by Contributed | Sep 24, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
Now more than ever, organizations are challenged with keeping their employees productive working remotely and interacting with their customers over digital channels. At the same time there has been an increase in evolving digital security threats as bad actors recognize an opportunity to disrupt your business. Moreover, security resources are stretched, and prioritization is important.
To help you protect all the assets within your organization earlier this week we announced Microsoft Defender. Microsoft Defender delivers comprehensive threat protection spanning users, devices, apps, data, servers, IoT devices, Operational Technology (OT), and more. Microsoft Defender is Microsoft’s leading Extended Detection and Response (XDR) solution for threat protection across all your technical assets composed of two experiences: Microsoft 365 Defender and Azure Defender. Azure Defender is an evolution of the threat protection technologies in Azure Security Center, protecting Azure and hybrid environments. With this announcement, we are rebranding the offerings previously called advanced threat protection services in Azure Security Center as Azure Defender. For example, Advanced Threat Protection for Azure Storage is now Azure Defender for Storage.
1. Updated Azure Security Center UI
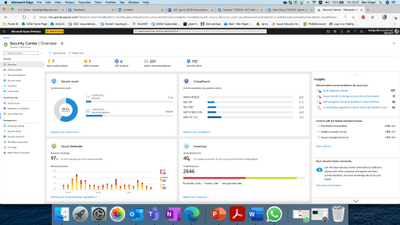
Following this rebranding, and in order to better reflect the different value pillars that Azure Security Center offers, we have also changed the main Security Center product experience. With the new experience, Security Center serves as the central overarching experience that includes multiple independent cloud security pillars such as Azure Secure Score, Regulatory Compliance and of course Azure Defender. In addition, each of these pillars has its own dedicated dashboard allowing deeper insights and actions around that vertical. Changes to the product can be seen at the following link (http://aka.ms/ascignite2020) during the conference and will be integrated into the product after Ignite 2020.

Figure 1: Azure Security Center Overview window
When you click on the Azure Defender dashboard, you can see that you have better visibility into Azure Defender coverage across your different resource types, visibility into onboarding state & agent installation and a holistic view of the threat detection alerts included in Azure Defender.
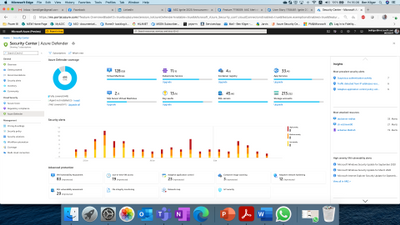
Figure 2: Azure Defender dashboard
2. Protection for multi cloud workloads (AWS & GCP)
As more organizations manage cloud workloads on multiple cloud platforms, they require a security solution that provides visibility & protection across all their cloud environments. To enable that, Security Center is announcing a public preview for protection of workloads in AWS & GCP –
- Customers will be able to onboard their AWS/GCP accounts into ASC.
- Security Center will include detected misconfigurations and findings from AWS Security Hub and GCP Security Command Center into its Secure Score model and Regulatory Compliance experience, thus providing a central pane to visualize security posture across multi-cloud assets.
- Azure Defender for Servers will leverage Azure Arc to extend its support for VMs in AWS & GCP including capabilities such as automatic agent provisioning, policy management, vulnerability management, embedded EDR and more., embedded EDR and more.
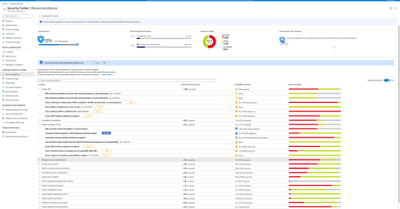
Figure 3: Secure Score Recommendations page including AWS and GCP recommendations
We are also delighted to announce the preview availability of Azure Arc enabled SQL Servers and its integration with Azure Defender and Azure Sentinel. With Azure Arc enabled SQL Server you can now protect SQL Servers anywhere (on-premises, and in other clouds such as AWS, GCP) the same way you protect Azure SQL directly from the Azure portal for a unified, hybrid security experience using Azure Defender. This unified experience simplifies protecting your entire SQL estate. In addition, your security operations team can take the threat information from Azure Security Center and surface it into Azure Sentinel, the industry’s first cloud native SIEM, where when combined with security intelligence from throughout your enterprise, you can now detect and mitigate threats that may traverse laterally across your hybrid environments before attackers have the opportunity to exfiltrate data.
