by Contributed | Sep 24, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
Hi Everyone,
This week we have announced the availability of the initial public preview of Azure Kubernetes Service (AKS) on Azure Stack HCI.
You can evaluate AKS on Azure Stack HCI by registering for the Public Preview here: https://aka.ms/AKS-HCI-Evaluate
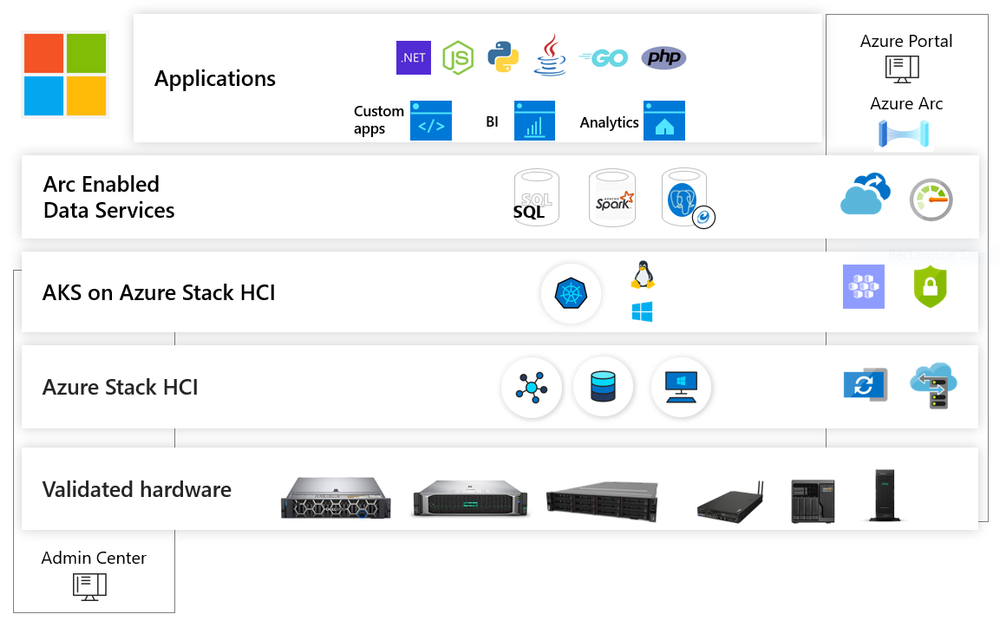
Azure Kubernetes Service on Azure Stack HCI takes our popular Azure Kubernetes Service (AKS) and makes it available to customers to run on-premises; delivering Azure consistency, a familiar Azure experience, ease of use and high security for their containerized applications. AKS on Azure Stack HCI enables developers and administrators to deploy and manage containerized apps on Azure Stack HCI. You can use AKS on Azure Stack HCI to develop applications on AKS and deploy them unchanged on-premises, run Arc enabled Data Services on a resilient platform and modernize Windows Server and Linux applications.
With AKS on Azure Stack HCI, Microsoft is delivering an Industry leading experience for modern application development and deployment in a hybrid cloud era. Microsoft is the only company that delivers technology that takes you from bare metal to a public cloud connected and consistent application and data platform in your datacenter.
AKS on Azure Stack HCI can run Windows and Linux containers, all managed and supported by Microsoft. AKS on Azure Stack HCI leverages our experience with AKS, follows the AKS design patterns and best-practices, and uses code directly from AKS. This means that you can use AKS on Azure Stack HCI to develop applications on AKS and deploy them unchanged on-premises. It also means that any skills that you learn with AKS on Azure Stack HCI are transferable to AKS as well.
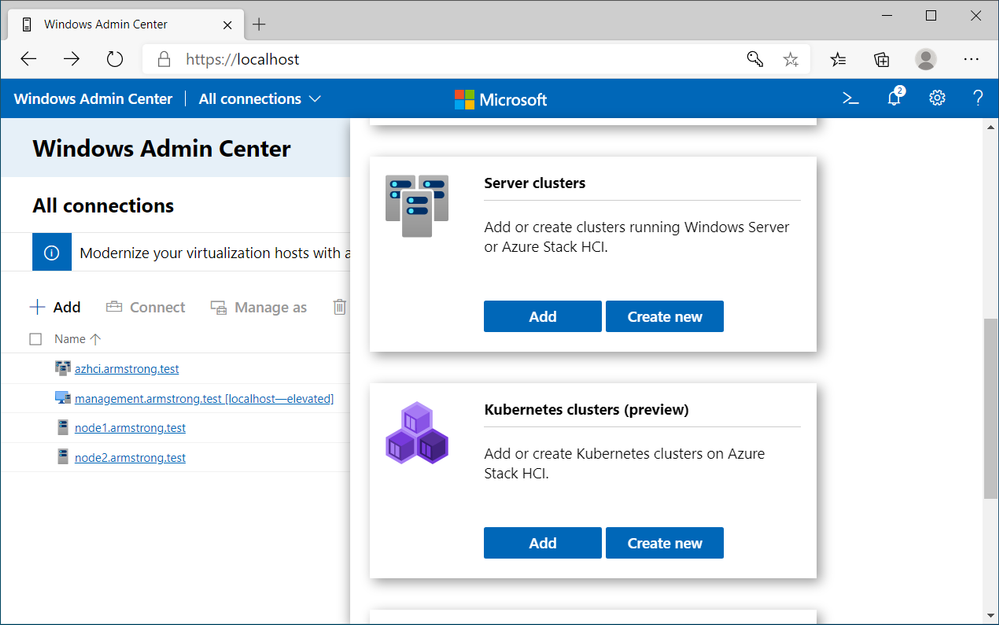
AKS on Azure Stack HCI uses Windows Admin Center and PowerShell to provide an easy to use and familiar deployment experience for any user of Azure Stack HCI. AKS on Azure Stack HCI simplifies the process of setting up Kubernetes on Azure Stack HCI and includes the necessary components to allow you to deploy multiple Kubernetes clusters in your environment.
