by Scott Muniz | Sep 18, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
Introduction
Hello everyone, this is Andrew Coughlin and I am a Customer Engineer at Microsoft focusing on Azure IaaS. In this blog I will focus on a couple of questions I get quite often around Azure File Sync, does Azure File Sync support DFS-N, how do you set DFS-N with Azure File Sync and can I have two Azure File Sync servers in a DFS-N target folder.
Azure File Sync is a service that allows you to turn your on-premises servers into caching servers. All files in the directory you specify for Azure File Sync will be copied to a file share in a storage account. You can also enable a feature called Cloud Tiering, with this feature you can set which files stay on premises and which ones are in the cloud only. To the end user this feature is seamless, and they don’t know if their file is on the file server or in the cloud. For more information about Azure File Sync head over to the planning for an Azure File Sync deployment page.
Prerequisites
- Share the folders out on each server(s)
- Create DFS Namespace as documented here.
Does Azure File Sync Support DFS-N
One of the most common questions I receive is can you use Azure File Sync with Distributed File System Namespaces (DFS-N). A lot of corporate customers use DFS-N to hide the backend file server. This allows them to change the backend server without having impact to their end users. Azure File Sync does support DFS-N, from an interoperability it also supports Distributed File System Replication (DFS-R) for those customers looking to migrate away from DFS-R to Azure File Sync. Let’s see how we can add a share on an Azure File Sync server to DFS-N.
Add Share under Azure File Sync to DFS-N
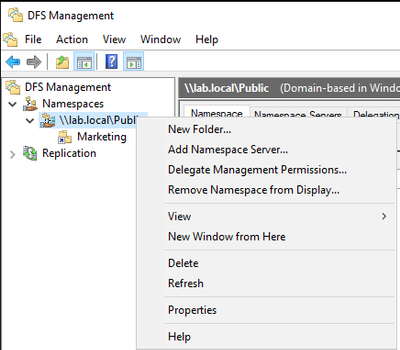
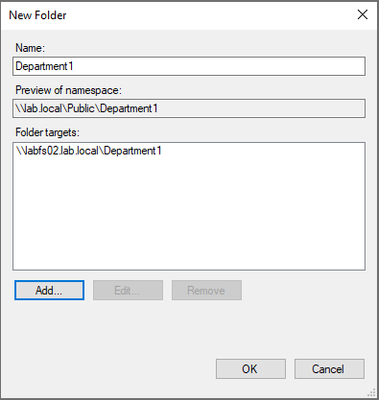
First, we will want to launch the DFS Management tool and connect to the name space if the name space doesn’t show up. Then we will right click on the name space and click “New Folder”.

Next you will provide the folder name and click Add.
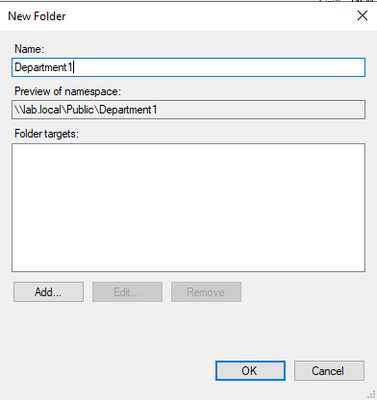
Then click Browse, type the Azure File Sync server, if needed, and select the folder and click OK.
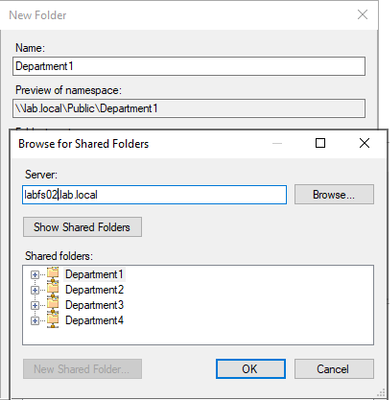
Click OK, on the Add Folder Target window.
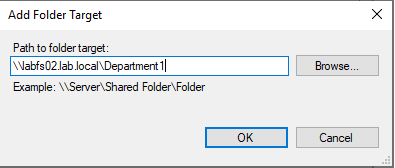
Click on OK, on the New Folder window.
Add Additional / New Azure File Sync Server to a Folder Target
There are a couple of reasons why you might want to add a second server to a folder target that has a share syncing with Azure File Sync:
- Two servers in different locations part of the same sync group
- DR purposes
- Retiring an older Azure File Sync server
NOTE: At the time of writing this article global locking is not supported for Azure File Sync or Azure Files.
To add an additional server to a target folder in DFS-N with Azure File Sync. First open DFS Management, find the folder you are wanting to add to the target folder and right click it and go to Add Folder Target.
