
by Scott Muniz | Aug 26, 2020 | Azure, Microsoft, Technology, Uncategorized
This article is contributed. See the original author and article here.

Today’s government organizations face ever-increasing and evolving mission demands, requiring greater speed and agility to modernize IT. Some agencies have discovered a path to success by establishing software factories and cloud PMOs to accelerate development and delivery of better mission apps.
To learn more about this new approach, we invite you to RSVP and join us for this virtual Azure Government meetup, “Strategies to stand up a modern gov software factory + cloud PMO, via Teams Live Event. You can register for free here.
During this meetup, which is free and open to the public, you’ll hear from government and industry experts who will share best practices, insights and demos covering:
• Strategies and approaches to get your software factory up and running
• How to take a factory approach to developing and modernizing applications
• Best practices for establishing and running a cloud-native PMO
•Tips for driving necessary talent development and culture change initiatives
•Demos of tools and technologies to accelerate delivery of mission apps
AGENDA (*subject to change)
6:3O PM – 6:40 PM
Welcome & announcements
•Karina Homme, Senior Director, Microsoft Azure Government
•Vishwas Lele, CTO, AIS, and Microsoft MVP/RD
6:40 PM – 7:00 PM
Presentation: 3 pillars that make up a successful cloud PMO
•Bob Ritchie, VP, Software Practice, SAIC
7:00 PM – 7:20 PM
Demo: Automated modern gov software factory in Azure
•Nirali Shah, Program, Manager, Microsoft Azure Government
•Michael Herndon, Chief Transformation Architect, CloudFit Software
7:20 PM – 8:00 PM
Panel: Strategies to stand up a modern gov software factory + cloud PMO
•Jyoti Anand, Lead AI/ML Architect, US Food and Drug Administration
•Irven Ingram, Cloud Architect, Spatial Data Branch, US Army Corps of Engineers
•Jason Payne, Chief Architect, US Regulated Industries, Microsoft Federal
•Karina Homme, Senior Director, Microsoft Azure Government (moderator)
We look forward to “seeing you” for this virtual meetup. Please help us get the word out and share this event with your colleagues and connections.
Be sure to also join the conversation using #AzureGovMeetup on social media.
*We will be adding the video of the session to this post after it has concluded
by Scott Muniz | Aug 26, 2020 | Uncategorized
This article is contributed. See the original author and article here.
We have heard your feedback and understand your need to focus on business continuity in the midst of the global pandemic. As a result, we have decided to delay the scheduled end-of-service date for the Enterprise, Education, and IoT Enterprise editions of Windows 10, version 1803. This means that security updates will continue to be released monthly until May 11, 2021. The final security update for these editions of Windows 10, version 1803 will be released on May 11, 2021 instead of November 10, 2020.
Security updates for Windows 10, version 1803 will be available via our standard servicing outlets: Windows Update, Windows Server Update Services, and the Microsoft Update Catalog. You will not need to alter your current update management workflows.
After May 11, 2021, devices running the Enterprise, Education, and IoT Enterprise editions of Windows 10, version 1803 will no longer receive security updates. Organizations should plan to update their devices to the latest version of Windows 10 to remain supported after this date.
For a comprehensive list of end-of-service dates for all versions and editions of the Windows client and Windows Server operating systems, bookmark the Windows lifecycle fact sheet or use the Microsoft Lifecycle Policy search tool to find lifecycle information for all commercial Microsoft products. We also recommend you bookmark the Windows message center and follow @WindowsUpdate for the latest news and announcements.
by Scott Muniz | Aug 26, 2020 | Uncategorized
This article is contributed. See the original author and article here.
Excel MVPs Liam Bastick and Tim Heng, together with over 50 other MVPs, leading experts across communities around the world, and Excel product managers (PMs) at Microsoft, held the Excel Virtually Global summit this past July, offering over 50 hours of in-depth discussions and presentations on Microsoft Excel, Power BI, and more.
