ProcMon 3.80, Sysmon 13.20, TCPView 4.10, ProcExp 16.40, PsExec 2.34, Sigcheck 2.81 and WinObj 3.10
This article is contributed. See the original author and article here.
This article is contributed. See the original author and article here.

This article is contributed. See the original author and article here.
SharePoint Syntex brings advanced AI-powered content management to SharePoint & Microsoft 365. We’re continuing to work with our customers and partners to make updates and improvements. Here are the latest updates to support powerful AI models that transform content into knowledge.

Coming soon, you can automatically set sensitivity labels in document understanding models. This is in addition to the ability to automatically apply retention labels. Applying sensitivity labels (aka Microsoft Information Protection or “MIP” labels) enables you to classify and protect your organization’s data, while making sure that productivity isn’t hindered.
Automatic sensitivity labels are important because:
These changes will start to rollout to Targeted Release users in May 2021, and can be tracked on the Microsoft 365 Public Roadmap ID 81975.
This month we also added a new regular expression (RegEx) explanation type, allowing you to provide more complex explanations when training a model. This update includes a set of RegEx explanation templates that can be used or edited like other explanation templates, such as date, currency, and phone number.
Regular expressions provide a powerful, flexible, and efficient method for processing text. The extensive pattern-matching notation of regular expressions enables you to quickly parse large amounts of text to find specific character patterns.
This update will also start rollout to Targeted Release users in May 2021, and can be tracked on the Microsoft 365 Public Roadmap ID 81976.
We’re thrilled to announce the release of or Syntex developer community n GitHub. Visit our GitHub repository for Syntex community work to get community samples that demonstrate different usage patterns of Document Understanding models in Syntex. To start you off, we included four samples focused on benefit changes, contract notices, services agreements, and trade confirmations.
The samples in this repository contain both the Document Understanding model files, as well as the files used to train the model. Once imported in your Syntex Content Center site, you’ll be able to use these models to process files, as well as view and edit the key model elements – the classifier and extractors – to match your needs. If you want to further deploy the model, then checkout the Deploying Models article to learn more.
You can also use this repository to submit a community contribution, view the issue list, and participate in a discussion forum.
We’re continuing to improve and enhance SharePoint Syntex and we’ll share new features with you as they become available. To stay up to date on Knowledge and Content Services, and products updates like those listed here, subscribe to the Microsoft Viva newsletter.

This article is contributed. See the original author and article here.
 Microsoft Viva Connections brings the next generation, personalized, Intranet to where people work… namely within Microsoft Teams. In this HLS Show Me How post Microsoft’s Scott Moore and Michael Gannotti walk you through all the elements of setting up and deploying Microsoft Viva Connections.
Microsoft Viva Connections brings the next generation, personalized, Intranet to where people work… namely within Microsoft Teams. In this HLS Show Me How post Microsoft’s Scott Moore and Michael Gannotti walk you through all the elements of setting up and deploying Microsoft Viva Connections.
Covered in these videos:
Set up an organizational Home Site in SharePoint Online
Create the Microsoft Viva Connections Package
Upload the Microsoft Viva Connections Package to Microsoft Teams
Setup the Viva Connections App in Microsoft Teams Admin Center under App setup policies/Global
Resources:
Thanks for visiting – Michael Gannotti LinkedIn | Twitter
Michael Gannotti
This article is contributed. See the original author and article here.
Every day in Azure, we spend time working with customers who are bringing mission critical enterprise workloads to Kubernetes with AKS. Their requirements drive our roadmap, ensuring that we are balancing the innovative capabilities of the cloud native ecosystem with the requirements of some of the world’s largest companies.
Many AKS customers are subject to the compliance requirements of a specific industry, such as finance, healthcare, or government services. Meeting those requirements can be onerous at the best of times, but it can be even more difficult to do in the context of Kubernetes, where patterns are nascent and flexibility is limited. To help address this challenge, we are announcing AKS for regulated industries, a collection of guidance, benchmarks, and best practices that makes it simpler for customers subject to those constraints to be successful on AKS. This includes a baseline cluster architecture for regulated industries, specific guidance for customers seeking Payment Card Industry (PCI) compliance, and an AKS-specific security benchmark published by the Center of Internet Security (CIS).
In support of that initiative, we are also pleased to announce a series of new product capabilities that will help customers deliver mission critical workloads with Kubernetes on Azure. First, we are excited to become the first cloud provider to offer integrated Kubernetes agent nodes meeting the Federal Information Processing Standards (FIPS) compliance bar, now available in public preview. With a single CLI flag and at no extra charge, AKS customers can now obtain a version of Ubuntu 18.04 that includes the necessary components for their agent nodes to be FIPS compliant. Windows Server-based agent nodes will follow in just a couple of weeks. Speaking of agent nodes, we are also announcing today the general availability of host-based encryption for AKS agent nodes. This capability provides an additional layer of security as OS, temp, and data disks can now be automatically encrypted with either platform or customer-managed keys. Finally, we are pleased to announce the general availability of Azure role-based access control (RBAC) for Kubernetes. This capability allows customers to manage granular access to AKS and Arc-connected Kubernetes clusters at scale leveraging the same framework that they use for all other Azure resources.
Of course, when it comes to meeting the needs of the enterprise, security is just one piece of the picture. Today, we are excited to announce several other capabilities designed meet the needs of our largest customers. We recently announced previews for cluster auto-upgrade, the ability to have AKS automatically trigger upgrade of your clusters, and planned maintenance, the ability to signal to the service when you would prefer to have potential impactful maintenance operations occur. Now, you can combine those two features with the integration of auto-upgrade with planned maintenance, ensuring that any potential disruptions from a cluster upgrade occur at a time that minimizes business impact.
Finally, we know how important it is for customers to stay up-to-date with the latest innovation happening in the Kubernetes community. That’s why we’re proud to once again lead the way among cloud providers in offering the latest upstream releases in AKS, with the preview of Kubernetes 1.21. This release includes a number of significant improvements, including the graduation of CronJobs and immutable secrets/configmaps to stable. Please give it a try and let us know if you have any trouble by logging an issue on GitHub.
This year’s //build conference marks an exciting milestone in the Kubernetes on Azure journey. No longer are customers simply looking for the core capabilities required to make their initial applications run in a cloud native environment. Now they are looking for the guidance and advanced features required to meet the high bar set by their most crucial workloads. Azure is committed to meeting those needs by building a platform that is enterprise-grade, by design. And with the announcement of application services for Kubernetes clusters, we are making it easier than ever for developers to build on top of the platform.
This article is contributed. See the original author and article here.
Today, businesses require big data streaming platforms and event ingestion services that can process millions of events per second to build dynamic data pipelines and immediately respond to business challenges. Azure Event Hubs, a fully managed, real-time data ingestion service, is designed to serve demanding big data streaming and event ingestion needs.
Today, we are announcing the public preview of Azure Event Hubs Premium, a new product SKU that is tailor-made for high-end event streaming scenarios which require elastic, superior performance with predictable latency.
Azure Event Hubs premium comes with reserved compute, memory, and storage resources, which increases the performance and minimize cross-tenant interference in a managed multi-tenant PaaS environment. Event Hubs premium introduces a brand-new log storage engine that drastically improves the data ingress performance and substantially reduce the end-to-end latency. On top of all the capabilities and protocol support of the Event Hubs Standard offering, Event Hubs Premium offers, and far more generous quota allocations.
Here are some of the key compelling benefits of Event Hubs Premium SKU.
Event Hubs premium uses a new, two-tier, native-code log engine that provides far more predictable and much lower send and end-to-end latencies than the prior generation, without any durability compromises. This enables you to ingest and processes large volumes of events and data with high throughput, low latency, and high reliability (events are triple replicated across Azure availability zones).
With Event Hubs premium you get reserved compute, memory, and storage resources for each tenant to achieve more predictable latency and far reduced cross-tenant interference risk in a multi-tenant PaaS environment.
As Event Hubs Premium is a multitenant offering, it can dynamically scale more flexibly and very quickly. Capacity of Event Hubs Premium tier is allocated in Processing Units which correspond to a share of isolated resources (CPU, Memory, and Storage) in the underlying infrastructure. Therefore, there are no throttling limits are applied for your data ingestion scenarios and you stream events up to the maximum level that the allocated processing units can handle (which can depend on multiple factors such as number of producers and consumers, payload size, partition count, and many more).
Events Hubs premium can bring you cost savings for certain use cases where you don’t need the power of a single tenant dedicated Event Hubs cluster, but you need to handle data streaming workloads that are beyond the limits of the standard tier.
Event Hubs Premium SKU is suitable for streaming use cases that require more throughput, isolation, and predictability than Standard SKU, while you don’t need a dedicated single tenant cluster which is intended for most demanding streaming needs at a higher price point.
If your data streaming use case needs very high number of throughput units of the standard SKU, then EventHub premium may offer better performance, minimal cross-tenant interference, more generous quota allocations and additional features for the same cost.
If the use case does not need the power of a dedicated single tenant cluster, compared to the Dedicated SKU, Event Hubs Premium can provide benefits such as dynamic scaling and the same reliability support (premium namespaces support AZs without the need to allocate extra capacity.)
To try out and learn more about Azure Event Hubs Premium check out the below links.
This article is contributed. See the original author and article here.
Whether you’re new or seasoned to cloud, development, and SQL, building and architecting applications in the cloud has become a required skill for many roles. Today, we’re excited to announce a new learning path to help developers of all skill levels learn how to create applications quickly and effectively with Azure. The new learning path is Build serverless, full stack applications in Azure.
In this learning path, you’ll learn how to create, build, and deploy modern full stack applications in Azure leveraging the language of your choice (Python, Node.js, or .NET) and with a Vue.js frontend. Topics covered include modern database capabilities, CI/CD and DevOps, backend API development, REST, and more. Using a real-world scenario of trying to catch the bus, you will learn how to build a solution that integrates Azure SQL Database, Azure Functions, Azure Static Web Apps, Logic Apps, Visual Studio Code and GitHub Actions.
This learning path is a great place for faculty to pull content for their application development classes. We’ve chatted with several schools and universities and confirmed that something like this would be useful for students and fit in their curriculum. Since the learning path was developed in three languages, it’s also useful for students and faculty trying to learn other languages. We’ve translated the code directly and structured it using development best practices, so hopefully it is useful.
In addition to this new learning path which allows you to get hands on for FREE in Microsoft Learn’s Azure sandbox, Davide Mauri and myself, who built the learning path, will be presenting one of the modules as part of Microsoft Build Learn Live TODAY at 3:30PM PT. Be sure to register and attend! Of course, if you’re reading this after the live session, the recording will also be available through the Microsoft Build website.
If you aren’t interested in completing all of the modules, but want to dive into a specific topic, the modules are standalone, and you can learn at your own pace. Here are the modules:
If you want more content like this, I recommend checking out Azure SQL Fundamentals and subscribing to Data Exposed where we have mini-series like Azure SQL for beginners, Migrating to SQL, and more! If you have other questions or feedback, please reach out to me on Twitter @AnalyticAnna.
This article is contributed. See the original author and article here.
Today, we are releasing an update (“hotfix”) to our latest generally available version of Windows Admin Center! Windows Admin Center version 2103.2 is now generally available. Thank you to our customers, partners, and fans for helping us to continue to improve and make Windows Admin Center better! We’re working constantly to ensure users of our product have the best user experience.
This version of Windows Admin Center includes key bug fixes and feature updates to the Azure sign in process, support for Azure China, support for seamless over-the-air updates for Azure Stack HCI as well as additional updates to the Events and Remote Desktop tool experience.
Download Windows Admin Center v2103.2 today
or navigate to gear icon (Settings) on the top right corner and go to Updates to install the update from within Windows Admin Center.
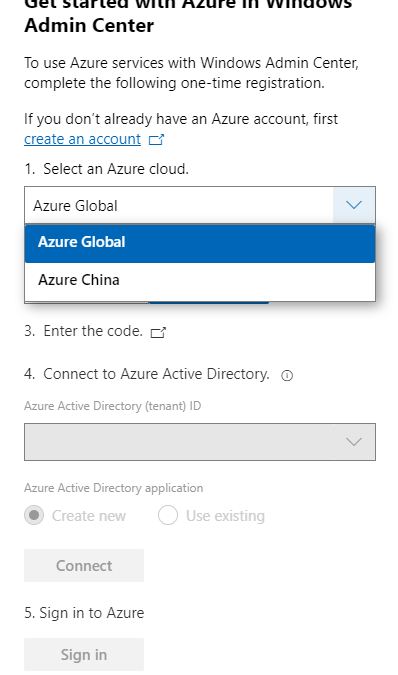
The request for Windows Admin Center to expand their Azure support matrix to sovereign clouds has been a long-standing ask, especially as we continue to introduce additional hybrid capabilities to Windows Admin Center. In this release, when you register your gateway to Azure, you will be prompted to select the cloud you’d like to register in. The two options in this dropdown are Azure Global and Azure China, with Azure Global selected by default. After registering your gateway with your selected cloud, Windows Admin Center will assume that further Azure operations, like Azure sign-in, will be done through the cloud your gateway is registered in.
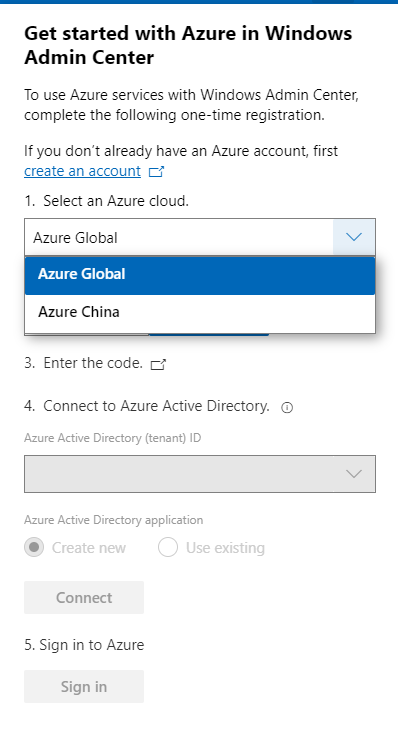
Some of the Azure services included in Windows Admin Center are not currently supported in Azure China. For more detailed information on the regional support for each Azure service, visit the Microsoft Azure website.
Today, we are introducing an all-new way of updating Azure Stack HCI clusters in Windows Admin Center. This experience will enable you to update clusters to the preview build of Azure Stack HCI 21H2 in a simple intuitive manner. The updates tool in Windows Admin Center is enhanced to allow Azure Stack HCI clusters to get over-the-air cumulative updates.
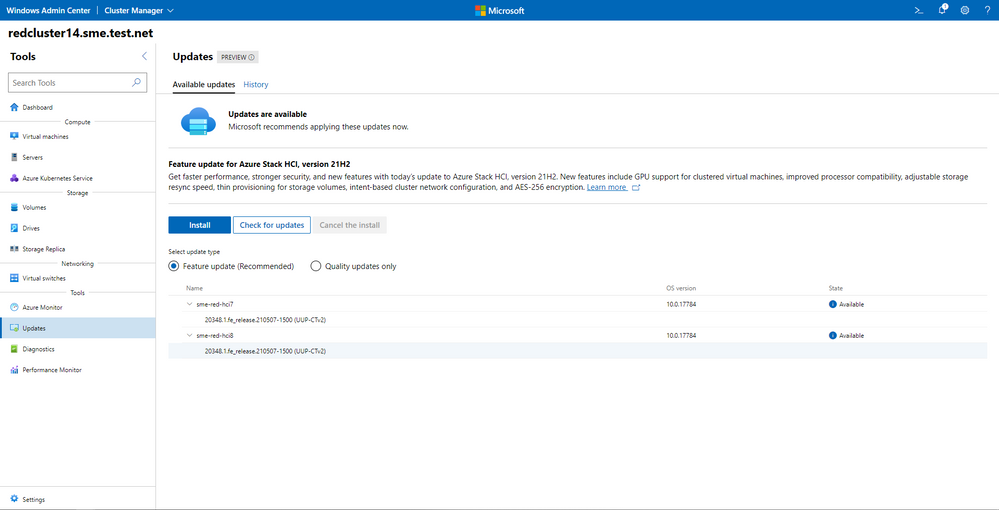
The update experience has built-in prechecks that would provide you with the required validations before the update run is triggered. This cross-stack validation informs you, as the IT admin, of any setup issues ahead of time that can cause failure of the update.
Windows Admin Center invokes the cluster-aware-updates (CAU) rolling-upgrade plugin to orchestrate the updates across the clusters. The update process status is polled in at regular time intervals and relayed back to Windows Admin Center. The Azure Stack HCI cumulative update releasing in June is only for non-production/test environments.
