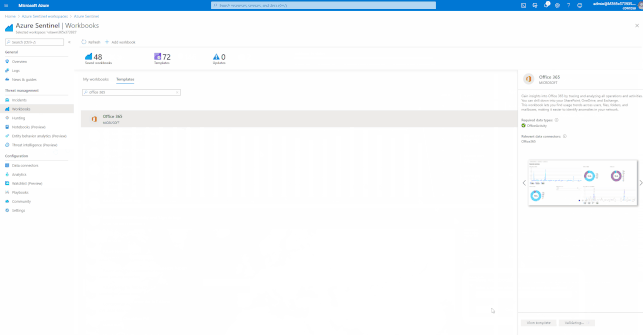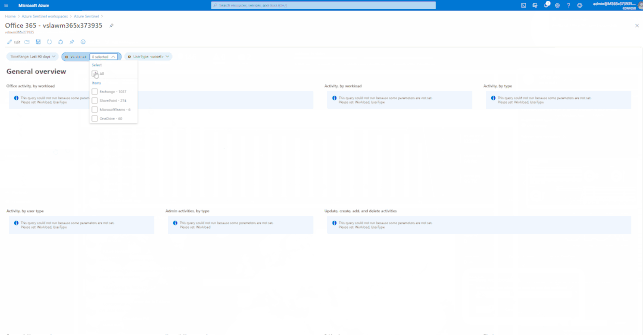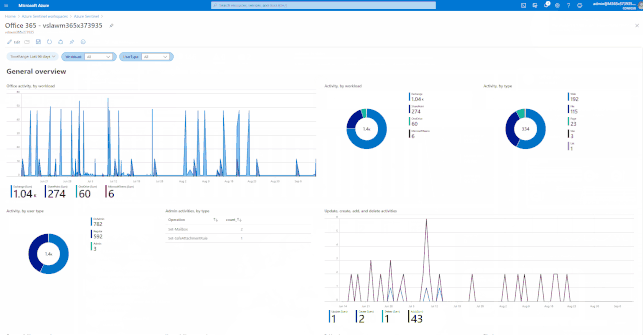
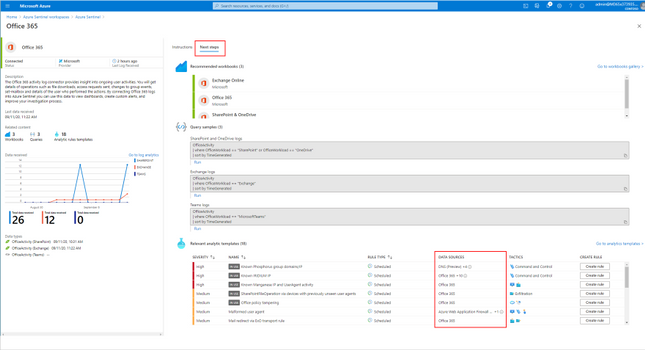
Using out of the box Analytics Rule Templates
Once you have connected your required data sources, you can use the Analytics Rule templates available in Azure Sentinel to generate incidents when certain criteria are matched. The Analytics Rules can be changed and customized as needed.
These Analytics Rule templates are available in Azure Sentinel for Office 365 and related workloads.
Tip: You see the related Analytics Rules (and required data) that match the connector on the “Next Steps” page of the “Add Connector” wizard.
