
by Contributed | Oct 15, 2020 | Azure, Technology
This article is contributed. See the original author and article here.
You want to use Just In Time access for Azure VMs, but do not want the users to select all available IPs when requesting the access. Try this policy out to prevent this from happening:
{
"mode": "All",
"policyRule": {
"if": {
"allOf": [{
"field": "type",
"equals": "Microsoft.Network/networkSecurityGroups"
}, {
"count": {
"field": "Microsoft.Network/networkSecurityGroups/securityRules[*]",
"where": {
"allOf": [{
"field": "Microsoft.Network/networkSecurityGroups/securityRules[*].sourceAddressPrefix",
"equals": "*"
}, {
"field": "Microsoft.Network/networkSecurityGroups/securityRules[*].access",
"equals": "Allow"
}, {
"field": "Microsoft.Network/networkSecurityGroups/securityRules[*].direction",
"equals": "Inbound"
}, {
"field": "Microsoft.Network/networkSecurityGroups/securityRules[*].name",
"contains": "SecurityCenter-JITRule"
}, {
"anyOf": [{
"field": "Microsoft.Network/networkSecurityGroups/securityRules[*].destinationPortRange",
"equals": "22"
}, {
"field": "Microsoft.Network/networkSecurityGroups/securityRules[*].destinationPortRange",
"equals": "3389"
}, {
"field": "Microsoft.Network/networkSecurityGroups/securityRules[*].destinationPortRanges",
"equals": "22"
}, {
"field": "Microsoft.Network/networkSecurityGroups/securityRules[*].destinationPortRanges",
"equals": "3389"
}]
}]
}
},
"greater": 0
}]
},
"then": {
"effect": "deny"
}
},
"parameters": {}
}
More details and comments/issues can be found here: Github: deny-wildcard-source-for-just-in-time-requests

by Contributed | Oct 15, 2020 | Azure, Technology
This article is contributed. See the original author and article here.
Staying “current” with the always evolving Azure platform is not an easy task. Here are some tricks and websites to make this a little bit easier:
Azure Learning Paths & Certifications
https://docs.microsoft.com/en-us/learn/azure/
The learning paths are super helpful to discover and master Azure topics – they are free but still very high quality. Once you have done some learning paths, I highly recommend getting Azure certifications – looks great in the CV and helps you speak the ‘Azure language’.
Azure Friday
Is it Friday again? The time of the week to stay current with short information presented from Scott Hanselman in ‘Azure Friday’! In these easy to digest 10-15 min videos Scott and his guests will present the best and latest in azure technologies and beyond.
Go subscribe to never miss an episode!
https://azure.microsoft.com/en-us/resources/videos/azure-friday/
Podcasts
Are you learning with your ears? Travelling a lot? Then maybe subscribe to an Azure podcast to stay current – the mentioned Azure Friday is available, too.
https://channel9.msdn.com/Shows/Azure-Friday
Or ‘The Azure Podcast’ going back till 2013 with lots of Azure engineers sharing their expertise:
http://azpodcast.azurewebsites.net/
Azure Community: Events & Social Media
A while back I would have recommended to attend local community events, user groups or Azure Saturday’s – most of them are fully virtual and its always great to connect with like-minded people: https://azure.microsoft.com/en-us/community/events/
Additionally, follow Azure engineers, PMs, advocates on Azure – the folks are very easy to reach there: https://twitter.com/azure
Azure Updates
https://azure.microsoft.com/en-us/updates/
Lastly, Azure updates – the central place for all new and updated Azure things. A must if you want to have the latest news, features and sometimes even retirements.
You have other tricks? Things that work for you?
Share them in the comments!
Hope it helps,
Max
by Contributed | Oct 15, 2020 | Azure, Technology
This article is contributed. See the original author and article here.
In this episode with Drew Skwiers-Koballa, you will be introduced to a new experience for database development with the SQL Database Projects extension for Azure Data Studio. Whether you are familiar with SQL Server Data Tools (SSDT) or new to SQL projects, you can start editing and building SQL projects in Azure Data Studio on Windows, macOS, and Linux.
Watch on Data Exposed
Resources:
View/share our latest episodes on Channel 9 and YouTube!