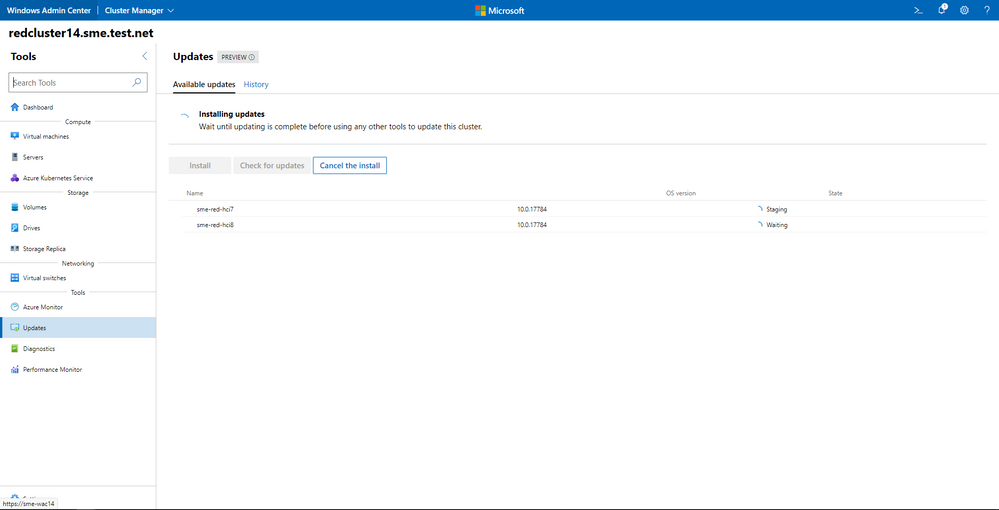
Only clusters that join the preview channel for Azure Stack HCI will receive over-the-air updates. In order to obtain the preview version of Azure Stack HCI, clusters need to join the preview channel either through Windows Admin Center or PowerShell. Click on Settings in cluster manager and navigate to Join the preview channel. The Azure Stack HCI cumulative updates will be available starting June 2021.
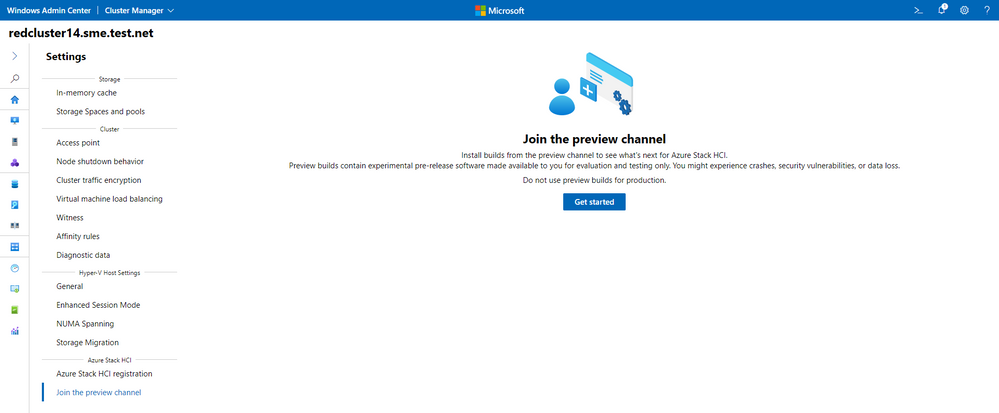
In this release, Windows Admin Center makes Azure Kubernetes Service (AKS) on HCI deployment natively available.
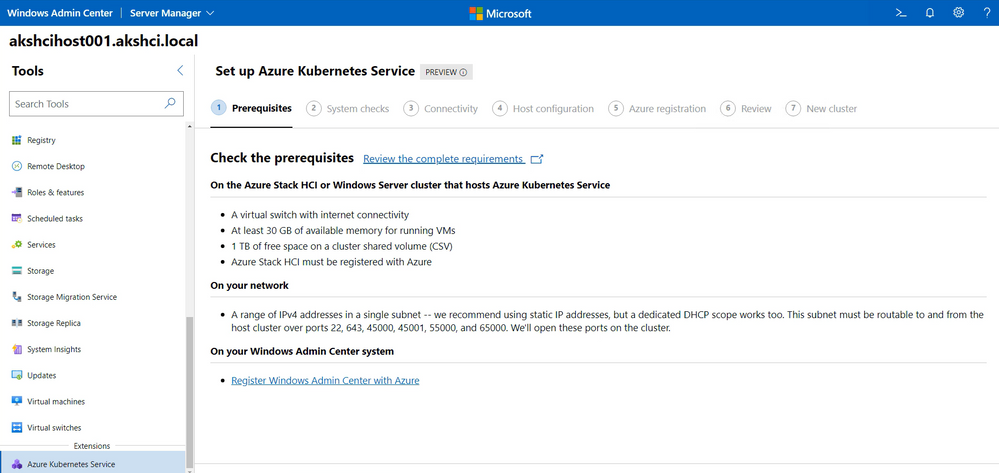
In just a few moments, Windows Admin Center allows you to deploy an AKS-HCI management cluster. This is a simple 7-step wizard that does system checks, allows you to set the appropriate network configuration and Azure registration required to successfully setup the management cluster.
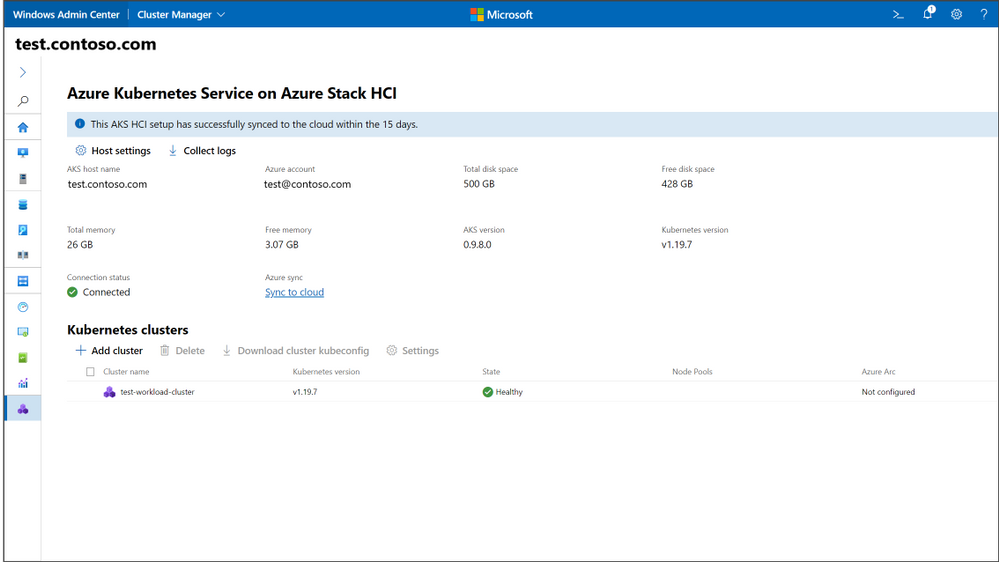
You may also create a Kubernetes workload cluster through the AKS management cluster dashboard by clicking Add cluster. This starts a wizard that takes inputs for the workload cluster creation and creates the Kubernetes cluster. You now have a successfully deployed Kubernetes workload cluster to run your container applications.
“Access Denied” fixed
We understand several users were met with an “Access denied” error upon starting Windows Admin Center and were unable to use the Windows Admin Center v2103 as a result. We have updated the logic of our automatic extension updates feature to fix this issue.
PowerShell commands fixed
In the 2103 release, several users were unable to utilize PowerShell to manage their Windows Admin Center settings and connections. In this release, you should be able to effectively use these commands to configure your Windows Admin Center gateway.
Certificate error fixed
In the 2103 release, some users were having difficulties navigating and were presented with an SSL certificate error message. In this release, we have added a fix for this issue and this SSL certificate error message should not occur.
Other updates
When we released the new look of the Events tool in our v2103 release, we did so with the caveat that not all the existing Events tool functionality was available in this new experience. In this release, we work towards rectifying that with the following improvements:
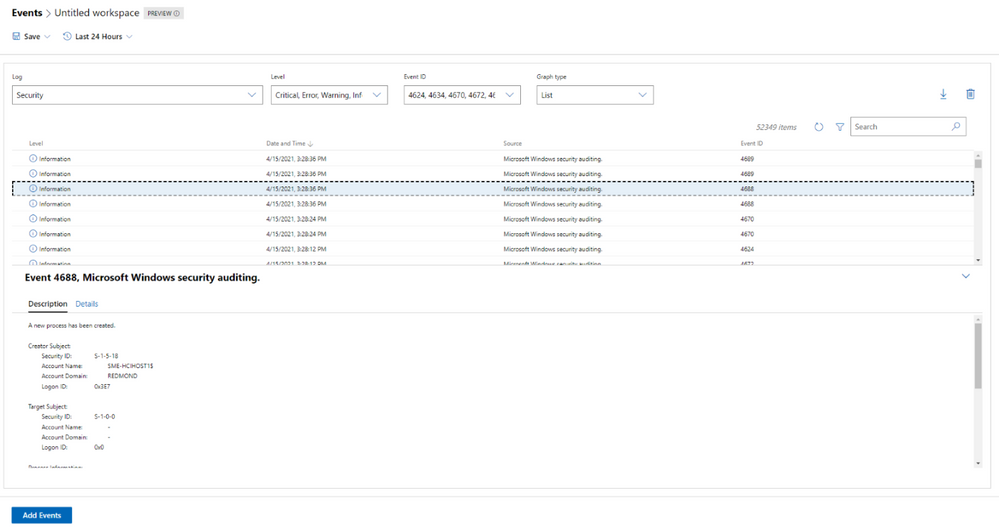
We’ve made a few changes to the Remote desktop tool in this release based on feedback we’ve received through UserVoice.
Windows Admin Center uses TLS ciphers in the Remote Desktop tool when connecting to a client machine. Historically, many of the ciphers offered by Windows Admin Center in this tool were cipher block chain (CBC) ciphers. In this release, we’ve upgraded the remote desktop web client library, and it now includes a wider selection of supported ciphers for you to choose from when you’re setting up RDP on your Windows Admin Center gateway. You should now be able to select ciphers from several suites, with options for both CBC and Galois/Counter mode (GCM).
Additionally, several users had reported through UserVoice that the language of their keyboard in the Remote Desktop tool did not match the language that had been selected. This was a large fix and it is currently only available to users who have access to our Windows Admin Center Insiders extension feed. To add the Insiders extension feed, navigate to the Feeds tab in Extension manager and add https://aka.ms/wac-insiders-feed to the feed list. Then, look for the updated “Remote Desktop” extension.
The Windows Time service extension uses the Windows Time service (W32Time) to synchronize the date and time for all computers running in Active Directory Domain Services (AD DS). Time synchronization is critical for the proper operation of many Windows services and line-of-business (LOB) applications. The Windows Time service uses the Network Time Protocol (NTP) to synchronize computer clocks on the network. NTP ensures that an accurate clock value, or timestamp, can be assigned to network validation and resource access requests.
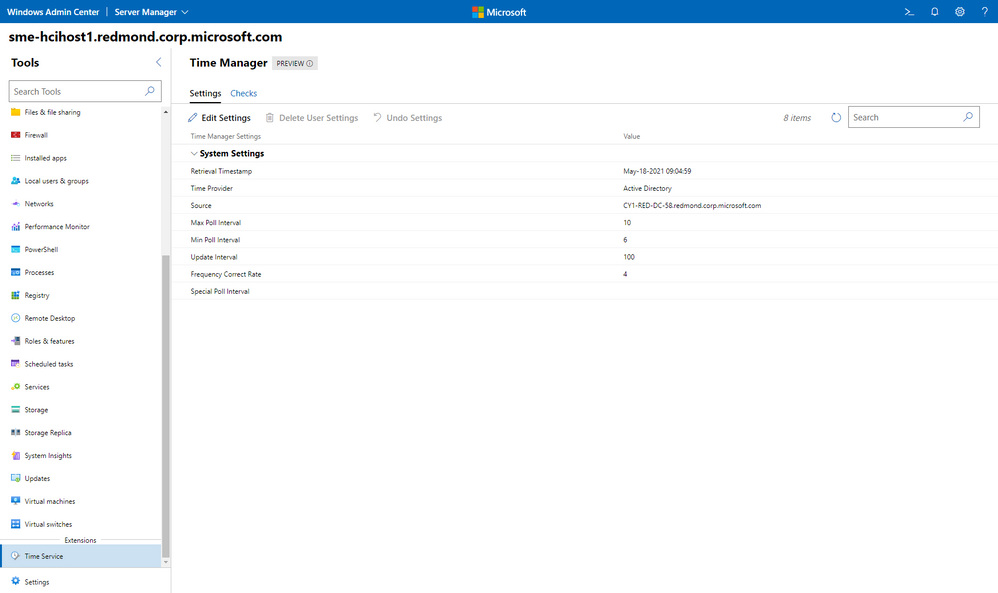
This extension is currently only available to users who have access to our Windows Admin Center Insiders extension feed. To add the Insiders extension feed, navigate to the Feeds tab in Extension manager and add https://aka.ms/wac-insiders-feed to the feed list.
Over the past year, we’ve been hard at work improving the Containers Extension. These improvements include better management of your container images either locally or in a container registry – including Azure Container Registry (ACR), a new wizard to create new container images based on existing applications, running your container images locally or on Azure Container Instance and much more.
Today, we’re happy to announce the capabilities in the Containers extension that will help you deploy workloads on Azure Kubernetes Service (AKS) and AKS on Azure Stack HCI (AKS-HCI).
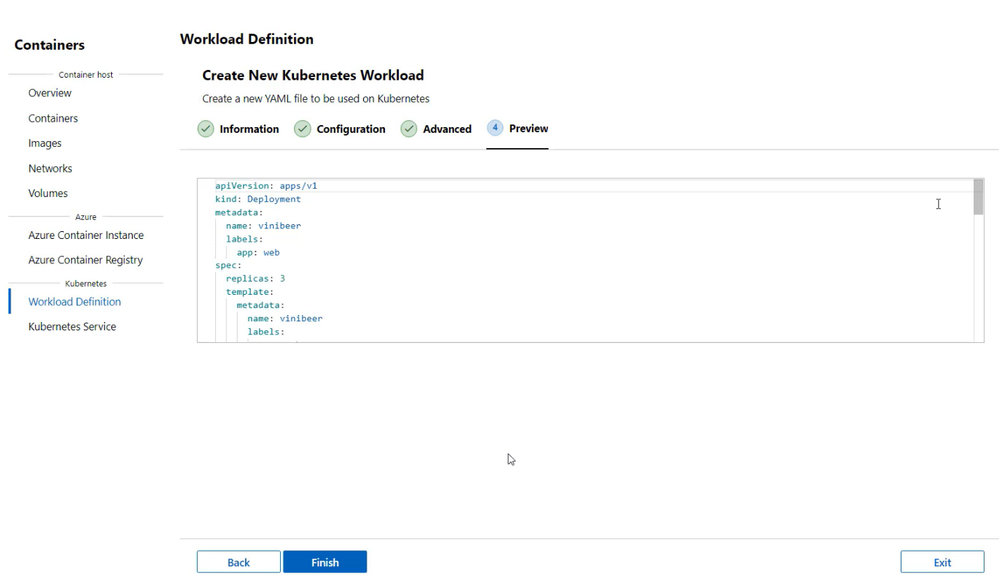
A new option to create Workload Definitions allows you to create new YAML files based on existing container images on ACR. With this option, you can provide details on your application and Windows Admin Center provides you with a deployment file ready for your AKS clusters. It also ensures your AKS nodes can securely retrieve the authentication for your ACR registries. Not only that, you can target AKS or AKS-HCI with these Workload Definitions and check if these were deployed correctly.
This extension is available publicly through our Windows Admin Center extension feed. Download it today by navigating to the gear icon on the top right corner and clicking on Extensions.
Windows Admin Center continues to value the collaboration efforts we have with our partners, and these past few months have been a very active period! Since our 2103 release in March, five of our partners have released new or updated versions of their extensions. If you’re interested in developing a Windows Admin Center extension, visit our documentation to get started.
