by Scott Muniz | Oct 28, 2021 | Security, Technology
This article is contributed. See the original author and article here.
Cisco has released security updates to address vulnerabilities in multiple Cisco products. A remote attacker could exploit some of these vulnerabilities to take control of an affected system. For updates addressing lower severity vulnerabilities, see the Cisco Security Advisory
CISA encourages users and administrators to review the Cisco advisory and apply the necessary updates.
by Scott Muniz | Oct 28, 2021 | Security, Technology
This article is contributed. See the original author and article here.
The Internet Systems Consortium (ISC) has released a security advisory that addresses a vulnerability affecting multiple versions of the ISC Berkeley Internet Name Domain (BIND). A remote attacker could exploit this vulnerability to cause a denial-of-service condition.
CISA encourages users and administrators to review the ISC advisory for CVE-2021-25219 and apply the necessary updates or workaround.
by Scott Muniz | Oct 28, 2021 | Security, Technology
This article is contributed. See the original author and article here.
The Homeland Security Systems Engineering and Development Institute, sponsored by the Department of Homeland Security and operated by MITRE, has released the 2021 Common Weakness Enumeration (CWE) Most Important Hardware Weaknesses List. The 2021 Hardware List is a compilation of the most frequent and critical errors that can lead to serious vulnerabilities in hardware. An attacker can often exploit these vulnerabilities to take control of an affected system, obtain sensitive information, or cause a denial-of-service condition.
CISA encourages users and administrators to review the Hardware Weaknesses List and evaluate recommended mitigations to determine those most suitable to adopt.

by Scott Muniz | Oct 27, 2021 | Security
This article was originally posted by the FTC. See the original article here.
 There’s a fake IRS email that keeps popping into people’s inboxes. It says that you can get a third Economic Impact Payment (EIP) if you click a link that lets you “access the form for your additional information” and “get help” with the application. But the link is a trick. If you click it, a scammer might steal your money and your personal information to commit identity theft. It’s yet another version of the classic government impersonator scam.
There’s a fake IRS email that keeps popping into people’s inboxes. It says that you can get a third Economic Impact Payment (EIP) if you click a link that lets you “access the form for your additional information” and “get help” with the application. But the link is a trick. If you click it, a scammer might steal your money and your personal information to commit identity theft. It’s yet another version of the classic government impersonator scam.
Here are ways to avoid this scam:
- Know that the government will never call, text, email, or contact you on social media saying you owe money, or to offer help getting a third Economic Impact Payment (EIP). If you get a message with a link from someone claiming to be from the IRS or another government agency, don’t click on it. It’s a scam. Scammers will often send fake links to websites or use bogus email addresses and phone numbers that seem to be from the government. Your best bet is to visit the IRS’s website directly for trustworthy information on EIP payments.
- Say no to anyone who contacts you, claiming to be from a government agency and asking for personal or financial information, or for payment in cash, gift cards, wire transfers, or cryptocurrency. Whether they contact you by phone, text, email, on social media, or show up in person, don’t share your Social Security, Medicare ID, driver’s license, bank account, or credit card numbers. And know that the government would never ask you to pay to get financial help.
- Report government impersonators to ReportFraud.ftc.gov. Your report makes a difference. Reports like yours help us investigate, bring law enforcement cases, and alert people about what frauds to be on the lookout for so they can protect themselves, their friends, and family.
Visit ftc.gov/imposters to find out more about government impersonators. And to learn more about the signs of a scam, what to do, and how to report it, check out ftc.gov/scams.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.
by Scott Muniz | Oct 27, 2021 | Security
This article was originally posted by the FTC. See the original article here.
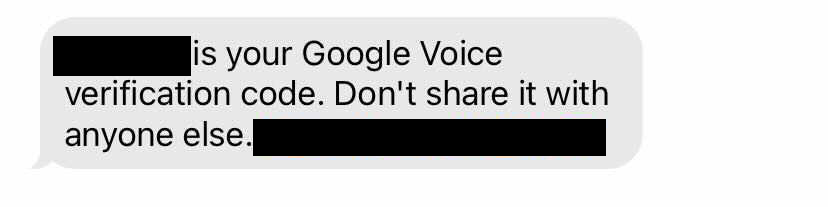
It’s Cyber Security Awareness month, so the tricks scammers use to steal our personal information are on our minds. If there’s one constant among scammers, it’s that they’re always coming up with new schemes, like the Google Voice verification scam. Have you heard about it? Here’s how it works.
Scammers target people who post things for sale on sites like Craigslist or Facebook Marketplace. They also prey on people who post looking for help finding their lost pet.
The scammers contact you and say they want to buy the item you’re selling — or that they found your pet. But before they commit to buying your item, or returning your pet, they feign hesitation. They might say they’ve heard about fake online listings and want to verify that you’re a real person. Or they might say they want to verify that you’re the pet’s true owner.
They send you a text message with a Google Voice verification code and ask you for that code. If you give them the verification code, they’ll try to use it to create a Google Voice number linked to your phone number. (Google Voice gives you a phone number that you can use to make calls or send text messages from a web browser or a mobile device.)

So, what’s the harm? The scammer might use that number to rip off other people and conceal their identity. Sometimes these scammers are after a Google Voice verification code and other information about you. If they get enough of your information, they could pretend to be you to access your accounts or open new accounts in your name.
If you gave someone a Google Voice verification code follow these steps from Google to reclaim your number.
No matter what the story is, don’t share your Google Voice verification code — or any verification code — with someone if you didn’t contact them first. That’s a scam, every time. Report it at ReportFraud.ftc.gov.
Cyber Security How-to Guides
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


 There’s a fake IRS email that keeps popping into people’s inboxes. It says that you can get a third Economic Impact Payment (EIP) if you click a link that lets you “access the form for your additional information” and “get help” with the application. But the link is a trick. If you click it, a scammer might steal your money and your personal information to commit
There’s a fake IRS email that keeps popping into people’s inboxes. It says that you can get a third Economic Impact Payment (EIP) if you click a link that lets you “access the form for your additional information” and “get help” with the application. But the link is a trick. If you click it, a scammer might steal your money and your personal information to commit 

Recent Comments