by Contributed | Dec 27, 2023 | Technology
This article is contributed. See the original author and article here.
Agenda
This article will provide a demonstration on how to utilize either SAS token authentication or managed identity from API Management to make requests to Azure Storage. Furthermore, it will explore and compare the differences between these two options.
Comparision
The choice between Managed Identity and SAS Token depends on factors such as the level of control required, the duration of access, and the specific security requirements of your application. Both options offer different levels of access control and security features for accessing Azure Storage.
Azure Managed Identity vs. SAS (Shared Access Signature) Token
Authentication |
Advantage |
Disadvantage |
Azure Managed Identity |
- Azure Managed Identity provides an automatic and seamless way to authenticate with Azure Storage.
- Managed Identity allows you to specify the necessary scopes and permissions required for accessing Azure Storage. You can assign specific roles to the managed identity.
- With Managed Identity, you can assign RBAC roles at a granular level to control access to Azure Storage resources.
- Managed Identity offers a secure way to access Azure Storage, as it eliminates the need to store and manage secrets or credentials in your application code.
|
- While Managed Identity offers RBAC, the level of granularity might be limited compared to SAS tokens.
- Managed Identity tokens have a default lifetime and are automatically refreshed by Azure. There is limited control over token expiration.
|
SAS Token |
- SAS token allows you to define specific permissions and access levels for resources in Azure Storage. This includes read, write, delete, or list operations.
- SAS tokens are generated for specific resources or containers in Azure Storage, providing a more restricted access scope compared to managed identities.
- You can set an expiration time for the SAS token, after which it becomes invalid. This provides an additional layer of security and helps to control access to storage resources.
- With SAS tokens, you can grant temporary access to specific resources or containers without the need for permanent credentials.
|
- SAS tokens require manual generation and management, which can be cumbersome and time-consuming, especially when dealing with multiple client applications or frequent token rotation.
- SAS tokens have an expiration date, and once expired, they become invalid. This requires additional effort to generate and distribute new tokens to maintain access, which may impact the continuity of your application.
- If not properly secured, an exposed SAS token could lead to unauthorized access to your Azure Storage resources. It is crucial to ensure secure handling and storage of SAS tokens to prevent potential security breaches.
- Revoking access granted through a SAS token can be challenging, as it usually requires updating the access policy or generating a new token. This might cause inconvenience and delay if you need to revoke access quickly and efficiently.
|
It is crucial to select the appropriate authentication method for accessing Azure Storage based on your specific use cases. For instance, if the permission for your client applications is permanent and long-term, it may be preferable to leverage Azure Managed Identity, as the assigned permission remains in place indefinitely. On the other hand, if you only need to grant temporary access to your client applications, it is more suitable to use SAS Token. SAS tokens can be created with an expiration date, and the permission will automatically expire once the token becomes invalid. This grants more control over the duration of access for temporary scenarios.
Below are the instructions to implement both Azure Managed Identity and SAS Token authentication options.
OPTION 1: Authentication via managed identity
This shows you how to create a managed identity for an Azure API Management instance and how to use it to access Azure Storage. A managed identity generated by Microsoft Entra ID allows your API Management instance to easily and securely access Azure Storage which is protected by Microsoft Entra ID. Azure manages this identity, so you don’t have to provision or rotate any secrets.
Configuration
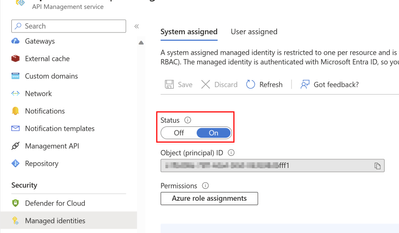
The initial step involves enabling the managed identity for your APIM service, followed by assigning the appropriate permissions for blob uploading. You must go to the “Managed identities” blade to enable the system assigned identity firstly.