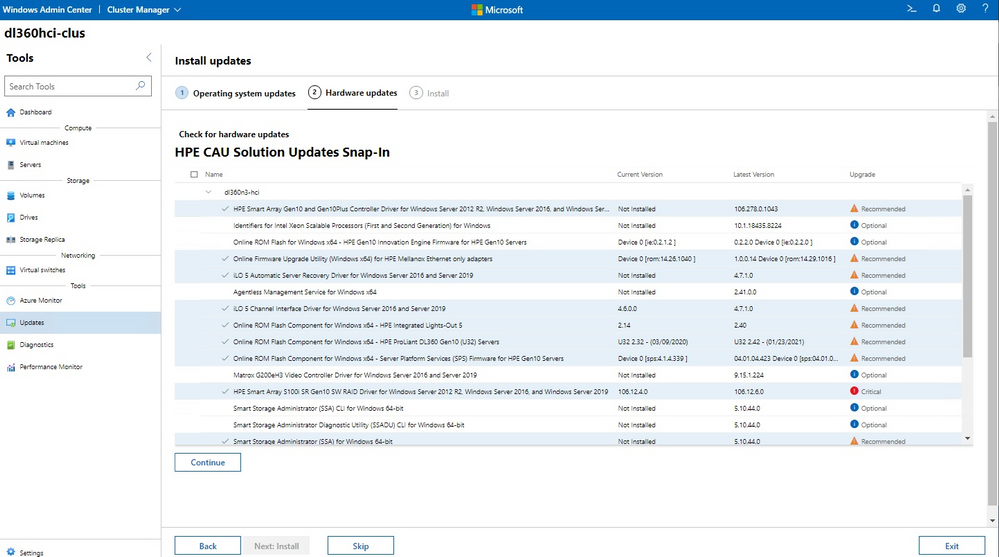
The HPE Azure Stack HCI Cluster Deployment and Update Snap-in is now available. The HPE Deployment snap-in reports the firmware and software inventory and status generated by HPE Smart Update Manager (SUM), then initiates installation of the selected components, followed by showing the completion status. The HPE Update snap-in reports the firmware and software inventory and status generated by HPE Smart Update Manager (SUM). The selected components will get updated on the cluster from Cluster-Aware-Updating (CAU) orchestration.
The cluster deployment snap-in will appear in the Azure Stack HCI cluster create wizard, and the update snap-in will appear in the update wizard in the Updates tool when connected to a cluster.
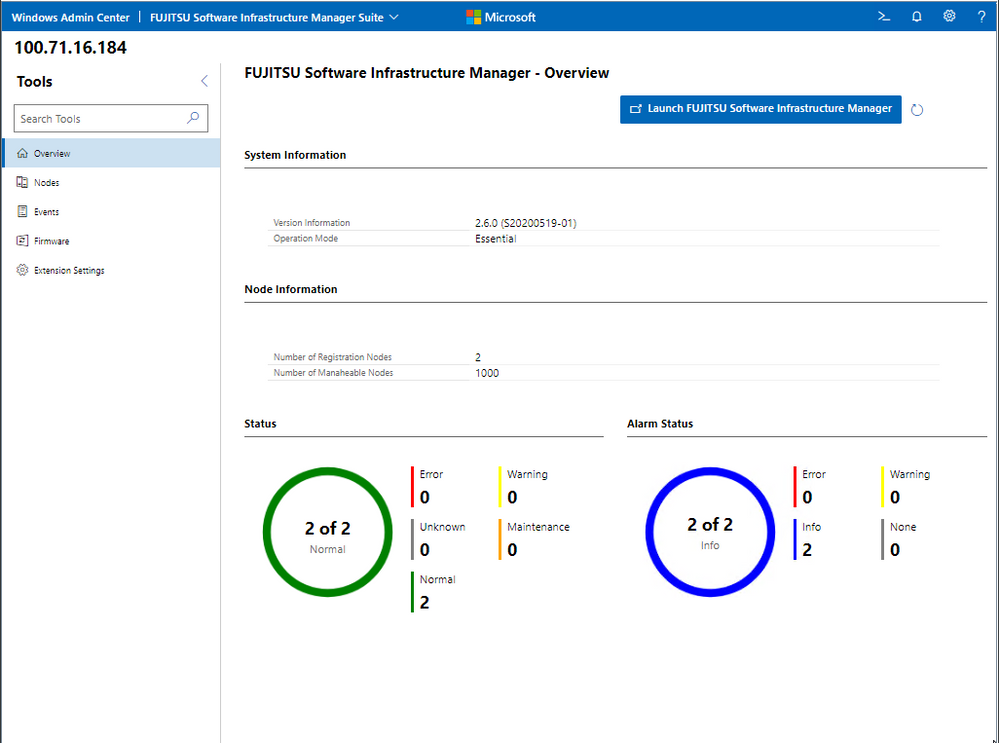
Fujitsu Software Infrastructure Manager (ISM) is now available. By installing ISM, multiple and various types of information and communications technology (ICT) devices can be managed in an integrated way. With this software, you can monitor the status of all the ICT devices in a data center or a machine room. You can also execute batch firmware updates for multiple devices and configure servers automatically. It can reduce costs of operation management and increase the operation quality.
Other partner extension updates
We hope you enjoy this latest update of Windows Admin Center, the various new functionality in preview, and all the extensions now available. Learn more and download today!
As always, thanks for your ongoing support, adoption, and feedback. Your contributions through user feedback continue to be very important and valuable to us, helping us prioritize and sequence our investments.
<3,
Windows Admin Center Team (@servermgmt)
This article is contributed. See the original author and article here.
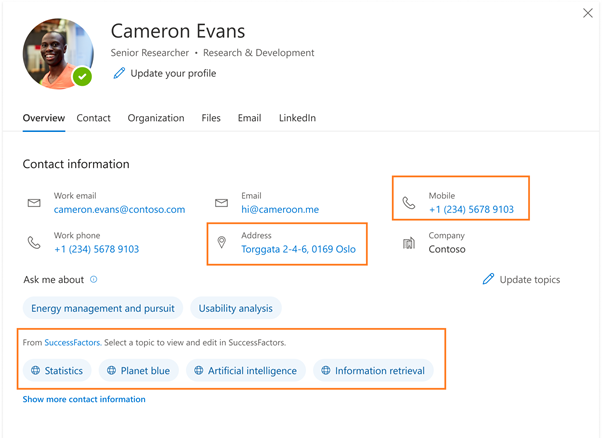
On the profile card in Microsoft 365, you can find information about users that is stored and maintained by your organization, for example Job title or Office location, but what if you don’t know what you don’t know? Sometimes what we’re looking for can be as simple as a Job title or Office location, but what if the information we need is more complex or outside of the boundaries of Microsoft 365? Often you would need to search across multiple systems and know what systems that information is in. What if you could find all the information about a person, even that information which is unique to your company, right in the context of the person?
This is where customization of people experiences in your organization helps. You can already customize some parts of people experience by surfacing AAD data on your profile cards. However, today we’re excited to announce new capabilities in profile enrichment where as an Microsoft 365 administrator you can directly enrich user profiles with information from HRMS systems like Workday, SAP SuccessFactors and more using Microsoft Graph connectors. With these capabilities, you can now find more information you need about a person right in a person’s context, in less time and in fewer places.

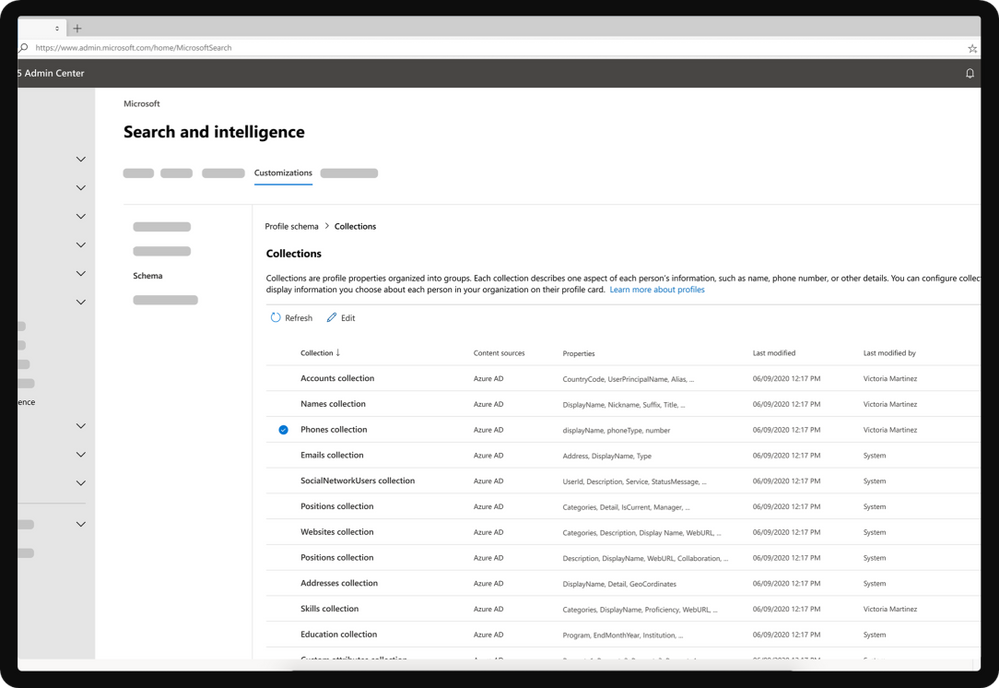
With new profile enrichment with Microsoft Graph connectors, enriching your profile is possible through few easy steps in Search & Intelligence admin center.
Through extending the capabilities of Microsoft Graph connectors to the Microsoft 365 profile, you’ll soon be able to ingest data from systems like SuccessFactors, Workday, and more.
While this work is new and coming soon, we’ll make a few connectors available initially; however, in the event the system you’re using does not have a pre-built connector, we’ve got you covered with Microsoft Graph APIs that allow you to build your own custom connector as well. To learn more visit externalItem resource type – Microsoft Graph beta | Microsoft Docs.
The Microsoft 365 Profile API is a set of APIs that provides a rich schema for storing profile data of a user in a tenant. Its entity-based model provides a wide range of entities like accounts, address, educations, interests, skills, projects and many more.
These entities have native semantic depth built-in to support rich profiles– making it easier for everyone to express themselves and be able to contextualize people within the company. These properties are surfaced in shared, people experience across Microsoft 365 and third-party services and experiences via Microsoft Graph.
 Search & intelligence dashboard in Microsoft 365
Search & intelligence dashboard in Microsoft 365
You can enrich your Microsoft 365 profile data through ‘Customizations’ in the Search & Intelligence admin center. Just jump into the Profile schema management dialog and choose the user properties of the Microsoft 365 profile you want to enrich using configured Microsoft Graph connectors. In addition, you will also be able to choose some of the properties that should be displayed on the user’s profile cards too.
Check out our demonstration video here https://youtu.be/OxeXiw0FwU8.
While you can enrich your Microsoft 365 user profiles with data from different third-party systems. There are a few limitations that will be relaxed going forward.
We will be launching a private preview of these features in CY21H2. Reach out to us at peoplecustomizationfeedback@service.microsoft.com if you have any feedback or if you are interested in joining our limited preview.
This article is contributed. See the original author and article here.
Information has gone from scarce to superabundant and while the benefits of having access to information are countless, how do we know what we don’t know? New capabilities coming to Microsoft Search provide more reach, more locations, and more flexibility to bring you more choice to find, do, and discover.
Microsoft Graph connectors for Microsoft Search are now generally available. This enables your organization to connect your islands of information to Microsoft 365 (index time merging) so you can find what you need wherever you’re working, whether in one of your favorite productivity apps or one of the many Microsoft 365 services such as SharePoint or Office.com.
Microsoft Graph connectors are the intelligent fabric that bring together information from disparate systems, on-premises and in the cloud, and your information in Microsoft 365 making it easier than ever to find what you need, when you need it. For example, maybe you want to improve self‑service and case resolution, but don’t want to have to remember where to go or what app to use.
With Microsoft Graph connectors, you can simply bring information from systems like ServiceNow into Microsoft 365 and make that information available across its apps and services. Microsoft Search eliminates the need to recall where information is, mitigates costly context switching, and takes advantage of the global perspective provided by the Microsoft Graph. Maybe you haven’t migrated those file shares to the cloud, no problem, we have you covered or maybe you need to not only connect to your customers, but want to connect your leads too – check, we’ve got you covered.
Microsoft Graph connectors empower your organization to discover more, in less time, in fewer places. Keep reading to learn more about Microsoft Graph connectors, how to get started, and what’s coming.
Getting started with Microsoft Graph connectors is as easy a few clicks in the Search & intelligence admin center and as part of your Microsoft 365 subscription, you have access to Microsoft built connectors to include:
The Azure Data Lake Storage Gen2 Graph connector allows users in your organization to search for files stored in Azure Blob Storage and Azure Data Lake Gen 2 Storage accounts.
The Azure DevOps Graph connector allows your organization to index work items in its instance of the Azure DevOps service.
The Microsoft SQL server or Azure SQL Graph connector allows your organization to discover and index data from an on-premises SQL Server database, or a database hosted in your Azure SQL instance in the cloud.
The MediaWiki Graph connector allows your organization to discover and index data from a wiki created by using MediaWiki software.
The Salesforce Graph connector allows your organization to index Contacts, Cases, Opportunities, Leads, and Accounts objects visible to users according to the user criteria permissions within your organization in your Salesforce instance. Learn about how to quickly set up your Salesforce connection and sync non-Azure AD users and groups with this video: https://youtu.be/SZYiFxZMKcM.
The ServiceNow Graph connector allows your organization to index knowledge-based articles visible to users according to the user criteria permissions within your organization. Learn about the latest improvements at https://youtu.be/TVSkJpk1RiE.
File Share Graph connector
The file share Graph connectors allows you index and search the following formats: DOC, DOCM, DOCX, DOT, DOTX, EML, GIF, HTML, JPEG, MHT, MHTML, MSG, NWS, OBD, OBT, ODP, ODS, ODT, ONE, PDF, POT, PPS, PPT, PPTM, PPTX, TXT, XLB, XLC, XLSB, XLS, XLSX, XLT, XLXM, XML, XPS, and ZIP.
Learn more about the file share Graph connector at https://docs.microsoft.com/en-us/microsoftsearch/fileshare-connector.
Microsoft SQL Server Graph connectors
The Microsoft SQL server or Azure SQL Graph connector allows your organization to discover and index data from an on-premises SQL Server database, or a database hosted in your Azure SQL instance in the cloud.
Learn more about the Azure SQL and Microsoft SQL Server Graph connectors at https://docs.microsoft.com/en-us/microsoftsearch/mssql-connector.
Oracle SQL Graph connector
The Oracle SQL Graph connector allows your organization to discover and index data from an on-premises Oracle database.
Learn more about the Oracle / SQL Graph connector at https://docs.microsoft.com/en-us/microsoftsearch/oraclesql-connector.
Enterprise websites Graph connector
The Enterprise websites Graph connector allows your organization to index articles and content from intranet websites including dynamic sites.
Learn more about the https://docs.microsoft.com/en-us/microsoftsearch/enterprise-web-connector.
In addition to connectors provided by Microsoft, our partners have delivered over 130+ connectors to help you connect your islands of information to Microsoft 365. to help you connect your islands of information to Microsoft 365.
Didn’t find what you need from Microsoft or our partners, not to worry, we’ve got you covered with Graph APIs that allow for building your own custom connector as well. Get started at externalItem resource type – Microsoft Graph beta | Microsoft Docs.

As we continue to innovate across the Microsoft Graph connector ecosystem and related capabilities, we’re bringing together more data sources, with more features, and the same ease of use.
In addition to these connectors, Microsoft Graph connectors results clusters (preview) now allow you to search for content from any data source in their default view, the All vertical in SharePoint, Office.com, and Bing.com when signed in with a work or school account.
Result clusters help users discover all third-party content in one place. The results shown in a result cluster are grouped together based on the search vertical configuration.
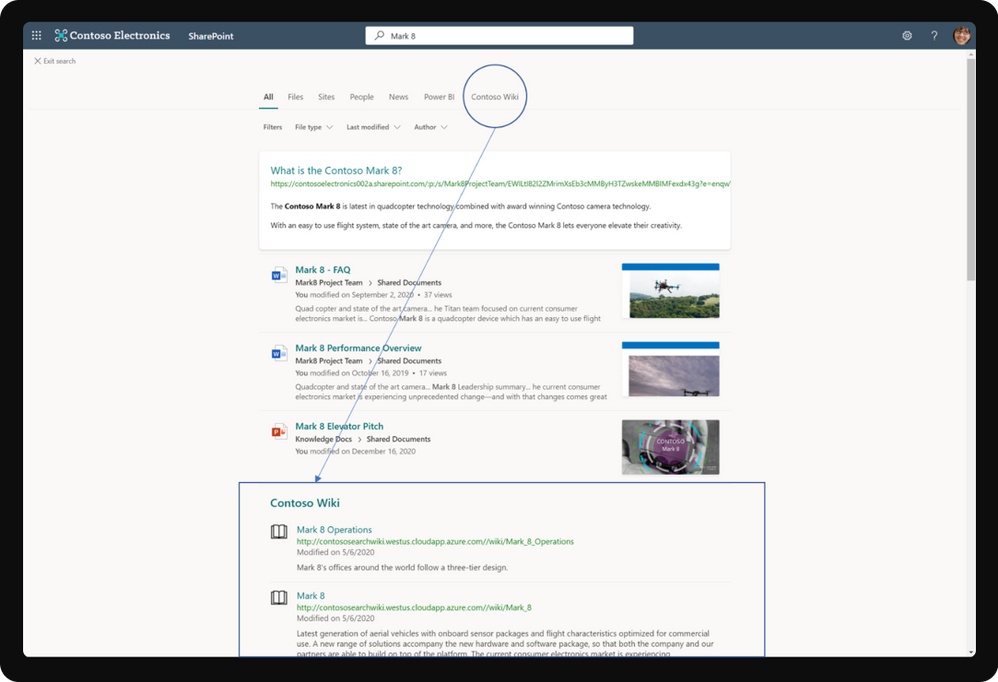 Result cluster with Microsoft Graph connectors in SharePoint Online
Result cluster with Microsoft Graph connectors in SharePoint Online
Query variables are used in query template of a vertical to provide dynamic data as an input to the query defined on a vertical. Profile query variables are now supported for connector verticals. Define any attribute from the user’s Profile, as a query variable and it would be resolved during query evaluation. This feature is currently in preview.