by Contributed | Oct 15, 2020 | Azure, Technology
This article is contributed. See the original author and article here.

Summary: Agentless security for unmanaged IoT/OT devices
As industrial and critical infrastructure organizations implement digital transformation, the number of networked IoT and Operational Technology (OT) devices has greatly proliferated. Many of these devices lack visibility by IT teams and are often unpatched and misconfigured, making them soft targets for adversaries looking to pivot deeper into corporate networks.
Business risks include financial losses due to production downtime, corporate liability from safety and environmental incidents, and theft of sensitive intellectual property such as proprietary formulas and manufacturing processes.
Incorporating agentless, IoT/OT-aware behavioral analytics from Microsoft’s recent acquisition of CyberX, Azure Defender for IoT addresses these risks by discovering unmanaged IoT/OT assets, identifying IoT/OT vulnerabilities, and continuously monitoring for threats.
Azure Defender for IoT is now available in public preview for on-premises deployments, with the option of connecting securely to Azure Sentinel to eliminate IT/OT silos and provide a unified view of threats across both IT and OT environments. It also integrates out-of-the box with third-party tools like Splunk, IBM QRadar, and ServiceNow.
Introduction
Announced at Ignite 2020, Azure Defender for IoT delivers agentless security for continuously monitoring OT networks in industrial and critical infrastructure organizations.
You can deploy these capabilities fully on-premises without sending any data to Azure. using our new native connector to integrate IoT/OT alerts into Azure Sentinel, benefiting from the scalability and cost benefits of the industry’s first cloud-native SIEM/SOAR platform.
Microsoft offers a number of end-to-end IoT security solutions for managed (or “greenfield”) IoT deployments, including Azure IoT Hub, Azure Sphere and micro-agents for embedded operating systems. However, most of today’s IoT/OT devices are “unmanaged” because they do not get provisioned, are not monitored, and lack built-in security such as agents or automated updates.
As a result, most IT security organizations have limited or no visibility into their OT networks. What’s more, these devices are often unpatched and misconfigured, making them soft targets for adversaries looking to pivot deeper into corporate networks.
Network security monitoring tools developed for IT networks are unable to address these environments because they’re blind to specialized industrial protocols (Modbus, DNP3, BACnet, etc.). They also lack an understanding of the specialized device types, applications, and machine-to-machine (M2M) behaviors in IoT/OT environments.
Key capabilities
Azure Defender for IoT enables IT and OT teams to auto-discover their unmanaged IoT/OT assets, identify critical vulnerabilities, and detect anomalous or unauthorized behavior — without impacting IoT/OT stability or performance.
Azure Defender for IoT delivers insights within minutes of being connected to the network, leveraging patented IoT/OT-aware behavioral analytics and machine learning to eliminate the need to configure any rules, signatures, or other static IOCs. To capture the traffic, it uses an on-premises network sensor deployed as a virtual or physical appliance connected to a SPAN port or tap. The sensor implements non-invasive passive monitoring with Network Traffic Analysis (NTA) and Layer 7 Deep Packet Inspection (DPI) to extract detailed IoT/OT information in real-time.
You also benefit from out-of-the box integration with third-party IT security tools like Splunk, IBM QRadar, and ServiceNow. Plus, it’s designed to fit right into existing OT environments, even across diverse automation equipment from all major OT suppliers (Rockwell Automation, Schneider Electric, GE, Emerson, Siemens, Honeywell, ABB, Yokogawa, etc.).
Integration with existing SOC workflows is key to removing IT/OT silos while delivering unified monitoring and governance across both IT and OT. To help automate this complex security challenge, we’ve also beefed up Azure Sentinel with IoT/OT-specific SOAR playbooks and
Combined with previous support in Azure Security Center for IoT for protecting managed IoT/OT devices connected via Azure IoT Hub, these new capabilities enable organizations to accelerate their digital transformation initiatives with a combined solution for both unmanaged and managed devices.