Which all means that you can focus on what matters most to you – your applications.
AKS on Azure Stack HCI is designed such that every layer is secure. Microsoft provides a secure baseline of all components in AKS on Azure Stack HCI and keeps them up to date. We will be adding mode security features and further hardening the platform over the course of the public preview.
AKS on Azure Stack HCI fully supports both Linux-based and Windows-based containers. When you create a Kubernetes cluster on Azure Stack HCI you can choose whether to create node pools (groups of identical virtual machine, like on AKS) to run Linux containers, Windows containers, or both. AKS on Azure Stack HCI creates and maintains these virtual machines so that you don’t have to directly manage operating systems.
If you have existing .NET applications that you want to modernize, and take advantage of the latest cloud development patterns, AKS on Azure Stack HCI is the platform for you. AKS on Azure Stack HCI provides an industry leading experience for Windows Containers on Kubernetes. We are also working on great tooling and documentation for the process of moving .NET applications from virtual machines to containers with AKS on Azure Stack HCI.
If you are building a new cloud native applications on AKS, AKS on Azure Stack HCI provides to easiest way for you to take those applications and run them in your datacenter. AKS on Azure Stack HCI shares a common code base with AKS, the user experience is consistent across both products, and Microsoft is investing to ensure that applications can move easily between these two environments.
If you are wanting to utilize new Microsoft technologies like Arc enabled Data Services in your datacenter, AKS on Azure Stack HCI delivers a complete solution from Microsoft. It is validated and supported by Microsoft, designed to deliver the best experience for these applications.
You can learn more about AKS on Azure Stack HCI by watching:
Working on this project has been a lot of fun for everyone involved, and we are excited to finally be able to share this with the world. I look forward to seeing what everyone is able to achieve with AKS on Azure Stack HCI!
Cheers,
Ben Armstrong
by Contributed | Sep 24, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
by Contributed | Sep 24, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
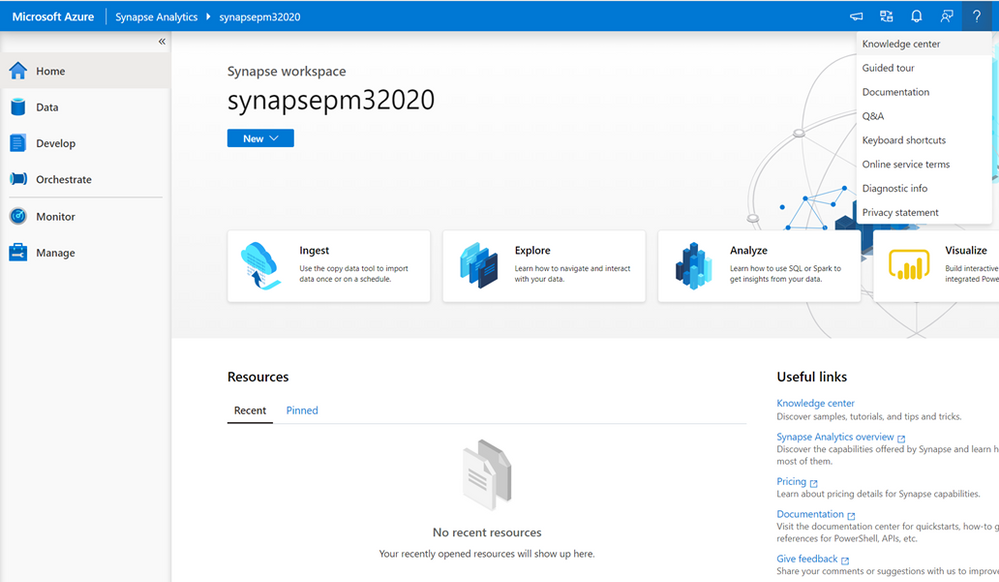
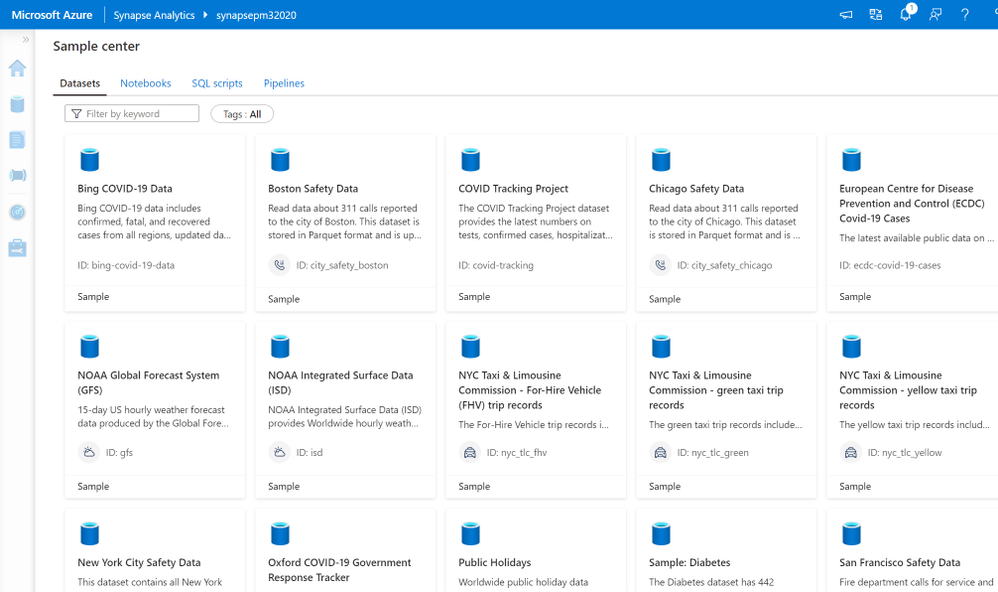
To help users be even more productive with Azure Synapse Analytics, we are introducing the Knowledge center in the Azure Synapse Studio. You can now create or use existing Spark and SQL pools, connect to and query Azure Open Datasets, load sample scripts and notebooks, access pipeline templates, and tour the Azure Synapse Studio − all from one place!