In addition to searching across connector data, you will soon be able to enrich Microsoft 365 profile properties like Job title, Phone numbers, Skills etc. with data from HRMS systems like SAP SuccessFactors, Workday, Oracle HCM, etc. using graph connectors. You can then surface this rich profile information on people experiences like profile cards seamlessly for everyone in your organization.
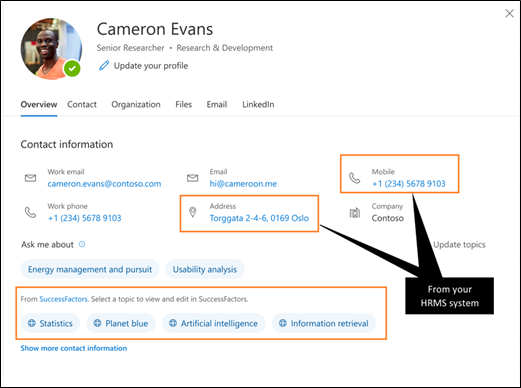 Profile enrichment with Microsoft Graph connectors
Profile enrichment with Microsoft Graph connectors
Check out the detailed blog on how you can do this at https://aka.ms/microsoftsearch/build21/profileenrichment.
For the Azure DevOps, Salesforce, and ServiceNow Microsoft-built connectors, you can now sync non-Azure AD users/groups from your external data source with your Azure AD users/groups so that your end users can see search results permissioned to them.
During the connection configuration process, you can choose Only people with access to this data source on the Manage search permissions screen. For the ServiceNow and Salesforce connectors, you may have to provide a set of mapping rules to map your non-Azure AD users to your Azure AD users. At the end of connection setup, your non-Azure AD users/groups will sync with your Azure AD users/groups along with your content. This will ensure that your end users see searched content permissioned only to them.
This feature is currently in public preview; to try it out, your tenant and users must be in the Targeted release ring.
Soon Microsoft Graph connector information will be available to search in Microsoft Teams and Windows, in addition to existing locations to include SharePoint, Office.com, and Microsoft Bing.
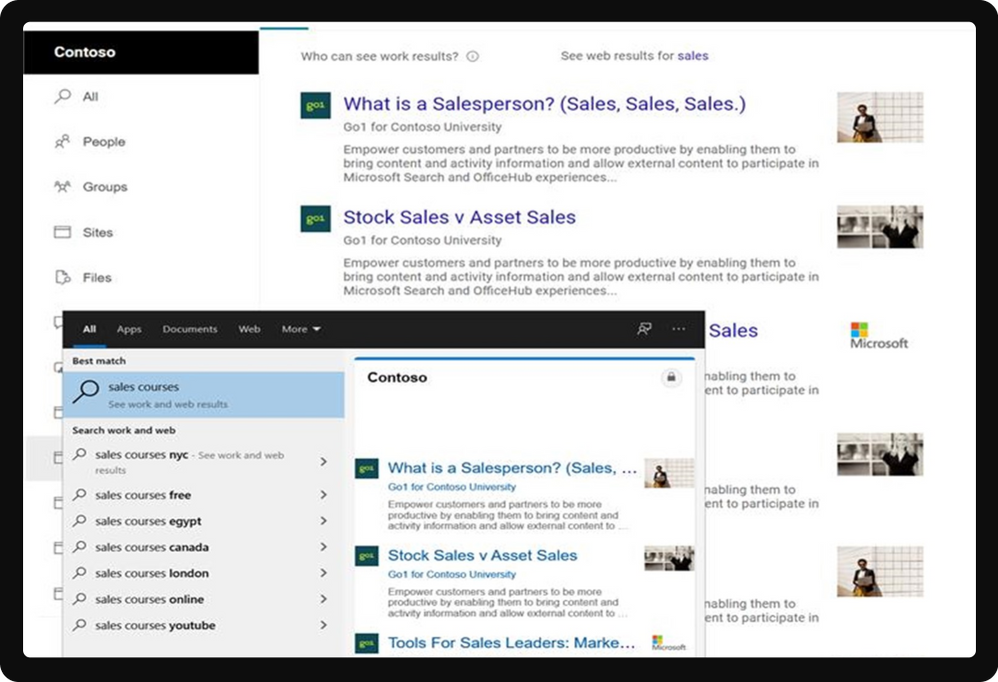 Microsoft Graph connector information in Windows 10
Microsoft Graph connector information in Windows 10
Search results on select Graph connectors will soon support actions that will allow users to interact with the result and perform changes to the Connector content within the Search application.
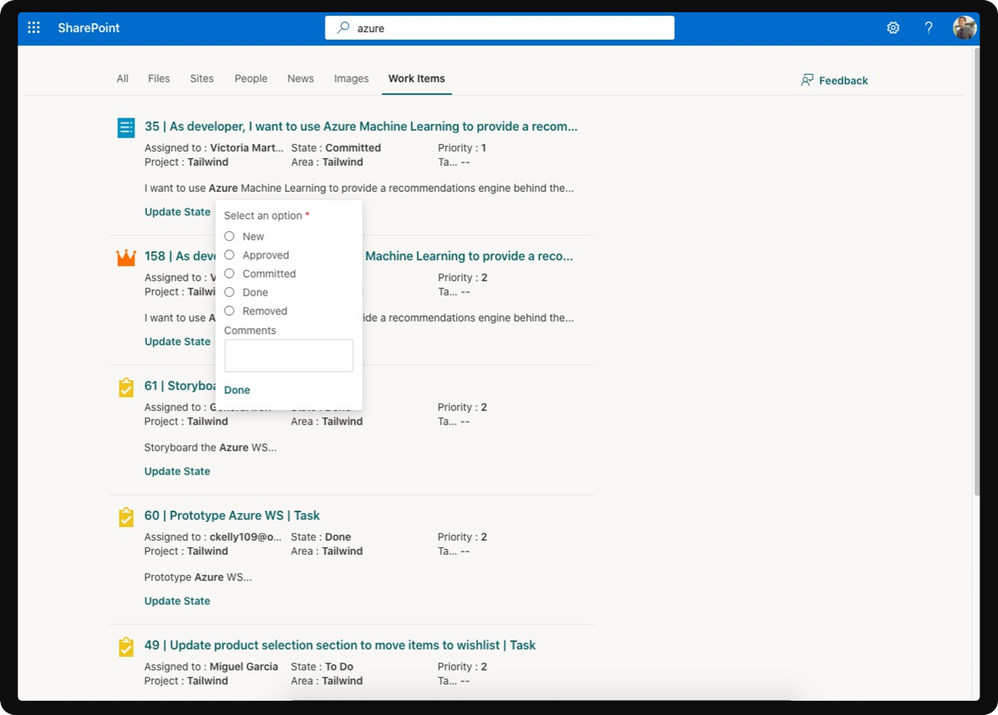 Actionable information with Microsoft Graph connectors in SharePoint Online
Actionable information with Microsoft Graph connectors in SharePoint Online
eDiscovery support for Graph connectors developer preview will be available in summer 2021. Use the same eDiscovery tools in Microsoft 365 to search for content in third-party systems connected to Microsoft Search.
Request a trial
Want to try Microsoft Graph connectors? If you would like to try Microsoft Graph connectors in Microsoft 365, contact your account representative to receive a limited trial experience to try out Microsoft Graph connectors today.
Didn’t find the connector you are looking for? Provide us with feedback at http://aka.ms/graphconnectorsfeedback.
In addition to new and improved Microsoft Graph connectors we’ll soon make available the new Microsoft Search Federation as part of the Microsoft Search product offering. New federation capabilities will allow enterprises to retrieve their CRM content from their enterprise Dynamics 365, also build and integrate their custom LOB search experiences, customized search providers, into the overall Microsoft Search.
Federated search is useful when you want to expose data from systems in Microsoft Search that may be subject to strict compliance requirements or where the systems data cannot leave the systems boundaries. In some other cases, sources with sensitive data that customer doesn’t want to be indexed on the cloud where data is on-prem to expand coverage for their sensitive data via federation. With federated search, you can make information from these systems available to search across in Microsoft 365 productivity apps and services, without indexing its data with Microsoft Search.
Information has become increasingly distributed, and often these islands of information are near, but outside of reach. Microsoft federation connectors help you pull together information and insights from across Microsoft clouds, merging that information and making it available to search in your favorite productivity apps and services, from SharePoint, to Office.com, to Microsoft Teams.
Getting started with Microsoft Search federation is as easy a few clicks in the Search & intelligence admin center. You can quickly set up the connection to a federated source using one of the available Microsoft built-in federation connectors (currently limited to Dynamics 365):
Dynamics 365 Federation Search (Preview)
Microsoft Dynamics 365 is a product line of enterprise resource planning and customer relationship management intelligent business applications. Dynamics 365 federation search allows you intelligently search for information in Dynamics 365 through Microsoft Search, which provides the seamless out-of-box search experience to easily and quickly find most relevant customer and business data across your organization without switching back and forth between Microsoft 365 productivity apps and services and Dynamics 365.
Check out a demonstration here https://youtu.be/TH9QUkQoEJM.
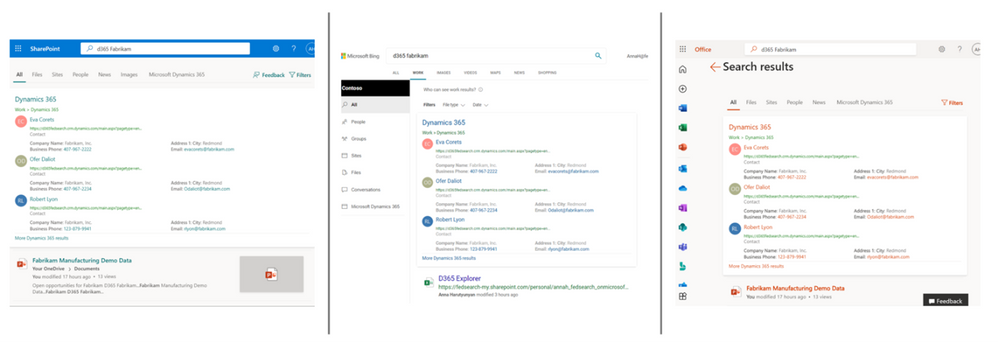
A private preview for Dynamics 365 federated search will be available this summer. If you are interested in taking part in the private preview, let us know at aka.ms/D365FederationSearchPreview.
Dynamics 365 is our first provider built on top of our federated search platform, and while a great milestone for federated search with Microsoft Search, this is only the beginning of the journey. We have ambitious plans to continue to add more search federation scenarios, such as Azure Cognitive Search, which will allow customers to seamlessly retrieve and display search results from their custom search index in Microsoft Search.
In addition to federation with native data sources, federated search also provides a platform to empower you to build custom search providers for your own unique information sources. The federated search platform:
The Microsoft Search federation provider will allow you to search for information from external sources and bring the results to Microsoft Search as high confidence Answer cards. You can make use of the platform to integrate HR tools, helpdesk, IT, or any other external content in the Microsoft Search experience.
Watch the demostration at https://youtu.be/AZcOskBTwNU.
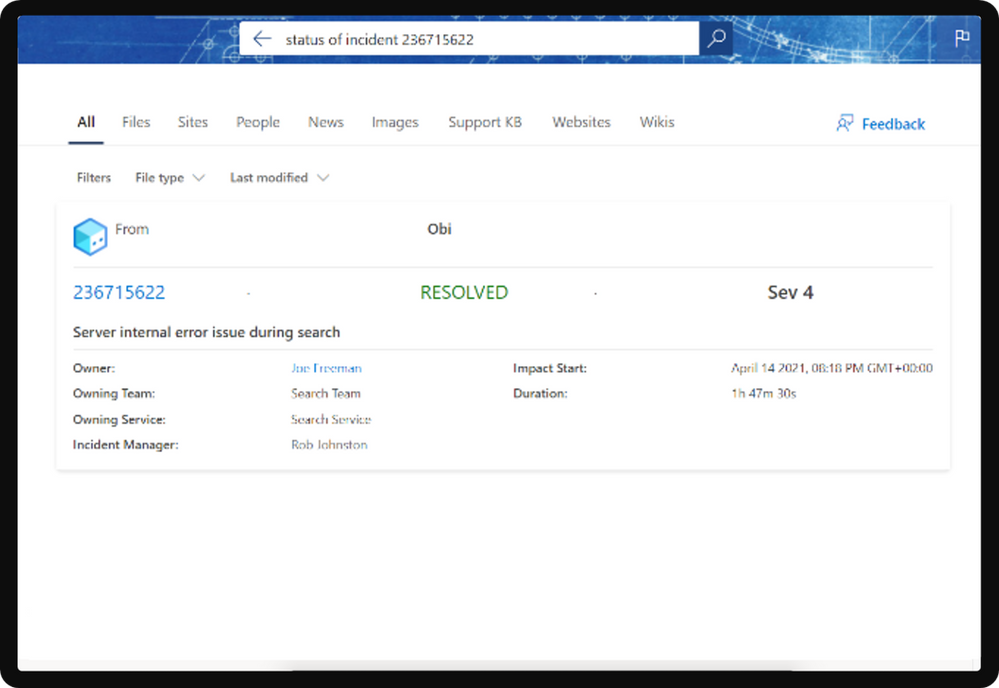 Search federation
Search federation
Microsoft Search federation will initially be available to SharePoint, Office.com and Microsoft Bing, and in the future across other Microsoft Search enabled apps and services. This platform will be available in private preview summer of 2021. If you are interested in taking part in the private preview, let us know at https://aka.ms/SearchDevPrivatePreview .
The Microsoft Search API provides one unified search endpoint that you can use to query data in the Microsoft cloud – messages and events in Outlook mailboxes, and files on OneDrive and SharePoint – that Microsoft Search already indexes.
Use Microsoft Graph connectors to include data outside of the Microsoft cloud in your search experience. For instance, connect to an organization’s human resources database or product catalog. Then use the Microsoft Search API to seamlessly query the external data source.
With connectors in place, you can provide your users with easy access to results and improve usage by adding a Microsoft Search embedded box to your company’s intranet sites.
Soon we’ll allow for the use of a new signals API, which will your app’s content take part in intelligent discovery experiences like “Recommended”, and “Recent” files in Office Hub.
Learn more about Microsoft Graph connectors with the following resources:
Documentation
Microsoft Graph Connectors Overview | Microsoft Docs
Videos
Graph connectors for Microsoft Search: What’s new
Getting started with Microsoft Graph connectors
Learn how to build Microsoft Graph connectors
In addition, we’re pleased to announce additional Microsoft Graph-powered experiences to help you find and do more to be more productive.
It’s the places and faces we remember and today we’re making it easier than ever to visualize and contextualize people and teams across your company with a new addition to Outlook.
This new application available to Office Insiders allows you to find, discover, and explore people and relationships through a delightful organizational browser experience.
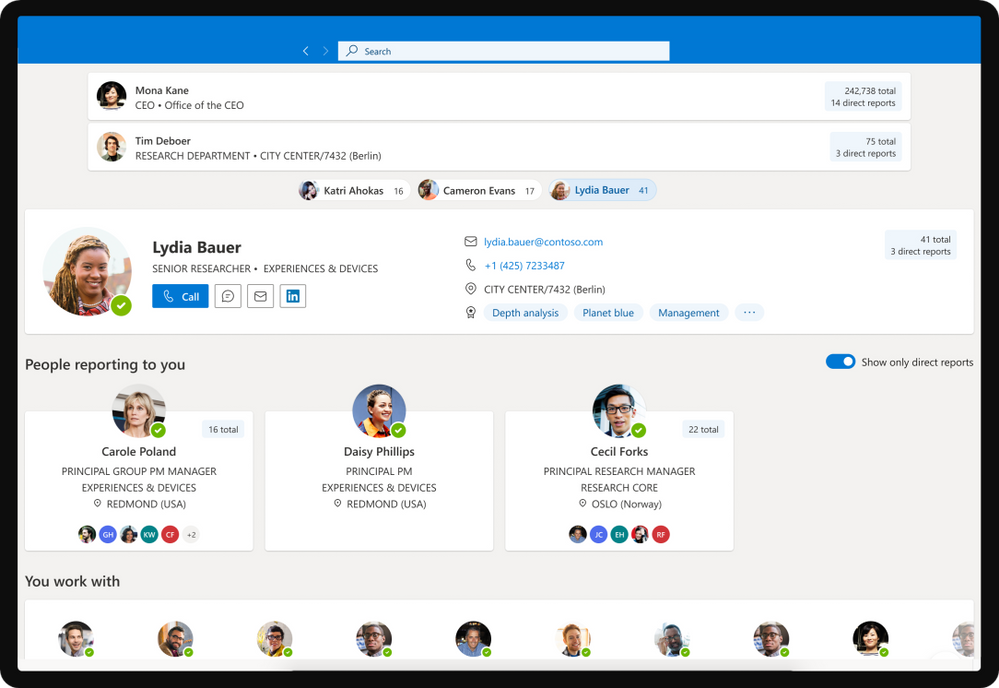 Org Explorer
Org Explorer
What’s Next
We’ll continue to evolve this experience over the next few months with some exciting new changes and features.