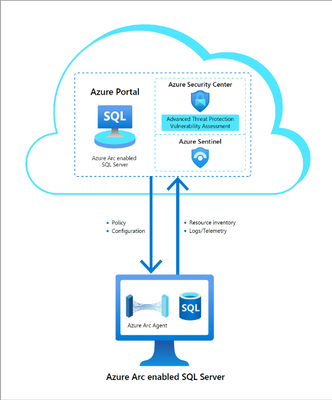
Figure 4. Integration of Azure Arc enabled SQL Server and Azure Security Center
3. Containers Enhancements
As containers and specifically Kubernetes are becoming more widely used, we are extending our Azure Defender for Kubernetes offering to include Kubernetes level policy management, hardening and enforcement with admission control to make sure that Kubernetes workloads are created secure by default. In addition, Container image scanning by Azure Defender for Container Registries will now support continuous scanning of container images in the Azure Container Registry and re-evaluate registry images for new vulnerabilities to minimize the exploitability of running containers.
4. General availability for more platform protection
We are announcing the general availability of Azure Defender for Key Vault and for Azure Defender for Storage protection for Azure Files and Azure Data Lake Storage Gen2.
5. Azure Defender for IoT, Now With CyberX Agentless Technology
At Ignite, we’re announcing Public Preview of new capabilities for securing Operational Technology (OT) environments such as manufacturing, building automation, life sciences, energy and water utilities, oil & gas, and warehousing & logistics.
Incorporating agentless technology from Microsoft’s recent acquisition of CyberX, Azure Defender for IoT enables organizations to auto-discover their IoT/OT assets, identify critical vulnerabilities, and continuously monitor for threats. It will initially be available for on-premises deployments, with an Azure-based console to follow. Read more.
Azure Security Center cloud security posture management enhancements
Azure Security Center continues to provide cloud security posture management enhancements. At Ignite this year, we are announcing general availability for the new Asset Inventory experience. The new experience enables customers to explore their security posture data in a much deeper way, providing view, filter and query abilities for all details and insights across all resources protected by ASC, via an easy to use and crystal clear user interface.
This new experience is fully built on top of Azure Resource Graph (ARG) which now holds all of ASCs security posture data, and leveraging its powerful KQL engine enables customers to quickly and easily reach deep insights on top of ASC data and cross reference with any other resource properties.
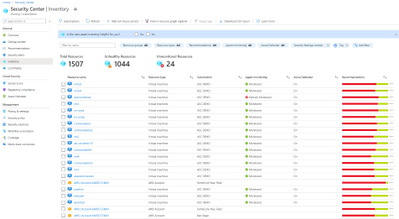
Figure 5: Azure Security Center Inventory view
We are also very excited to announce the public preview of a more fine-grained ability to manage and control security recommendations and their application on one’s resources. This includes ability to exempt specific resources from specific security recommendations, with documented reasoning and easy monitoring of exemptions. Another advanced capability is to customize security findings either by configuring which findings should be applicable, such as by severity, type, name or any other category. This allows maximum flexibility of adjusting the security recommendations to the organization’s policy and priorities and by that better representation of their security posture in Secure Score.
For related material, see the following articles:
by Contributed | Sep 24, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
Initial Update: Thursday, 24 September 2020 13:10 UTC
We are aware of issues within Application Insights and are actively investigating. Some customers may experience data access issue and issues with missed or delayed Log Search alerts in South UK and North Europe regions.
-
Work Around: None
-
Next Update: Before 09/24 15:30 UTC
We are working hard to resolve this issue and apologize for any inconvenience.