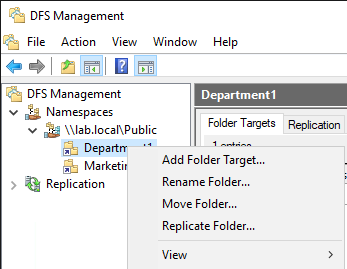
Click Browse, Type the second file server, and click Show Shared Folders. You will then select the shared folder and Click OK.
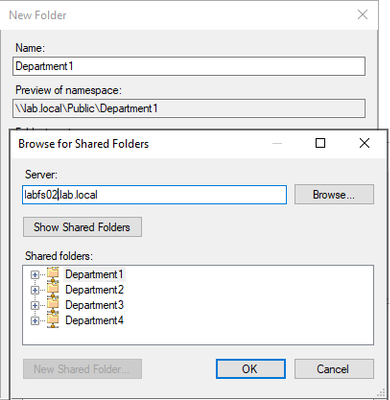
Click OK, on New Folder Target window.
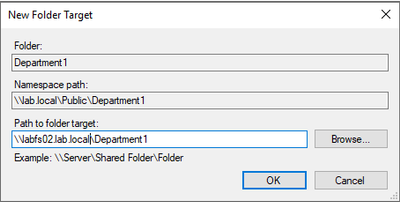
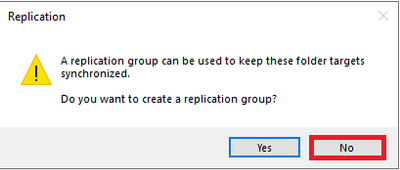
You will receive a replication message. This message is asking you if you want to setup a replication group. With two servers’ part of the same sync group we are using Azure File Sync to keep both servers synchronized. You will click No because of this.
NOTE: DFS-R and Azure File Sync can co-exist, the use case for this is for migrating from DFS-R to Azure Files, for more information about this migration process please see this link.
Conclusion
In this blog I covered supportability with Azure File Sync with DFS-N, how to add a server with Azure File Sync to DFS-N and how to add an additional server to a target folder in a DFS Namespace. Thank you for taking the time to read this blog, I hope this helps you and see you next time.
by Scott Muniz | Sep 17, 2020 | Uncategorized
This article is contributed. See the original author and article here.
Looking for a quick guide to Microsoft Endpoint Manager sessions, expert Q&As, deep dives, and more? You’ve found it!
The world changed what seems like eons ago, and Microsoft Endpoint Manager has helped make the IT side of those changes easier to navigate. With Microsoft Endpoint Manager, you can rely on the power of hybrid or cloud-based environment that can maintain fluidity and business continuity, all while delivering a great user experience—and the security you need to protect it all.
Where can you learn more? Microsoft Ignite 2020! This year’s conference is 100% remote, 100% virtual, and 100% free. That’s right! If you haven’t had an opportunity to attend Microsoft Ignite in the past – due to time, travel, or budgetary constraints – this is your chance!
Not only are we presenting digital breakouts (with live Q&A) and live Ask the Expert sessions, we are doing so with a global audience in mind so you can choose the time that works best with your schedule. We are also supplementing our live programming with on demand videos that dive deeper into the what, how, and why of each technology and capability—plus offering up some juicy post-event opportunities for those yearning for the pre-days of the past.
How do I access all these activities?
Register for free today and start building your schedule for the 48-hour live event. Click the hyperlinks below to add our live sessions to your schedule or save them to your digital “backpack” for reference later on.
Most importantly, make sure you bookmark this blog as we’ll be posting updates on day one (September 22nd), including links to all the on demand sessions you see listed below.
Now let’s get to what’s on the agenda for Microsoft Endpoint Manager at Microsoft Ignite 2020!
|
Digital breakouts (with live Q&A)
|
|
Session name
|
Times offered (duration: 30 min.)
|
|
Playing chess on a trampoline: How to innovate in an era of uncertainty (Brad Anderson)
|
Tues. Sept 22,
11:30 AM PST
|
Tues. Sept 22,
7:30 PM PST
|
Wed. Sept 23,
3:30 AM PST
|
|
Building a resilient organization on Microsoft 365 (Catherine Boeger)
|
Tues. Sept 22,
12:15 PM PST
|
Tues. Sept 22,
8:15 PM PST
|
Wed. Sept 23,
4:15 AM PST
|
|
Windows 10 innovations for enhanced productivity and resiliency (Joe Lurie and Karen Simpson)
|
Tues. Sept 22,
1:45 PM PST
|
Tuesday Sept 22,
9:45 PM PST
|
Wed. Sept 23,
5:45AM PST
|
|
Introducing modern admin capabilities to better service Microsoft 365 Apps for enterprise (Aleš Holeček)
|
Wed. Sept 23,
11:30 AM PST
|
Wed. Sept 23, 7:30 PM PST
|
Thurs. Sept 24,
3:30 AM PST
|
Looking to dive deeper into the topics covered in our digital breakouts? We’ll have a variety of technical overviews and deep dives available in the Video Hub on Tech Community—direct from our engineering and product teams!