Availability
This feature has started rolling out to Beta Channel users running Version 14107 of Outlook or later.
We typically release features over some time to ensure that things are working smoothly. This is true for Insiders as well. We highlight features that you may not have because they’re slowly releasing to larger numbers of Insiders. Similarly, sometimes we remove elements to improve them. Though rare, we also reserve the option to pull a feature entirely out of the product.
Sign up for the Office Insider newsletter and get the latest information about Insider features in your inbox once a month!
This article is contributed. See the original author and article here.
By Anders Ahl – Principal Program Manager | Microsoft Endpoint Manager – Intune
As an admin that manages Windows 10 devices, you can take advantage of joining large numbers of new Windows devices to Azure Active Directory (Azure AD) and Intune.
This article will help IT pros and mobile device administrators understand the steps required to create a provisioning package, as well as enrolling them into the Intune service.
Current state: CATAhlyst Corp has hundreds of stand-alone Windows 10 devices in their stores, acting as kiosks or electronic signs. These machines are not Active Directory joined today and the management platform is an old and outdated proprietary solution that has proven to be too expensive to maintain.
Desired state: All userless devices should be joined to Azure Active Directory and enrolled into Intune.
Process: The goal is to Azure AD join these machines and enroll them into Intune using a provisioning package. The IT Pro tasked with the job has read through the Microsoft Docs article Bulk enrollment for Windows devices but doesn’t like the requirement to rename the device as all devices are already conforming to the established naming standard, we will therefore examine how this requirement can be overcome by modifying the provisioning package.
Automatic MDM enrollment into Intune is enabled for Azure AD joined machines. If this is not the configuration you use in your tenant you would simply end up with an Azure AD joined device, without Intune management after applying the provisioning package. There is nothing in the provisioning package itself that will address the MDM enrollment, it’s all automatically taken care of by Azure AD.
Let’s get started!
Creating provisioning packages is preferably done using the Windows Configuration Designer (WCD) available from the Microsoft Store.
 Figure 1: Windows Configuration Designer Store App
Figure 1: Windows Configuration Designer Store App
As you download and install WCD on an ITPro Windows 10 device, make sure you’re running at least Windows 10 2004 (20H1) to be able to leverage the new computer rename logic. In this particular scenario, we will be removing it altogether which is a new functionality introduced in 20H1.
Start WCD and from the first screen, make sure you select “Provision desktop devices”. As we will see later on, the template we want to use is actually “Advanced provisioning” but if we start off with that, it is much more work to create and supply the Bulk Azure AD Token than it is to first use the Wizard and then delete the items we don’t need.
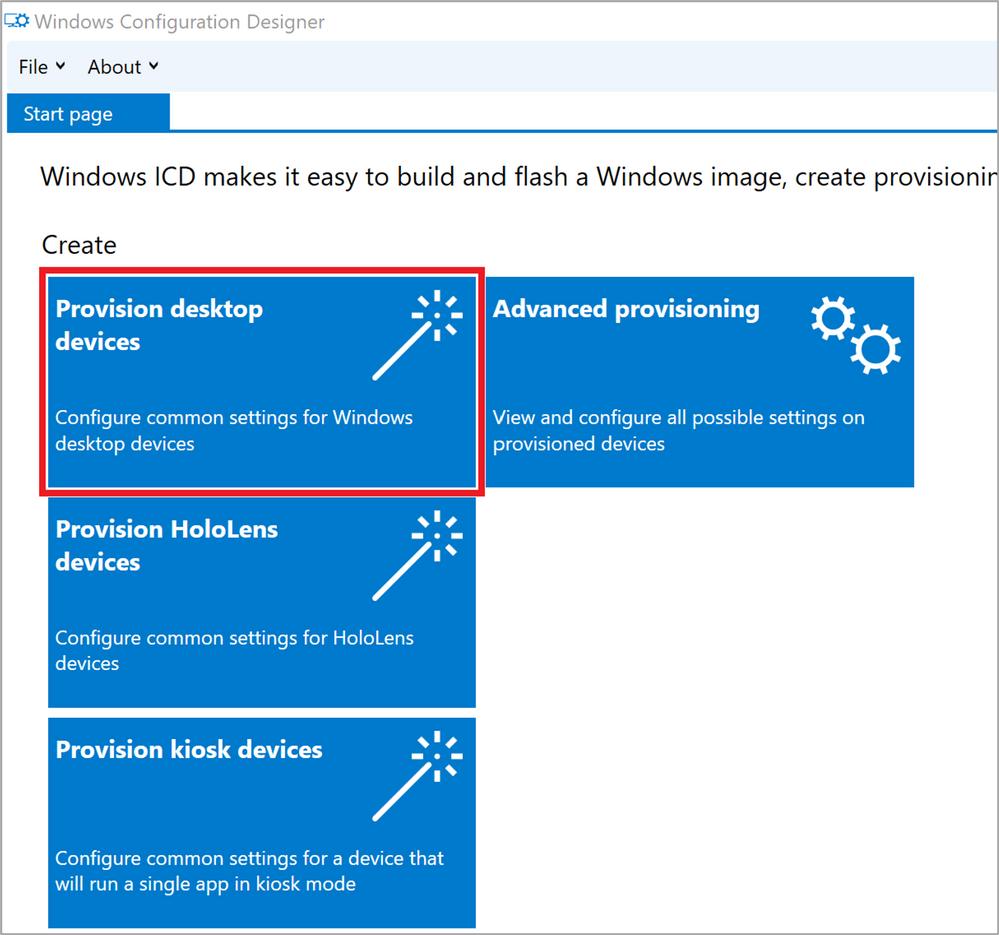 Figure 2: WCD Create profile
Figure 2: WCD Create profile
Supply the necessary project details for your package and if you regularly create provisioning packages, make sure you give it both a relevant name and a fitting description, especially if you have to come back later to make modifications.
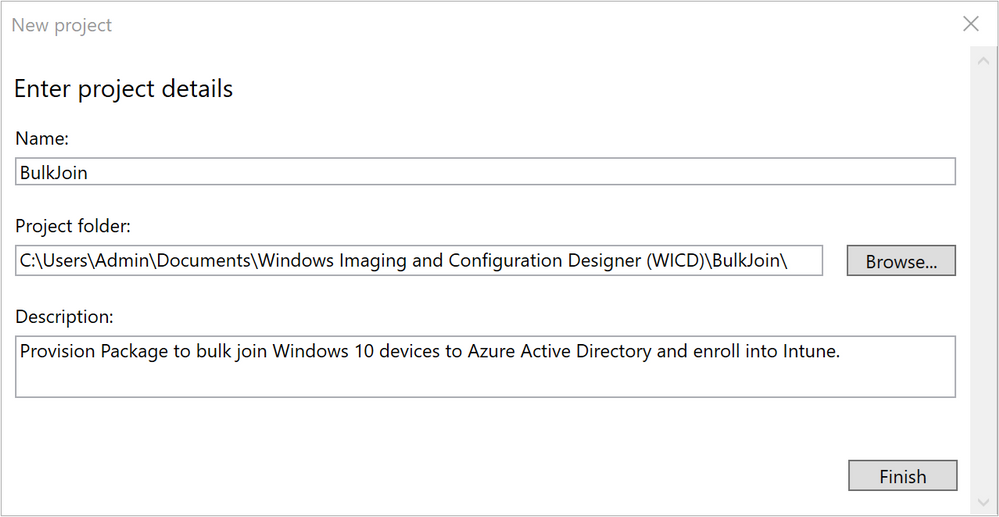 Figure 3: WCD Enter project details
Figure 3: WCD Enter project details
As you probably can tell from the Project folder path, I’m running as a local account on my ITPro machine. This is not a requirement, but I usually prefer to create provisioning packages from standalone/Workgroup machines just to make sure I’m not involuntarily using any domain references or single sign-on abilities.
Although the button in the bottom right says “Finish” it’s literally the opposite so press it and let’s get started!
Already on the next screen is our first little trick to get what we want: An Azure AD joined, Intune enrolled device without renaming it along the way. The device name value, highlighted in red in Figure 4: WCD Set up device could be anything that the wizard accepts as we will delete this in a later step. As of Windows 10 20H2, the value is required so you have to enter something to be able to continue.
Also worth noting is the statement highlighted in green which tells you that this operation requires Windows 10 2004 (20H1), even if we intend on deleting this part from our package, earlier versions of Windows 10 doesn’t like this so make sure you have an up-to-date client estate before you venture on.
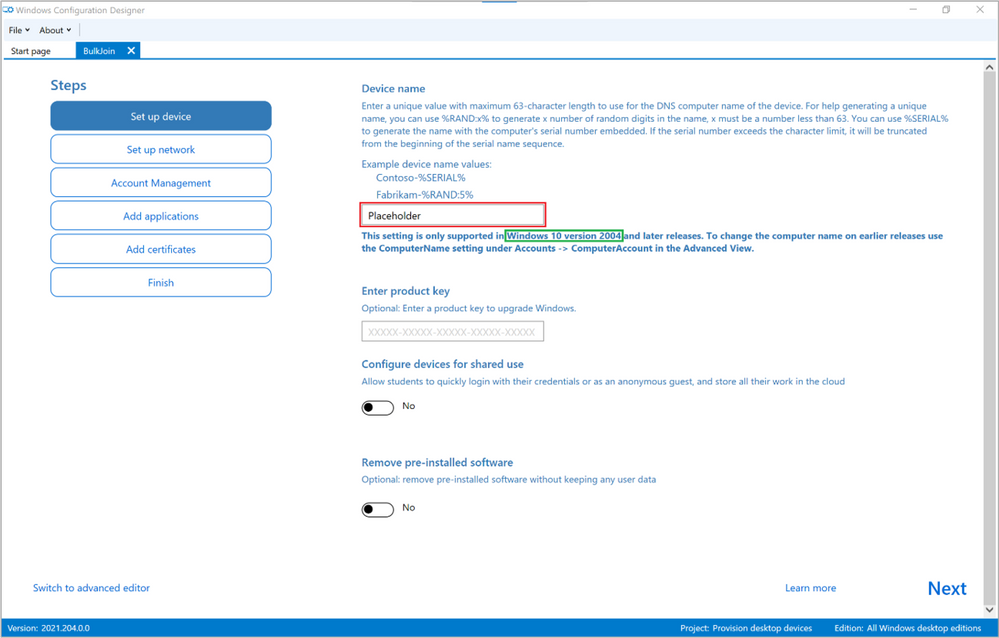 Figure 4: WCD Set up device
Figure 4: WCD Set up device
When you’re done, click Next, on ‘Set up network’ page de-select the option to provision a Wireless Network and then click Next again. You should now be on the ‘Account Management’ page.
This is where we prepare the provisioning package to join the machine to Azure AD by supplying a Bulk Azure AD Token. Choose an expiration for the Token itself (the default is 180 days) and click the “Get Bulk Token” button. When the provisioning package is created, there are no other credentials needed to add a machine to your tenant so make sure you set the expiration date as short as possible without requiring you to re-create the provisioning package again if you haven’t completed your migration on time.
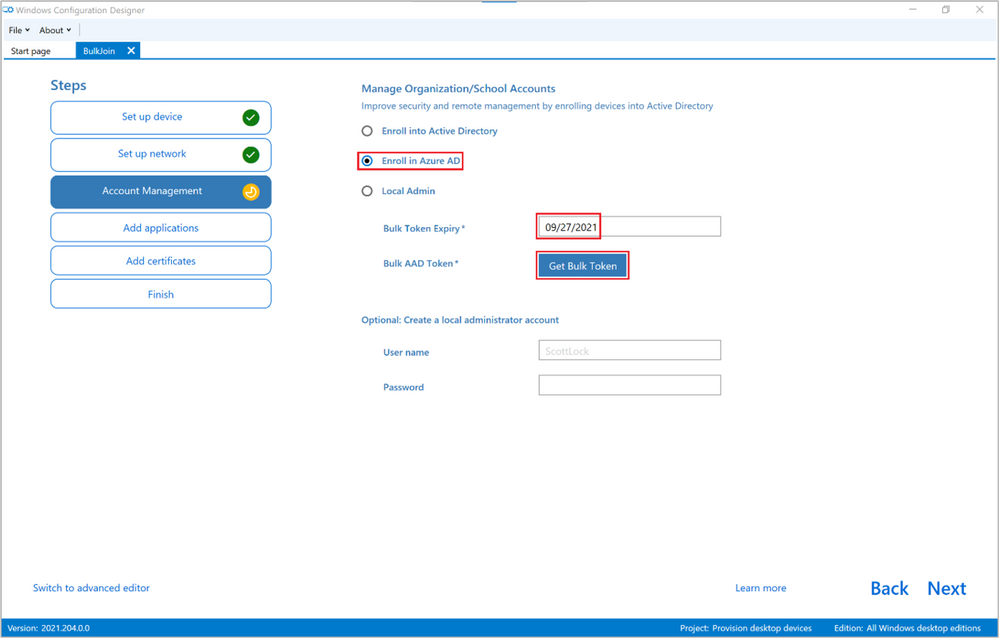 Figure 5: WCD Account Management
Figure 5: WCD Account Management
Depending on your Azure AD settings, the next couple of screens will look different, potentially asking you for multi-factor authentication (MFA) along with your credentials. Unless you have tweaked your default user settings in Azure AD, the credentials you use to request the Bulk Azure AD Token could be any valid user credentials in your tenant, it doesn’t have to be an admin or a user with any particular rights. As I will show in a bit, the Bulk Azure AD Token will be flagged with the users’ name, so I suggest you use a non-personal account or one that IT has control over. The standard Intune scenario is typically that a user enrolls their own machine and thereby attaches themselves to that device going forward. In this example, as we’re bulk enrolling hundreds of non-personal kiosks and digital signage devices it’s perfectly fine to use a non-personal account.
Note: Using a Bulk Registration token (BPRT) doesn’t count against any enrollment restrictions by number of enrolled devices, it’s for most intents and purposes considered unlimited.
As you have successfully supplied the necessary credentials and honored potential MFA requests, if this is the first time you use WCD to request a Bulk Azure AD Token, you will be presented with a Permission request as seen in Figure 6: WCD Permission request.
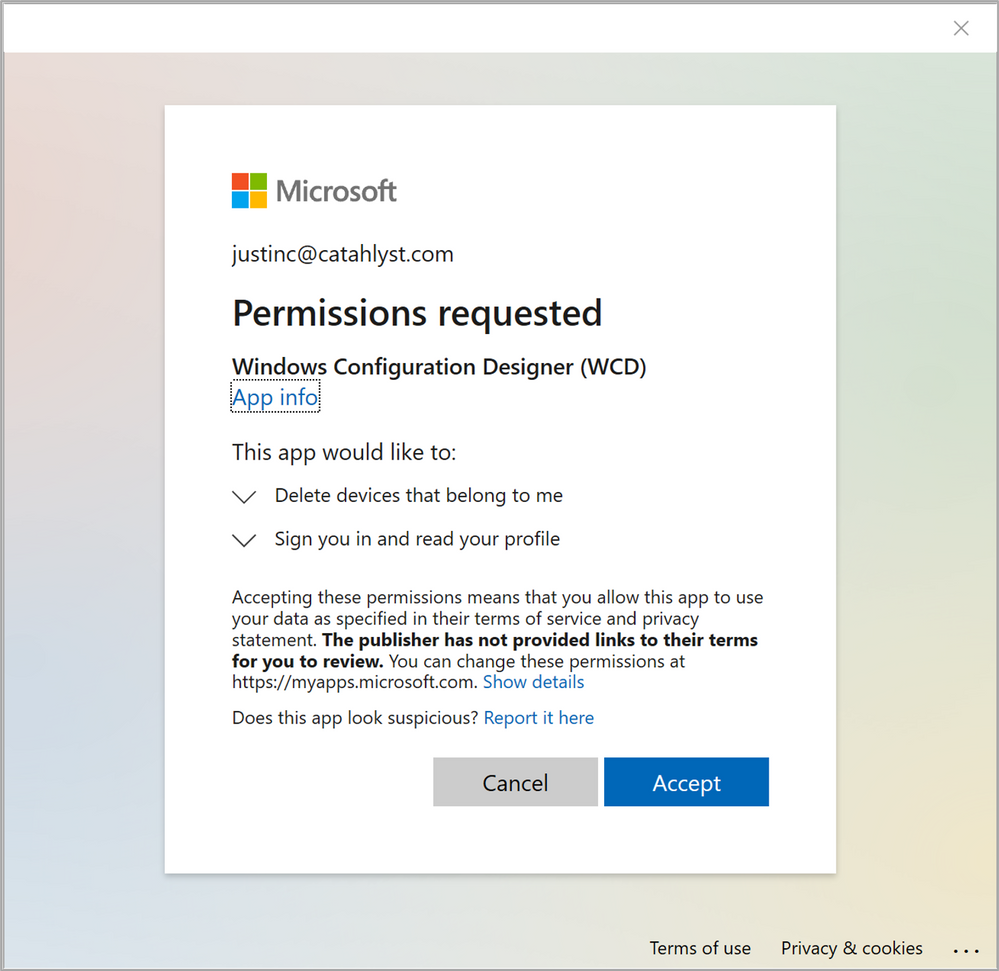 Figure 6: WCD Permission request
Figure 6: WCD Permission request
Accepting this permission request will bring you to a crucial step in the provision package creation. Please read the entire paragraph before you click Accept.