Liam recently shared with us a bit more on how the event came about, lessons learned, and what’s next:
“I had the brainwave to host a bigger virtual event that would run for two days – 48 hours – straight. I asked around and actually had enough for 55 hours (which ended up 57 on the day!), made up of MVPs, Microsoft staff and other experts. I didn’t want to stop anyone from presenting, so I invited them all.“
“Working around the clock was just as fun as we envisaged… To be fair, it was an absolute blast. Running on adrenaline with three to four hours sleep a night, feeding off the energy of other presenters, it’s quite a unique feeling! In terms of what the audience got to see though, one of the best bits in the conference was an ad hoc session that we ran in one of the breaks.”
“To be balanced though, some things were not challenges: it was easy to fill 48+ slots, language barriers were easily overcome, everyone happily marketed, everyone was fully committed and contributed, people turned up on time and hitches were at a minimum (just one internet drop-out). And we all had fun – and then said we’d never do it again. But of course we will!”
“The main thing that inspires me to continue is seeing all the way people use Excel. When it’s good, I want to propagate it and let the world know. When it’s bad, I want to show people how they can do things faster and more easily.”
Read more in Liam’s Excel Virtually Global 2020: A Personal Look Back.
by Scott Muniz | Aug 26, 2020 | Azure, Microsoft, Technology, Uncategorized
This article is contributed. See the original author and article here.
After an introduction to Enterprise-Scale and further information about possible use cases, I would like to focus on one of the design principles: policy-driven governance.
Policy-driven governance means the usage of Azure Policy to build and provide guardrails, and to enable autonomy for the platform and application teams, regardless of their scale points. Those guardrails ensure that deployed workloads and applications are compliant with your organization’s security and compliance requirements, and therefore a secure path to the public cloud.
What is Azure Policy?
From the Azure Policy overview:[1]
Azure Policy evaluates resources in Azure by comparing the properties of those resources to business rules. These business rules, described in JSON format, are known as policy definitions. To simplify management, several business rules can be grouped together to form a policy initiative (sometimes called a policySet). Once your business rules have been formed, the policy definition or initiative is assigned to any scope of resources that Azure supports, such as management groups, subscriptions, resource groups, or individual resources. The assignment applies to all resources within the scope of that assignment. Subscopes can be excluded, if necessary.
Azure Policy uses a JSON format to form the logic the evaluation uses to determine if a resource is compliant or not. Definitions include metadata and the policy rule. The defined rule can use functions, parameters, logical operators, conditions, and property aliases to match exactly the scenario you want. The policy rule determines which resources in the scope of the assignment get evaluated.
In order to understand the behavior of policies in the context of Enterprise-Scale, some basic Policy characteristics must be known.
- Policy operates at a level above other Azure services by applying policy rules against PUT and PATCH requests and GET responses of resource types going between Azure Resource Manager (ARM) and the owning resource provider (RP).[2]
- A newly assigned policy or policySet, to any supported scope, takes around 30 mins for the assignment to be applied scope.[3]
- Compliance data is updated as follows:[3]
- New policy assignments: 30 mins
- Update existing policy definition: 30 mins
- Update existing policy assignment: 30 mins
- On-demand scan (REST API, PowerShell): 3 mins
- Standard compliance evaluation cycle: 24 hours
- Policy provides different effect types (what happens when the policy rule is evaluated), which do behave differently.[4] The effect types are also evaluated in a specific order, as shown below:[6]
- Disabled
- Append and Modify
- Deny
- Audit
- AuditIfNotExists and DeployIfNotExists
In order to understand how the compliance works and when a resource is marked as non-compliant, you need to understand the following:[5]
- For Audit and Deny: It requires IF statement to be TRUE then effect takes place.
- For Audit resource is marked as non-compliant.
- For Deny, new deployment (for new or update resource) is denied while existing resource is marked as non-complaint.
- For DeployIfNotExists and AuditIfNotExists: It requires IF statement to be TRUE and existence condition to be FALSE.
Azure Policy in the context of Enterprise-Scale
As outlined in the Enterprise-Scale design principles, Policy is used build and provide the required guardrails for all landing zones. For example, a policy ensures that all required activity logs for all subscriptions (selected categories in diagnostic settings) are sent to a central Azure Log Analytics workspace. Or all virtual machines are protected by Azure Backup, as another example. For this, Enterprise-Scale is primarily focusing on proactive and preventive policies (e.g. with DeployIfNotExists, or in short DINE) to enable autonomy for the platform, autonomy for the application teams, and ensures that resources are in their compliant goal state, no matter how those resources got created.
