by Contributed | Jun 16, 2021 | Technology
This article is contributed. See the original author and article here.
It’s been a few months since our last update on Basic Authentication in Exchange Online, but we’ve been busy getting ready for the next phase of the process: turning off Basic Authentication for tenants that don’t use it, and therefore, don’t need it enabled.
We have millions of customers who have Basic Auth enabled in their tenant, but only use Modern Auth. Many of them don’t know Basic is enabled, and the risks that it presents – so we are going to do our bit to help secure their data by turning it off for them.
Over the last few months, we have been building the supporting process and tools we need to do that at scale, and now we’re ready to start rolling it out.
The Process
As we’ve said before, we’re only currently planning to turn off Basic Auth for those customers who are not using it. For customers that use still Basic for some or all the affected protocols*, we are not touching authentication settings for those protocols (for the time being).
(*as previously announced these are: Exchange Web Services (EWS), POP, IMAP, Exchange ActiveSync (EAS), Remote PowerShell (RPS) , Outlook (EWS + MAPI, RPC, and OAB) and SMTP AUTH)
We have been busy analyzing Basic Auth usage data for our customers and now have a solid understanding of who uses it and who does not. And we’re going to start turning it off for those who are not using it.
The process is: We’ll randomly select customers with no usage in any, or all affected protocols, send them a Message Center post informing them that in 30 days we’re going to turn off Basic Auth. 30 days later, we’ll turn it off and send another Message Center post to confirm it was done. Customer protected… check!
We’ve already done this for a pilot set of tenants so we feel good about how this works, but before we scale up we wanted to build a tool to help our customers just in case we get it wrong. Why would we get it wrong? Well, very low usage is hard to detect if connections are rare, and some customers might even suddenly start using Basic auth. On that note….
You should know that we can’t really tell if Basic auth usage is legitimate usage, or an account that has already been compromised – we just see this as someone logging in to the mailbox, and in this case will not disable the protocol. Now therefore is another great moment to plug the Azure AD Sign-In log, as it can help surface ‘unexpected’ usage.
What if we do not spot that new usage , and we disable Basic? What then? Well, that’s where a new tool we’ve been building comes in – a tool that provides self-service re-enablement.
We’ve built a new diagnostic into the Microsoft 365 admin center. You may have seen this before for things like EWS migration throttling, or you read this excellent recent post about it. These diagnostics have proven really popular with customers, so we simply built on that technology.
Self-Service Re-Enablement
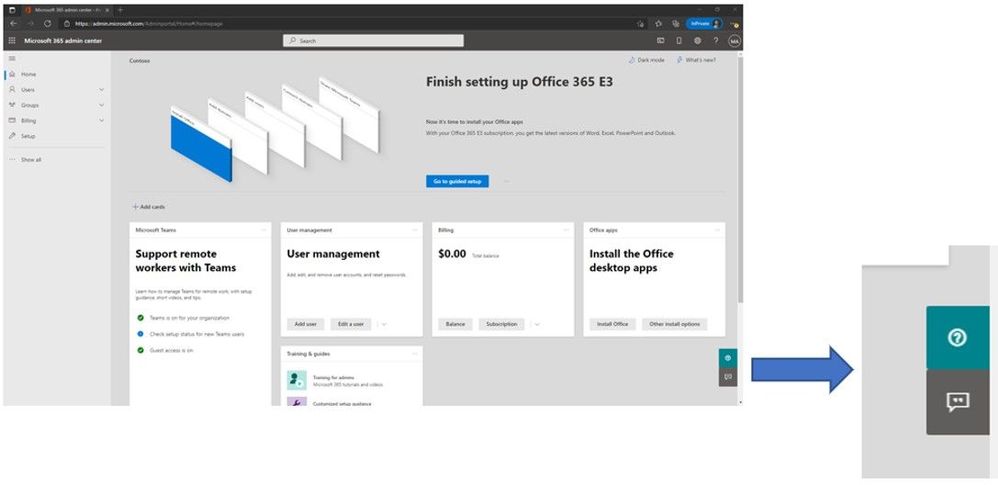
If you want to re-enable a protocol that we have disabled for Basic Auth, or want to see what protocols we have disabled, open the Microsoft 365 admin center and click the small green ? symbol in the lower right hand corner of the screen.