-Rama
by Contributed | Sep 24, 2020 | Uncategorized
This article is contributed. See the original author and article here.
Last week Microsoft released a new version of the Containers extension on Windows Admin Center. This release was focused on helping IT Admins getting their container hosts up and running without much effort.
The process of deploying the containers feature on Windows and Docker is actually well documented on our docs page – for both Windows 10 and Windows Server. However, installing the necessary components is just the first step you have to take to prepare your container host. So let’s take a look at what the process looks like on Windows Admin Center.
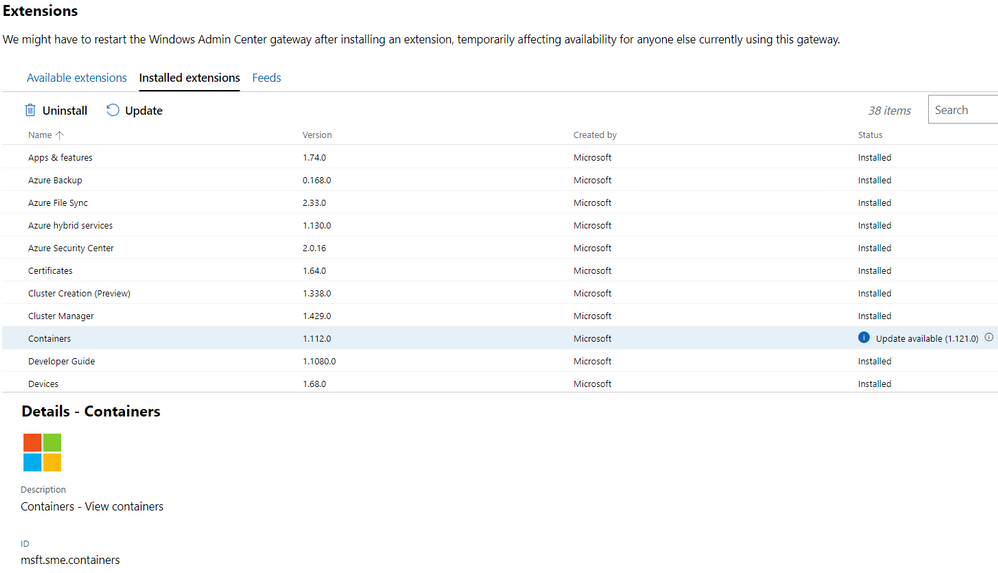
To get started, make sure you have the latest version of the Containers extension installed on your Windows Admin Center instance. To do that, go to the Extension Manager on the Windows Admin Center Settings and check for the Containers extension version 1.121.0:
If you don’t have the extension installed, you’ll see it under Available extensions. If you have a previous version of it installed you can check the Installed extensions tab and look for the update.
An important note here is that the previous version of this extension was available on the Windows Admin Center Insiders feed – which required some additional configuration. This is not a requirement anymore, as the new version is now available on the public feed.
Next, you can go the Windows Admin Center main page and target the server you want to deploy as a container host. Once you open the connection to the targeted server, you’ll see the Containers extension show up:
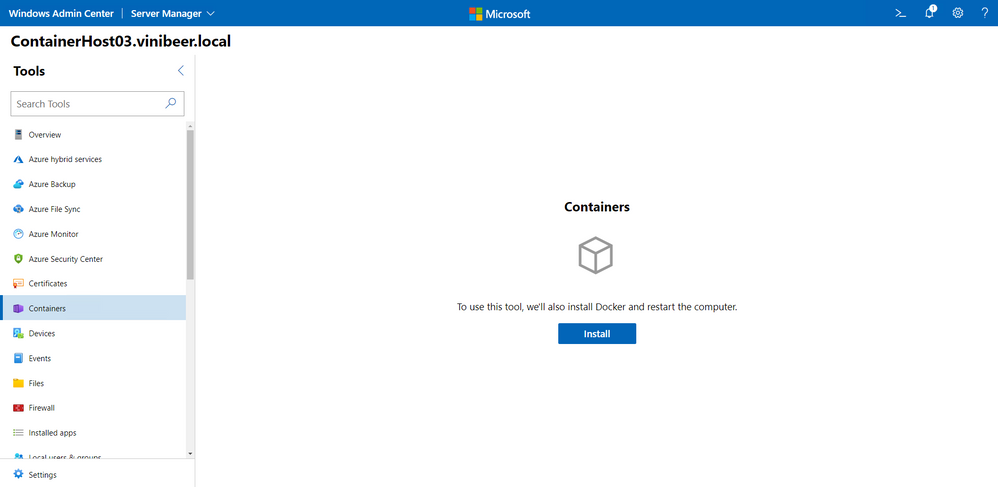
Once you click Install, Windows Admin Center will start the deployment of the Docker components as well as the container feature on Windows. This process might take a few moments to complete and will restart your server:
After the server restarts, you’ll be taken to the Windows Admin Center main page.