In order to simplify the adoption of those proactive and preventive policies, Enterprise-Scale includes three reference implementations for three different customer use cases, all with an extensive list of policy definitions and policy assignments.[7] For example:
- Enable Azure Security Center with Standard tier
- Deploy a virtual network including network peering
- Deploy and enable security features for Azure SQL Databases (Transparent Data Encryption, auditing, etc.)
The three included reference implementations are:[8]
- Contoso – a hybrid networking example using Azure Virtual WAN
- AdventureWorks – a hybrid networking example using the traditional hub and spoke network architecture
- WingTip – an Azure-only example
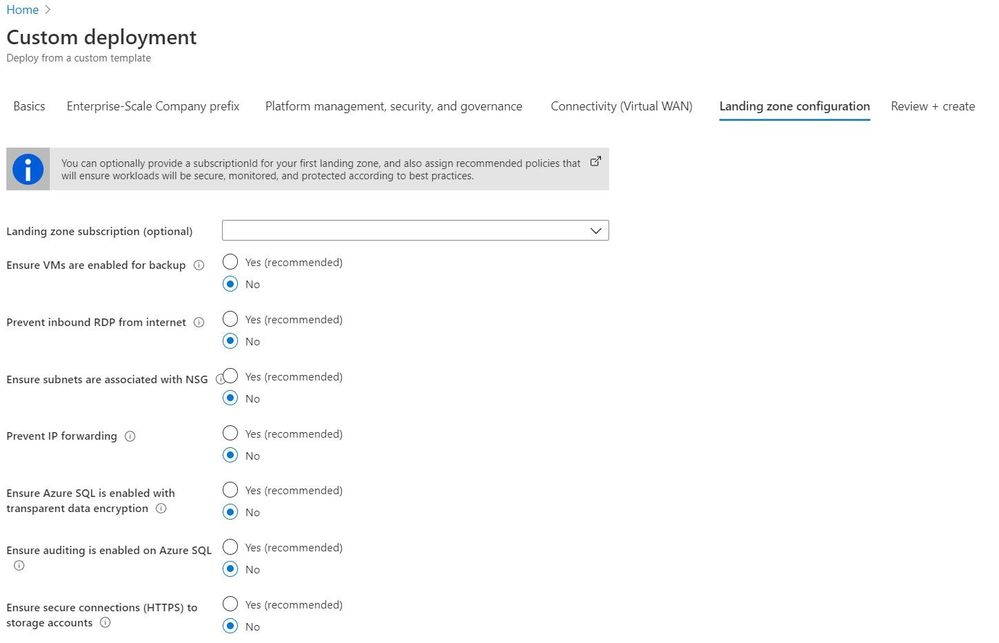
The provided user experience allows you to easily deploy (bootstrap) the selected reference implementation, with all included definitions and assignments. Furthermore, policy definitions and assignments can also be deploy out-of-band on targeted management groups and subscriptions. The user experience when deploying a reference implementation is shown in the figure below:
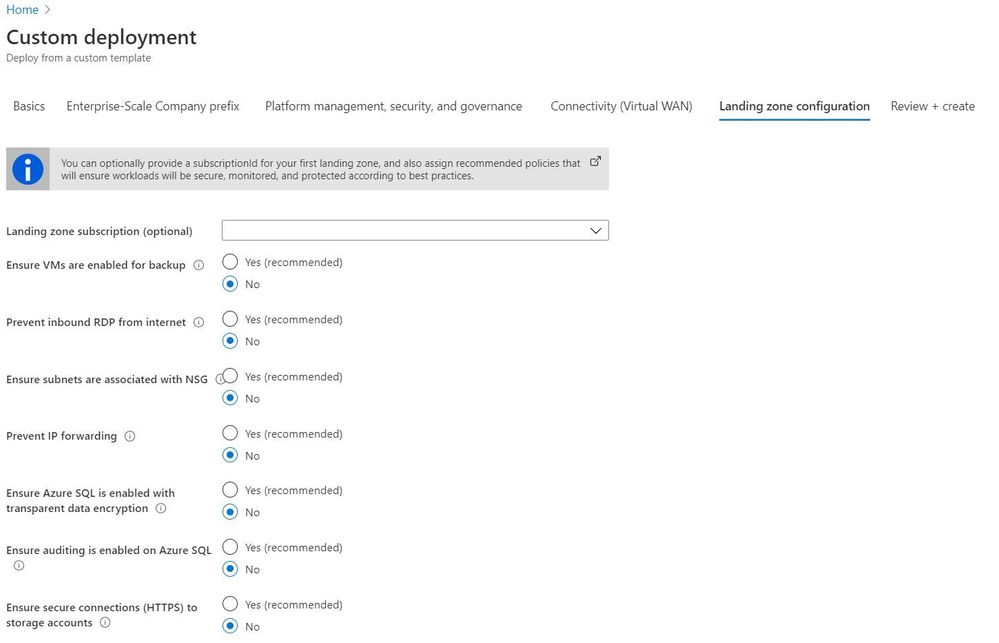 User experience when deploying a reference implementation.