The Knowledge center can be accessed through the Azure Synapse Studio via both “Useful links” in the bottom right of the Homepage on the main navigation and via the “?” icon in the header.

Use samples immediately
The Knowledge center offers several one-click tutorials that create everything you need to instantaneously explore and analyze data.
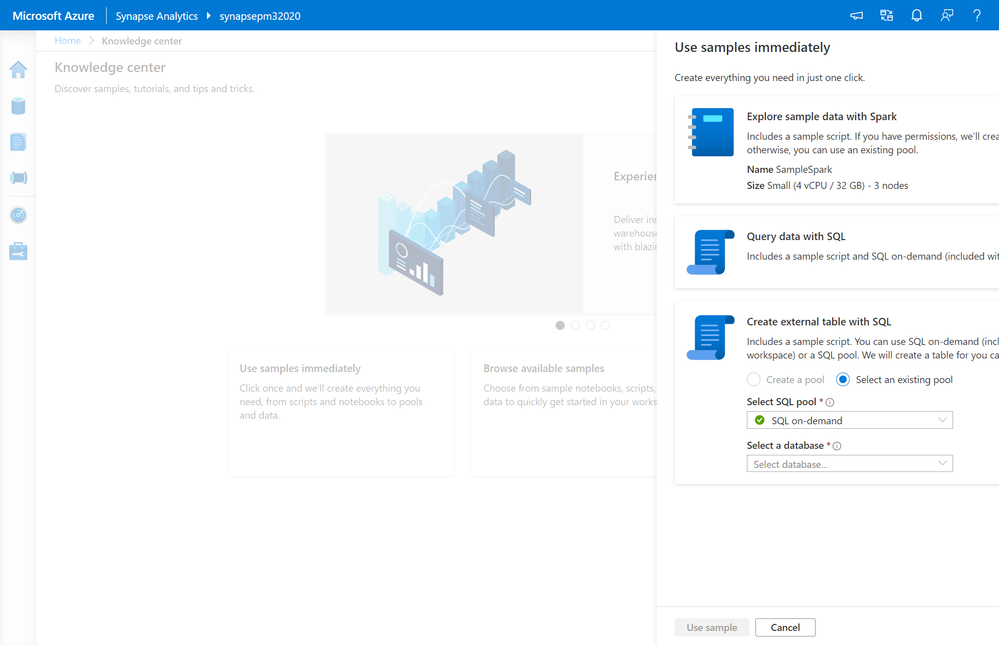
In the “Explore sample data with Spark” tutorial, you can easily use Apache Spark for Azure Synapse to ingest New York City (NYC) Yellow Taxi data and then use notebooks to analyze the data and customize visualizations.
