by Scott Muniz | Sep 21, 2020 | Uncategorized
This article is contributed. See the original author and article here.
Need insight on how your applications will perform with the next release of Windows 10—prior to it being available in market? Don’t want to maintain an environment to validate new Windows features? Want to run your validation tests against Windows Insider Program builds in our Azure environment?
Feature update validation on Update Staging Lab can help you achieve all these and more!
Check out the step-by-step outline below to find out how to access this new capability in the Update Staging Lab service. (Not yet taking advantage of Update Staging Lab? Sign up here to join the preview.)
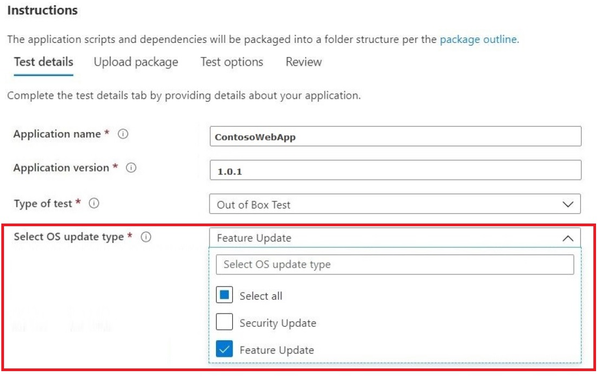
To get started with feature update validation in Update Staging Lab, upload your applications (and related files) through the self-service onboarding portal. As you fill out the Test details:
- Select Feature Update as your OS update type:

- Choose the Windows Insider Channel against which you want your application validated. (We currently support the Insider Beta Channel.)
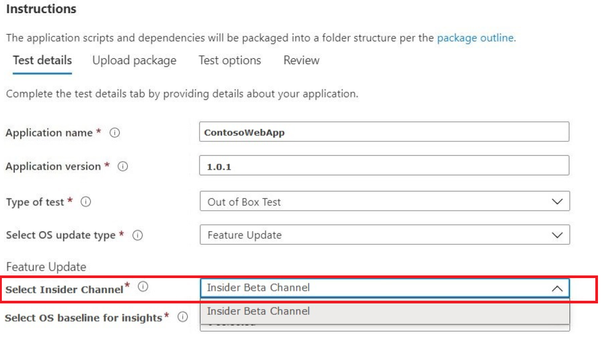
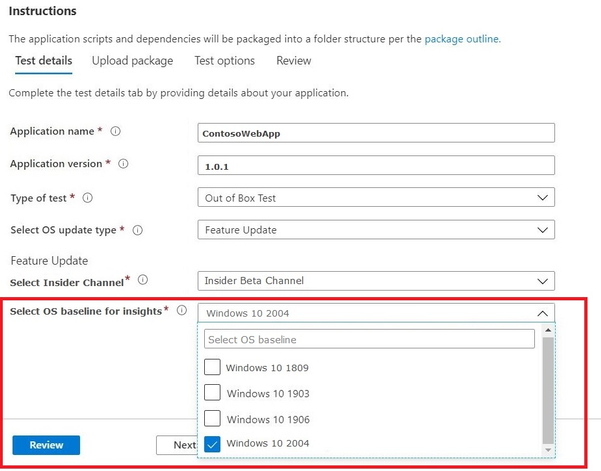
- Select an in-market release of Windows 10 as the baseline for your test (and resulting insights!) and provide the other details required to onboard your package successfully.
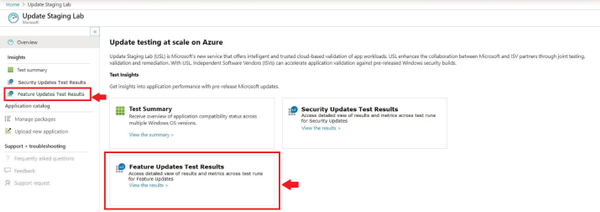
- To view the results and insights from the validation of your application against pre-release Windows 10 feature updates, visit Feature Updates Test Results.
We look forward to hearing your comments/feedback on this new feature as we enhance and evolve our service to meet your validation needs. You can also email us at USLPreview@microsoft.com.
by Scott Muniz | Sep 21, 2020 | Uncategorized
This article is contributed. See the original author and article here.