To add the storage permission, you can navigate to the same blade and click on the “Azure role assignments” button. It is important to carefully consider the role assignment based on your specific use cases, as there are multiple built-in roles available for authorizing access to blob data using Microsoft Azure Active Directory. For testing purposes, you can grant the “Storage Blob Data Contributor” permission to the managed identity.
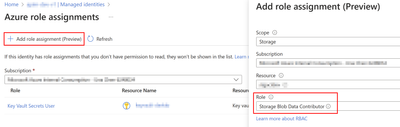
For more detailed information regarding the built-in roles for blobs, please refer to the documentation provided below.
Assign an Azure role for access to blob data – Azure Storage | Microsoft Learn
Authorize access to blobs using Microsoft Entra ID – Azure Storage | Microsoft Learn
Policy
In the
<rewrite-uri template="@{
var requestId = context.RequestId;
return $"/{{blob-container-name}}/log-{requestId}.txt?{{blob-sas-token}}";
2019-07-07
BlockBlob
@(context.Request.Body.As(preserveContent: true))
Within the
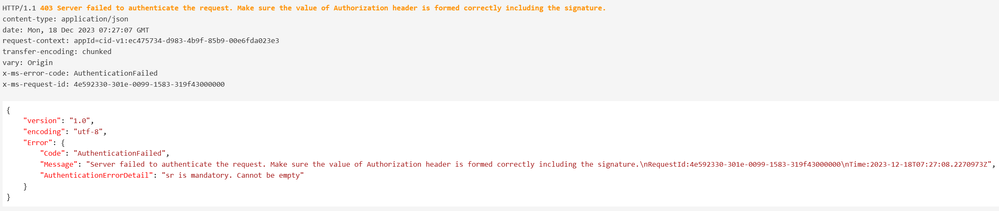
Error example:
Test
Simply using the test panel to do a test and check if everything works fine. The response will come back with 201-Created when the file has been uploaded successfully.
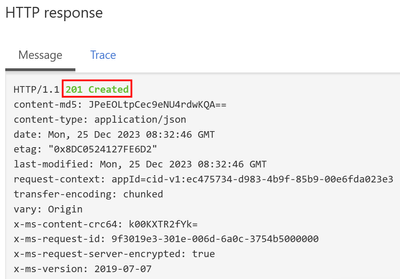
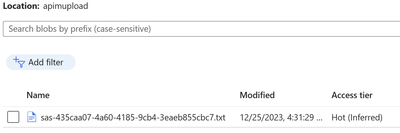
The file upload to the storage container was successful.
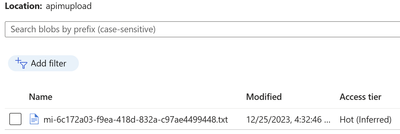
OPTION 2: Access Storage through SAS token
This is a method to access Storage Account from APIM service using SAS token. By setting the SAS token as named values, it can help reuse the SAS token.
One thing you might need to be careful about is that the SAS token should be handled and maintained manually because there is no integration between Storage Account and Key Vault for key re-creation.
Prerequisite
A SAS token is required before implementation. There are some ways to create a SAS token. You can generate the token from the Azure portal by selecting “Shared Access Signature” from the menu and providing the necessary information.
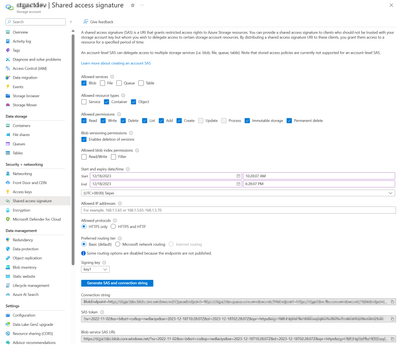
Additionally, both Azure PowerShell and Azure CLI can be utilized to generate the token.
– By using the Azure PowerShell, the examples within the below documentation can help you to create the SAS token.
New-AzStorageAccountSASToken (Az.Storage) | Microsoft Learn
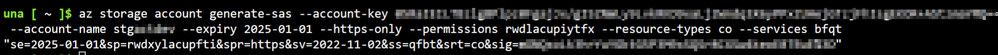
– By using Azure CLI
az storage account | Microsoft Learn
Example:
Configuration
After generating the SAS token, let’s move forward to API management service to set up the required configurations to restore the SAS token in the Named values on for API reference.
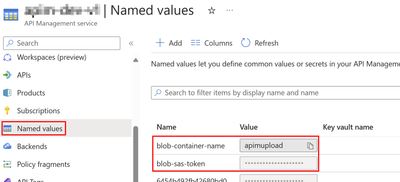
Policy
In the
<rewrite-uri template="@{
var requestId = context.RequestId;
return $"/{{blob-container-name}}/log-{requestId}.txt?{{blob-sas-token}}";
2019-07-07
BlockBlob
@(context.Request.Body.As(preserveContent: true))
Within the
Error example:

Test
Simply using the test panel to do a test and check if everything works fine. The response will come back with 201-Created when the file has been uploaded successfully.
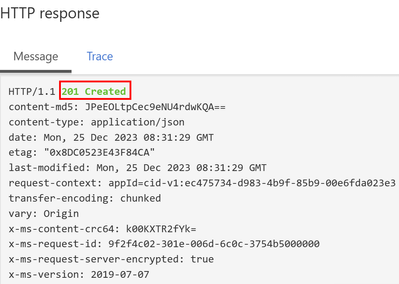
The file upload to the storage container was successful.
Conclusion
In conclusion, both Azure Managed Identity and SAS Token authentication methods offer secure ways to upload blob files to Azure Storage from API Management.
Azure Managed Identity provides seamless authentication and eliminates the need to store and manage credentials, improving security. It allows for granular access control through RBAC and is suitable for permanent permission scenarios. However, it is limited to Azure services and requires dependency on Azure AD.
SAS Token authentication offers greater flexibility with temporary access and fine-grained control over permissions. It allows for the generation of tokens with specific expiration dates, providing enhanced security. However, SAS token management can be more complex, requiring manual generation and distribution of tokens.
When choosing between the two methods, consider the longevity of permissions needed and the level of control required. Azure Managed Identity is ideal for long-term permissions. Assess your specific use case to determine the most secure and convenient authentication approach for uploading blob files to Azure Storage from API Management.

by Contributed | Dec 22, 2023 | Technology
This article is contributed. See the original author and article here.
Hi everyone! Brandon Wilson here once again with this month’s “Check This Out!” (CTO!) guide, and apologies for the delay!
These posts are only intended to be your guide, to lead you to some content of interest, and are just a way we are trying to help our readers a bit more, whether that is learning, troubleshooting, or just finding new content sources! We will give you a bit of a taste of the blog content itself, provide you a way to get to the source content directly, and help to introduce you to some other blogs you may not be aware of that you might find helpful.
From all of us on the Core Infrastructure and Security Tech Community blog team, thanks for your continued reading and support!

Title: Collecting Debug Information from Containerized Applications
Source: Ask The Performance Team
Author: Will Aftring
Publication Date: 11/17/2023
Content excerpt:
This blog post will assume that you have a fundamental understanding of Windows containers. If that isn’t the case, then then I highly recommend reading Get started: Run your first Windows container.
Many developers and IT Admins are in the midst of migrating long standing applications into containers to take advantage of the myriad of benefits made available with containerization.
NOTE: Not all applications are able to equally take advantage of the benefits of containerization. It is another tool for the toolbox to be used at your discretion.
But moving an existing application into a container can be a bit tricky. With this blog post I hope to help make that process a little bit easier for you.

Title: Bring Azure to your System Center environment: Announcing GA of SCVMM enabled by Azure Arc
Source: Azure Arc
Author: Karthik_KR07
Publication Date: 11/15/2023
Content excerpt:
At Microsoft, we’re committed to providing our customers with the tools they need to succeed wherever they are. By extending Azure services to the customer’s preferred environments like System Center, we empower customers with access to Azure’s potential along with a consistent experience across their hybrid estate.
Today we’re excited to deliver on that commitment as we announce that System Center Virtual Machine Manager (SCVMM) enabled by Azure Arc is now generally available to manage SCVMM resources in Azure.

