by Contributed | Sep 15, 2024 | Technology
This article is contributed. See the original author and article here.
The Azure Storage product group is heading to the SNIA Developer Conference (SDC) 2024 in Santa Clara, California, USA from September 16th through September 18th. We have a large contingent of Product Managers and Engineers responsible for Azure Blob Storage and Azure Files presenting across multiple sessions at the conference as well as the Cloud Object Storage Plugfest.
If you’re attending the conference, stop by our sessions, listen in, say “Hello!” and introduce yourself as we demonstrate how Azure Storage can accommodate the largest AI training and AI inference workloads using Azure Blob Storage. Or if you’re a Files customer, stop by our sessions on Azure Files and SMB.
Session catalog

by Contributed | Sep 13, 2024 | Technology
This article is contributed. See the original author and article here.
September V1 Title Plan has been uploaded. Go to: aka.ms/Courseware_Title_Plan

aka.ms/Courseware_Title_Plan
Don’t forget to checkout updates made to the Title Plan, shared in its permanent location, linked above.

Please note: This is not a support forum. Only comments related to this specific blog post content are permitted and responded to.
- For ILT Courseware Support, please visit: aka.ms/ILTSupport
- If you have ILT questions not related to this blog post, please reach out to your program for support.

by Contributed | Sep 13, 2024 | Technology
This article is contributed. See the original author and article here.
In this blog series dedicated to Microsoft’s technical articles, we’ll highlight our MVPs’ favorite article along with their personal insights.
Pratheep Sinnathurai, Microsoft Azure MVP, Switzerland

Azure Arc overview – Azure Arc | Microsoft Learn
“I always compare Azure Arc to the Lord of the Rings, seeing it as the one ring to rule them all. If you’re seeking a solution to manage all your Windows and Linux servers, Azure Arc could be the answer. It provides a unified management experience across diverse environments, whether on-premises, in Azure, or other clouds.
Using Azure Arc, I’ve also gained valuable insights into other technologies, such as Kubernetes (AKS) and AWS, through its Multi-Cloud Connector. This feature enhances your ability to manage and govern resources across multiple cloud platforms seamlessly.
In essence, if you’re looking for a comprehensive solution to manage your hybrid and multi-cloud infrastructure efficiently, Azure Arc offers the tools and capabilities you need.”
*Relevant Blog: In my blog post I explained how to use pre and post events fro Azure Update Manager on Azure Arc Enabled Servers.
Using Pre and Post events from Azure Update Manager on Azure Arc-Enabled Windows Server | by Pratheep Sinnathurai | Medium
Elton Bordim, Microsoft Azure MVP, Brazil

Bring Azure innovation to your hybrid environments with Azure Arc – Training | Microsoft Learn
“This content is comprehensive, helping with the solution support of Azure Arc and the supported resources. Understanding how to innovate with Azure Arc is essential nowadays, and by contributing Azure Arc content to the community, without a doubt, this training is the one I most like to recommend.”
*Relevant Activities:
– Blog: Encerramento da série: Azure Arc para iniciantes – Elton Bordim – MCT | AZ-104 | AZ-305 | SC-200 | AZ-800 e 801
– Video: Azure Arc – YouTube
Joe Carlyle, Microsoft Azure MVP, Ireland

Networking architecture design – Azure Architecture Center | Microsoft Learn
“Networking is core to Azure, and core to architecting excellent solutions. While the architecture center offers a range of guidance from foundational to niche, the networking section should be common to nearly all deployments. It is unique in its importance to Azure design.”
*Relevant Blog: A lot of my content would relate to Azure Networking, and I do have a recent blog highlighting this area – Exploring – Network Design in the Azure Architecture Center – wedoAzure
Luke Murray, Microsoft Azure MVP, New Zealand