That’s it, no command line and PowerShell commands needed. However, there’s more to be done in order to run your first container. Let’s open the connection to the server again and open the Containers extension, then click on the Images tab:
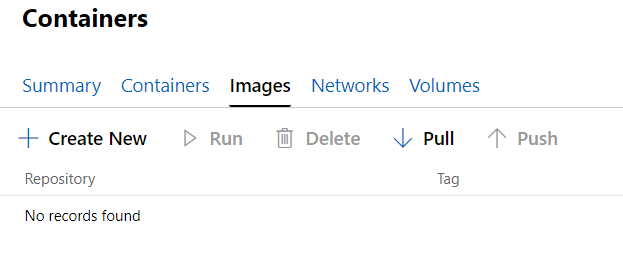
As you can see, there are no images available to create new containers from. While you could go to the command line and simply pass on the image name you want to run, it will take a while to pull the layers needed to run that image. Since all Windows containers are created from the base container images, it’s probably a good idea to have those images already pulled for when you need it. to do that, click the Pull option:
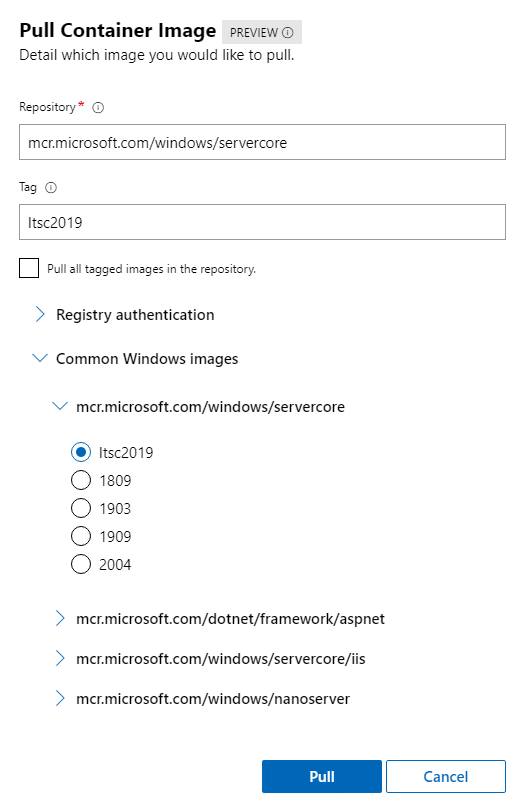
Another great update to this extension is that now you have a list of the most common container images, including the base container images of Server Core and Nano Server. After you pull the images, the process of running new containers based on those images will be way faster.
I hope this blog post was useful and that will help you get started in using Windows Containers with Windows Admin Center. Let us know what you think in the comments or in our GitHub repo.
You can find on Twitter @vrapolinario.
by Contributed | Sep 24, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
Currently Azure marketplace SQL Images are only available in English locale. If you want to change your SQL locale to any other than English, then you can deploy a virtual machine that contains SQL Server initially. We will walk through the steps involved in changing SQL Server language from English to Japanese in this blog.