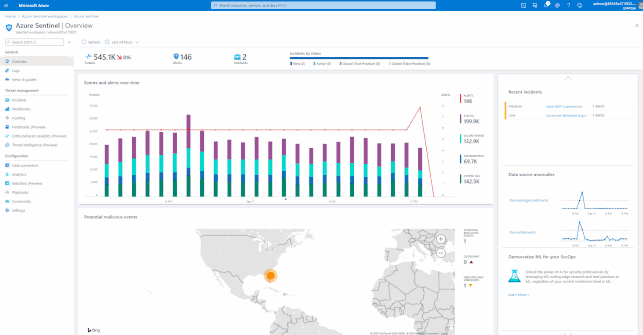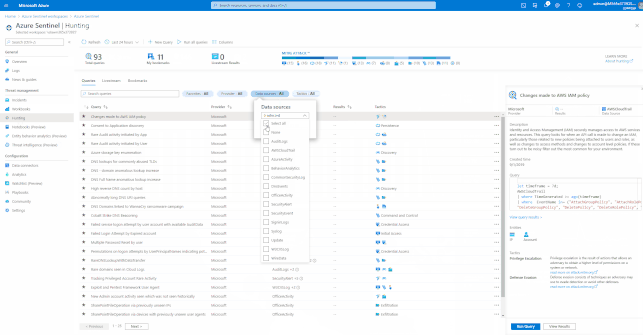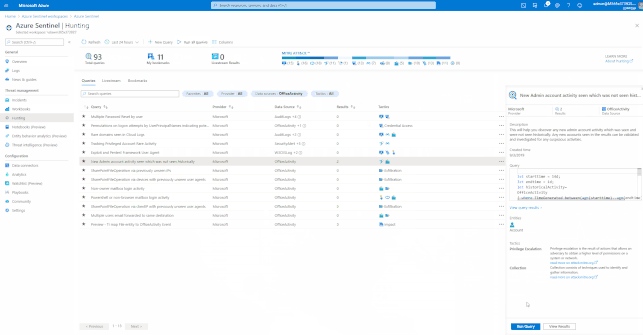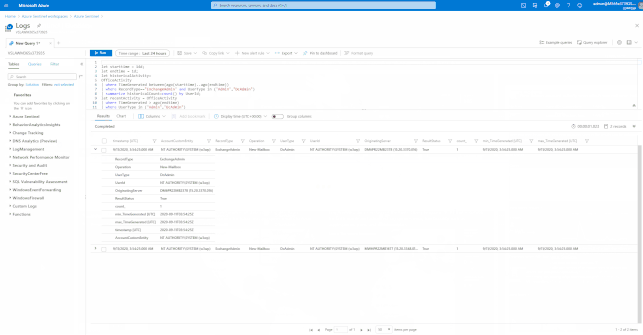
Hunting with Azure Sentinel
Azure Sentinel has built-in Hunting Queries to look proactively for new anomalies that you are not yet detecting with your Analytics Rules. You can use these Hunting Queries and Live Stream to create interactive sessions that let you test newly created queries as events occur, get notifications from the sessions when a match is found, and launch investigations if necessary. You can quickly create a livestream session using any Log Analytics query.
- Test newly created queries as events occur
- You can test and adjust queries without any conflicts to current rules that are being actively applied to events. After you confirm these new queries work as expected, it’s easy to promote them to custom alert rules by selecting an option that elevates the session to an alert.
These Hunting Queries are available in Azure Sentinel for Office 365 and related workloads.
GIFT Demonstration – Using the Built-In Hunting Queries for Office 365:
Integration with 3rd Party Threat Intelligence
Azure Sentinel lets you import you own threat intelligence indicators, which can enhance your security analysts’ ability to detect and prioritize known threats.
You can stream threat indicators to Azure Sentinel by using one of the integrated threat intelligence platform (TIP) products listed in the next section, connecting to TAXII servers, or by using direct integration with the Microsoft Graph Security tiIndicators API.
The Threat Intelligence data connector includes out of the box Analytics Rules and Hunting Query templates for Office 365 and related workloads.
Threat Intelligence Analytics Rules
Threat Intelligence Hunting Queries
Data enrichment capabilities
Data enrichment is key to associating data in context of enterprises. For instance, data enrichment would add additional information or context to the ingested logs to make it more valuable.
For Office 365 and related workloads Azure Sentinel provides these enrichment use cases:
Automation with SOAR capabilities
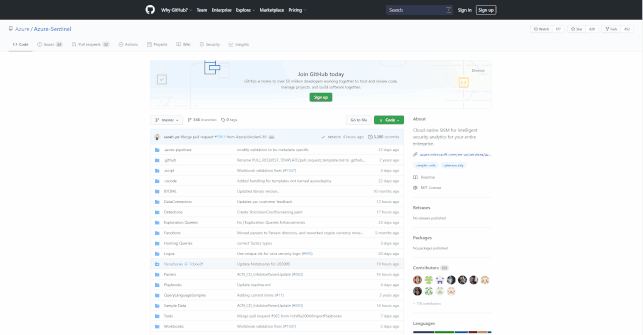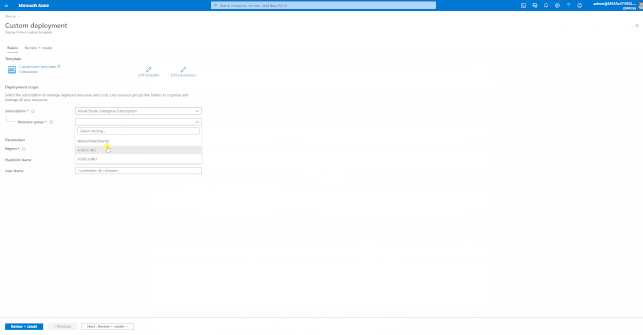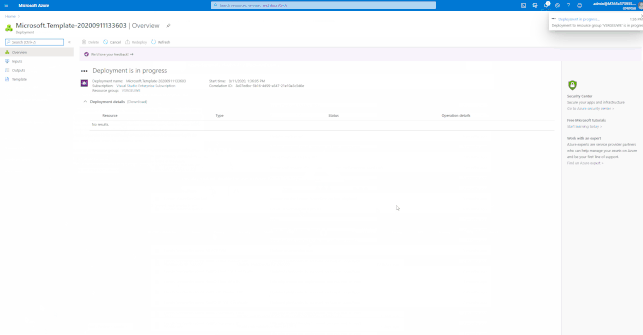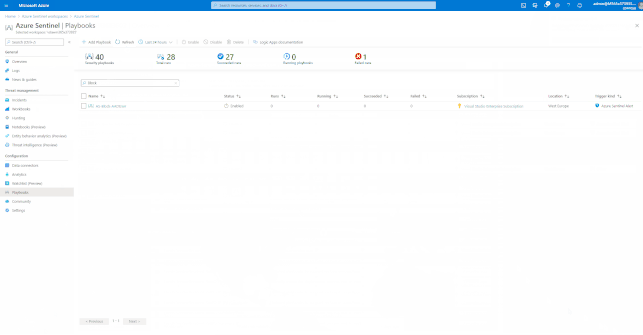
Azure Sentinel has built-in SOAR capabilities to orchestrate and automate common and complex tasks. Azure Sentinel uses Azure Logic App and Azure Function Apps for automation. Both services are built-in in Azure. The SOAR use cases are published here: GitHub, and can be deployment via ARM-Templates.