Important: In the next step, the first check box, highlighted in red in Figure 7: WCD Stay signed in to all your apps “Allow my organization to manage my device” is checked by default and will enroll the device you’re running on right now into Intune. Make sure to un-check this box. This has nothing to do with the provisioning package you’re in the middle of creating.
Do not click the “OK” button in the lower right corner of the dialog box as this will register your device (the device you’re running WCD on) in Azure AD. Instead, click the tiny text in the lower left corner “No, sign in to this app only” to start creating the Bulk Token.
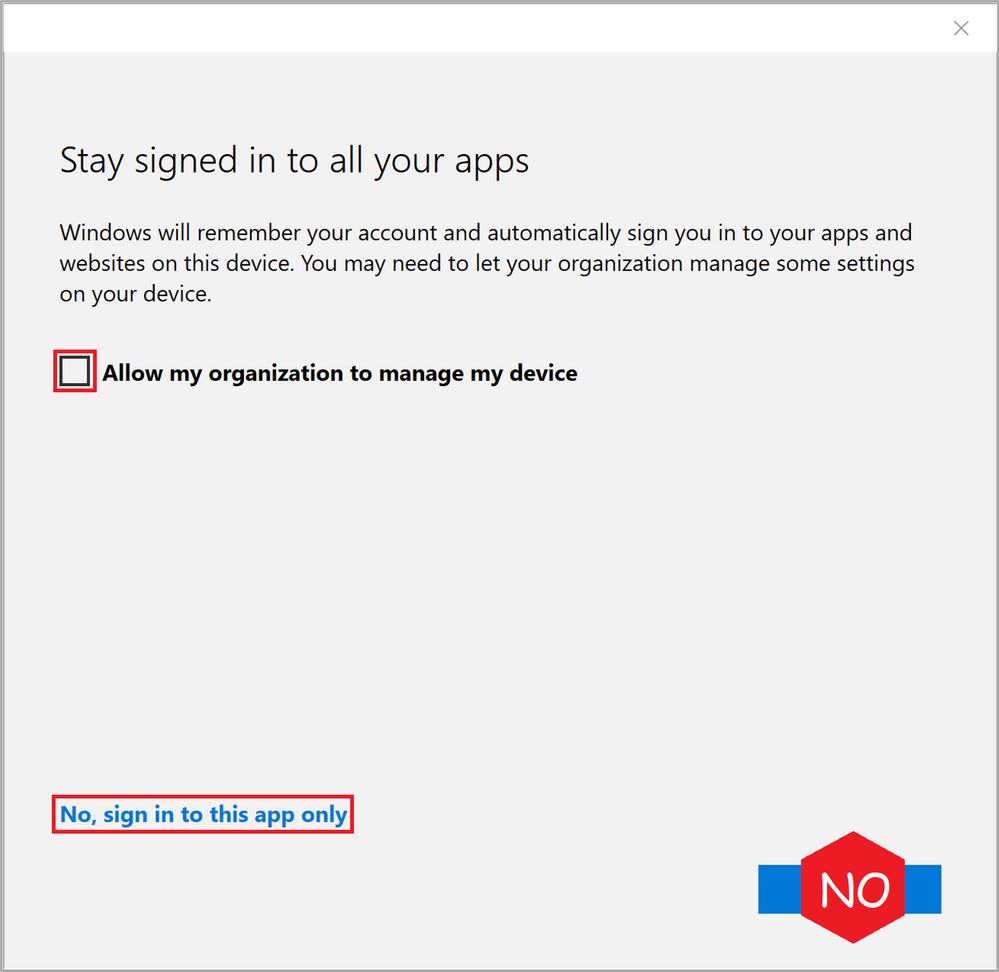 Figure 7: WCD Stay signed in to all your apps
Figure 7: WCD Stay signed in to all your apps
If you’re on any of the Insider builds, this message has now been updated to reflect this potentially unwanted behavior and avoid making mistakes. The new dialog looks like this:
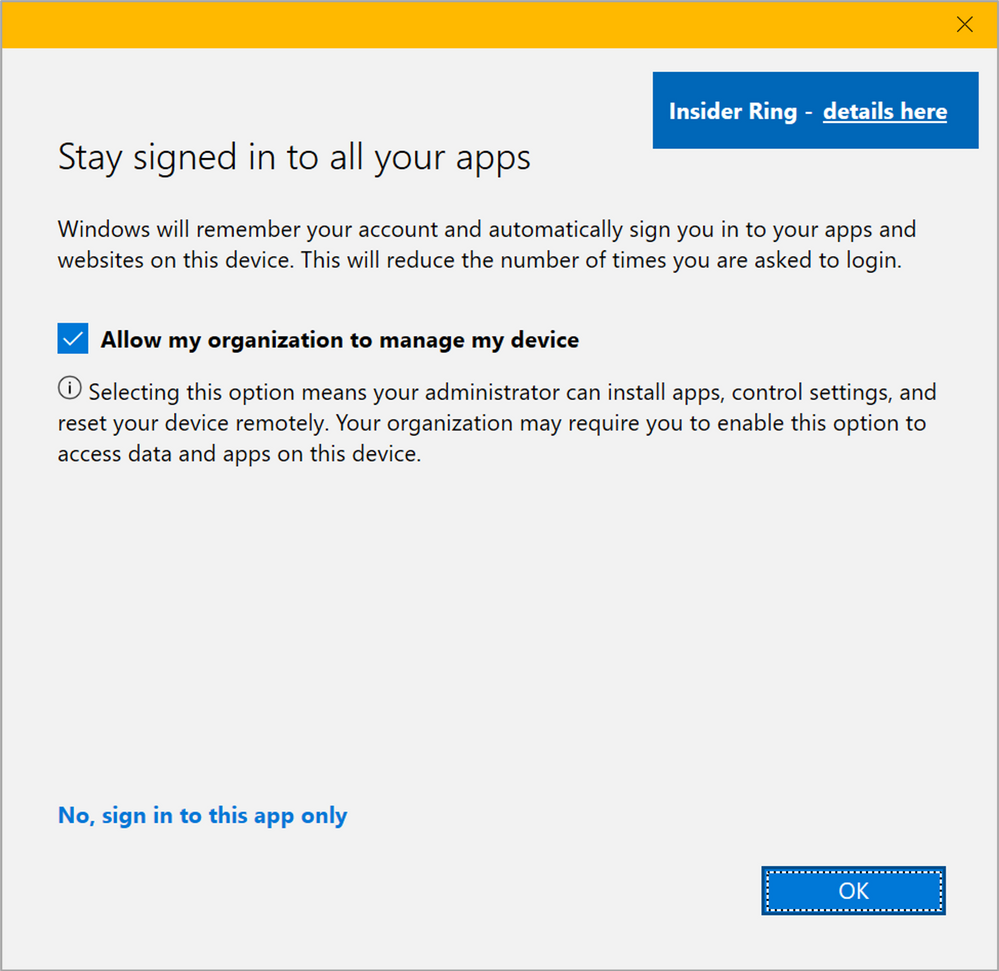 Figure 8: WCD Stay signed in to all your apps – Upcoming dialog
Figure 8: WCD Stay signed in to all your apps – Upcoming dialog
If everything was successfully created in Azure AD you will return back to the WCD editor as shown in Figure 9: Bulk Token fetched successfully.
Common errors at this stage could be:
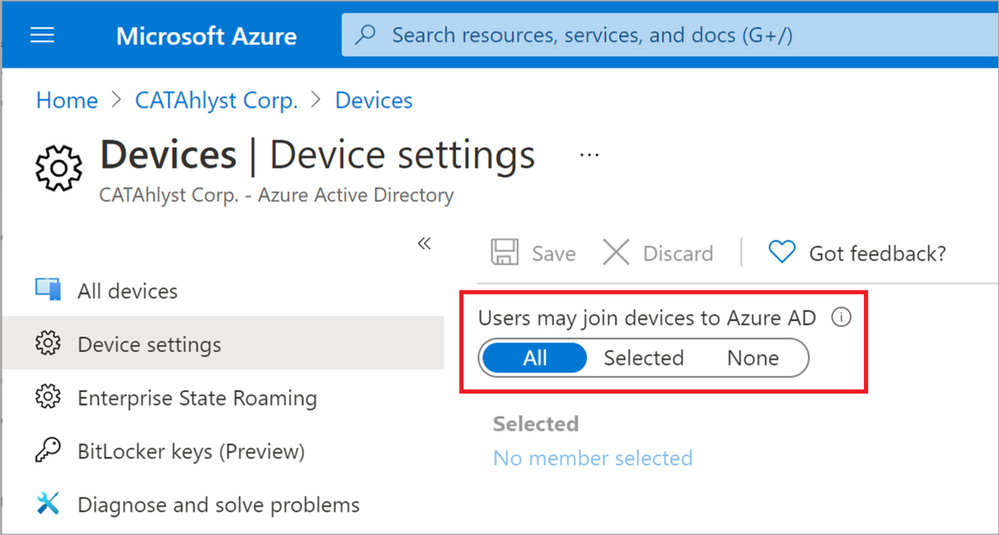 Figure 9: Users may join devices to Azure AD
Figure 9: Users may join devices to Azure AD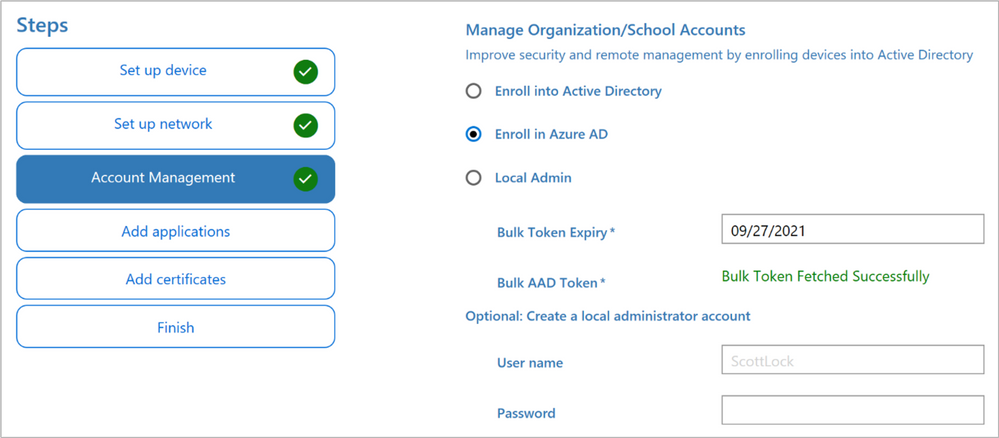 Figure 10: Bulk Token fetched successfully
Figure 10: Bulk Token fetched successfully
If you’re wondering what just happened in the backend, open up your Microsoft Endpoint Manager admin center and head over to the Users blade.
Unless you have created any Bulk Tokens in the past you should only have a single user called “package_<GUID>@yourdomain.com”. This is the placeholder account used for joining the devices, and an easy way of invalidating the provisioning package before it expires automatically would be to remove this account.
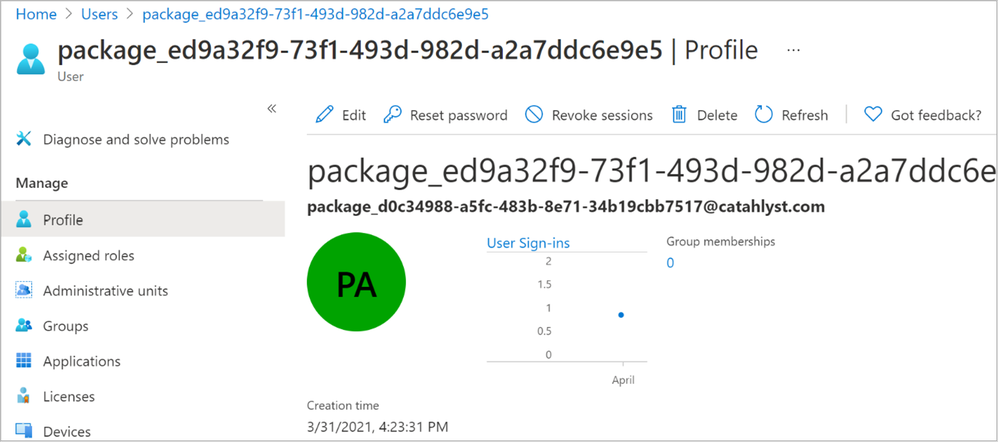 Figure 11: Bulk Token user account in AAD
Figure 11: Bulk Token user account in AAD
Want to keep track of who created a particular Bulk Token? Scrolling down to the “Contact info” section of the account will show you the UPN under “Alternate email” as seen in Figure 12.
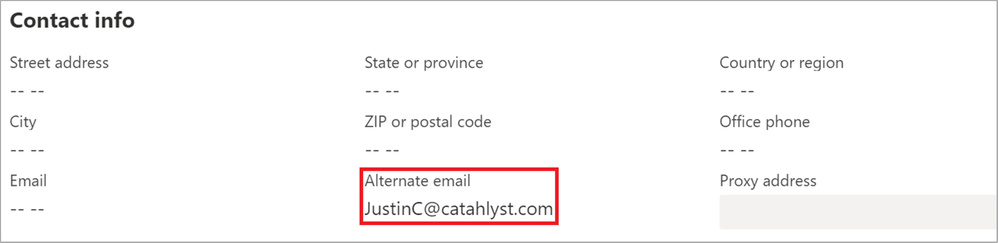 Figure 12: Alternate email contains the bulk enroller UPN
Figure 12: Alternate email contains the bulk enroller UPN
This account will be the owner of all joined devices but the user will not be assigned as the primary user, nor will it be listed on the device object as the “Enrolled by” account. We will come back to this a bit later in this post when we have joined our first machine to Azure AD.
After a slight detour in explaining the behind-the-scenes work, hopefully you’ve arrived back at the WCD editor without running into any issues and you could click through the rest of the screens without any modifications until you end up at the summary shown in Figure 13: Final WCD screen, ready to create package.
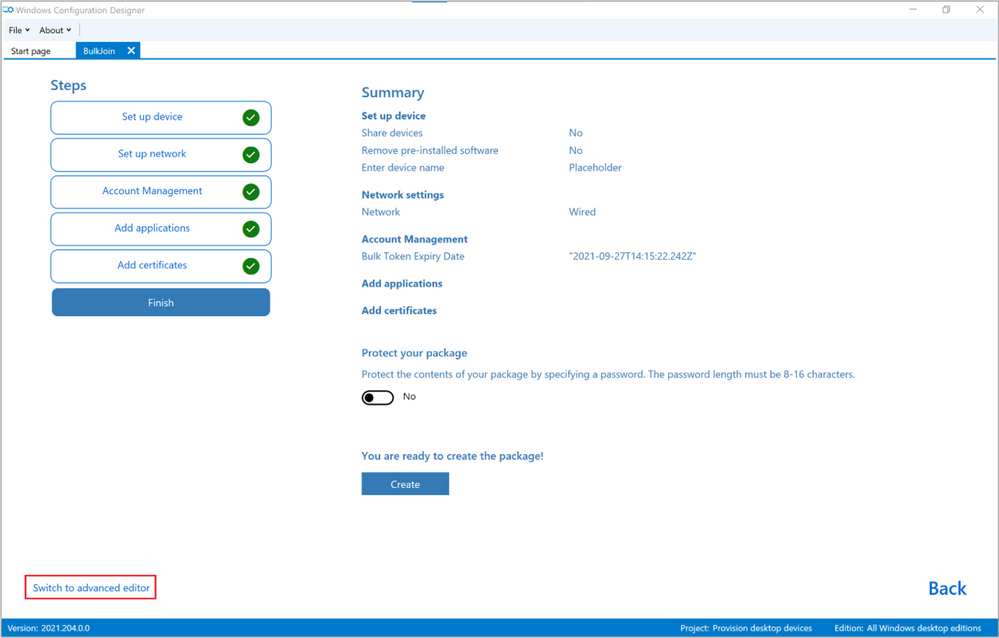 Figure 13: Final WCD screen, ready to create package
Figure 13: Final WCD screen, ready to create package
At this stage, don’t click the blue “Create” button just yet. Remember where we used “Placeholder” in the beginning of this scenario instead of specifying a proper device name? We need to clean up that reference so instead of pressing “Create”, use the option in the bottom left to “Switch to advanced editor”.