Design review checklist for Reliability – Microsoft Azure Well-Architected Framework | Microsoft Learn
“Hyperscaler Cloud offerings, like Microsoft Azure, offer businesses worldwide to compete on a global stage, but with the ability to scale up business offerings comes more complexity and additional risk of outages. One of the key pillars (for good reason) of the Azure Well-Architected Framework is Resiliency, and Microsoft Learn offers a great way of checking off, using a data-validated approach, of not only your Resiliency at a Technical level, but Business as well, using resources, such as the Design review checklist for Reliability.”
*Relevant Blog: Running your own Azure Proactive Resiliency Assessment | luke.geek.nz
by Contributed | Sep 12, 2024 | Technology
This article is contributed. See the original author and article here.
At Microsoft Learn, we continually review and evolve our portfolio of Microsoft Certifications to help learners around the world stay up to date with the latest technologies in our fast-changing digital world, especially as AI skills become increasingly important in the workplace. Microsoft Certifications are globally recognized credentials that validate your skills for various job roles using these technologies.
According to the 2023 Skillsoft IT Skills & Salary report, 62% of those who earned certifications felt that the quality of their work improved. They’re also more engaged at work (47%) and perform their duties faster (45%). Whether you’re a student, a professional, or someone changing careers, earning a Microsoft Certification can help you accomplish your goals and demonstrate your commitment to continuous learning and improvement. This achievement can also help boost your confidence and credibility at work as you showcase your expertise to employers and customers.
What’s changing?
We regularly update our exam content, format, and delivery to help ensure that our exams are aligned with industry standards and best practices. In recent years, we’ve made significant investments in developing and launching new exams and certifications for critical roles that use Microsoft apps and services, like Azure, Microsoft 365, Dynamics 365, and Microsoft Power Platform.
We also review and adjust exam prices to help maintain the quality and value of our Certification program. As a result, effective November 1, 2024, Microsoft is updating the retail prices for its Certification exams to reflect the current market conditions and the value of the Certifications. Our goal is to make the exam pricing simpler and more consistent across geographies while still offering a fair and affordable value proposition for our Certification candidates.
What are the new prices?
The new retail prices for Certification exams vary depending on the country or region where you take the exam. For most areas, there will be no change in the price. For some areas, the price will decrease to make the exams more affordable. In a few areas, the price will increase to align with global and regional standards. To find the updated price of the exams in your area, check out the full list of new prices for Microsoft Certifications by country or region.