User experience when deploying a reference implementation.
Resource deployment and remediation
Although ARM templates can be deployed to all scopes (tenant, management group, subscription, and resource group scope), policies can only deploy to the subscription and resource group scope.[3] This has an impact on the behavior when deploying resources and policy remediations:
- If a deployment is created via Enterprise-Scale, the remediation for the subscription scope is included; consequently, the policy is evaluated and the specific resources (e.g. with DINE) are deployed.
- If a deployment is created outside of Enterprise-Scale, the remediation is not included; consequently, remediation tasks must be created manually or by using Azure CLI or PowerShell.
Finally, a big thank you to @KristianNese for reviewing and providing feedback.
[1] https://docs.microsoft.com/en-us/azure/governance/policy/overview
[2] https://github.com/Azure/azure-policy
[3] https://docs.microsoft.com/en-us/azure/governance/policy/how-to/get-compliance-data
[4] https://docs.microsoft.com/en-us/azure/governance/policy/concepts/effects
[5] https://docs.microsoft.com/en-us/azure/governance/policy/how-to/get-compliance-data#how-compliance-works
[6] https://docs.microsoft.com/en-us/azure/governance/policy/concepts/effects#order-of-evaluation
[7] https://github.com/Azure/Enterprise-Scale/tree/main/azopsreference
[8] https://github.com/Azure/Enterprise-Scale/blob/main/docs/EnterpriseScale-Deploy-reference-implentations.md
by Scott Muniz | Aug 26, 2020 | Uncategorized
This article is contributed. See the original author and article here.
In recent months, we have many changes at architecture design and security, with users, services, and devices. This article attempts to describe the scenarios that could be driven by remote work and could identify possible configurations based on the business requirements.
Keep in mind that for these scenarios the users’ accounts must be synchronized with Azure AD.
Scenario 1 (Cached Credentials in Workstations/Laptops):
Users who frequently worked from the office (being able to have weekly home offices), today are working from remote locations. Workstations/Laptops no longer connect to Domain Controllers; therefore, it is not possible to change configurations by GPO and to be impacted. In case the user changes his password (through Cloud or VDI services), the device will keep the old password. The user will have to log in to their computer with an old password and then use the new one to access the services.
This scenario is common in those organizations that do not use VPN services. Where your applications are accessed through Remote Apps, Cloud services or VDIs.