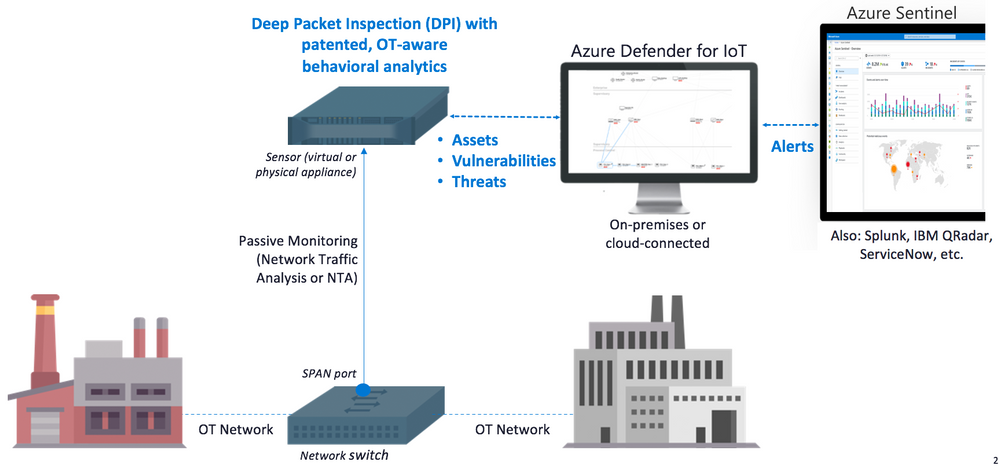
Rapid non-invasive deployment leveraging patented IoT/OT-aware behavioral analytics, available either for on-premises or Azure-connected environments.
Real-time threat alerts provided by Azure Defender for IoT (examples)
- Unauthorized device connected to the network
- Unauthorized connection to the internet
- Unauthorized remote access
- Network scanning operation detected
- Unauthorized PLC programming
- Changes to firmware versions
- “PLC Stop” and other potentially malicious commands
- Device is suspected of being disconnected
- Ethernet/IP CIP service request failure
- BACnet operation failed
- Illegal DNP3 operation
- Master-slave authentication error
- Known malware detected (e.g., WannaCry, EternalBlue)
- Unauthorized SMB login
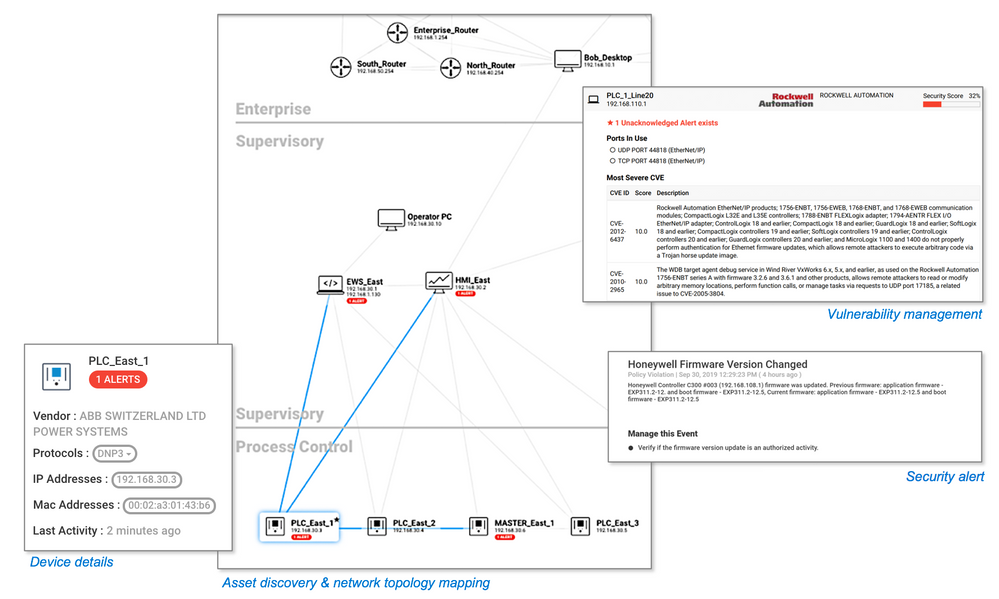
Azure Defender for IoT provides holistic IoT/OT security including asset discovery, vulnerability management, and continuous threat monitoring, combined with deep Azure Sentinel integration.