|
Video Hub (links available on September 22nd)
|
|
Get started with Microsoft Endpoint Manager (Joe Lurie & Mayunk Jain)
|
|
Managing Windows devices with Microsoft Endpoint Manager and Windows Autopilot (Michael Niehaus & Miz Rahman)
|
|
Managing Apple devices with Microsoft Endpoint Manager (Tiffany Silverstein & Arnab Biswas)
|
|
Managing Android devices with Microsoft Endpoint Manager (Esther Salter & Courtenay Bernier)
|
|
Configuring zero trust with Microsoft Endpoint Manager (Matt Shadbolt & Clay Taylor)
|
|
What’s new in Microsoft Endpoint Manager. Part 2 (Steve Dispensa & Ramya Chitrakar)
|
|
Flexible paths to cloud management with Microsoft Endpoint Manager (Rob York)
|
|
Endpoint analytics deep dive: putting the end-user experience front and center (Zach Dvorak)
|
|
Microsoft Endpoint Manager Configuration Manager Deep Dive (Rob York, Jason Githens, David James)
|
|
Secure and deploy Microsoft 365 mobile apps for productivity, collaboration, email, and browsing (Ross Smith & Shiv Patel)
|
|
Unify endpoint security management with Microsoft Endpoint Manager and Microsoft Defender ATP (Matt Shadbolt & Dilip Radhakrishnan)
|
|
Introducing Microsoft management tools to secure and manage work from home (Matt Shadbolt & Scott Duffey)
|
|
Setting up Windows Update for Business via Microsoft Intune (Aria Carley & Dune Desormeaux)
|
|
Enabling remote management with Cloud Management Gateway & Cloud Attach (Danny Guillory)
|
|
Securing Teams with Microsoft Endpoint Manager (Mayunk Jain & John Gruszczyk)
|
|
What’s new in Microsoft Intune for Education (Liz Cox)
|
|
Eliminate on-premises print servers with Universal Print (Saurabh Bansal & Jimmy Wu)
|
|
Intune App Protection Policies with policy assurance (Ross Smith)
|
|
Microsoft Endpoint Manager Reporting Graph APIs and Log Analytics (Spencer Shumway)
|
|
Modern policy management for security and productivity (Aasawari Navathe & Laura Arrizza)
|
|
Enable security and productivity quickly using Microsoft Endpoint Manager (Lance Crandall & Tyler Castaldo)
|
|
Deep dive into Role Based Access Control (RBAC) in Intune (Pallavi Joshi)
|
|
Accelerating the journey to modern management (Chris Sweeney)
|
Post-event activities
Post-conference: Manage, Configure, and Secure Devices with Microsoft Endpoint Manager
We are offering a special, one-day post-conference event for those seeking to roll up their sleeves and dramatically increase their endpoint management IQ on Tuesday, September 29th from 10:00 AM to 6:00 PM Australian Eastern Standard Time (AEST). The event will take place in two, four blocks with a Windows devices track and a mobile devices track. Click here to register!
Additional resources
For a closer look at sessions and resources related to Microsoft 365 Admin Tools and Experiences, see the Microsoft 365 Admin Guide to Microsoft Ignite 2020.
To see what’s what at Microsoft Ignite 2020 related to Windows deployment and servicing: https://aka.ms/MicrosoftIgnite2020/Windows
For the latest in all things Office and Microsoft 365 Apps, bookmark: https://aka.ms/MicrosoftIgnite2020/Office
I’ll personally be moderating some of the Ask the Experts sessions, and monitoring comments on Tech Community, so I look forward to “seeing” you at Microsoft Ignite!
by Scott Muniz | Sep 17, 2020 | Uncategorized
This article is contributed. See the original author and article here.
It’s that time of the year again!
Microsoft Ignite 2020 is here to give you early access to the latest product developments and news with guidance from Microsoft experts and your worldwide community. This year’s event will be all digital, taking place over 48 hours from September 22-24.
To help you manage the change to an all virtual event, and navigate the hundreds of videos published during this timeframe, please review the guide below for important content related to Microsoft Stream.