This will prompt you for confirmation as there’s no possibility of using the wizard again after you leave it. We used the Wizard simply to facilitate the Bulk Token creation so go ahead and click “Yes”.
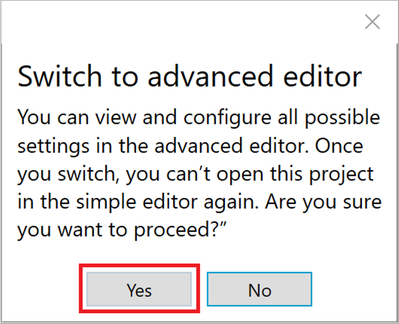 Figure 14: Switch to advanced editor
Figure 14: Switch to advanced editor
As we get into the Advanced editor, locate the DNSComputerName on the right-hand side of the screen. Clearing out the field “Placeholder” in the middle pane of the editor will not work, you will have to go to the right pane and select “Remove” to take out the DNSComputerName altogether, as shown in Figure 15: DNSComputerName removal.
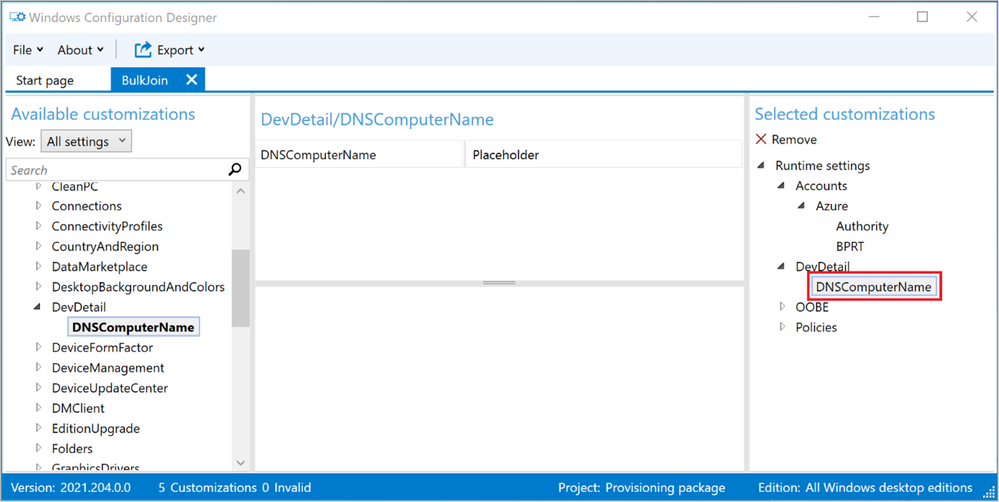 Figure 15: DNSComputerName removal
Figure 15: DNSComputerName removal
This should leave you with exactly two customizations: Authority and BPRT as shown in Figure 16: Authority and BPRT.
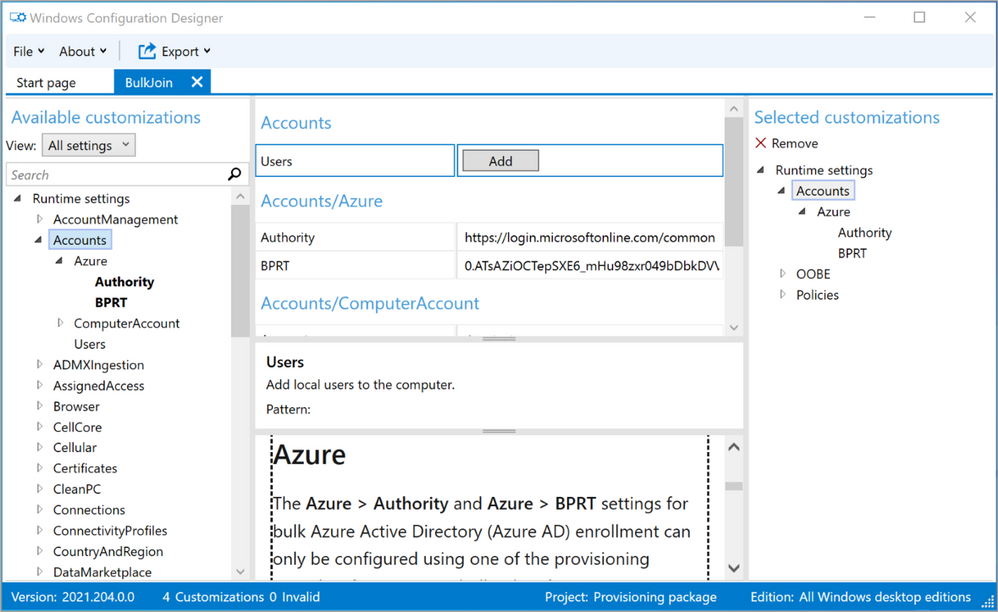 Figure 16: Authority and BPRT
Figure 16: Authority and BPRT
We knew from the start that these two items were the only one of interest to us but if you look at the “BPRT” value you can see that it’s a very long, seemingly garbled string that makes up our Bulk Token. Using PowerShell or GraphExplorer to create the BPRT would have been more work than running the Wizard and then cleaning up the DNSComputerName but feel free to ask for a PowerShell scenario and I’d be happy to add one.
With a provisioning package containing only two items/customizations we are now ready to select “Export” from the menu bar up top, shown in Figure 17: Export Provisioning package.
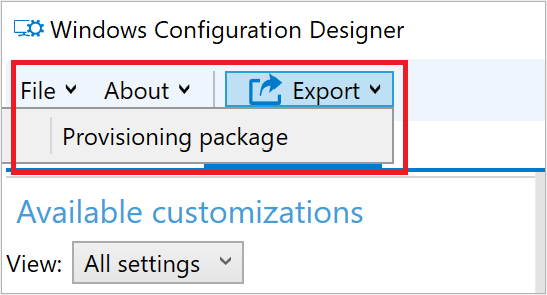 Figure 17: Export Provisioning package
Figure 17: Export Provisioning package
The next series of dialog boxes will cover provisioning package metadata as well as an option to sign the package. Signing scripts and packages is of course always recommended but as you will see in this scenario, we will consciously not sign this package as the target systems are thought of as not being managed at this point and therefore we don’t have an easy method to distribute the necessary certificate trust requirements.
On the first screen, shown in Figure 18: Describe the provisioning package we provide at set of metadata properties for easier versioning control of the package. Feel free to accept the defaults and click “Next” or provide additional data if it makes sense in your specific case. You might have several provisioning packages for different device types and if so, giving them descriptive names is a very good idea.
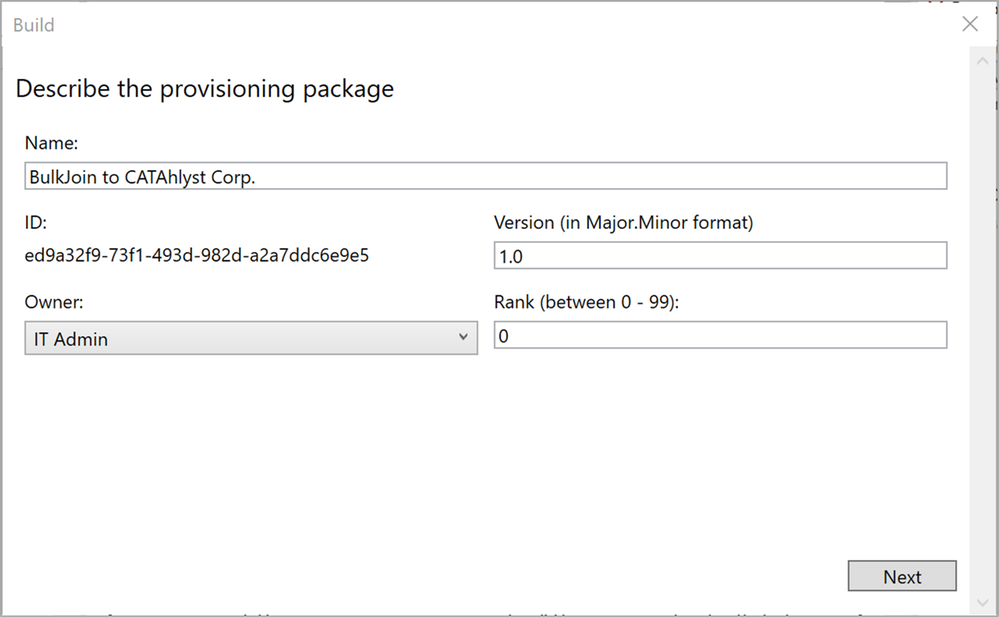 Figure 18: Describe the provisioning package
Figure 18: Describe the provisioning package
Up next is the Encrypt & Sign details which we will skip right past for the purpose of this scenario. Selecting to encrypt the package will provide you with a password and the signing process should be straight forward if you are used to signing scripts and have a code signing certificate already available on your device. Click “Next”.
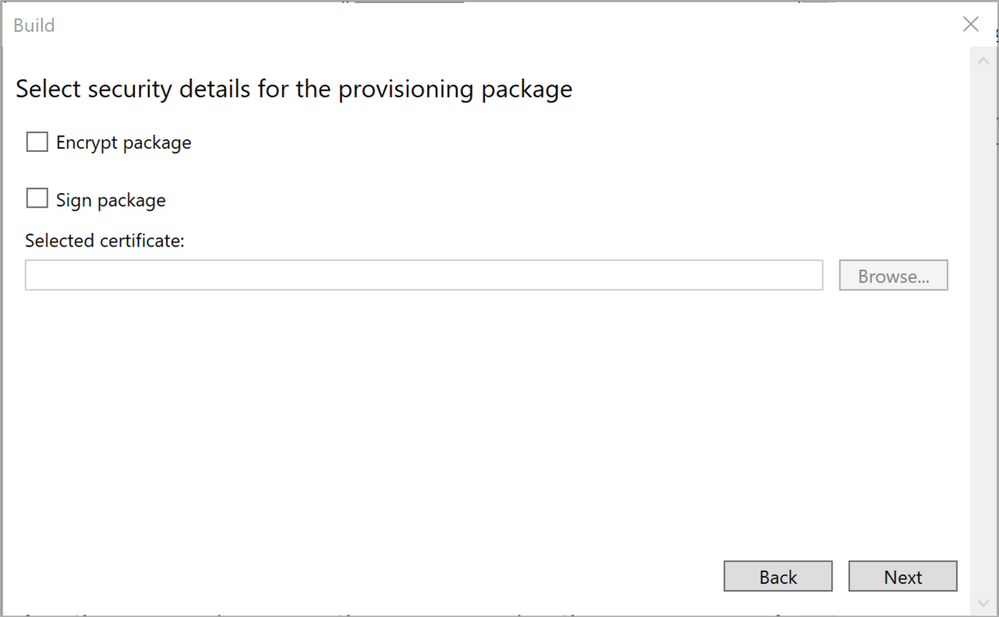 Figure 19: Security details for the provisioning package
Figure 19: Security details for the provisioning package
Select a good place to store the finished provisioning package, then click “Next”. Make sure you store the package somewhere suitable for rebuilding and/or resetting the machine you work on, in case you use a lab/test machine for the creation. I.e. the local hard drive might not be the best choice.
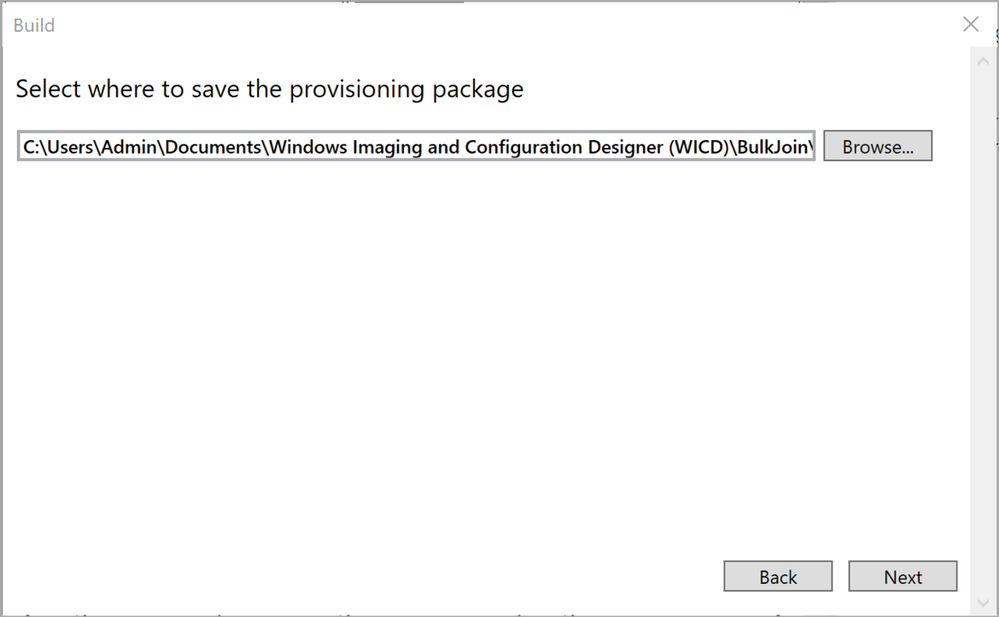 Figure 20: Select where to save the provisioning package
Figure 20: Select where to save the provisioning package
Figure 21: Build the provisioning package – Summary shows the summary screen and offers you a last chance to back out of creating the package in case you want to change something. Unless you spot something that doesn’t look right, click “Build”.
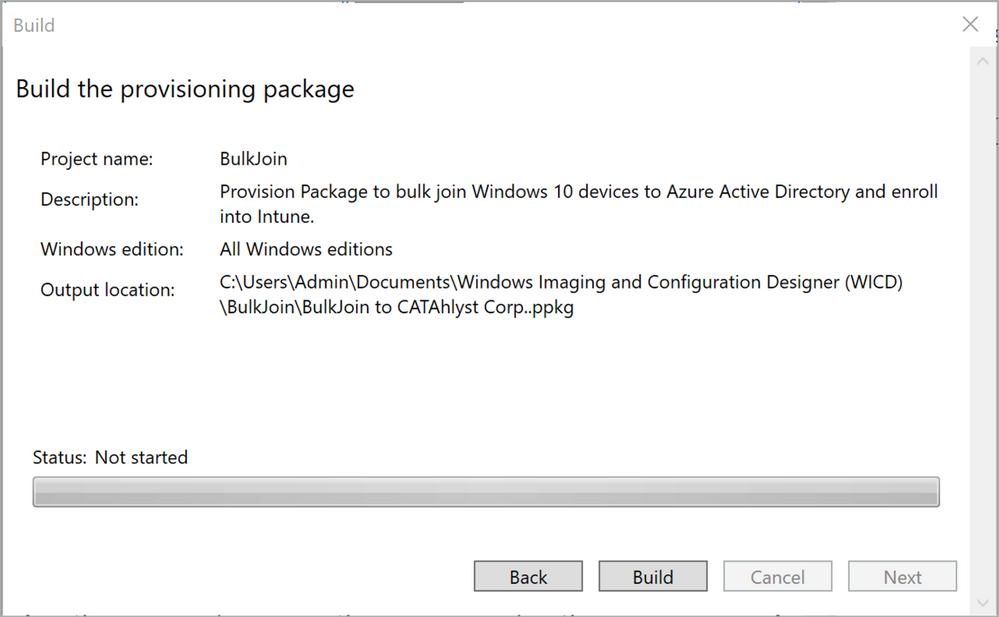 Figure 21: Build the provisioning package – Summary
Figure 21: Build the provisioning package – Summary
After a couple of seconds of creation time, your package should now be created and ready for use. Click “Finish” and we’re all done!