You have been challenged to support your organization with the enormous shift to remote work (and back again) and keep everyone protected and productive. Come see how we can help you manage your Office apps and keep them up-to-date with greater simplicity and control. From managing multiple update channels to security mitigations, this year’s sessions at Microsoft Ignite 2020 contain gems for anyone wanting to ramp things up, streamline, or just plain learn.
All our digital breakouts and live Ask the Expert sessions are offered with a global audience in mind, so choose the times that work best with your schedule. Simply register at Microsoft Ignite—if you aren’t already—and use our handy guide below to build your schedule. We’ll keep adding content to this blog post so come back to us on day one for quick links to the on demand sessions and more!
While there are many sessions on specific Office products and capabilities, here is the quick list of the ones that will help you optimize the way you manage and service Microsoft 365 Apps as a whole.
|
On demand sessions (links available on September 22nd)
|
|
Featured session:
Office Apps and Teams: Enabling virtual collaboration for the future of our hybrid work environment (Shalendra Chhabra)
|
|
Best practices for deploying Microsoft 365 Apps (Martin Nothnagel)
|
|
How to keep users secure and productive with Microsoft 365 Apps (Sriram Iyer)
|
|
Tell your story powerfully – how AI and flexible input help you craft and communicate your story (Mary Votava Sheppard)
|
|
Microsoft 365: Enabling virtual collaboration for the future of our hybrid work environment (Shalendra Chhabra)
|
For a closer look at sessions and resources related to Microsoft 365 Admin Tools and Experiences, see the Microsoft 365 Admin Guide to Microsoft Ignite 2020
To catch up on the latest in Microsoft Endpoint Manager, bookmark https://aka.ms/MicrosoftIgnite2020/MEM.
To see what’s what at Microsoft Ignite 2020 related to Windows deployment and servicing, visit https://aka.ms/MicrosoftIgnite2020/Windows.
by Scott Muniz | Sep 21, 2020 | Uncategorized
This article is contributed. See the original author and article here.
test
by Scott Muniz | Sep 21, 2020 | Uncategorized
This article is contributed. See the original author and article here.
Group Policy Analytics has gone into public preview with the 2009 release, you can learn more here. There is a known issue with the new “Migration readiness report” where Group Policy Objects (GPOs) that you have uploaded in past releases of Group Policy analytics will be excluded in calculations done in the graphic at the top of the workload, Summary blade and Migration Readiness report.
Below are three workarounds for this issue:
- Force a re-compute of calculations by manually taking GPOs through the “Import” workflow again.
- Use the PowerShell script that was provided to help automatically re-compute the calculations. Follow the instructions hosted on our GitHub repository.
- Wait until a future release of Group Policy analytics in Q4 of this calendar year where we will be doing an automatic re-compute for all GPOs across all tenants.
Upcoming feature improvements
We are working on an experience that lets you easily migrate your Group Policy settings into MDM. Tenants who were in private preview will see a “Migrate” button before anyone else. Today, the “Migrate” workflow supports creation into Administrative Template profiles via the profile creation workflow only.
In future releases, support will be added to migrate to other Device Configuration profiles in addition to Administrative Templates, alongside other user experience improvements to help you on your journey to cloud-based policy management. For tenants not who were not in our preview and want to see the “Migrate” workflow, please reach out to gpanalyticspreview@microsoft.com with your tenant ID.
Let us know if you have any additional questions on this by replying to this post or tagging @IntuneSuppTeam out on Twitter.
by Scott Muniz | Sep 21, 2020 | Uncategorized
This article is contributed. See the original author and article here.
By: Spencer Shumway – Program Manager | Microsoft Endpoint Manager – Intune
We’ve been working hard since announcing a new reporting framework at last year’s Ignite conference and wanted to provide an update on some new reports that have shipped as well as the current list of migrated/new reports all up. We’d also like to lightly cover the different report types we’ve identified and are delivering:
-
Organizational reports are generally broad, contain aggregate data/visualizations, and may be less frequently accessed. You can see the entire estate of the report area (like all of your device compliance) with these reports. Reports of this type are usually located in the Reports menu item on the main left navigation of the MEM console.