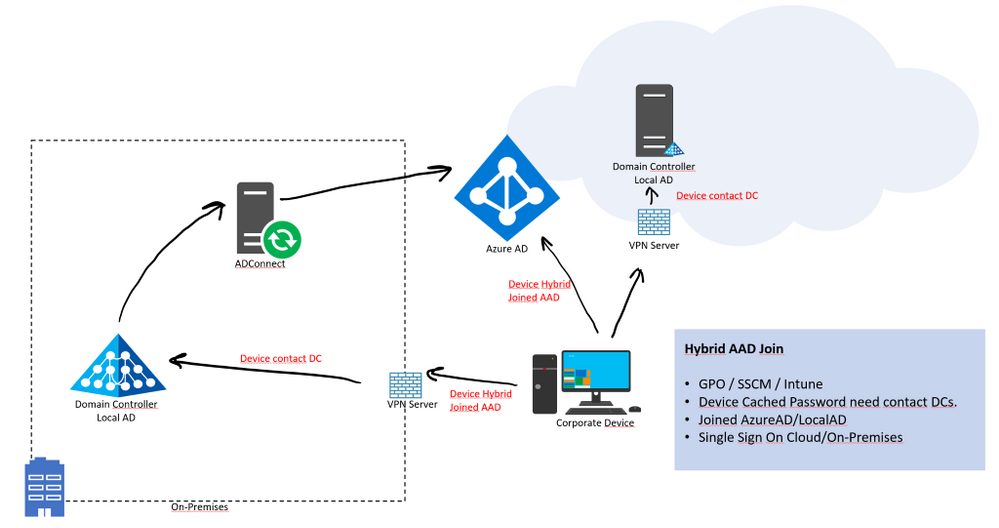
Machines must have network connectivity line of sight to a domain controller to use the new password and update cached credentials. This means that devices must either be on the organization’s internal network or on a VPN with network access to an on-premises domain controller.
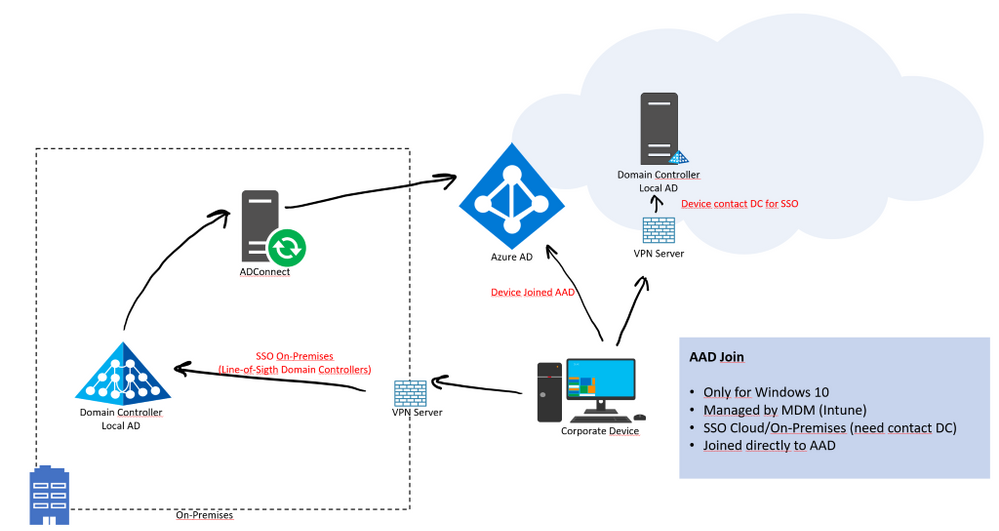
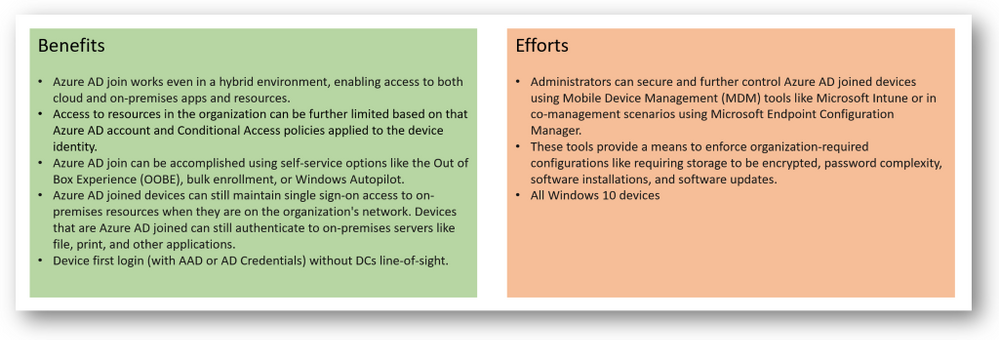
If your environment has an on-premises AD footprint and you also want benefit from the capabilities provided by Azure Active Directory, you can implement hybrid Azure AD joined devices. These devices are joined to your on-premises Active Directory and registered with your Azure Active Directory.