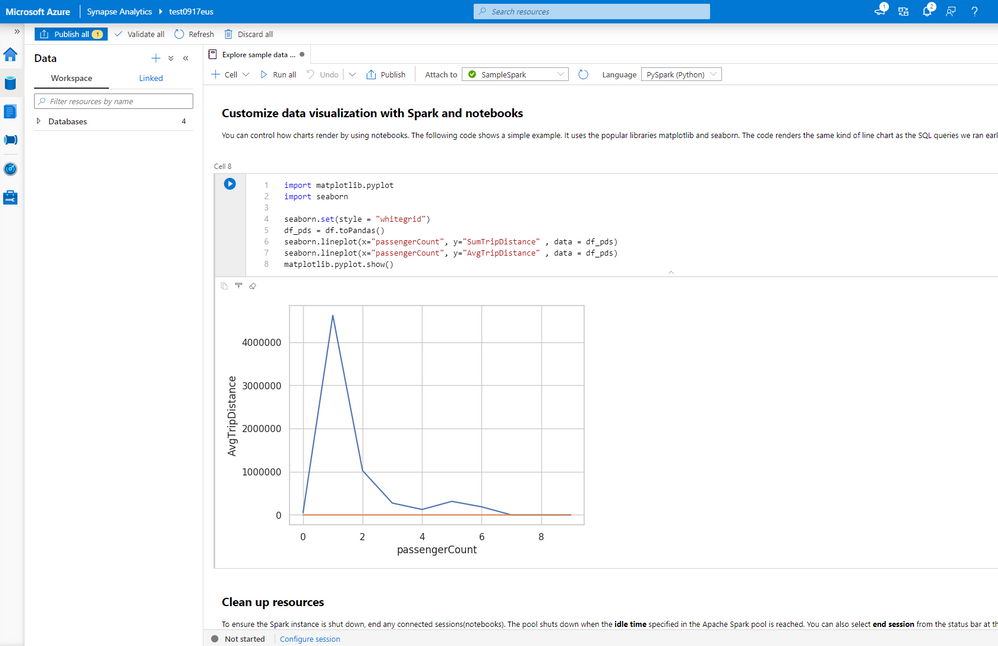
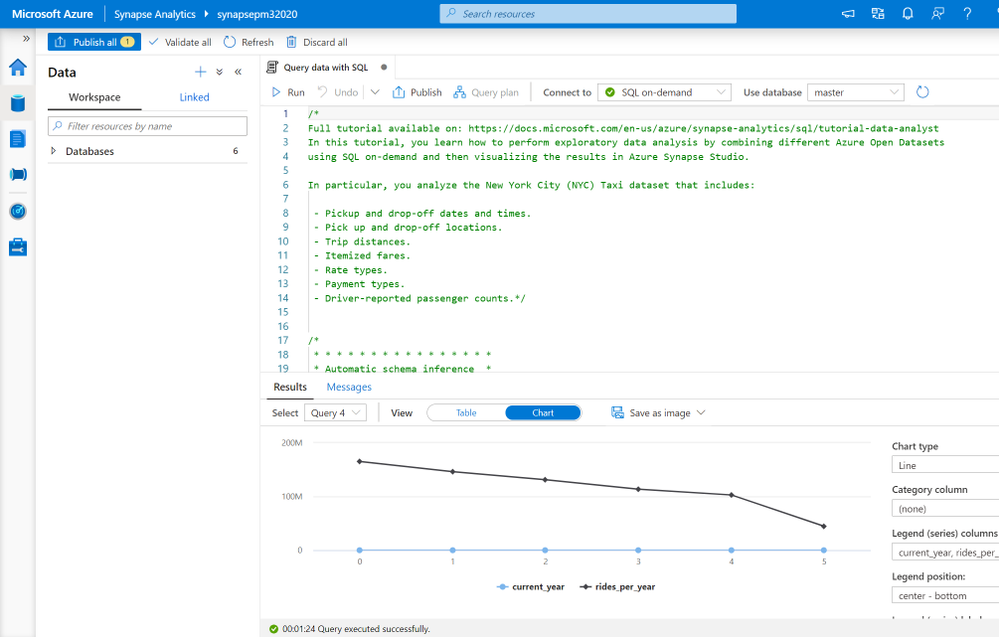
In the “Query data with SQL” tutorial, you can query and analyze data from the NYC Yellow Taxi dataset with a serverless SQL pool, which allows you to use T-SQL for quick data lake exploration without provisioning any additional resources. The tutorial also enables you to quickly visualize results with one click.
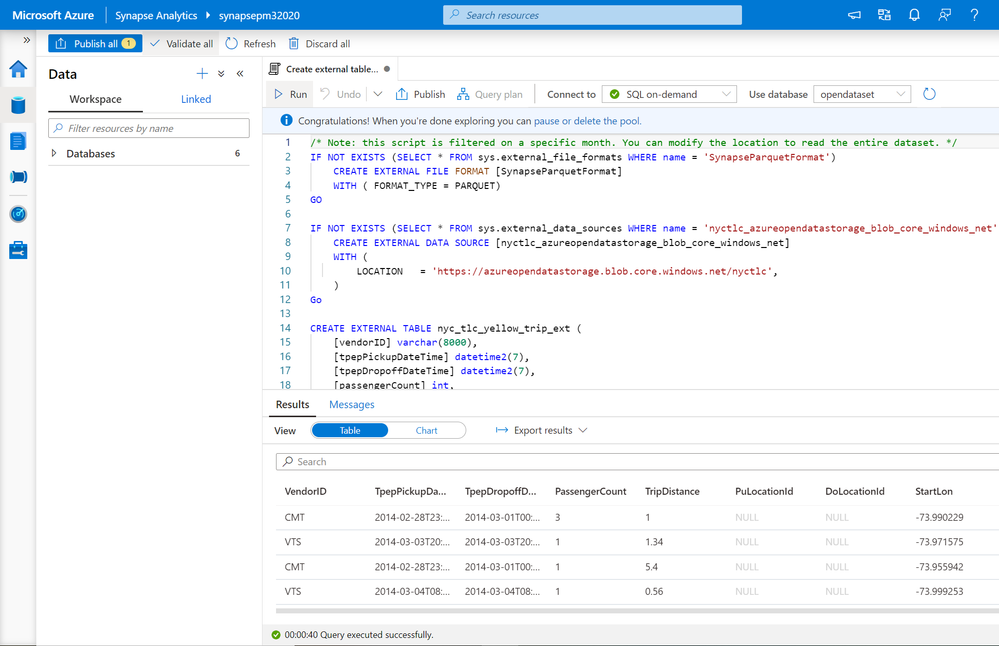
The “Create external table with SQL” tutorial allows you to use either a serverless or dedicated SQL pool to create an external table.