While this content is being made available during the Ignite timeframe, it is meant to serve as foundational learning material beyond the scope of the event. As a result you will not see Ignite specific branding, but rest assured this is the most up-to-date and in-depth content; all delivered by our Microsoft subject matter experts as you have hopefully come to expect from Microsoft Ignite.
Stream sessions
Video is central to modern communications and empowers people to connect authentically, share knowledge, and to drive communication, training and employee engagement.
The sessions below will explore ways you can get the most out of video with Microsoft Stream:
Microsoft Stream also features in other Ignite sessions. If you’re curious to learn why, you should check out the sessions below:
- DB158 | “Enabling collaboration, communication, and knowledge sharing with Microsoft Teams, SharePoint, Project Cortex, and more” by Jeff Teper, CVP – SharePoint, OneDrive, and Teams engineering (delivered three times):
- KEY04 | “The Future of Work” by Jared Spataro, CVP – Microsoft 365 marketing (delivered three times):
- DB150 | “Employee Engagement and Communities in Microsoft 365” by Dan Holme and Murali Sitaram – VP Yammer+M365 Groups (delivered three times):
We look forward to seeing you at this year’s Ignite!
by Scott Muniz | Sep 17, 2020 | Uncategorized
This article is contributed. See the original author and article here.
2020 has been a year of change, including our approach to Microsoft Ignite. The event will be entirely virtual this year, taking place over 48 hours from September 22-24.
To help you manage this change in approach and navigate the hundreds of videos published during this timeframe, please review the below guide for important content related to Network Connectivity. While this content is being made available during the Ignite timeframe, it is meant to serve as foundational learning material beyond the scope of the event. As a result you will not see Ignite specific branding, but rest assured this is the most up to date and in-depth content; all delivered by our Microsoft subject matter experts as you have hopefully come to expect from Microsoft Ignite.
As you review the content below, make sure to add the Microsoft 365 Network Connectivity Office Hours to your calendar. It’s on Wednesday, Sept 23rd from 8am – noon PST. Please drop in any time to ask our panel of network experts your questions. Set a reminder on your calendar now, and visit aka.ms/nettalk for details on how to join.
Pages to know:
Optimizing Microsoft 365 network connectivity – Aka.ms/netvideos
If you are interested in the Microsoft 365 network connectivity topic – you should bookmark this page. Not only will all the latest video content from Ignite be posted here, but you’ll find links to the most important Microsoft network configuration resources and guidance on how to handle critical topics like remote work or Zero Trust security. This is a recently launched page and going forward will serve as the central hub for updates and information regarding Microsoft 365 network connectivity.
Interactive guide: Configure your network for Microsoft 365 and Teams – aka.ms/MSLearnNetworkM365
Launching on Sept 18th, this interactive guide provides step by step instructions to configure your network for optimal connectivity to the Microsoft 365 suite, with a focus on Teams. As more organizations adopt Microsoft Teams, we’ve seen increasing demands for guidance on how to get the best experience with native in-platform experiences that are performance sensitive – like video/audio conferencing, document co-editing, chat, and search. Use this guide to ensure your users have the best Teams experience possible.
Network connectivity discussion forum
Use this discussion forum to ask questions, see hot topics from your peers, and engage directly with our Microsoft 365 networking experts. See the latest post from Paul Andrew, Microsoft 365 Principal Program Manager, on the new features of the connectivity.office.com network assessment tool.
Core content videos:
Topic: Overview of Network Connectivity Principles
Speaker: Konstantin Ryvkin, Microsoft 365 Partner Architect
Location: aka.ms/netvideos
Learn about the Microsoft 365 Network Connectivity Principles, which serve as foundational elements to achieve optimal network connectivity and most performant user experience with Microsoft 365. Learning about these key principles can help ensure your network strategy and design choices are optimal for your Microsoft 365 users, competitive in the marketplace, and future proof to the constant evolution of the cloud.
Topic: Microsoft’s enterprise network design for the cloud era
Speaker: Paul Collinge, Microsoft 365 Senior Program Manager
Location: aka.ms/netvideos
This video discusses why a traditional enterprise network built for the on-premises world isn’t a good fit for a cloud-first world. We’ll look at some of the common modern enterprise network design models which our customers are using to achieve great performance, agility, security—and often cost savings. We will also cover how Microsoft 365’s design and network principles lend themselves well to this approach.
Topic: Microsoft 365 network connectivity for remote users
Speaker: Roshan Padmanabhan, Microsoft 365 Senior Program Manager
Location: aka.ms/netvideos
In this video we will discuss Microsoft 365 network connectivity best practices for remote users working from home, we will go through remote connectivity strategies like VPN split-tunneling to facilitate continued user productivity during large scale work from home events such as the COVID-19 pandemic.