For more Information, please see: https://docs.microsoft.com/en-us/azure/active-directory/devices/concept-azure-ad-join-hybrid
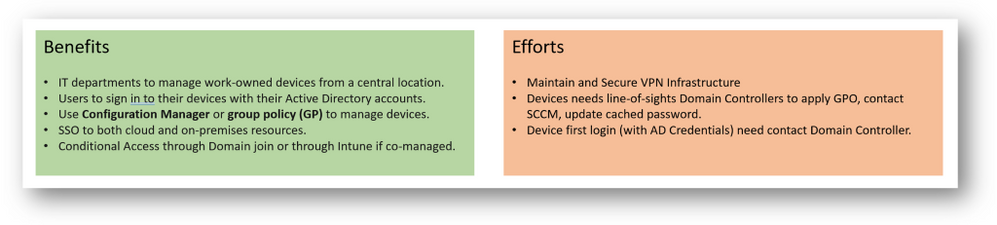
Scenario 2: (Device Provisioning for Distributed Users – only Win10 devices)
Continuing with the remote work scenarios, maybe, we need to assign new devices (Workstation / Laptops) to users who are outside our offices, therefore, it is not possible to log in for the first time to contact a Domain Controller so that the password is stored (cached) on the device, and then by logging in “offline”.
In this scenario, we can use Azure AD Join. It will allow users to log in with their network account (eg UPN) and offer a single sign-on (SSO) experience for both the cloud and their AD Local based applications. If Azure AD joined machines are not connected to your organization’s network, a VPN or other network infrastructure is required. On-premises SSO requires line-of-sight communication with your on-premises AD DS domain controllers.
You can provision Azure AD join using the following approaches:
- Self-service in OOBE/Settings - In the self-service mode, users go through the Azure AD join process either during Windows Out of Box Experience (OOBE) or from Windows Settings. For more information, see Join your work device to your organization’s network.
- Windows Autopilot - Windows Autopilot enables pre-configuration of devices for a smoother experience in OOBE to perform an Azure AD join. For more information, see the Overview of Windows Autopilot.
- Bulk enrollment - Bulk enrollment enables an administrator driven Azure AD join by using a bulk provisioning tool to configure devices. For more information, see Bulk enrollment for Windows devices.
Mobile Device Management (example: Microsoft Intune) is recommended.

by Scott Muniz | Aug 26, 2020 | Azure, Microsoft, Technology, Uncategorized
This article is contributed. See the original author and article here.
|
Microsoft partners like Zaloni, Seeq Corporation, and CloudEngage deliver transact-capable offers, which allow you to purchase directly from Azure Marketplace. Learn about these offers below:
 |
Zaloni Arena: Arena, an augmented data operations platform by Zaloni, provides an active data catalog that enables self-service data enrichment and consumption. Arena drives business and analytics success while providing the controls and extensibility needed across today’s decentralized, multi-cloud data complexity. Safeguard data assets and conquer data sprawl with Arena.
|
 |
Seeq Software – User License: Seeq from Seeq Corporation is an advanced analytics solution that enables process manufacturers to rapidly investigate and share insights from data on Microsoft Azure, as well as contextual data in manufacturing and business systems. Seeq’s extensive support for time series data accelerates analytics, publishing, and decision-making.
|
 |
Personalization Platform: CloudEngage helps retailers give website visitors a personalized, relevant, and intuitive experience. It works seamlessly with any content management or commerce system, and it automatically builds 360-degree audience profiles and segments with machine learning. Serving content based on the individual needs and interests of site visitors improves customer engagement and increases web and mobile conversion rates.
Chord: CloudEngage’s live-chat product, built on a personalization core with machine learning, makes it easy for customers to connect with a real person when browsing your website. Chord keeps track of a visitor’s interests and browsing history, and smart profile cards show ads, interest categories, geolocation, and weather. Adapt in real time to whatever your customer is looking for, and make it easy for your agents to pick up where they left off.
|
|






Recent Comments