Try it now at no charge
Try Azure Defender for IoT during public preview. This version includes the agentless security provided via the integration of CyberX, plus the ability to connect to Azure Sentinel. And please give us your feedback in the IoT Security Tech Community.
Learn more with these educational resources
by Contributed | Oct 15, 2020 | Azure, Technology
This article is contributed. See the original author and article here.
We have a number of customers that leverage the benefits offered by the SQL IaaS extension which I had blogged about a few days ago. One of the common feedback was the effort required to enable the extension for multiple VMs especially if you were running multiple SQL Server on Azure VM instances. We have created an easy option for customers to enable the SQL IaaS extensions on all SQL Server virtual machines in an Azure subscription using a feature called Automatic Registration.
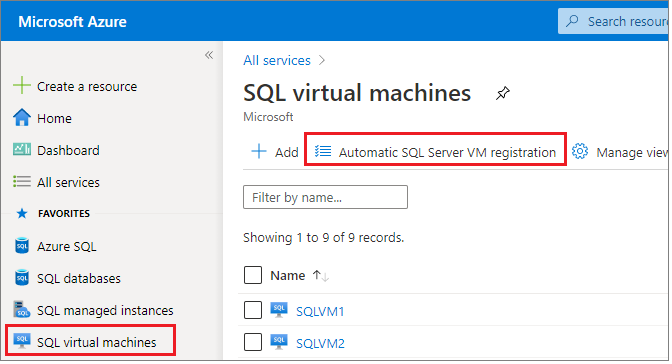
To enable automatic registration of your SQL Server VMs in the Azure portal, follow the steps:
Sign into the Azure portal.
Navigate to the SQL virtual machines resource page.
Select Automatic SQL Server VM registration to open the Automatic registration page as shown in the screenshot below.
Choose your subscription from the drop-down.
Read through the terms and if you agree, select I accept.
Select Register to enable the feature and automatically register all current and future SQL Server VMs with the SQL VM resource provider. This will not restart the SQL Server service on any of the VMs.

If you need to enable this option on multiple Azure subscriptions, then you can leverage this PowerShell script on GitHub to enable this option for a list of subscriptions.
We also introduced new Reporting Services virtual machine images for SQL Server 2016, 2017 and 2019. Now customers have the ability to deploy a Reporting Services virtual machine (SSRS) using Standard and Enterprise edition using pre-configured image types for ease of deployment. This also introduces the choice to deploy a SSRS virtual machine with flexible licensing model using Pay As You Go pricing or leverage your Software Assurance license mobility or Azure Hybrid Benefit when deploying on an Azure virtual machine.
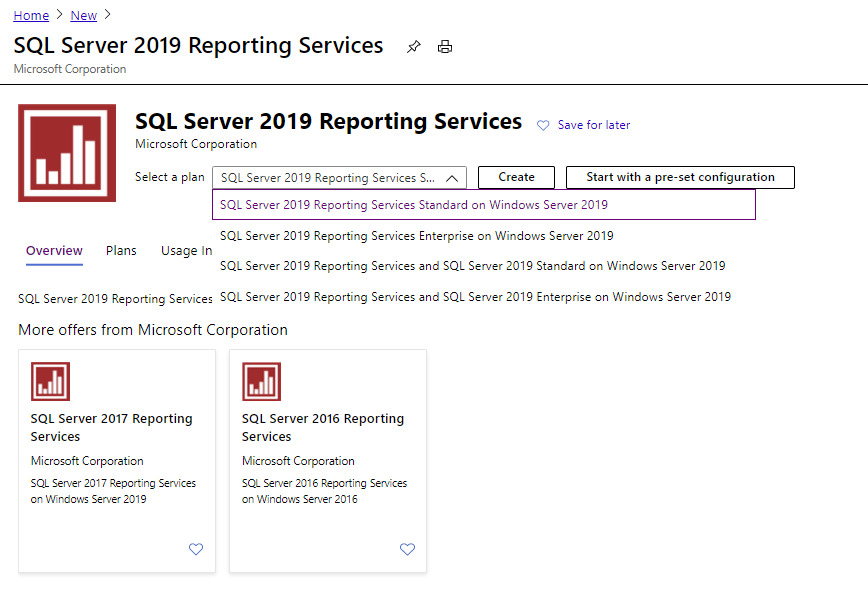
Now you have the ability to move your database engine and reporting workloads into Azure virtual machines using our pre-configured images and automate the entire process using ARM templates. This saves you the time to install reporting services and configure it separately.
by Contributed | Oct 15, 2020 | Azure, Technology
This article is contributed. See the original author and article here.