Topic: Microsoft 365 Networking Partner Program
Speakers:
John Mighell, Microsoft 365 Senior Product Marketing Manager
Fraser Street, Silver Peak, VP Technical Alliances
Ritesh Mukherjee, 128 Technology, Vice President Product Management
Joseph Chung, VMWare, Director Strategic Alliances
Location: aka.ms/netvideos
Customers often ask Microsoft if partner solutions work with Microsoft 365 and whether they align with Microsoft’s Network Connectivity Principles. This session will review our Networking Partner Program and explain how we designate verified partner solutions that can help optimize your network connectivity.
Topic: How Microsoft does Zero Trust
Speakers: Mark Simos, Microsoft Lead Cybersecurity Architect; Lesley Kipling, Microsoft Chief Security Advisor
Location: aka.ms/netvideos
Learn about Microsoft’s approach to Zero Trust within the context of network configuration. Research shows that the Zero Trust concept is used to discuss very different approaches to the same problem and it is often left to the organization to determine which approach is best for their environment. In this session, we’ll outline an approach that details 4 critical categories that evolve the discussion from “Trust but verify” to “Verify everything, trust nothing” including the network.
Topic: Managing connections using the IP/URL web service [NOTE: will be available 9/22]
Speaker: Jeff Mealiffe, Microsoft 365 Principal Architect
Location: aka.ms/netvideos
In this video, we will explain how Microsoft publishes details on the service endpoints across Microsoft 365 workloads, and how you can consume these details to keep your infrastructure configuration up to date and ensure the best possible experience for your users.
Topic: Microsoft 365 network connectivity testing tools [NOTE: will be available 9/22]
Speaker: Paul Andrew, Microsoft 365 Principal Program Manager
Location: aka.ms/netvideos
For large enterprises Microsoft 365 connectivity often requires different network perimeter design than generic Internet connectivity. We publish connectivity principles and best practices for optimizing network perimeters for Microsoft 365. This session will show tooling that is available for testing against those connectivity principles and it will evaluate network connectivity for impact on Microsoft 365 user experience. Passive network measurements from Microsoft 365 clients are shown in the Microsoft 365 Admin Center. Active testing can be run using the Microsoft 365 Network Connectivity Test tool which is available at https://connectivity.office.com. This talk will review the test tools, describe when you would use them, and explain the output and what you can learn from them using demos. We will look at network latency, DNS configuration, download speed, network media elements, home VPN configuration, and more. Take a look and you’ll learn how to get the most out of your network perimeter supporting Microsoft 365 user experience.
![[Updated 2020] Introducing the SensorExplorer App](https://www.drware.com/wp-content/uploads/2020/09/medium-94)
by Scott Muniz | Sep 17, 2020 | Uncategorized
This article is contributed. See the original author and article here.
How to get the app
1. From the Microsoft Store: Search “SensorExplorer” or follow this link https://aka.ms/sensorexplorer
2. From GitHub: Go to https://aka.ms/sensorstrace, the app package is available inside the SensorExplorer folder for sideloading.
* The source code is available at https://github.com/Microsoft/busiotools/tree/master/sensors/SensorExplorer/code/SensorExplorer
Overview
SensorExplorer is an app available on the Microsoft Store (https://aka.ms/sensorexplorer) and the app package can be accessed through GitHub (https://aka.ms/sensorstrace). The app offers tests that allow you to quickly verify the installation of supported sensors such as orientation sensors (accelerometer, simple orientation sensors, etc.), and detailed tables and plots that enable you to monitor different sensors. In addition, logs can be conveniently saved later for debugging.
There are three modes (menu bar on the left-hand side) in SensorExplorer:
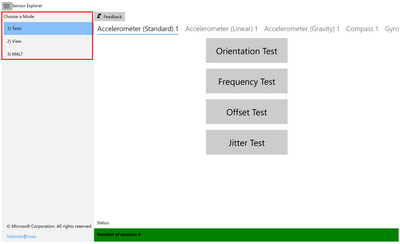
1. Test: This mode is used for manual testing of supported sensors. The orientation test verifies orientation sensors are installed in the correct position and the sensor data is as expected. Other tests, such as frequency, offset and jitter test, are also available. The sensor data is read using the UWP Sensors API (Windows.Devices.Sensors: https://docs.microsoft.com/en-us/uwp/api/Windows.Devices.Sensors).