Once you do that you enter the self-help system which, (in case you didn’t know) can use some very clever logic to help you find a solution to all kinds of problems. But if you want to get straight to the new Basic Auth self-help diagnostic simply enter the magic phrase “Diag: Enable Basic Auth in EXO”.
(Don’t tell anyone, this is our little secret. Published on one of the most popular blogs we’ve ever had at Microsoft. Shhh.)
Once you do that, you’ll see a page very similar to this:
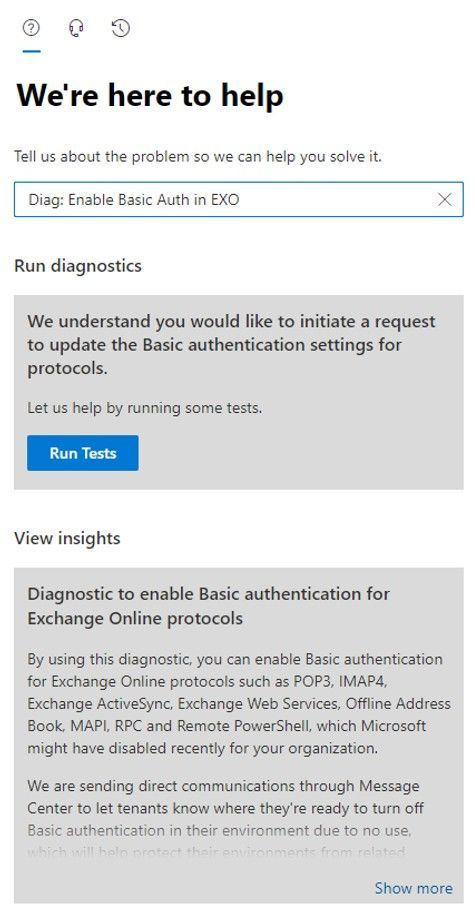
Once you click Run Tests, the tool will check your tenant settings to see if we have disabled Basic Auth for any protocols, and then display the results.
If we have not disabled Basic Auth for any protocols we’ll tell you just that. But assuming we have done something, you’ll see a list of protocols that are disabled. My tenant has the full set of protocols disabled as you can see from the following:
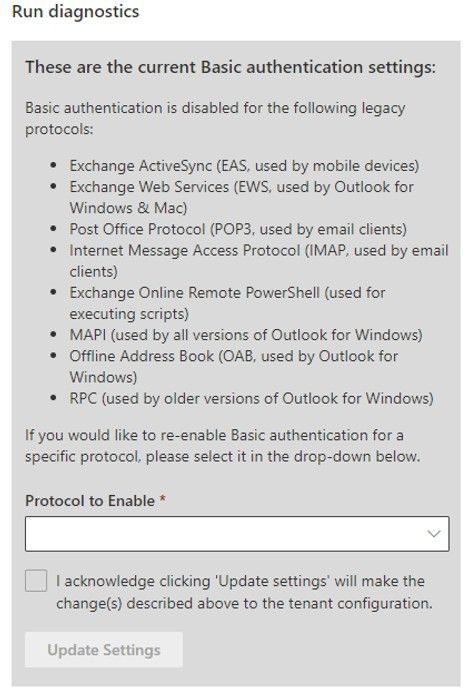
Now that’s great, you can see what we did, but the best thing is, you can also re-enable the protocols yourself (if you want to). You can simply select the protocol (or a group of protocols, in the case of Outlook), check the box to agree to the warning (you know turning Basic Auth back on is bad right?) and then click Update Settings:
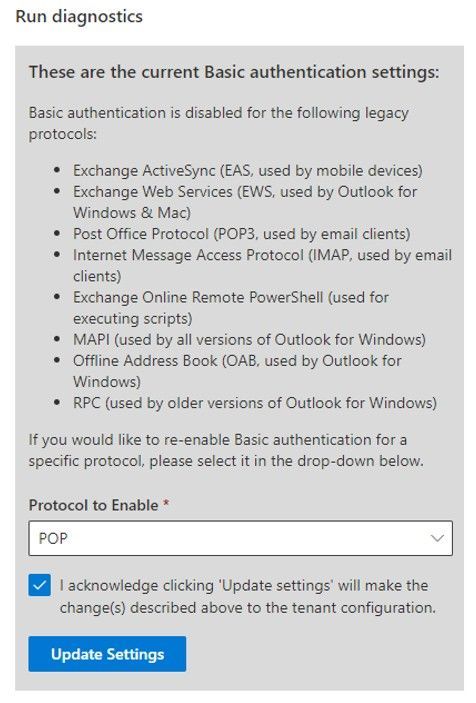
If you want to re-enable another protocol (again – why would you do that…?) re-run the diag and you can do just that.