Browse available samples
The new Knowledge center also contains numerous sample datasets, notebooks, scripts, and pipeline templates to allow you to quickly get started. Add and query sample data on COVID-19, public safety, transportation, economic indicators, and more. Regardless of whether you prefer to use PySpark, Scala, or Spark.NET C#, you can get started using a variety of sample notebooks. In addition to sample notebooks, there are samples for SQL scripts like “Analyze Azure Open Datasets using SQL On-demand,” “Generate your COPY Statement with Dynamic SQL,” and “Query CSV, JSON, or Parquet files” along with more than 30 templates for pipelines.
Tour Azure Synapse Studio
The Knowledge center offers a comprehensive tour of the Azure Synapse Studio to help familiarize you with key features so you can get started right away on your first project!
Try the Knowledge center today
by Contributed | Sep 24, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
Join us to hear all about the great new features, announcements, and collaborations for Azure Data Explorer – Azure’s fast, fully- service for real-time analysis of telemetry big data streaming from apps, websites, IoT devices, and more.
One of Azure’s most used services and the foundation of Microsoft’s telemetry platform, Azure Data Explorer , combines broad data exploration and powerful analytical queries with lightning-fast interactivity.
Use Azure Data Explorer to:
- Monitor mission-critical systems.
- Analyze IoT data from thousands of devices.
- Explore and identify trends and anomalies in your data.
- Tune up customer experience.
- And many more exciting capabilities!
Join us to learn how to harness the growing volume of telemetry data to drive business success while keeping costs at bay with the super cost-efficient Azure Data Explorer service.
Capacity is limited to make sure to save your spot today!
Register to our online event to learn about the latest groundbreaking innovations, new features, and exciting collaborations.
The event includes a keynote by Rohan Kumar, CVP, Azure Data and fascinating content by the product group team members, delivering sessions on various topics. See the full agenda below.
Win a brand-new Surface Duo
In every session, one participant will win the newest Surface Duo from Microsoft.
Register now for a chance to enter the contest and win!
When: October 14th, 2020
Where: Wherever you are! The event will be streamed on Teams Live.
1st round: 09:00 BST (London Time)
2nd round: 09:00 PST (US Pacific Time)
Register Now
Agenda
|
Name
|
Description
|
Speakers
|
Duration (Min)
|
|
Opening Session
|
Opening words, brief overview of the agenda and service
|
Oded Sacher, Partner Group Manager
Uri Barash, Principal Group Program Manager
|
15
|
|
Re-imagine Telemetry Analytics, with Rohan Kumar
|
Join us to hear from Rohan Kumar, Corporate Vice President of Azure Data, about the exciting developments with Azure Data Explorer, Microsoft’s telemetry analytics platform that is powering Microsoft’s internal and external business
|
CVP, Azure Data, Rohan Kumar
|
30
|
| |
|
|
|
|
What’s new with ADX
|
Updates on the latest and greatest in ADX ingestion, query, dashboards and more
|
Gabi Lehner, Program Manager
Tzvia Gitlin Troyna, Program Manager
|
30
|
|
Powering Engineering Excellence With Azure Data Explorer
|
Taboola on AzureDataExplorer “It’s magic, interactive & intuitive. My users are in love”
|
Ariel Pisetzky, VP Information Technology & Cyber at Taboola.
|
15
|
|
Start Fast and Accelerate!
The next generation of the Kusto engine
|
Azure Data Explorer engine enhancements.
|
Evgeney Ryzhyk, Partner Software Engineer
Alexander Sloutsky, Principal Engineering Manager
Avner Aharoni, Principal Program Manager
|
30
|
|
|
|
|
|
|
Breakout Sessions– 30 minutes 11:30 – 12:00
All Breakout sessions are running in parallel at the end of Azure Data Explorer engine enhancements session
|
|
|
|
ADX overview
|
Azure Data Explorer is a big data interactive analytics platform for telemetry. Join this session to learn about ADX, where does it fit, when to use it, what are its key features, scenarios and customers
|
Uri Barash, Principal Group Program Manager
Minni Walia, Senior Program Manager
|
|
Enterprise Readiness
|
This session is about all the great features needed to run Azure Data Explorer at enterprise scale. We will cover security, business continuity, high availability CI/CD related details.
|
Henning Rauch, Senior Program Manager
Anagha Khanolkar, Principal Program Manager
|
|
ML, Time Series
|
Anomaly detection, forecasting, diagnostics & RCA for preventive maintenance in IIoT, cloud services and other markets. Training/scoring ML models in ADX using Python.
|
Adi Eldar, Principal Program Manager
Manoj Raheja, Principal Program Manager
Roy Ofer, Senior Data Scientist
|
|
Operating ADX optimally: Cost and performance
|
Choosing optimal SKU for your workload and utilizing auto-scale can significantly reduce your cluster cost. Join us for a deep dive session where we drill into the different cost reducing options.