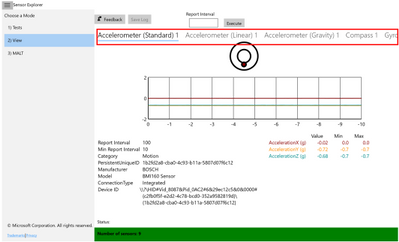
2. View: This mode is used for viewing sensor data and properties. In this mode, the app displays a data visualization from a variety of sensors (such as accelerometer, compass, gyrometer, inclinometer, light sensor, and orientation sensor, etc.), and shows detailed sensor information in tabular format. It can help you monitor the abnormal behaviors of the sensors, and you can also use this mode to set the report interval of sensors.
3. MALT: This mode is used for connecting to and controlling MALT (Microsoft Ambient Light Tool), a simple low-cost light testing apparatus. The tool combines a microcontroller, light sensors, and a controllable light panel to calibrate light sensors and visually measure a panel’s light curve.
How to test your sensors
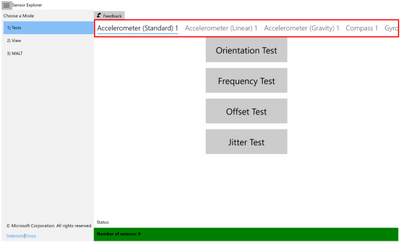
You may explore what tests are available for each sensor on your system by scrolling the top menu bar (highlighted in the screen shot below as a red box).
1. Orientation test
This test asks you to orient the device in different directions and then checks the sensor reading accordingly.
A pass/fail result will be displayed at the end of the test.
1.1 Before you begin the tests
- Under the test mode, if you find that the display rotates when you rotate your device, please turn off auto-rotation on your device (Search “Rotation Lock” in Settings and turn it on). Otherwise, you do not need to turn off auto-rotation.
- Please refer to the Device Reference Frame section found in the whitepaper at https://msdn.microsoft.com/en-us/library/windows/hardware/dn642102(v=vs.85).aspx) for more information on orientation and reference frame.
1.2 During the tests
- Click the “Start” button to begin the tests.
- For each test, you have 10 seconds to orient your device so that the arrow on the screen is pointing down toward the ground.
Note:
(1).You may click the icon (highlighted in the screen shot below as a red box) to hide the menu bar during the test.
(2). The menu bar is disabled during the test and will be enabled once the test finishes.
(3). For the Simple Orientation Sensor, the four directions tested are face up, face down, left, and right. For all other sensors, the four directions tested are up, down, left and right.
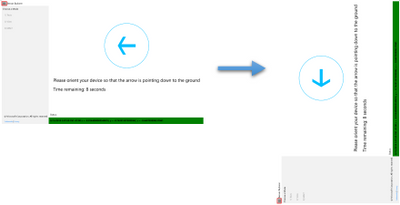
- Once the sensor data reflects that your device is indeed in the desired orientation, a green checkmark will be displayed. And you will automatically move on to the next test.

- Otherwise, after 10 sec, a red x will be displayed as this round of tests has failed.

1.3 After the tests
- Click the “Save Log” button to save the log file(data for all rounds of tests will be saved).
- Or click the “Restart” button to start another test.
2. Frequency Test
This test calculates the number of sensor readings received/60 seconds.
A numeric value will be displayed at the end of the test.
3. Offset Test
This test calculates the average error in sensor readings compared with the expected value.
A numeric value will be displayed at the end of the test.
4. Jitter Test
This test calculates the maximum difference in sensor readings during a period of time, compared with the initial reading.
A numeric value will be displayed at the end of the test.
5. Resolution Noise Density Test
This test checks actual sensor resolution and noise of the physical accelerometer sensor in the device.
A numeric value will be displayed at the end of the test.
How to monitor your sensors
The View mode will automatically detect any sensors that are attached to or embedded in your platform. It will then display the information that it reads from the sensors.
1. View
- You may scroll the top menu bar (highlighted in the screen shot below as a red box) to change the sensor being displayed.
- For each sensor, the current data and properties are shown in a table and plotted as moving waveforms.
- The report interval of a specific sensor can be changed here.
More on Logging
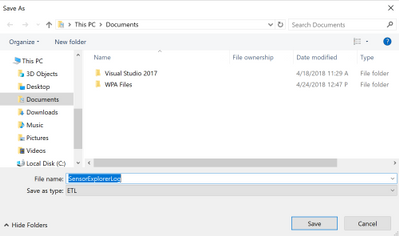
When you click the “Save Log” button, you may choose the location to save the log file. The default name of the ETL (Event Trace Log) file is “SensorExplorerLog”, but you may change it.
To view the ETL file, you may use the tracerpt command (https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/tracerpt_1).