That’s it – that’s how you can re-enable a protocol if we turn it off as part of this larger security effort. This is the only way to re-enable 8 of the 9 protocols included in the scope of this effort. (Up until the point at which we start to disable Basic Auth for protocols which are in-use – we are still planning on doing that and will have news on that later this year)
The only protocol you cannot re-enable in this way is SMTP AUTH – that’s not a part of this diagnostic because there’s already a lot of diagnostic wizardry available to help you with SMTP AUTH, and you can already switch SMTP AUTH on and off yourself by using the Set-TransportConfig cmdlet. Because unlike the other 8, all we’re doing to disable Basic Auth for SMTP AUTH is Set– SmtpClientAuthenticationDisabled to $False for tenants, and you can just go right ahead and turn it back on if you subsequently decide you need and want to use it.
One other notable difference in behavior with SMTP AUTH compared to the others is that the switch for SMTP AUTH controls Basic and OAuth client submission, they are not individually switchable. You can still enforce the use of OAuth using Conditional Access, but it’s a little more involved than just on or off for Basic, you can read more about authenticated SMTP submission here.
So how are we controlling the use of Basic Auth for the other 8 protocols? Good question, so good in fact we added that to the list of other excellent questions you might have below.
Some Questions and Answers
Why do I need this diagnostic tool? Why can’t I just go look at the Authentication Policies in my tenant and disable/delete them if I do not want Basic disabled for any protocol?
Good question! We are not turning off Basic using Authentication Policies. Therefore, Authentication Policies setting has no effect on the way that we will disable (and you can re-enable) Basic Auth using this diagnostic.
I use Basic Auth still for <insert your device, third party app, home grown app, etc. here> and I do not want you to turn it off!!
As long as your app checks mail or does whatever it does pretty regularly, we’ll consider that ‘active usage’ and not touch the authentication settings for the protocol it uses for the time being.
How exactly is Microsoft turning Basic Auth on or off on a per-protocol level?
We’ve added a new org level parameter that can be set to turn Basic Auth on or off for individual protocols within a tenant. Admins can view the parameter (-BasicAuthBlockedApps) using Get-OrganizationConfig. It’s not something you can change, and the values we store in there aren’t very user friendly, but luckily Exchange Online knows how to read and enforce them. A value of Null there means we’ve not touched your tenant. A value other than Null means we have, and the diagnostic is the way to determine what is disabled there.
I just got the Message Center post but I know I have an app that still needs to use Basic Auth. Please do not turn it off, I don’t want to have to re-enable it.
We are looking to add ‘opt-out of Basic Auth disablement’ functionality to this diag quite soon so you can do just that. The idea is that once you get the Message Center post you can use the diag to say “please don’t disable basic auth for IMAP” for example. And we’ll respect that. However… we strongly encourage you to request an opt-out only for the protocols you know you need, and don’t just ask for them all. Leaving unused protocols enabled for Basic Auth is a huge security risk to your tenant and your data.
When is Microsoft going to start turning off Basic Auth for protocols that we are actively using?
As announced earlier this year we’ve paused that program for now, but it will be coming back, so make sure you keep an eye on the blog and the Message Center for that announcement and keep working to eliminate the need for Basic Auth in your environment!
The Exchange Team
by Contributed | Jun 16, 2021 | Technology
This article is contributed. See the original author and article here.
This blog post is a collaboration between @Cristhofer Munoz and @JulianGonzalez
This installment is part of a broader series to keep you up to date with the latest features/enhancements in Azure Sentinel. The installments will be bite-sized to enable you to easily digest the new content.
Introduction
Security operations (SecOps) teams need to be equipped with the tools that empower them to efficiently detect, investigate, and respond to threats across your enterprise. Azure Sentinel watchlists empower organizations to shorten investigation cycles and enable rapid threat remediation by providing the ability to collect external data sources for correlation with security events. Additionally, correlations and analytics help SecOps stay appraised of bad actors and compromised entities across the environment. Incorporating external data and performing correlation across analytics allows security teams to get a better view of their entire infrastructure and take steps to reduce risk.