|
Avner Aharoni, Principal Program Manager
Deepak Agrawal, Senior Program Manager
Guy Reginiano, Program Manager
|
|
Ingestion
|
In this session we will focus on ingestion methods, how to choose the right method to your customer scenario, and what are the available options
|
Vladik Branevich, Principal Engineering Manager
Tzvia Gitlin Troyna, Senior Program Manager
|
|
Visualizing big data
|
Overcoming scale and performance challenges when building dashboards solution in big data scenarios
|
Gabi Lehner, Principal Program Manager
Olga Goldenberg, Senior Program Manager
|
Please share and subscribe,
Azure Data Explorer
by Contributed | Sep 24, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
Azure Kubernetes Service on Azure Stack HCI (AKS-HCI) is an on-premises implementation of the popular Azure Kubernetes Service (AKS) orchestrator, which automates running containerized applications at scale. AKS on Azure Stack HCI enables developers and admins to deploy and manage Linux and Windows containerized apps on Azure Stack HCI.
With AKS-HCI, enterprises can take advantage of consistent AKS experience across cloud and on-premises environments, extend to Azure with hybrid capabilities, run apps with confidence through built-in security, and use familiar tools to modernize Windows apps. For a more detailed overview of AKS-HCI capabilities, refer to this blog.
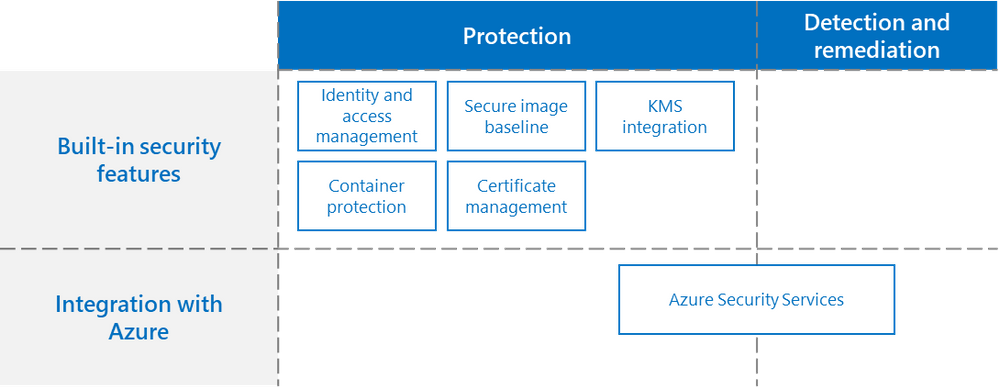
One of the core strengths of AKS-HCI is using security-first approach. At Microsoft, we believe that leading with strong security posture is table stakes for an enterprise-grade offering. Our security roadmap is comprehensive, starting with a mindset of placing strong protection guardrails and bolstering that with industry-hardened threat detection, and remediation and recovery. The protection-related hardening is built into AKS-HCI. To bring threat detection and remediation, and we integrate with security management systems such as Azure Security Center.
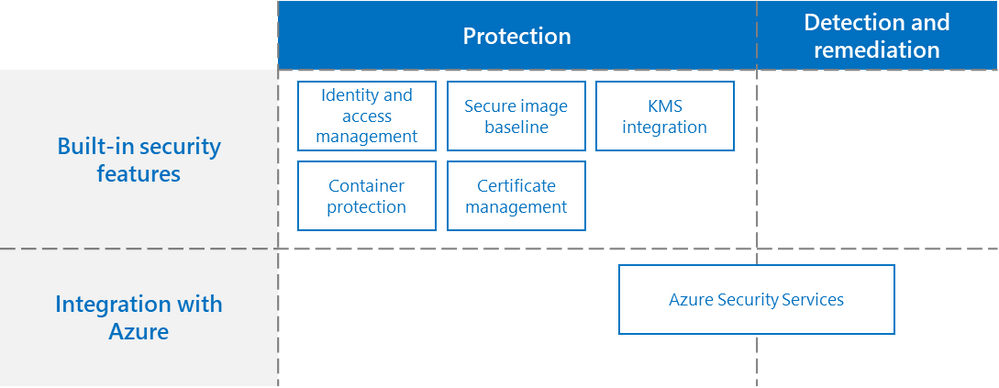
Figure 1. Securing AKS-HCI Deployment
In this blog, we will describe the security capabilities in AKS-HCI. These security features are not available in the current public preview version, but these and more will be released in the lead-up to general availability.
Secure image baseline and container protection
Microsoft provides a secure baseline for Windows and Linux container host images and services the updates of those images to maintain consistency and standards.