1. Test
The following will be logged:
- Properties of the selected sensor
- Information about each test
- For orientation test:
- The sensor reading when you pass a test
- The last sensor reading before the countdown ends, in the case you fail the test
- For other tests:
- All sensor readings collected during the test
- The final result
Future Work
Some of the functionalities that we are planning to add to SensorExplorer include:
- Integrate all functions of MALT (Microsoft Ambient Light Tool)
- Other types of sensor tests
- Improve logging infrastructure
by Scott Muniz | Sep 17, 2020 | Uncategorized
This article is contributed. See the original author and article here.
In the modern workforce, the emergence of hybrid cloud deployments and collaborative applications make it easy for employees to share information, data, and files with other internal as well as external users, helping them collaborate easily with vendors, business partners, contractors and customers. Managing all the access across different resources – Office groups, Teams, SharePoint sites, as well as your own applications and SaaS applications – is challenging. As requirements change with new applications being added, or users needing additional access rights, IT staff may not know who should have access or to which applications. To succeed at scale, an identity governance process must enable all users’ access to be able to change with their needs, without burdening IT staff to be involved in each access request.
Azure AD entitlement management, a feature of Azure AD identity governance, helps organizations manage their access lifecycle at scale by automating request workflows, assignments, reviews, and expiration. You can empower users to request access to the resources they need. These requests and the resulting access can be approved and regularly reviewed by people across the organization who know whether someone should still have access
Here are some common questions we’ve received from customers about how to manage employee access.
Question 1. In the past we’ve configured that our AD- and ADFS-connected applications were open to everyone in the directory to access, as we only had employees and vendors in our AD. Now that we’ve moved these applications to Azure AD, we want to lock down access to those apps and move to app assignments so that users don’t inadvertently have access. What are the best ways to manage application assignments to make sure users don’t have access they don’t need?
Azure Active Directory (Azure AD) supports multiple approaches for access management for your own applications, including SaaS apps, cloud-based federation-based apps and on-premises AD-connected applications via the Azure AD app proxy, enabling organizations to easily achieve the right balance of access policies ranging including automatic, attribute-based assignment, as well as delegated assignment.
As described in the article managing access to apps, traditionally access management starts with either individual assignment, one for each user, or group-based assignment. Group–based assignment works well if you have an existing security group that you could re-use. However, keeping the membership consistent could be challenging if you have multiple applications. Suppose a user named Alice, and others in the same department as her, need access today to two apps. If there’s a group that has Alice and the other users as members, you could assign that group to those two apps. However, if Alice no longer needs one of the apps, that would require restructuring the groups to avoid audit findings of users having excessive access, and could lead to a proliferation of groups, potentially as many as there are apps.
Another way to manage access to applications is for the users to receive entitlement management assignments for an access package that includes those applications and have those assignments set to expire or be regularly reviewed. Through Azure AD entitlement management in the Azure portal, an administrator or a resource owner can create an access package with one or more applications. A user can request access to that access package through the myaccess.microsoft.com UI, or an access package catalog owner can assign access to users in the Azure portal. You can also have users request or create assignments programmatically, through Microsoft Graph, as shown in the tutorial for how to create an access package using Microsoft Graph APIs. When a user is approved for access to the access package, they are assigned to the application.
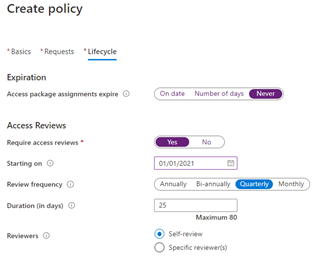
You can ensure that users do not have access indefinitely by configuring automatic access reviews as part of the policy. You could have different policies for different collections of users so that their review schedule is based on the likelihood of the user no longer needing access or the risk of inadvertent continued access. Each policy in an access package can have a different access review frequency for reoccurrence or different reviewers.
 The “Create policy” screen in the Azure portal for an Azure AD access package, showing the lifecycle tab in which quarterly reviewing access reviews are required.
The “Create policy” screen in the Azure portal for an Azure AD access package, showing the lifecycle tab in which quarterly reviewing access reviews are required.
For example, you could have one policy that gives users in the IT department a shorter maximum duration of access as they’re performing administrative tasks and another policy from users in other departments.
Question 2. What about giving users access to Office 365 and other Microsoft applications? Not everyone in the directory has a license, and we don’t have relevant data in our HR system to be able to create a dynamic group of just those people who need a license.
For applications in Office 365 or other paid suites, users can be granted access through license assignment either directly to their user account or through a group using the group-based license assignment.
Combining group-based licensing and entitlement management for users to request an access package that results in license assignments simplifies giving users licenses they need.