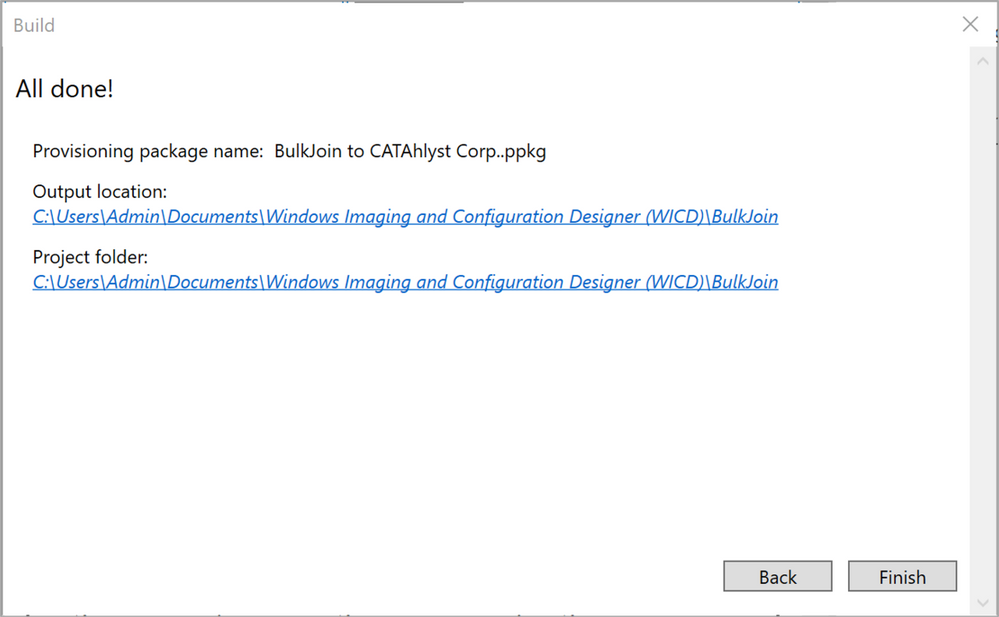 Figure 22: Provisioning package – All done!
Figure 22: Provisioning package – All done!
To test our shiny new provisioning package, find a machine that is meeting the requirements for being brought into management by Intune as well as added to Azure AD. The quickest way to check the status of a machine is probably to use the dsregcmd /status command from a PowerShell or Command Prompt. As we can see in Figure 23: we have a standalone Windows 10 device called CATScreen42, driving one of the many digital displays that CATAhlyst Corp. have spread around their locations in Europe.
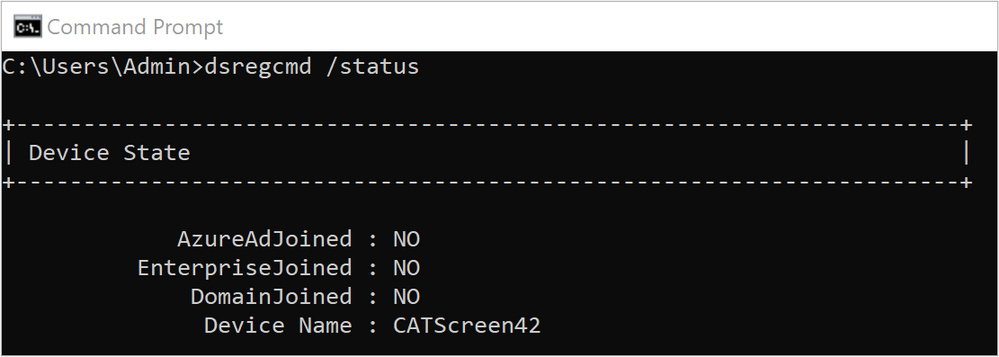 Figure 23: Device Domain Status – Pre Azure AD join
Figure 23: Device Domain Status – Pre Azure AD join
By double-clicking on the provisioning package it will launch but as we didn’t sign it, it prompts for user consent. Note that one (the only one actually) of the actions is “Enrolls in Azure Active Directory”. Click “Yes, add it” to start the Azure AD-join process.
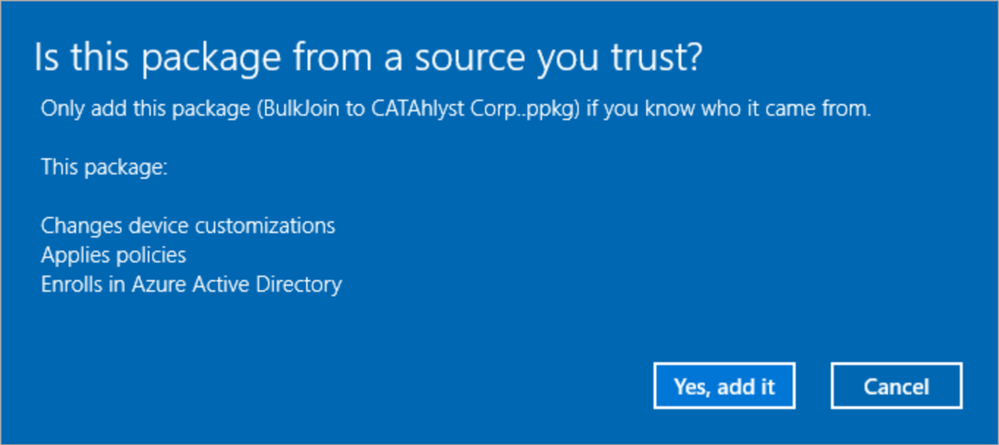 Figure 24: Provisioning package – Trusted Source
Figure 24: Provisioning package – Trusted Source
Note: If you prefer to apply the provisioning package using a Command Line instead of double-clicking it, the syntax as described here is:
DISM.exe /Image=C: /Add-ProvisioningPackage /PackagePath:C:BulkJoin.ppkg
The package should apply instantly and there is no noticeable activity on the machine. The Azure AD-join itself is instantaneous and the same way we checked on the device domain status above, let’s run the dsregcmd /status command again.
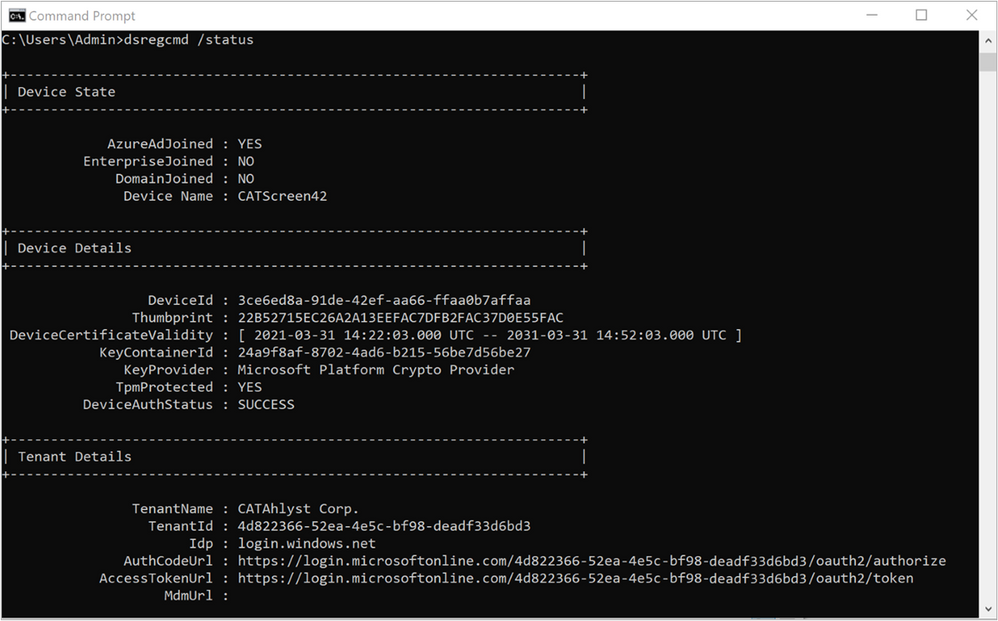 Figure 25: Device Domain Status – Post Azure AD join
Figure 25: Device Domain Status – Post Azure AD join
As if by magic, the device is now joined to Azure AD and we haven’t even rebooted the device yet.
Let’s have a look at the Sign-in blade in the Microsoft Azure console and see what has happened. This is a very busy log in an Enterprise environment so we’ll make use of the filter options to get rid of the noise. The flow is outlined in Figure 26: AAD Sign-in logs. From the Azure AD blade in the Azure portal, scroll down to “Sign-ins” and then make sure you switch to the non-interactive view as the entries we’re after are showing up here. The last step is to press the “Add filters” button and add the “User” field. If this is your first attempt at Bulk Token joining devices, specifying “package” as the string to look for is likely enough. If you have several Bulk Tokens or a naming standard that includes users with the string “package” in the name, feel free to qualify the User-field further to narrow your search as necessary.
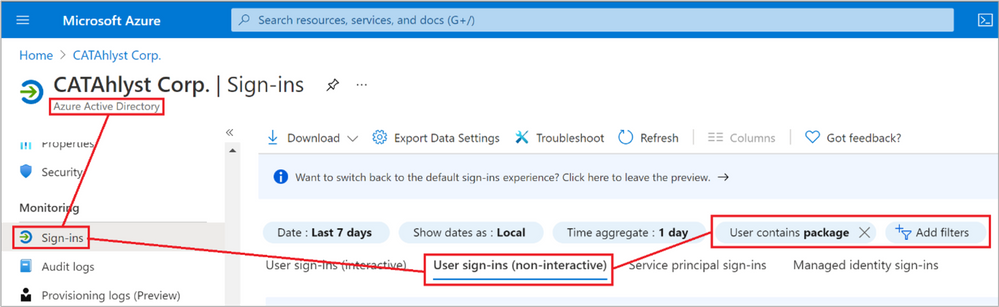 Figure 26: Azure AD Sign-in logs
Figure 26: Azure AD Sign-in logs
You should see two log entries for each device you run the provisioning package on. As the log is sorted chronologically with the oldest entry at the bottom, we first see the Device Registration entry as the device is brought into Azure AD. Right after this, in my example illustrated in Figure 27, 11 seconds later we see a Microsoft Intune Enrollment event. That’s it!
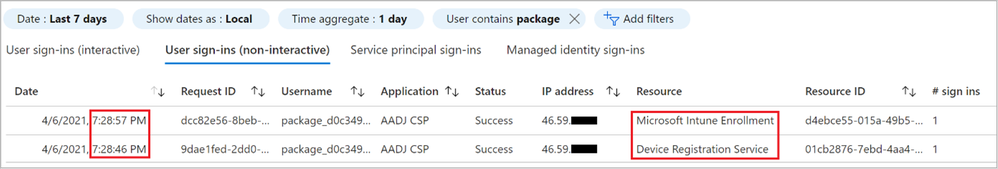 Figure 27: Sign-in log entries
Figure 27: Sign-in log entries
Diving into these individual log entries shows that for the Device Registration the Device Info details is pretty empty as the device wasn’t fully registered in Azure AD yet but for the Intune Enrollment entry we can start tracking the lifecycle of the Device ID as well as filter on some of the basic attributes of the device such as Operating System and Join Type. This will be investigated further in a future post about a new concept called Filters.
From an Azure AD perspective, the device object is owned by the Bulk Token user as seen in Figure 28.
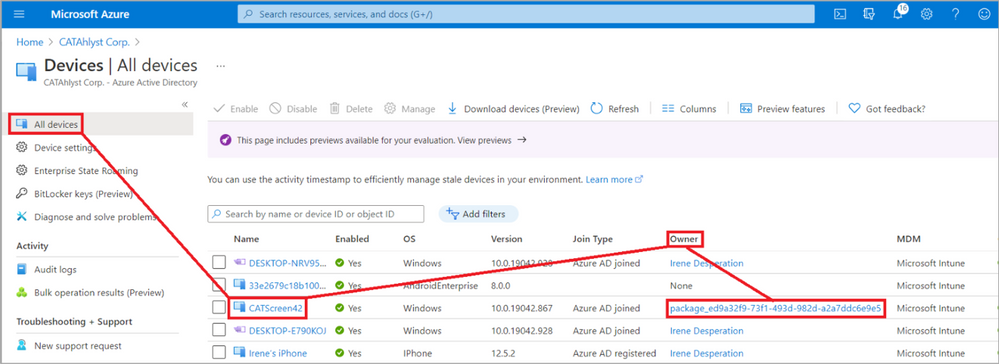 Figure 28: Azure AD Device owner
Figure 28: Azure AD Device owner
Wrapping up the scenario, you probably recall from earlier that the Bulk Token user won’t be assigned as the primary user for any of the devices it joins, nor will it be listed on the Intune device object as the “Enrolled by” account. We see this on the Overview blade for the device itself, illustrated in Figure 29.
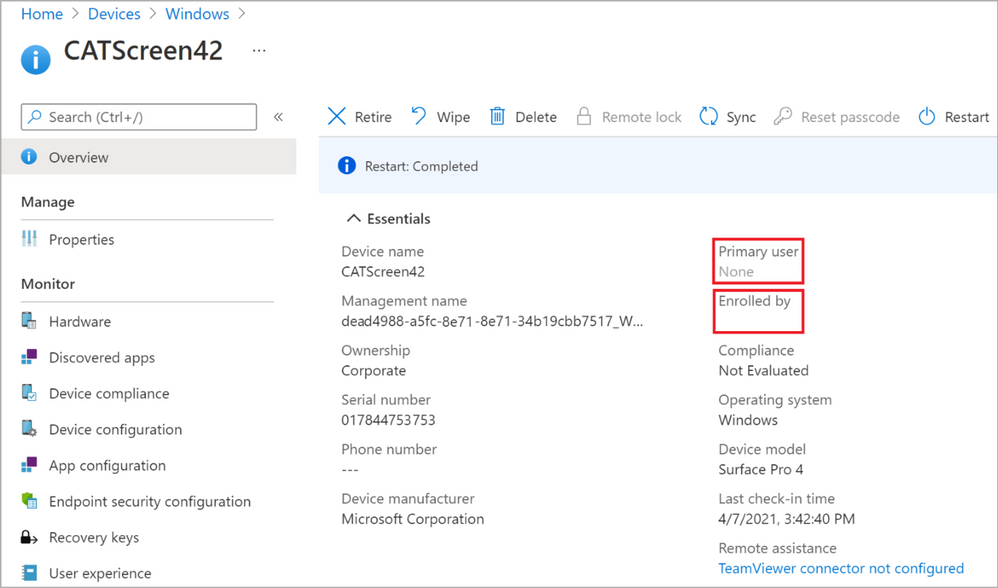 Figure 29: Primary user and Enrolled by are intentionally empty
Figure 29: Primary user and Enrolled by are intentionally empty
This could possibly be unfortunate for some scenarios but remember that this enrollment method is primarily intended for non-personal devices which shouldn’t necessarily have a primary user. The default behavior for Bulk Enrolled devices using a provisioning package is to flag the device as “Shared”. If you like, there’s always the option of assigning a primary user yourself by going to the Properties blade of the device and press the “Change primary user” button as highlighted in Figure 29.
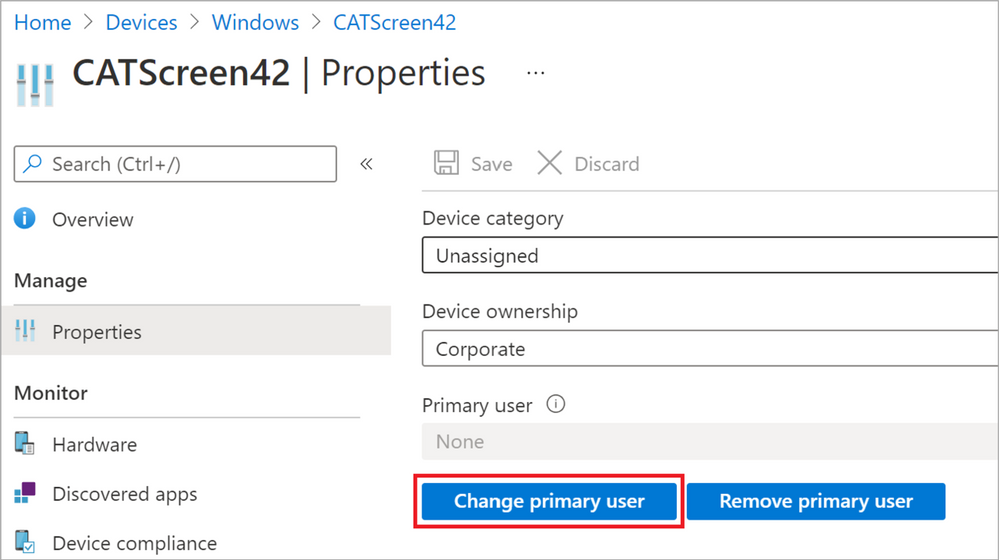 Figure 30: Change primary user for a device
Figure 30: Change primary user for a device
That concludes the “Bulk join a Windows device to Azure AD/Intune using a Provisioning package” scenario. I hope you found it useful! Let us know in the comments below or on Twitter (@IntuneSuppTeam) if you have any questions or feedback.
Recent Comments