Due to evolving and constant change in the cybersecurity landscape that we live in, it is very challenging for SecOps to stay appraised of new indicators of compromise.
Azure Sentinel Watchlists provides the ability to quickly import IP addresses, file hashes, etc. from csv files into your Azure Sentinel workspace. Then utilize the watchlist name/value pairs for joining and filtering for use in alert rules, threat hunting, workbooks, notebooks and for general queries.
Due to the constant change, security analysts need the flexibility to update watchlists to stay ahead. With that in mind, we are super excited to announce the Azure Sentinel Watchlist enhancements that empower security analysts to drive efficiency by enabling the ability to update or add items to a watchlist using an intuitive user interface.
———————————————————————
For additional use case examples, please refer to these relevant blog posts:
Utilize Watchlists to Drive Efficiency during Azure Sentinel Investigations:
Utilize Watchlists to Drive Efficiency During Azure Sentinel Investigations – Microsoft Tech Community
Playbooks & Watchlists Part 1: Inform the subscription owner
https://techcommunity.microsoft.com/t5/azure-sentinel/playbooks-amp-watchlists-part-1-inform-the-sub…
Playbooks & Watchlists Part 2: Automate incident response
https://techcommunity.microsoft.com/t5/azure-sentinel/playbooks-amp-watchlists-part-2-automate-incid…
Please refer to our public documentation for other additional details.
———————————————————————
Watchlist Updating Functionality
The new watchlist UI encompasses the following functionality:
– Add new watchlist items or update existing watchlist items.
– Select and update multiple watchlist items at once via an Excel-like grid.
– Add/remove columns from the watchlist update UI view for better usability.