Title: The first Windows Server 2012/R2 ESU Patches are out! Are you protected?
Source: Azure Arc
Author: Aurnov Chattopadhyay
Publication Date: 11/27/2023
Content excerpt:
It’s been almost two weeks since the first post-End of Life Patch Tuesday for Windows Server 2012/R2. To receive that critical security patch from November’s Patch Tuesday, your servers must be enrolled in Extended Security Updates. Fortunately, it’s not too late. You can enroll in WS2012 ESUs enabled by Azure Arc anytime, with just a few steps!

Title: Discover the latest Azure optimization skilling resources
Source: Azure Architecture
Author: Megan Pennie
Publication Date: 11/8/2023
Content excerpt:
Optimizing your Azure cloud investments is crucial for your organization’s success, helping you minimize unnecessary expenses, and ultimately drive better ROI. At Microsoft, we’re committed to optimizing your Azure environments and teaching you how to do it with resources, tools, and guidance, supporting continuous improvement of your cloud architectures and workloads, in both new and existing projects. We want you to gain confidence to reach your cloud goals, to become more effective and efficient when you have a better grasp of how to work in the cloud most successfully. To do that, our wide range of optimization skilling opportunities help you confidently achieve your cloud goals, resulting in more effectiveness and efficiency through a deeper knowledge of successful cloud operations.

Title: Deepening Well-Architected guidance for workloads hosted on Azure
Source: Azure Architecture
Author: Uli Homann
Publication Date: 11/14/2023
Content excerpt:
I am excited to announce a comprehensive refresh of the Well-Architected Framework for designing and running optimized workloads on Azure. Customers will not only get great, consistent guidance for making architectural trade-offs for their workloads, but they’ll also have much more precise instructions on how to implement this guidance within the context of their organization.

Title: Start Your Cloud Adoption Journey with the New Azure Expert Assessment Offering!
Source: Azure Architecture
Author: Pratima Sharma
Publication Date: 11/28/2023
Content excerpt:
Are you looking for a way to accelerate your cloud journey and optimize your IT infrastructure, data, and applications? If so, you might be interested in the Brand New Azure Expert Assessment Offering! It is being launched as a new option within the Microsoft Solution Assessment Program. This is a free one-to-one offering from Microsoft that helps you plan your cloud adoption by collaborating with a Certified Azure Expert who will personally guide you through the assessment, and will make remediation recommendations for your organization.

Title: Reduce Compute Costs by Pausing VMs (now in public preview)
Source: Azure Compute
Author: Ankit Jain
Publication Date: 11/15/2023
Content excerpt:
We are excited to announce that Azure is making it easier for customers to reduce Compute costs by providing them the ability to hibernate Virtual Machines (VMs). Starting today, customers can hibernate their VMs and resume them at a later time. Hibernating a VM deallocates the machine while persisting the VM’s in-memory state. While the VM is hibernated, customers don’t pay for the Compute costs associated with the VM and only pay for storage and networking resources associated with the VM. Customers can later start back these VMs when needed and all their apps and processes that were previously running simply resume from their last state.

Title: Security and ransomware protection with Azure Backup
Source: Azure Governance and Management
Author: Utsav Raghuvanshi
Publication Date: 11/17/2023
Content excerpt:
Ransomware attacks can cause significant damage to organizations and individuals, including data loss, security breaches, and costly business disruptions. When successful, they can disable a business’ core IT infrastructure, and cause destruction that could have a debilitating impact on the physical, economic security or safety of a business. And unfortunately, over the last few years, the number of ransomware attacks have seen a significant growth in their numbers as well as their sophistication. Having a sound BCDR strategy in place is essential to meeting your overall goals when it comes to ensuring security against ransomware attacks and minimizing their possible impact on your business. To make sure all customers are well protected against such attacks, Azure Backup provides a host of capabilities, some built-in while others optional, that significantly improve the security of your backups. In this article, we discuss some such capabilities offered by Azure Backup that can help you prepare better to recover from ransomware attacks as well as other data loss scenarios.