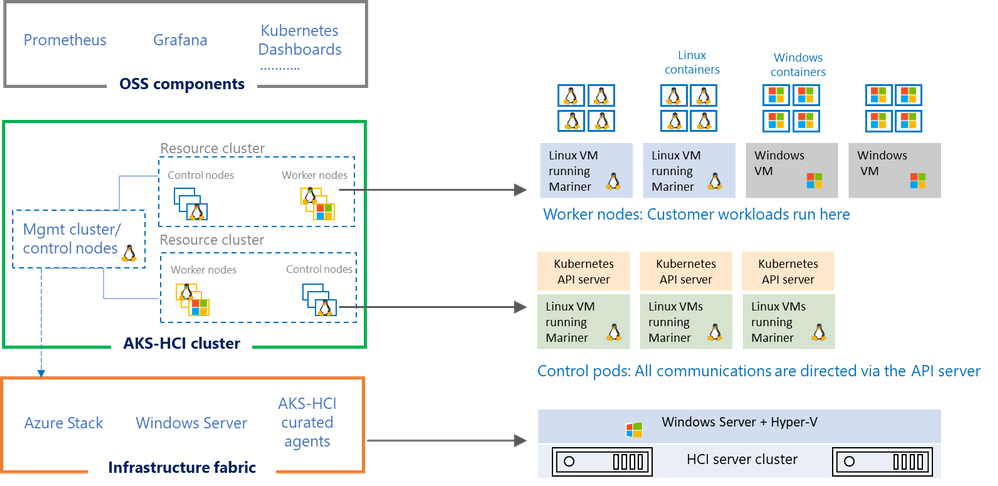
Figure 2. AKS-HCI implemented with hypervisor isolation
AKS-HCI is designed such that every layer is secure. The container host is deployed as a virtual machine. Each tenant cluster runs on its dedicated set of container hosts and uses the same strong Hyper-V-based isolation used in Azure which provides the strong kernel isolation among the container hosts.
In addition, AKS-HCI has multiple layers of protection built in. The first cluster to be bootstrapped is the management cluster, which is then used to bootstrap other tenant clusters. The container pods are run within Hyper-V virtual machines, enforcing strong isolation guarantees wherein the impact of a compromised container or pod is contained within the Hyper-V VM itself.
Identity and access management (IAM)
AKS-HCI integrates with Active Directory (AD), providing strong identity and facilitating seamless single sign-on (SSO) to manage the AKS-HCI environment and deploy the container workloads. Additionally, there is provision for Windows containerized application workloads to be bootstrapped with group Managed Service Account (gMSA) identity. gMSA is an AD-managed service account for which the passwords are automatically rotated.
Secure communication and secrets Management
Communication between the control plane components is protected by Transport Layer Security (TLS). AKS-HCI comes with zero-touch, out-of-the-box provisioning, and management of certificates for the infrastructure and Kubernetes built-in components. Additionally, the Kubernetes secrets are encrypted at rest using strong Advanced Encryption Standard (AES), with the ability to rotate the key encryption keys (KEK).
Integration with Azure security assets
AKS-HCI is integrated into the Microsoft security ecosystem, which allows extending Azure security constructs such as Azure Container Registry and Azure policies. In the future, integration with Azure assets like Azure Security Center will provide customers the ability to monitor for threats and offer pre- and post-runtime security assessments for both the infrastructure fabric and the Kubernetes cluster. This helps in monitoring for threats and keeping a strong security posture.
Join us in this journey
Security is a journey, not a destination. These are just some of the security features that we are working on and making generally available (GA) soon. AKS-HCI is going to be continually updated like a service. We will add more security features and continue to further harden the platform. Join us in this journey: we would love to hear feedback, experience, and insights on security. Be part of discussions in our Github repository.
by Contributed | Sep 24, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
Now more than ever, organizations are challenged with keeping their employees productive working remotely and interacting with their customers over digital channels. At the same time there has been an increase in evolving digital security threats as bad actors recognize an opportunity to disrupt your business. Moreover, security resources are stretched, and prioritization is important.
To help you protect all the assets within your organization earlier this week we announced Microsoft Defender. Microsoft Defender delivers comprehensive threat protection spanning users, devices, apps, data, servers, IoT devices, Operational Technology (OT), and more. Microsoft Defender is Microsoft’s leading Extended Detection and Response (XDR) solution for threat protection across all your technical assets composed of two experiences: Microsoft 365 Defender and Azure Defender. Azure Defender is an evolution of the threat protection technologies in Azure Security Center, protecting Azure and hybrid environments. With this announcement, we are rebranding the offerings previously called advanced threat protection services in Azure Security Center as Azure Defender. For example, Advanced Threat Protection for Azure Storage is now Azure Defender for Storage.
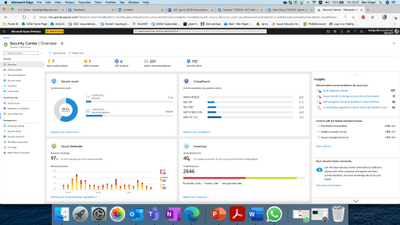
1. Updated Azure Security Center UI
Following this rebranding, and in order to better reflect the different value pillars that Azure Security Center offers, we have also changed the main Security Center product experience. With the new experience, Security Center serves as the central overarching experience that includes multiple independent cloud security pillars such as Azure Secure Score, Regulatory Compliance and of course Azure Defender. In addition, each of these pillars has its own dedicated dashboard allowing deeper insights and actions around that vertical. Changes to the product can be seen at the following link (http://aka.ms/ascignite2020) during the conference and will be integrated into the product after Ignite 2020.

Figure 1: Azure Security Center Overview window
When you click on the Azure Defender dashboard, you can see that you have better visibility into Azure Defender coverage across your different resource types, visibility into onboarding state & agent installation and a holistic view of the threat detection alerts included in Azure Defender.