How to update watchlist
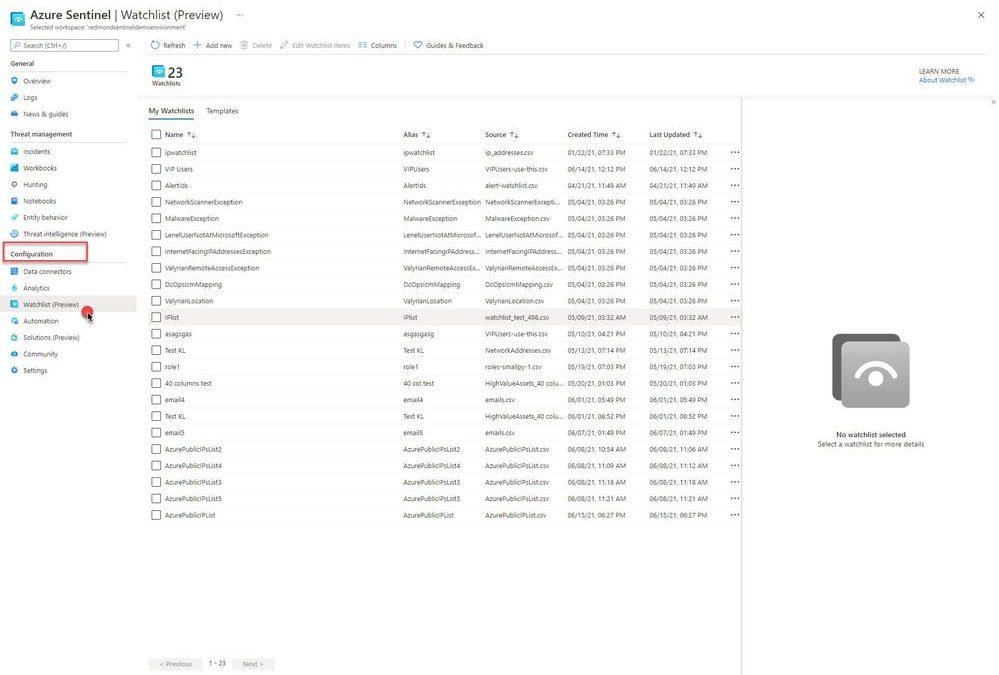
From the Azure portal, navigate to Azure Sentinel > Configuration > Watchlist
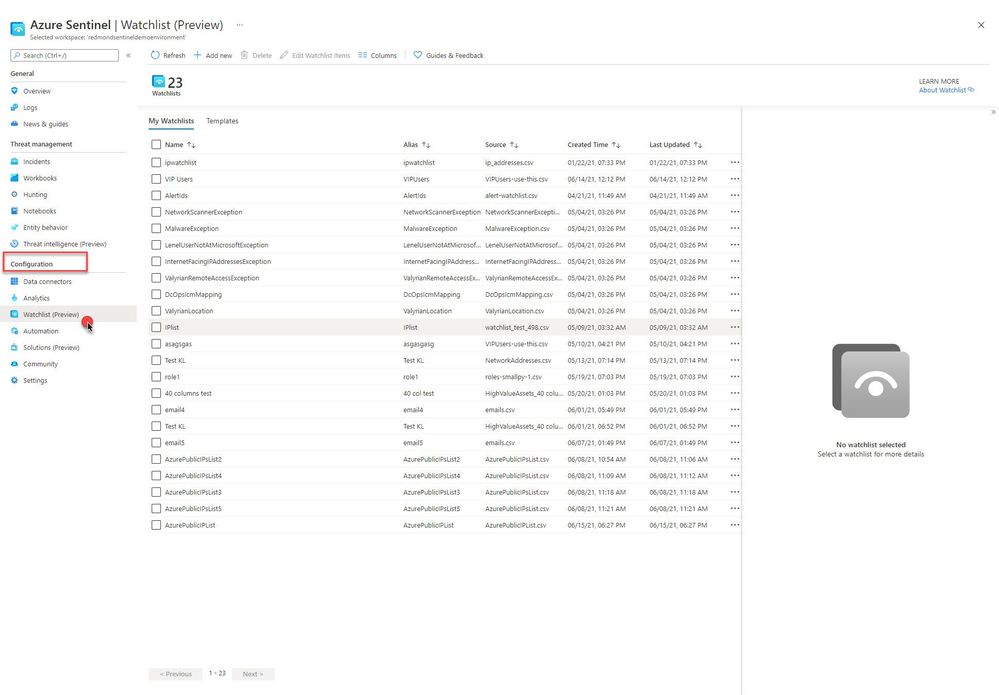
Select a Watchlist, then select Edit Watchlist Items
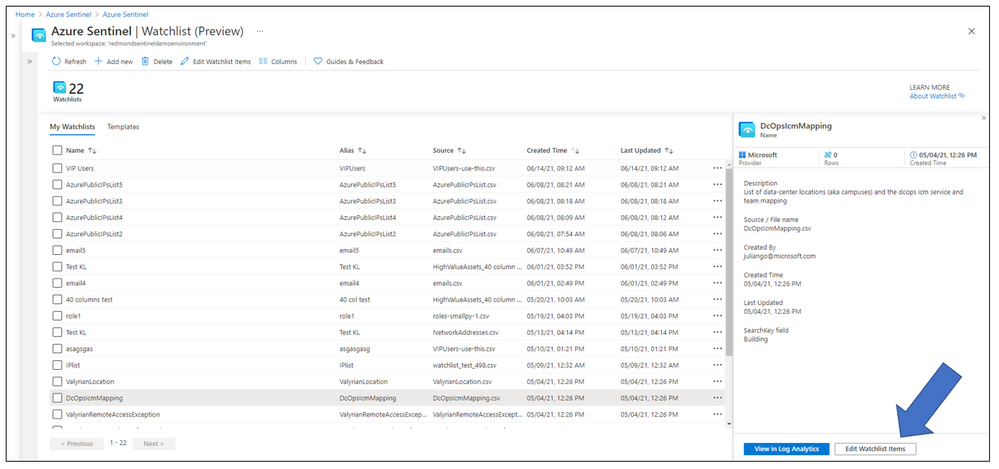
Select > Add New, update watchlist parameters
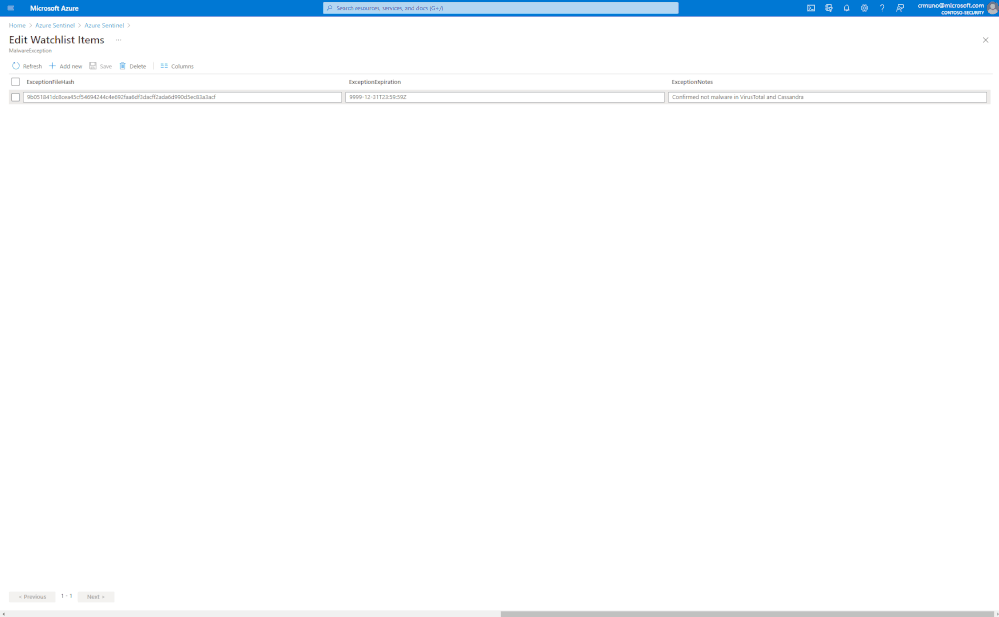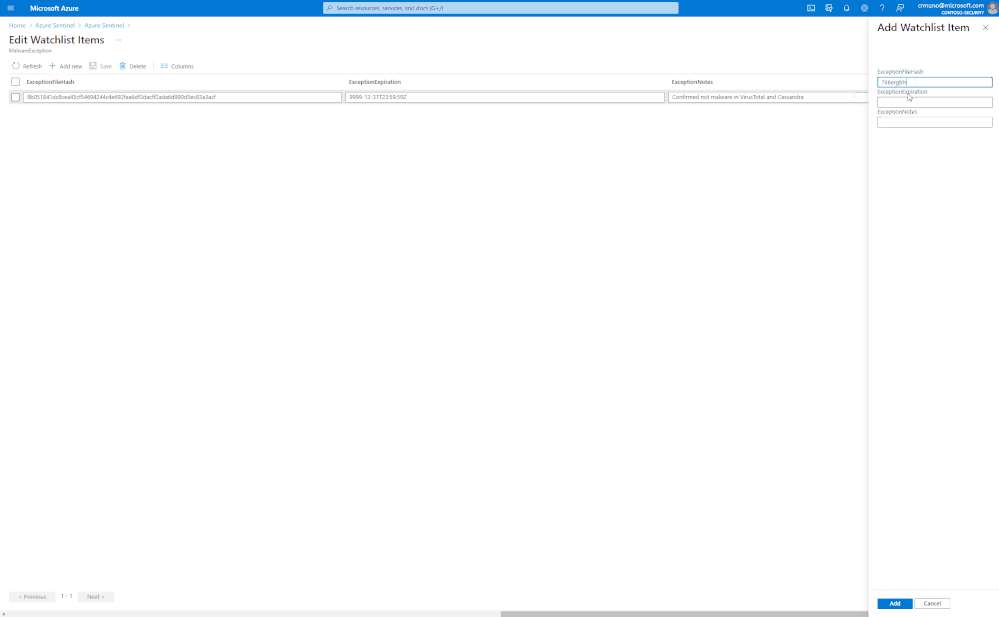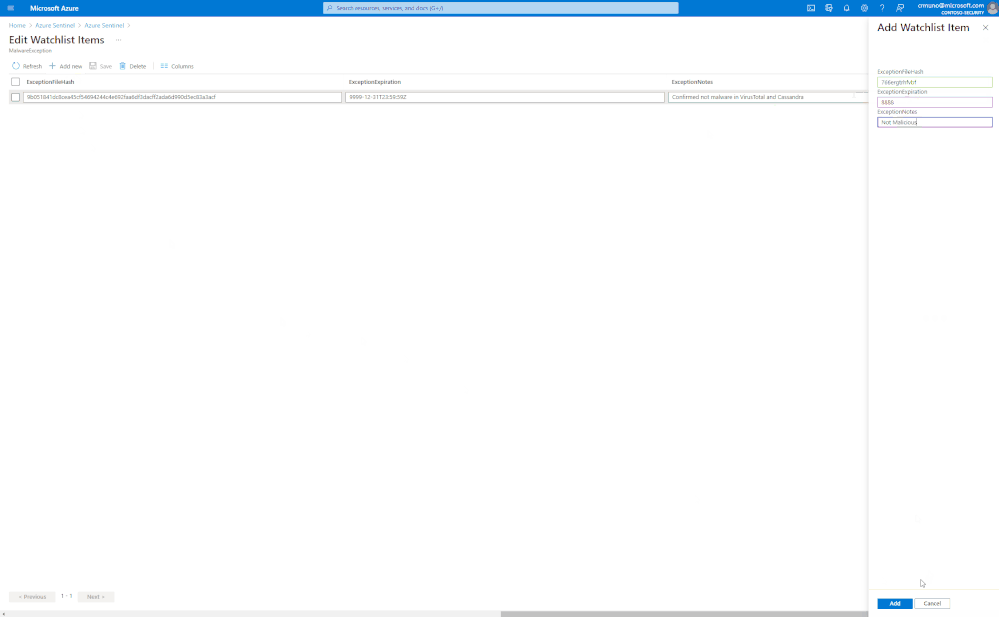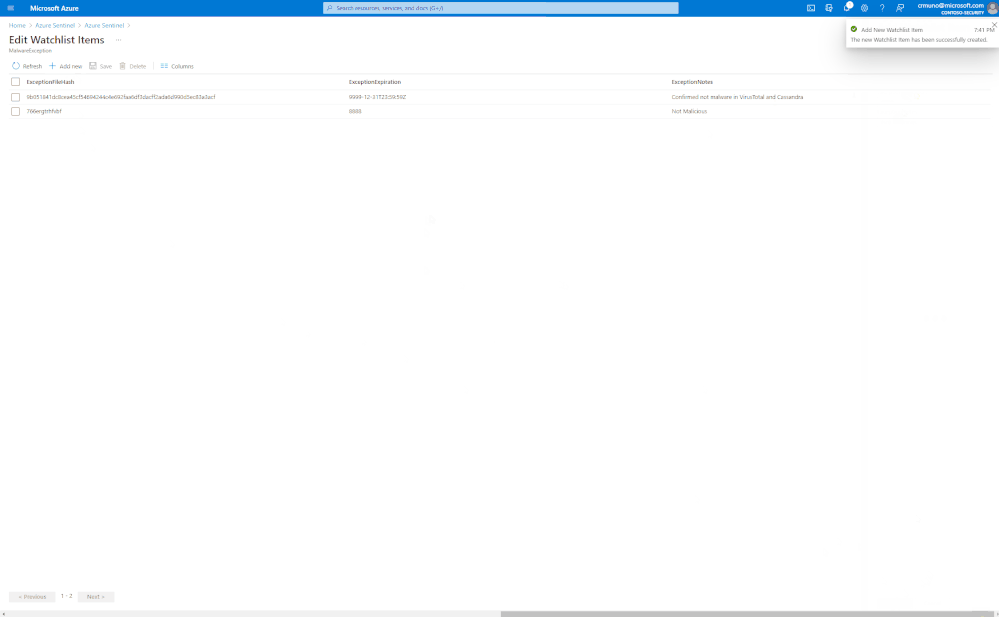
Get started today!
We encourage you to try out the new Wachlist update UI enhancement to drive efficiency across your data correlation.
Try it out, and let us know what you think!
![[ANNOUNCEMENT] Humans of IT: Amplifying Black Voices Blog Series](https://www.drware.com/wp-content/uploads/2021/06/fb_image-487.png)
by Contributed | Jun 16, 2021 | Technology
This article is contributed. See the original author and article here.

Humans of IT strives to deepen human connection to Microsoft products via meaningful community interactions, human-centered storytelling and nurturing of tech advocates. Our goal is to create excitement around using Microsoft solutions to create positive social impact.
This summer and in celebration of Juneteenth, the Humans of IT team is proud to announce the “Amplifying Black Voices” blog series. This effort is being spearheaded by Microsoft MBA intern, Skylar Dunn. The series will tell and uplift important, human centric stories of Black employees at Microsoft. The goal of the series is two-fold: to help raise awareness of the great work so many of our Black colleagues are already doing at Microsoft, and in turn, inspire and empower future generations of Black technologists with the confidence that they can achieve anything.