Title: Improve visibility into workload-related spend using Copilot in Microsoft Cost Management
Source: Azure Governance and Management
Author: Antonio Ortoll
Publication Date: 11/20/2023
Content excerpt:
Reducing spend is more important than ever given today’s dynamic economy. Today’s businesses strive to create efficiencies that safeguard against unpredictable shifts in the economy, beat competitors, and prioritize what matters most. But accomplishing this is less about cutting costs and more about the ability to continuously optimize your cloud investments. Continuous optimization can help you drive innovation, productivity, and agility and realize an ongoing cycle of growth and innovation in your business.

Title: Using Azure Site Recovery & Microsoft Defender for Servers to securely failover to malware-free VMs
Source: Azure Governance and Management
Author: Utsav Raghuvanshi
Publication Date: 11/29/2023
Content excerpt:
In this article, we will see how Azure Site Recovery offers an automated way to help you ensure that all your DR data, to which you would fail over, is safe and free of any malware using Microsoft Defender for Cloud.
Azure Site Recovery helps ensure business continuity by keeping business apps and workloads running during outages. Site Recovery replicates workloads running on physical and virtual machines (VMs) from a primary site to a secondary location. After the primary location is running again, you can fail back to it. Azure Site Recovery provides Recovery Plans to impose order, and automate the actions needed at each step, using Azure Automation runbooks for failover to Azure, or scripts.

Title: Accelerate Innovation with Azure Migrate and Modernize and Azure Innovate
Source: Azure Migration and Modernization
Author: Cyril Belikoff
Publication Date: 11/15/2023
Content excerpt:
In July this year, we announced the launch of Azure Migrate and Modernize, and Azure Innovate, our flagship offerings to help accelerate your move to the cloud. Azure Migrate and Modernize helps you migrate and modernize your existing applications, data and infrastructure to Azure, while Azure Innovate helps you with your advanced innovation needs such as infusing AI into your apps and experiences, advanced analytics, and building custom cloud native applications.

Title: Secure your subnet via private subnet and explicit outbound methods
Source: Azure Networking
Author: Brian Lehr, Aimee Littleton
Publication Date: 11/16/2023
Content excerpt:
While there are multiple methods for obtaining explicit outbound connectivity to the internet from your virtual machines on Azure, there is also one method for implicit outbound connectivity – default outbound access. When virtual machines (VMs) are created in a virtual network without any explicit outbound connectivity, they are assigned a default outbound public IP address. These IP addresses may seem convenient, but they have a number of issues and therefore are only used as a “last resort”…

Title: Understanding Azure DDoS Protection: A Closer Look
Source: Azure Network Security
Author: David Frazee
Publication Date: 11/15/2023
Content excerpt:
Azure DDoS Protection is a service that constantly innovates itself to protect customers from ever-changing distributed denial-of-service (DDoS) attacks. One of the major challenges of cloud computing is ensuring customer solutions maintain security and application availability. Microsoft has been addressing this challenge with its Azure DDoS Protection service, which was launched in public preview in 2017 and became generally available in 2018. Since its inception, Microsoft has renamed its Azure DDoS Protection service to better reflect its capabilities and features. We’ll discuss how this protection service has transformed through the years and provide more insights into the levels of protection offered by the separate tiers.

Title: 2023 Holiday DDoS Protection Guide
Source: Azure Network Security
Author: Amir Dahan
Publication Date: 11/21/2023
Content excerpt:
As the holiday season approaches, businesses and organizations should brace for an increase in Distributed Denial of Service (DDoS) attacks. Historically, this period has seen a spike in such attacks, targeting sectors like e-commerce and gaming that experience heightened activity. DDoS threats persist throughout the year, but the holiday season’s unique combination of increased online activity and heightened cyber threats makes it a critical time for heightened vigilance.