SQL Server database engine executable file is common to all languages, you can store, extract, and search Japanese data without having to perform the following steps. The default collation of the database can be specified when the database is created. You can explicitly specify the collation of a table column, or if not, the collation of the database is inherited.
If you want to manage from SQL Server Management Studio with a Japanese UI on a remote machine, you do not need to do the following. If you only need the Japanese user interface for administrative tools, you will need to Change locale for SQL Server. The following is an example of SQL Server 2016, but the procedure remains almost the same for other versions of SQL Server:
Uninstall SQL Resource Provider
From the Azure Portal, navigate to your resource group. Click on your “SQL virtual machine” Resource.
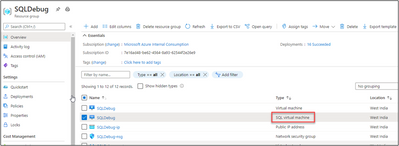
Delete SQL Virtual Machine resource. We are not deleting the Virtual Machine here.
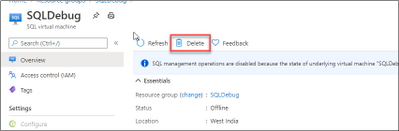
Uninstall SQL Server and its related components.
-
To start the Uninstall process, we will Uninstall SQL instance. Review the list of features and components that will be uninstalled so you can install those when you install the new instance.
-
We need to uninstall “Data Tier Application Framework” and “Microsoft Visual Studio Shell” related packages from programs and features.
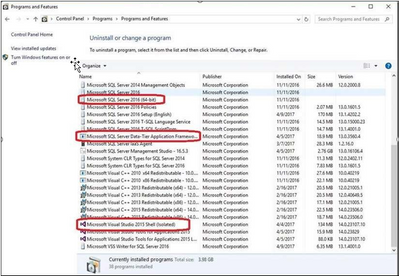
At the end of this step there are no SQL instance, features or components on this machine. Everything has been uninstalled.
Configure Operating System to Support Localized Versions
Before you can install the Japanese version of SQL Server on an English operating system, you must change the language settings of the operating system. Please follow the below steps:
-
User interface settings for the operating system
-
User locale settings for the operating system
-
System locale settings
To change the operating system user interface setting
-
If not already installed, install the operating system MUI that matches your localized version of SQL Server.
-
In Control Panel, open Regional and Language Options.
-
On the Languages tab, for Language used in menus and dialogs, select a value from the list. This setting will affect the user interface language of SQL Server, so it must match your localized version of SQL Server.
-
Click Apply to confirm the change, and OK to close the window.
To change the operating system user locale setting
- If not already installed, install the operating system MUI that matches your localized version of SQL Server.
-
In Control Panel, open Regional and Language Options.
-
On the Regional Options tab, for Select an item to match its preferences, select a value from the list. This setting will affect culture-specific data formatting.
-
Click Apply to confirm the change, and OK to close the window.
To change the system locale setting
-
If not already installed, install the operating system MUI that matches your localized version of SQL Server.
-
In Control Panel, open Regional and Language Options.
-
On the Advanced tab, for Select a language to match the language version of the non-Unicode programs you want to use, select a value from the list. This setting will allow SQL Server Setup to choose the best default collation for your SQL Server installation.
-
Click Apply to confirm the change, and OK to close the window.
Installing the SQL Server with your preferred Locale/Language
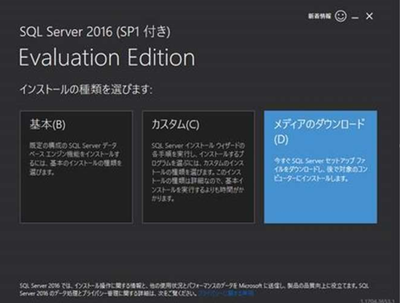
-
Set the package type to ISO and download it.