Using automation can save time, improve efficiency and help you improve your SOC (Security Operations Center) metrics and reduce the workload for the Securtity analyts.
https://docs.microsoft.com/en-us/azure/sentinel/manage-soc-with-incident-metrics
Azure Sentinel includes these automation solutions for Office 365 and related workloads:
GIFT Demonstration – How to enable the “Block Azure Active Directory User” Playbook:
Integration with Ticketing Systems
As part of the SOAR capabilities, Azure Sentinel support integration with ticketing systems. You can also just send a simple email or Teams message with the same data if you prefer (or do this in parallel with your Ticket).
Integration with 3rd Party SIEM
In case you are approaching Side-by-Side along with your exiting SIEM.
Summary
Ingesting of Office 365 alert logs are free, Azure Sentinel comes with a lot of use cases which help organizations to monitor and protect Office 365 workload, as well allows easy integration into existing SOC environment.
In this post we have covered the basics, looking at the data required, how to on-board connectors, how to manage Alerts, how to Hunt and automate responses to the results, and also connecting to 3rd party ticketing or SIEM solutions.
by Scott Muniz | Sep 11, 2020 | Uncategorized
This article is contributed. See the original author and article here.
Today, I worked on a service request that our customer needs to avoid that some users could retrieve some rows depending on a specific role. In this situation, we are going to use Is_RoleMember function.
For example, we have an Azure Active Directory group called MyAADGroup that contains all the users that we will have access to the data.
1) We are going to create the group in Azure SQL Database, running the following query:
CREATE USER [MyAADGroup] FROM EXTERNAL PROVIDER
2) We’re going to create the role, for example, auditors that will assign to the group MyAADGroup, running the following command:
sp_addrolemember 'auditors','MyAADGroup'
3) The next step, would be to create the security function, running the following command:
CREATE or alter Function [dbo].[fn_securitypredicateOrder] (@UserName sysname)
returns table
with Schemabinding
as
return select 1 as [fn_securityPredicateOrder_result] where IS_ROLEMEMBER('auditors')=1
4) Finally, we need to create the security policy running the following command:
create security Policy fn_securitydata
add Filter Predicate
dbo.fn_securitypredicateOrder(suser_name())
on MyTableDummy
Enjoy!
by Scott Muniz | Sep 11, 2020 | Uncategorized
This article is contributed. See the original author and article here.
Today, I worked on a service request that our customer needs to avoid that some users could retrieve some rows depending on a specific role. In this situation, we are going to use Is_RoleMember function.
For example, we have an Azure Active Directory group called MyAADGroup that contains all the users that we will have access to the data.
1) We are going to create the group in Azure SQL Database, running the following query:
CREATE USER [MyAADGroup] FROM EXTERNAL PROVIDER
2) We’re going to create the role, for example, auditors that will assign to the group MyAADGroup, running the following command:
sp_addrolemember 'auditors','MyAADGroup'
3) The next step, would be to create the security function, running the following command:
CREATE or alter Function [dbo].[fn_securitypredicateOrder] (@UserName sysname)
returns table
with Schemabinding
as
return select 1 as [fn_securityPredicateOrder_result] where IS_ROLEMEMBER('auditors')=1
4) Finally, we need to create the security policy running the following command:
create security Policy fn_securitydata
add Filter Predicate
dbo.fn_securitypredicateOrder(suser_name())
on MyTableDummy
Enjoy!




Recent Comments