-
Operational reports are live, and usually have a negative focus to trim down the data to only what an admin needs to take action. You will often see only a subset of your data (like just the non-compliant devices) with these reports. These reports are usually shown inline with the devices or apps workloads in their respective Monitor tabs.
-
Historical reports show aggregate data over a period of time, typically with daily data points. These can be found throughout the console.
-
Resource reports are located on individual resources like a single app, a single policy, or a single device. When you click on an app you will see examples of resource reports in the Device install status and the user install status report. These report types are operational in nature- as they support troubleshooting and remediation actions, but are defined mainly by where you can find them in the console.
-
List view reports aren’t reports in the traditional sense, but they do convey information in the form of lists of objects. As these lists grow in size, they benefit from our reporting framework sort, search, filter, export, and paging controls and so are candidates for migration. A good example of a list view that is supported by our reporting framework is the All devices blade.
-
Specialist reports are reports that have been published as diagnostic settings in Azure Monitor after migrating to our new reporting framework. Once available as a diagnostic setting, you can select a destination for your data to be published- event hub, storage, or Log Analytics. These various destinations enable integration with security information and event management (SIEM) tools, custom alerting, custom aggregation and business logic, external data joins, and long term storage.
Some new reports shipping with our 2009 release:
We also want to call out that as part of our new reporting framework, we’ve made available an export API that can reliably download a compressed CSV file containing the contents of the report in minutes instead of the hours it might have used to take. For reports that are available in this API we strongly
recommend that you no longer page through the reports using the Get-MSGraphNextPage or Get-MSGraphAllPages cmdlets. Those cmdlets may have worse performance, or even stop working. You should instead use the new export API as we’ve shown here.
We also plan on making changes to the way we render data in the console to limit reports to rendering 500,000 rows. While sort will only take place on the 500,000 rows displayed, search, filter, and export will still work across the entire dataset, so we recommend using search and filter to narrow the scope of a report that you need to interact with in the UI. If you need access to the full dataset you can quickly download it via export in the UI, or our export API.
Here is the total list of reports now supported by our new framework:
|
Removed report
|
New report
|
Sprint Released (YYMM)
|
|
Device Compliance
|
Non-compliant devices operational report (Devices > Monitor)
|
1911
|
|
Device Compliance
|
Device Compliance organizational report (Reports > Device Compliance)
|
1911
|
|
|
Device compliance trends report (Reports > Device Compliance)
|
1911
|
|
|
Device compliance logging
|
1911
|
|
Device List
|
New Devices List – With upgraded controls for search, sort, filter, export and with better performance
|
2003
|
|
Devices List (EDU)
|
New Devices List in EDU console – With upgraded controls for search, sort, filter, export, and with better performance
|
2005
|
|
|
Antivirus agent status organizational report (Reports > Microsoft Defender Antivirus (Preview))
|
2009
|
|
|
Antivirus agent status operational report (Endpoint security > Antivirus)
|
2009
|
|
|
Detected malware organizational report (Reports > Microsoft Defender Antivirus (Preview))
|
2009
|
|
|
Detected malware operational report (Endpoint security > Antivirus)
|
2009
|
|
|
Windows 10 feature updates organizational report (Reports > Windows updates(Preview))
|
2009
|
|
|
Windows 10 feature updates operational report (Devices > Monitor)
|
2009
|
| |
Group policy migration readiness organizational report (Reports > Group policy analytics (Preview))
|
2009
|
As a reminder, our sprints are year-month (YYMM), so 1911 was the November 2019 release and 2009 is the September 2020 release.
We will keep posting updates as more reports become available as part of our reporting framework improvements. We’d love to hear any questions or feedback – You can comment on this post orreach out to us on Twitter @spencershum or @IntuneSuppTeam.
by Scott Muniz | Sep 21, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
Check out the following deep dive videos to learn more about new Azure Disk Storage capabilities and features:
Understanding disk IO and how to leverage disk bursting
Overview of Azure Disk Storage security features
Run clustered applications on Azure with shared disks



Recent Comments