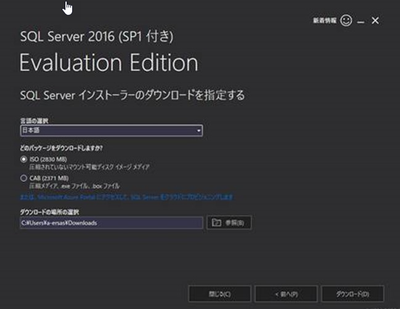
-
You will also need a Microsoft account to download. After downloading, mount the appropriate ISO file and load it into the DVD drive.
-
On the SQL Azure VM, open C:/SQLServer_13.0_Full/x64/DefaultSetup.ini.
DefaultSetup.ini
********************
SQL Server 2016 Configuration File
[OPTIONS]
PID:”XXXXX-XXXXX-XXXXX-XXXXX-XXXXX”
PCUSOURCE: “.
********************
The XXXXX becomes the actual product key which we need to use while installing. Start the installation of the Japanese version of SQL Server 2016. (By default, it is mounted on the E drive, so start setup from here.) )
On the Product Key page, you can change the Edition from Evaluation by entering the product key.
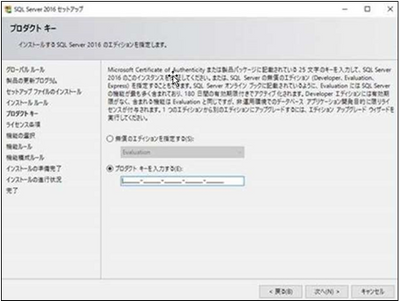
For more information about installing SQL, please check Install SQL Server 2016 from the Installation Wizard (Setup)
Reinstall Resource Provider
Install SQL Resource Provider . This will sync your billing and the SQL Version/Edition we installed with the Azure Portal.
References
Install non-English language versions of SQL Server Management Studio (SSMS)
Microsoft 2012 SP1 Japanese locale Evaluation
Microsoft 2014,2016,2017,2019 Japanese locale Evaluation Version
Local Language Versions in SQL Server
by Contributed | Sep 24, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
Final Update: Thursday, 24 September 2020 09:50 UTC
We’ve confirmed that all systems are back to normal with no customer impact as of 9/24, 09:40 UTC. Our logs show the incident started on 9/24, 09:00 UTC and that during the 40 minutes that it took to resolve the issue some customers may have experienced failure accessing live metrics data.
-
Root Cause: The failure was due to configuration changes in one of our dependent service.
-
Incident Timeline: 40 minutes – 9/24, 09:00 UTC through 9/24, 09:40 UTC
We understand that customers rely on Application Insights as a critical service and apologize for any impact this incident caused.
-Harshita
by Contributed | Sep 24, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
If Azure Kubernetes Services (AKS) was the first Kubernetes based home on Azure that Windows containers have, I am so happy now we got a second brand new home. That is AKS on Azure Stack HCI announced at Ignite this week! As the driver to build and execute the product strategy helping customers lift and shift, and modernize traditional Windows apps with Windows containers, I am thrilled we are bringing AKS on Azure Stack HCI to customers for on-prem or hybrid needs of leveraging Windows containers.
As a starter, from the official doc here, “Azure Kubernetes Service on Azure Stack HCI is an on-premises implementation of Azure Kubernetes Service (AKS), which automates running containerized applications at scale. Azure Kubernetes Service is now in preview on Azure Stack HCI, making it quicker to get started hosting Linux and Windows containers in your datacenter.”
I had the honor participating as an SME in a few Digital Breakout sessions and the Ask the Experts sessions related to AKS on Azure Stack HCI this Ignite. I was blown away by the strong interest from the community. Lots of great questions were asked. To make it easy, I compiled the following relevant links for folks who wanted to get started:
General materials:
Ignite Sessions:
If you are interested in learning more about WAC tooling related to containers, check out 2 previous blogs from Vinicius:
Have fun at Ignite. Have fun trying out Windows containers on AKS on Azure Stack HCI. Keep your questions coming in. Share your feedback with us. Thank you!
Weijuan
Twitter: @WeijuanLand
Email: win-containers@microsoft.com





Recent Comments