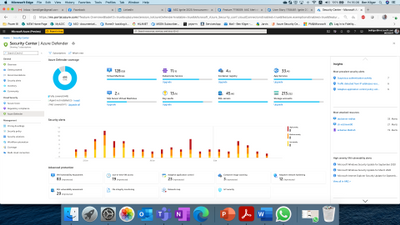
Figure 2: Azure Defender dashboard
2. Protection for multi cloud workloads (AWS & GCP)
As more organizations manage cloud workloads on multiple cloud platforms, they require a security solution that provides visibility & protection across all their cloud environments. To enable that, Security Center is announcing a public preview for protection of workloads in AWS & GCP –
- Customers will be able to onboard their AWS/GCP accounts into ASC.
- Security Center will include detected misconfigurations and findings from AWS Security Hub and GCP Security Command Center into its Secure Score model and Regulatory Compliance experience, thus providing a central pane to visualize security posture across multi-cloud assets.
- Azure Defender for Servers will leverage Azure Arc to extend its support for VMs in AWS & GCP including capabilities such as automatic agent provisioning, policy management, vulnerability management, embedded EDR and more., embedded EDR and more.
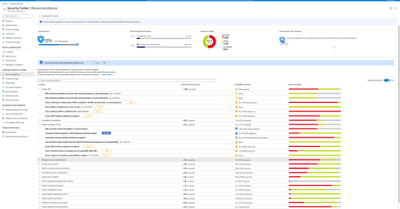
Figure 3: Secure Score Recommendations page including AWS and GCP recommendations
We are also delighted to announce the preview availability of Azure Arc enabled SQL Servers and its integration with Azure Defender and Azure Sentinel. With Azure Arc enabled SQL Server you can now protect SQL Servers anywhere (on-premises, and in other clouds such as AWS, GCP) the same way you protect Azure SQL directly from the Azure portal for a unified, hybrid security experience using Azure Defender. This unified experience simplifies protecting your entire SQL estate. In addition, your security operations team can take the threat information from Azure Security Center and surface it into Azure Sentinel, the industry’s first cloud native SIEM, where when combined with security intelligence from throughout your enterprise, you can now detect and mitigate threats that may traverse laterally across your hybrid environments before attackers have the opportunity to exfiltrate data.
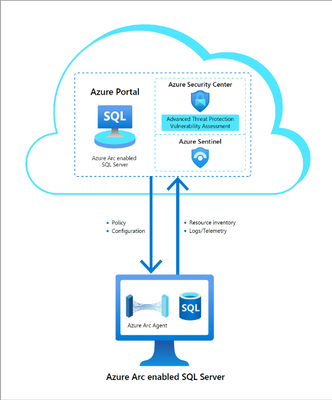
Figure 4. Integration of Azure Arc enabled SQL Server and Azure Security Center
3. Containers Enhancements
As containers and specifically Kubernetes are becoming more widely used, we are extending our Azure Defender for Kubernetes offering to include Kubernetes level policy management, hardening and enforcement with admission control to make sure that Kubernetes workloads are created secure by default. In addition, Container image scanning by Azure Defender for Container Registries will now support continuous scanning of container images in the Azure Container Registry and re-evaluate registry images for new vulnerabilities to minimize the exploitability of running containers.
4. General availability for more platform protection
We are announcing the general availability of Azure Defender for Key Vault and for Azure Defender for Storage protection for Azure Files and Azure Data Lake Storage Gen2.
5. Azure Defender for IoT, Now With CyberX Agentless Technology
At Ignite, we’re announcing Public Preview of new capabilities for securing Operational Technology (OT) environments such as manufacturing, building automation, life sciences, energy and water utilities, oil & gas, and warehousing & logistics.
Incorporating agentless technology from Microsoft’s recent acquisition of CyberX, Azure Defender for IoT enables organizations to auto-discover their IoT/OT assets, identify critical vulnerabilities, and continuously monitor for threats. It will initially be available for on-premises deployments, with an Azure-based console to follow. Read more.
Azure Security Center cloud security posture management enhancements
Azure Security Center continues to provide cloud security posture management enhancements. At Ignite this year, we are announcing general availability for the new Asset Inventory experience. The new experience enables customers to explore their security posture data in a much deeper way, providing view, filter and query abilities for all details and insights across all resources protected by ASC, via an easy to use and crystal clear user interface.
This new experience is fully built on top of Azure Resource Graph (ARG) which now holds all of ASCs security posture data, and leveraging its powerful KQL engine enables customers to quickly and easily reach deep insights on top of ASC data and cross reference with any other resource properties.
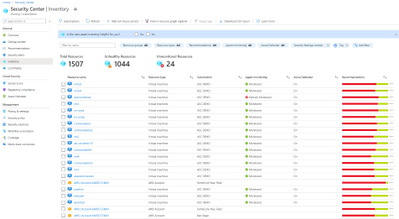
Figure 5: Azure Security Center Inventory view
We are also very excited to announce the public preview of a more fine-grained ability to manage and control security recommendations and their application on one’s resources. This includes ability to exempt specific resources from specific security recommendations, with documented reasoning and easy monitoring of exemptions. Another advanced capability is to customize security findings either by configuring which findings should be applicable, such as by severity, type, name or any other category. This allows maximum flexibility of adjusting the security recommendations to the organization’s policy and priorities and by that better representation of their security posture in Secure Score.
For related material, see the following articles:






Recent Comments