Title: Personal Desktop Autoscale on Azure Virtual Desktop generally available
Source: Azure Virtual Desktop
Author: Jessie Duan
Publication Date: 11/28/2023
Content excerpt:
We are excited to announce that Personal Desktop Autoscale on Azure Virtual Desktop is generally available as of November 15, 2023! With this feature, organizations with personal host pools can optimize costs by shutting down or hibernating idle session hosts, while ensuring that session hosts can be started when needed.

Title: Microsoft Assessments – Milestones
Source: Core Infrastructure and Security
Author: Felipe Binotto
Publication Date: 11/7/2023
Content excerpt:
In this post, I want to talk about Microsoft Assessments but more specifically Microsoft Assessments Milestones because they are a very useful tool which is not widely used.
In case you don’t know what Microsoft Assessments are, they are a free, online platform that helps you evaluate your business strategies and workloads. They work through a series of questions and recommendations that result in a curated guidance report that is actionable and informative.

Title: Azure MMA Agent Bulk Removal
Source: Core Infrastructure and Security
Author: Paul Bergson
Publication Date: 11/13/2023
Content excerpt:
In the following sections of this blog, I will provide a step-by-step guide to help you migrate away from MMA to AMA. This guide is designed to make the transition as smooth and seamless as possible, minimizing any potential disruptions to your monitoring workflow.
But that is not all. To make things even easier, there is a GitHub site that hosts the necessary binaries for this migration process. These binaries will be used to install a set of utilities in Azure, including a process dashboard. This dashboard will provide you with a visual representation of the migration process, making it easier to track and manage.

Title: Active Directory Hardening Series – Part 2 – Removing SMBv1
Source: Core Infrastructure and Security
Author: Jerry Devore
Publication Date: 11/20/2023
Content excerpt:
Ok, let’s get into today’s topic which is removing SMBv1 from domain controllers. Like my previous blog on NTLM, a lot of great content has already been written on SMBv1. My objective is to not to rehash the why but rather focus on how you can take action in a production environment.

Title: The Twelve Days of Blog-mas: No.1 – A Creative Use for Intune Remediations
Source: Core Infrastructure and Security
Author: Michael Hildebrand
Publication Date: 11/28/2023
Content excerpt:
For Post #1, I offer to you a quick’n’easy way to use Intune Remediations to get some info from Windows PCs.
Last reboot dates/times are frequently used as simple indicators of life for devices. I was asked if this is captured anywhere in Intune and oddly, I’d never looked – but as I went hunting through Intune (Portal and Graph), the more I looked, the more I couldn’t find it anywhere obvious. “Surely it can’t be THIS hard…?“

Title: Connecting to Azure Services on the Microsoft Global Network
Source: Core Infrastructure and Security
Author: Preston Romney
Publication Date: 11/28/2023
Content excerpt:
Azure Services and the solutions you deploy into Azure are connected to the Microsoft global wide-area network also known as the Microsoft Global Network or the Azure Backbone. There are a few different ways to connect to an Azure service from a subnet, depending on your requirements around securing access to these services. Your requirements should dictate which method you choose. There are some common misconceptions around connectivity, and the goal of this article is to provide some clarity around connecting to Azure Services.

Title: The Twelve Days of Blog-mas: No.2 – Windows Web Sign in and Passwordless
Source: Core Infrastructure and Security
Author: Michael Hildebrand
Publication Date: 11/29/2023
Content excerpt:
Hi folks – welcome to the second post in the holiday ’23 series.
Today’s post is about a capability that came to preview long ago but recently surprised much of the world and moved to General Availability (GA).