We’ll be kicking things off on Friday, June 18th, with weekly posts that will run through the summer.
We are excited to host this series and look forward to future collaborations with members of Microsoft’s rich and vast community.
Be sure to check back on the 18th to read the first blog of the series!

by Contributed | Jun 16, 2021 | Dynamics 365, Microsoft 365, Technology
This article is contributed. See the original author and article here.
Online fraud increased significantly during the recent pandemic and economic downturn, with losses of an estimated $12 billion worldwide.1 To ensure continuous protection, organizations need modern solutions to protect from a range of fraudfrom payment fraud, bots, account takeover, and returns and discounts fraud.
We are partnering with Worldline, the European leader in the payments and transactional services industry, to help protect thousands of global organizations and their customers from a wide scope of fraud. Worldline will integrate our award-winning Microsoft Dynamics 365 Fraud Protection services into their leading digital payments suite to provide their users additional security and trust by future-proofing their businesses.
Helping to protect world-class digital payments for a trusted world
With its global reach and its commitment to innovation, Worldline is the technology partner of choice for merchants, banks, and third-party acquirers as well as public transport operators, government agencies, and industrial companies in all sectors. Powered by over 20,000 employees in more than 50 countries, Worldline provides its clients with sustainable, trusted, and secure solutions across the payment value chain, fostering their business growth wherever they are.
Now, Worldline’s customers will benefit from Microsoft’s award-winning fraud prevention technology. Purchase protection can help protect revenue by improving the transaction acceptance rate reduce checkout friction. Account protection can help protect a business’s reputation and safeguard user accounts from abuse and fraud by combating fake account creation, account takeover, and fraudulent account access. Finally, loss prevention helps protect revenue by identifying anomalies and potential fraud on returns and discounts and provides the tools to quickly take action to mitigate losses.
How it works: scalable fraud protection across millions of transactions
Screening every transaction for traceable ‘fingerprints’ on fraudulent transactions would be impossible without technology such as the award-winning adaptive AI that powers Dynamics 365 Fraud Protection. Worldline customers can start with a mixture of pre-set fraud controls and adaptive AI that can learn to better identify fraud both on a client’s own site and as part of a globe-spanning fraud protection network. Customers will be able to see Dynamics 365 Fraud Protection working right away thanks to an intuitive user interface and real-time analytics.
Users can also customize their rules and controls to find the perfect balance of preventing fraud and reducing customer friction. Users will be able to curate their fraud prevention to meet their unique business needs with the help of a comprehensive dashboard that analyses false positives, optimizes rules to increase acceptance, and a virtual fraud analyst interface.
By leveraging the world-class digital payment and transactional services of Worldline and leading AI-powered fraud protection capabilities from Dynamics 365, customers can protect against the impact of fraud, which can range from severe disruptions to society to minor inconveniences; from widespread cyber-attacks across payment systems to day-to-day false-positive transaction alerts that can both be annoying to customers and harmful to businesses.
Our mission at Microsoft is to empower every person and every organization on the planet to achieve more. We are honored to be a part of Worldline’s leading payment solutions and to empower them to achieve their vision to “design and operate leading digital payment and transactional solutions that enable sustainable economic growth and reinforce trust and security in our societies. We make them environmentally friendly, widely accessible and support social transformation.” Read the full Worldline story.
Learn more
To learn more about Dynamics 365 Fraud Protection and our capabilities including how purchase protection helps protect your revenue by improving the acceptance rate of e-commerce transactions, how account protection helps protect your reputation by defending against bot attacks, fake account creation, account takeover, and fraudulent account access, and how loss prevention helps protect revenue by identifying anomalies on returns and discounts. For more advanced and technical details, check out our Dynamics 365 Fraud Protection documentation.
Don’t forget to read our free e-book “Protecting Customers, Revenue, and Reputation from Online Fraud” for a more in-depth look at Dynamics 365 Fraud Protection.
1-“eCommerce Fraud Presents A $12 Billion Problem,” PYMNTS, March 14, 2020.
The post How Microsoft Dynamics 365 Fraud Protection helps Worldline combat fraud appeared first on Microsoft Dynamics 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.










![[ANNOUNCEMENT] Humans of IT: Amplifying Black Voices Blog Series](https://www.drware.com/wp-content/uploads/2021/06/fb_image-487.png)


Recent Comments