I’ve talked to customers about migrating their workloads to Azure for a number of years now and at some point in the conversation we’ll start to mention where can cost savings can be made and one place that organisations can explore is the Azure Hybrid Benefit (formally Azure Hybrid Use Benefit) offers.
Windows
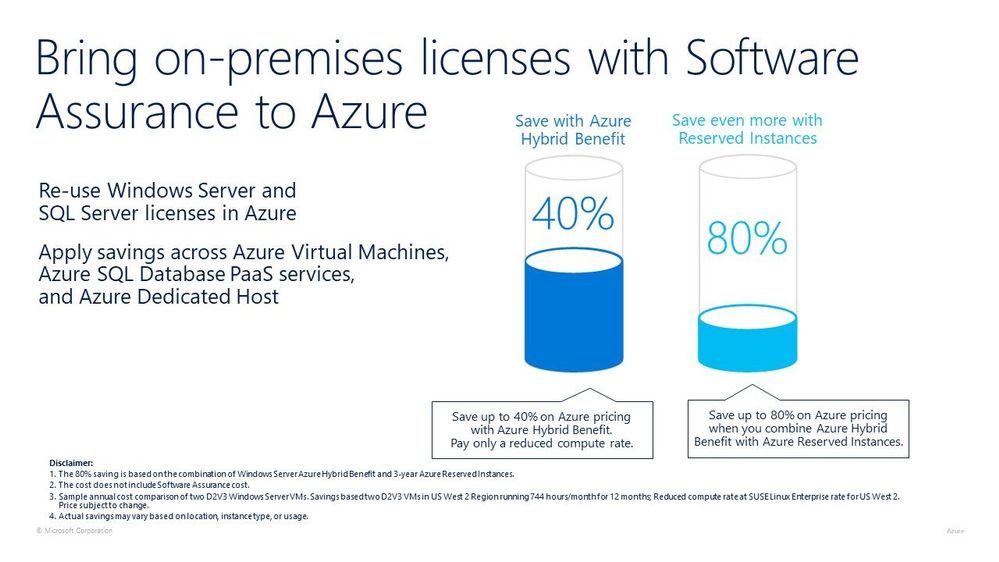
When you migrate or run your Windows workloads within Azure you can leverage your on prem Software Assurance licenses on Azure. Using Hybrid Benefit is supported on all Azure regions and also on virtual machines (VM) that are running SQL or third party marketplace software. You can also use it on Azure Dedicated Host.
You can apply the offer to your VM when you create it or to your existing VMs.
SQL
Customers with Software Assurance with their SQL license also have the option to use those license when they run SQL on an Azure Virtual Machine. You aren’t just constrained to using the license on Infrastructure as a Service (IaaS) implementation, there is also a chance to save up to 30 percent or even higher on SQL Database & SQL Managed Instance by using your SQL Server licenses with Software Assurance.
 Azure Hybrid Benefit
Azure Hybrid Benefit
Linux
At Microsoft Ignite 2020, the team announced a new Azure Hybrid Benefit program, which is in preview. This new program allows you to use your on prem Red Hat Enterprise Linux (RHEL) and SUSE Linux Enterprise Server (SLES) licenses within Azure. The benefit is applicable to all RHEL and SLES Marketplace pay-as-you-go (PAYG) images.
If you wish to use the Red Hat benefit you need to apply to become part of the program. To get started with the SUSE program you need to apply here.
Call to Action
If you are looking for more information on the Azure Hybrid Benefit offer, a great place to start is the FAQ the team have configured. Also check out the Azure Hybrid Benefit Saving Calculator which can help you determine what your cost savings will be.







Recent Comments