Title: The Twelve Days of Blog-mas: No.3 – Windows Local Admin Password Solution (LAPS)
Source: Core Infrastructure and Security
Author: Michael Hildebrand
Publication Date: 11/30/2023
Content excerpt:
Buenos días and welcome to número tres in the holiday ’23 series.
This one is sure to please the crowd – it’s the NEW AND IMPROVED easy to setup/deploy/use solution for when IT Ops/Support needs a local admin ID and password to perform some management task(s) on a Windows endpoint.

Title: First Party Services Adoption for Migrated Virtual Machines via Azure Policy
Source: FastTrack for Azure
Author: Alejandra8481
Publication Date: 11/2/2023
Content excerpt:
Server migrations to Azure Virtual Machines either through Azure Migrate or via a redeploy approach can benefit from Azure policies to accelerate adoption of Azure first party services across BCDR, Security, Monitoring and Management.
Our Cloud Adoption Framework’s guidance for Azure Landing Zones already provides a good baseline of recommended Azure policies. However, a variation to this baseline is described in this article with a focus on newly migrated Azure Virtual Machine resources.

Title: Windows Events, how to collect them in Sentinel and which way is preferred to detect Incidents
Source: FastTrack for Azure
Author: Lizet Pena De Sola
Publication Date: 11/20/2023
Content excerpt:
How can a SOC team ingest and analyze Windows Logs with Microsoft Sentinel? What are the main options to ingest Windows Logs into a Log Analytics Workspace and use Microsoft Sentinel as a SIEM to manage security incidents from events recorded on these logs?
Read on to find out!

Title: Step-by-Step : Assign access packages automatically based on user properties in Microsoft Entra ID
Source: ITOps Talk
Author: Dishan Francis
Publication Date: 11/27/2023
Content excerpt:
Traditionally, during the setup of an access package, you could specify who can request access, including users and groups in the organization’s directory or guest users. Now, you have the option to use an automatic assignment policy to manage access packages. This policy includes membership rules that evaluate user attribute values to determine access. You can create one automatic assignment policy per access package, which can assess built-in user attributes or custom attribute values generated by third-party HR systems and on-premises directories. Behind the scenes, Entitlement Management automatically creates dynamic security groups based on the policy rules, which are adjusted as the rules change.

Title: Extended Security Updates (ESUs): Online or proxy activation
Source: Windows IT Pro
Author: Poornima Priyadarshini
Publication Date: 11/9/2023
Content excerpt:
When your Windows products reach the end of support, Extended Security Updates (ESUs) are there to protect your organization while you modernize your estate. To take advantage of this optional service, you’d purchase and download ESU product keys, install them, and finally activate the extended support.

Title: Windows Server 2012/R2: Extended Security Updates
Source: Windows IT Pro
Author: Poornima Priyadarshini
Publication Date: 11/9/2023
Content excerpt:
You can now get three additional years of Extended Security Updates (ESUs) if you need more time to upgrade and modernize your Windows Server 2012, Windows Server R2, or Windows Embedded Server 2012 R2 on Azure. This also applies to Azure Stack HCI, Azure Stack Hub, and other Azure products.

Title: Universal Print makes cloud printing truly “universal”
Source: Windows IT Pro
Author: Robert Cunningham
Publication Date: 11/15/2023
Content excerpt:
Universal Print is a cloud-based print solution that enables a simple, rich, and secure print experience for users while also reducing time and effort for IT pros. By shifting print management to the cloud, IT professionals can simplify administration and end-users can easily print, reducing the expense of organizations’ print infrastructure.

Title: Copilot coming to Windows 10
Source: Windows IT Pro
Author: Alan Meeus
Publication Date: 11/20/2023
Content excerpt:
Today, we start to roll out Copilot in Windows (in preview) for Windows 10, version 22H2 to Windows Insiders in the Release Preview Channel. Bringing Copilot to Windows 10 enables organizations managing both Windows 11 and Windows 10 devices to continue considering a rollout of Copilot in Windows and provide this powerful productivity experience to more of their workforce.

Previous CTO! Guides:
Additional resources:


































Recent Comments