First, in the Azure portal, create an Azure AD security group, and configure that group to give license assignments.
Then, create an access package containing membership in that group as a resource. If you select to have the requestor’s manager as approver in the policy, then each requestor’s manager can decide if the requesting user has a need for the license for these applications.
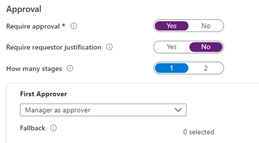 The “New access package” screen in the Azure portal, for a policy configuring manager as approver.
The “New access package” screen in the Azure portal, for a policy configuring manager as approver.
Once a user requests and is approved, they’re automatically added to the security group, and Group-based license assignment gives them a license.
In access packages which give licenses, you may wish to configure a long duration prior to access package expiration or a “Never” setting with access reviews to avoid a user inadvertently losing their access package assignment and their use of Office while on vacation or on leave.
Question 3. As we roll out Office groups and Microsoft Teams in our organizations, employees may inadvertently try to join public teams that sound relevant but aren’t the appropriate team for them. How can we cut down on unnecessary work for teams owners to approve requests and maintain their memberships?
An organization can publish a curated collection of teams that they want to make available for users to join by creating access packages for each one (they can include multiple teams in a single access package as well). They can then configure the requestor’s manager as needed for approval, approval by a departmental list of approvers, or both. Once approved, the user is then added to the Office group and team, and can collaborate.
For example, if it wasn’t known in advance everyone who might need to be a member of a team, such as for a marketing launch, the marketing department could create the team as private. Next, the team owners could manually add or share a code with those individuals who are known and likely to need to be part of that team.
To bring in the rest of the necessary members from other departments who aren’t known but avoid users being added who do not have a business requirement, they could create an access package for that team.
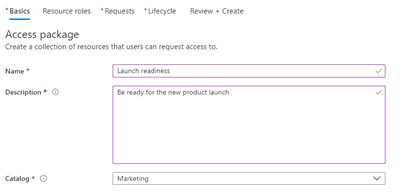 The “New access package” screen in the Azure portal.
The “New access package” screen in the Azure portal.
If there are additional resources, such as a SharePoint Online site or applications, those could be added to the access package as well.
The policies for the access package could scope to only allowing certain users to request access, and could also require approval by both the requestor’s manager, and by the members of a departmental group.
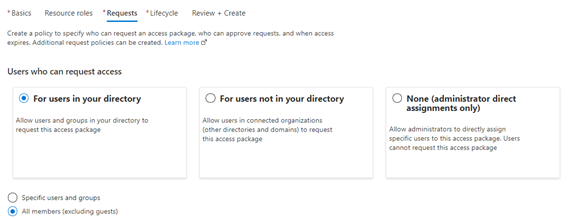 The “New access package” screen in the Azure portal, creating a policy for all member users to be able to request.
The “New access package” screen in the Azure portal, creating a policy for all member users to be able to request.
The first stage would specify the manager as approver. You can also configure a fallback approver for requestors who don’t have a manager.
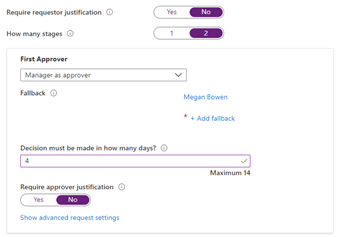 The “New access package” screen in the Azure portal, setting the first approver stage in a multi-stage approval workflow.
The “New access package” screen in the Azure portal, setting the first approver stage in a multi-stage approval workflow.
And the second stage could have a different approver, such as members of a group.
The assignments created through that access package could also be set to expire automatically on a predefined date, to avoid users remaining in the team indefinitely.
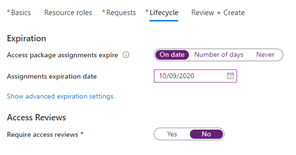 The “New access package” screen in the Azure portal, setting the access package assignment lifecycle for the policy.
The “New access package” screen in the Azure portal, setting the access package assignment lifecycle for the policy.
Furthermore, additional resources that users might need access to,including access to SaaS applications, in-house developed applications, other existing security and Office groups, and SharePoint Online sites, can be added to the access package. Users with assignments to the access package will then automatically be given access to those resources as well.
To find out more about Azure AD identity governance, including access reviews, privileged identity management, and how to manage the lifecycle of business partner guests see What is Azure AD identity governance? and What is Azure AD entitlement management?. There are also case studies for how digital innovator Avanade chose Azure AD Identity Governance for streamlined, highly secure collaboration and how the leading energy and services company Centrica solved collaboration challenges with Azure Active Directory entitlement management.





Recent Comments