How does this news affect you?
If you’re planning to take a Microsoft Certification exam, you can register for and take the exam at the current price until October 31, 2024. If you register to take the exam on or after November 1, 2024, you’ll pay the updated price. Remember, in many countries and regions, the retail price is not changing and might even be decreasing. For more information on how to register and pay for your exam, go to the Microsoft Certification exam policies and FAQs.
To prepare for the Certification exam, make the most of the many resources and opportunities available on Microsoft Learn, such as free self-paced training, along with exam readiness resources, like Practice Assessments, exam prep videos, and more. You can also enroll in instructor-led training with Microsoft Training Services Partners or join the Microsoft Learn Community to prepare with peers and colleagues.
Earn a Microsoft Certification today
Microsoft Certification exams are more than just a test of your knowledge. They demonstrate your commitment, passion, and excellence in the IT industry. Earning a Certification is an investment in your professional life that can pay off in many ways, helping you build your skills and enhance your career. A Certification can boost your career prospects, improve your professional credibility, and unlock new opportunities for growth and success. Invest in your future and earn a certification today!
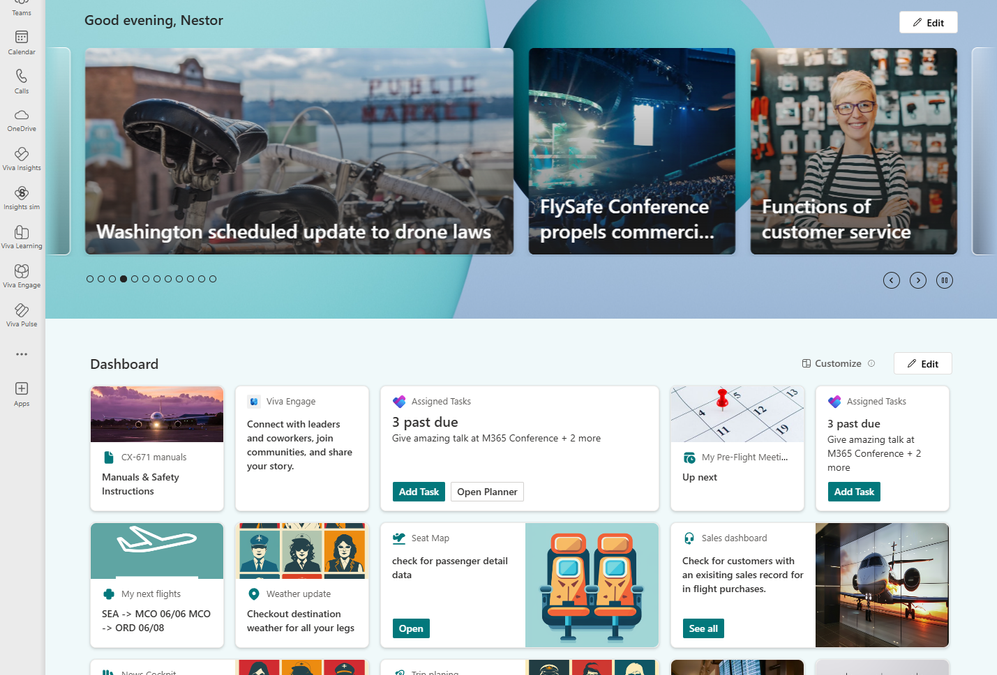
by Contributed | Sep 11, 2024 | Technology
This article is contributed. See the original author and article here.
Viva Connections is the gateway for the employee experience and provides an extensible platform through the dashboard, where employees can see a targeted list of actionable cards that can connect to Microsoft Teams apps, Viva apps and services, partner apps, and custom solutions using the SharePoint Framework (SPFx) framework, internal links, and external links.
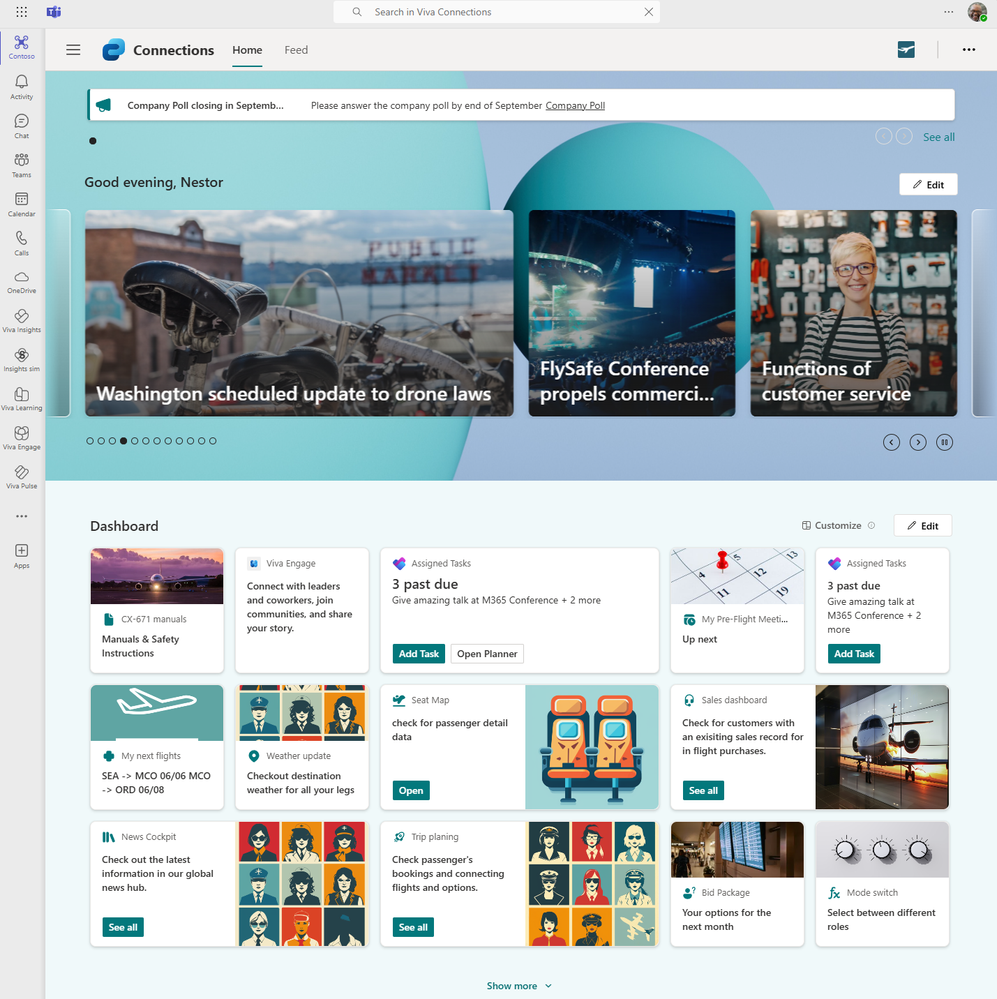 A Viva Connections dashboard showing some examples of third party cards.
A Viva Connections dashboard showing some examples of third party cards.
This blog will explore a few of our diverse third-party card integrations available from can extend the capabilities of Viva Connections, allowing organizations to incorporate third party external tools, services, and data directly into their flow of work and ensure business critical investments that they have made in other services can be added directly into employee dashboards. There are countless ways to customize or build your own dashboard cards to meet the needs of employees at virtually any organization, but this blog will highlight a few pre-packaged cards from Microsoft partners that can easily be added to your app.
With the ServiceNow card, enable employees to get support, find answers, and act on tasks across HR, IT, and other departments. Once deployed, the card offers a quick view of their task list by selecting View My Tasks. The ServiceNow Adaptive Card extension also provides a quick entry point into the app by simply selecting Visit Employee Center.

With the UKG card employees can view their respective pay information and review their work schedules, shifts, and PTO, to see a clearer picture of upcoming priorities.

Achievers for Viva Connections extends the Achievers Employee Experience platform into employees’ daily workflows. Members can enjoy some of their favorite activities found on their Achievers program: view upcoming celebrations, recognitions received, the latest trending recognitions, and perform quick actions, all on one dashboard within Viva Connections.

The Qualtrics card brings experience management into Viva Connections seamlessly. It enables quick access to surveys and feedback tools, allowing organizations to gather valuable insights and act on employee, customer, and product experiences right from the dashboard. The Qualtrics card can link directly to surveys and let employees know when feedback is due, eliminating common barriers to organization-wide feedback.

With the Workday card, Viva Connections brings Workday data and actions to employees’ fingertips right in the dashboard. With this integration, users can access Workday tasks such as inbox items, time off balances, and more, simplifying HR processes and saving employees time on administrative tasks.
Features:
- Customizable Workday® Web part in SharePoint & Adaptive Card extension for Viva Connections dashboard
- Seamless Microsoft 365 integration: Get instant access to your Workday® data right within SharePoint using our Web part integration.
- Developer-friendly: Easily customize the integration to fit your organization’s unique needs.
- Streamlined workflows: Enjoy a seamless connection between Workday® and your Microsoft 365 apps for smooth data sharing and collaboration.

The Jira integration transforms how employees manage tasks, bugs, and user stories by pulling them directly into the Viva Connections card.
Features:
- Unified view: Gain a comprehensive overview of your Jira tasks, including tickets, comments, and updates, all within a single SharePoint Web part.
- Advanced search: Quickly define your own JQL queries to locate specific sets of tasks, shining a light on your path to productivity.
- Real-Time updates: Stay informed with live data synchronization, ensuring you’re always up-to-date with the latest project developments.

The Zendesk card for Viva Connections allows users to access and manage their Zendesk tickets directly, facilitating a more efficient customer support workflow.
Features:
- Display your Zendesk data right within SharePoint with a custom web part
- Enjoy a seamless experience within your Microsoft 365 environment
- Redefine productivity by viewing and creating tickets from a single place

This seamless connection allows for the direct embedding of Asana tasks into your Viva Connections dashboard, creating a unified workspace where you can manage tasks without switching between applications.
Features:
- Integrate Asana tasks directly into SharePoint, providing a centralized view of your projects
- Utilize advanced search capabilities within Asana’s data to generate dynamic views for your SharePoint web part
- Ensure a cohesive workflow across the Microsoft 365 suite, enhancing productivity and collaboration
- Turn Viva Connections into a project management superhub by adding Asana cards

Many of the third-party cards highlighted in this blog are available through the Microsoft partner Adenin. Check out more about their Viva Connections cards in our recent partner showcase blog.
How to access and install third-party cards
There are a few simple steps to . Anyone can look up the available applications but only IT administrators can install them.
- All users can find applications via Microsoft AppSource or the SharePoint store. Installation requires administration permissions in SharePoint.
- Select “Get it Now” to request the application is added to the App Catalogue site in your SharePoint environment.
- Work with the IT Admin to Deploy the app and add it to your Viva Connections dashboard.
- Once Viva Connections is deployed for the organization, all employee users can access the app on their Viva Connections .
- Learn how to build your own dashboard cards to meet your business needs.
Learn more about third-party and adaptive cards
With dozens of third-party partner apps and M365 Viva apps to choose from, the opportunities for customization and enhanced productivity are vast. To start leveraging these powerful integrations, visit the SharePoint store and Microsoft AppSource today.

To learn more about the extensibility capabilities within the Viva Connections dashboard. View this course on Microsoft Learn.
For further guidance and resources, check out our comprehensive documentation as well as our latest blog featuring a guide of Viva Connections first-party .


Recent Comments