
by Contributed | May 21, 2021 | Technology
This article is contributed. See the original author and article here.

Today’s technology travels at light speed; enabling faster transformation and innovation for agencies to meet mission demands. The next-era revolution features a host of cutting-edge emerging technologies that will impact and shape the future of US government on the ground and into space.
We invite you to RSVP and join the Azure Government User Community Wednesday, May 26 from 6 p.m. to 7 p.m. EST for a meetup on “What’s next? Emerging tech impacting US government” via Teams Live.
During this event, which is free and open to the public, we’ll look at several emerging technologies and what it means to government including:
- Extension of cloud capabilities and innovation to space
- Making the most of 5G networking capabilities for cloud and edge computing
- Strategies to prepare your agency for what’s next
Featured speakers:
- Jim Perkins – Senior Program Manager, Azure Edge + Platform, Microsoft
- Steve Kitay – Senior Director, Azure Space, Azure Global MisSys US, Microsoft
We hope to see you at this virtual meetup. We also invite you to join our government cloud community of 3,900 innovators by visiting https://www.meetup.com/DCAzureGov/
by Contributed | May 21, 2021 | Technology
This article is contributed. See the original author and article here.
Recently we have fixed an very interesting issue for a customer. ; sharing the details below
ISSUE:
SQL Server generates below error for every one minute.
2021-05-20 08:15:09.96 spid32s Error: 17053, Severity: 16, State: 1.
2021-05-20 08:15:09.96 spid32s UpdateUptimeRegKey: Operating system error 5(Access is denied.) encountered.
2021-05-20 08:16:10.08 spid24s Error: 17053, Severity: 16, State: 1.
2021-05-20 08:16:10.08 spid24s UpdateUptimeRegKey: Operating system error 5(Access is denied.) encountered.
Even though there is no impact these messages fill up the error log and are noisy.
Background:
Every 1 minute, SQL wakes up and updates the Process ID and the Uptime in the registry keys
Key Name: HKEY_LOCAL_MACHINESOFTWAREMicrosoftMicrosoft SQL ServerMSSQL14.MSSQLSERVERMSSQLServer
Name: uptime_pid
Type: REG_DWORD
Data: 0x1a5c
Name: uptime_time_utc
Type: REG_BINARY
Data: 00000000 98 61 19 0e 42 4e d7 01 –
Troubleshooting and solution :
- SQL Server writes the PID and Uptime of SQL process to Registry key for every one minute and this operation is failing with “Access denied” hence the error.
- We provided permission to the SQL Service Account on the required registry key (HKEY_LOCAL_MACHINESOFTWAREMicrosoftMicrosoft SQL ServerMSSQL14.MSSQLSERVERMSSQLServer) but it didn’t fix the issue.
- From the process monitor, it has been identified that Office components are interacting with SQL Server while writing the data to registry key.
- We have identified that SQL Server is using MS Office components to import and export data into Excel through BULK Insert queries. So we couldn’t uninstall Office.
- The Office has been upgraded to latest version but still the issue persists
- Upon further investigation, we have identified that Office is using Virtual registry and we need to bypass it.
- For the same we have added (Don’t overwrite it) the required SQL reg key(HKEY_LOCAL_MACHINESOFTWAREMicrosoftMicrosoft SQL ServerMSSQL14.MSSQLSERVERMSSQLServer) to the list of exceptions at HKEY_LOCAL_MACHINESOFTWAREMicrosoftOfficeClickToRunREGISTRYMACHINESoftwareMicrosoftAppVSubsystemVirtualRegistry under “passthroughPaths” and this fixed the issue.
Thanks,
Rambabu Yalla
Support Escalation Engineer
SQL Server Team

by Contributed | May 21, 2021 | Technology
This article is contributed. See the original author and article here.
Some time ago I wrote this post about different storage options in Azure Red Hat OpenShift. One of the options discussed was using Azure NetApp Files for persistent storage of your pods. As discussed in that post, Azure NetApp Files (ANF) has some advantages:
- ReadWriteMany support
- Does not count against the limit of Azure Disks per VM
- Different performance tiers, the most performant one being 128MiB/s per TiB of volume capacity
- The NetApp tooling ecosystem
There is one situation where Azure NetApp Files will not be a great fit: if you only need a small share, since the minimum pool size in which Azure NetApp Files can be ordered is 4 TiB. You can carve out many small volumes out of that pool with 4 TiB of capacity, but if the only thing you need is a small share, other options might be more cost effective.
The three different performance tiers of Azure NetApp Files can be very flexible, offering between 16 and 128 MiB/s per provisioned TiB. For example, at 1 TiB a Premium SSD (P30) would give you 200 MiB/s, while a an ANF volume would give you up to 128 MiB/s. Not quite the performance of a Premium SSD, but it doesn’t fall too far behind either.
But’s let’s go back to our post title: what is Trident? In a standard setup, you would have to create the ANF volume manually, and assign it to the different pods that need it. However, with the project Trident NetApp offers the possibility for the Kubernetes clusters of creating and destroying those volumes automatically, tied to the Persistent Volume Claim lifecycle. Hence, when the application is deployed to OpenShift, nobody needs to go to the Azure Portal and provision storage in advance, but the volumes are created using the Kubernetes API, through the functionality of Trident.
As the Trident documentation says, OpenShift is a supported platform. I did not find any blog about whether it would work on Azure RedHat OpenShift (why shouldn’t it?), so I decided to give it a go. I installed Trident on my ARO cluster following this great post by Sean Luce: Azure NetApp Files + Trident, and it was a breeze. You need the client tooling tridentctl, which will do some of the required operations for you (more to this further down).
I created the ANF account and pool with the Azure CLI (Sean is using the Azure Portal). Trident needs a Service Principal to interact with Azure NetApp Files. In my case I am using the cluster SP, to which I granted contributor access for the ANF account:
az netappfiles account create -g $rg -n $anf_name -l $anf_location
az netappfiles pool create -g $rg -a $anf_name -n $anf_name -l $anf_location –size 4 –service-level Standard
anf_account_id=$(az netappfiles account show -n $anf_name -g $rg –query id -o tsv)
az role assignment create –scope $anf_account_id –assignee $sp_app_id –role ‘Contributor’
Now you need to install the Trident software (unsurprisingly, Helm is your friend here), and add a “backend”, which will teach Trident how to access that Azure NetApp Files pool you created a minute ago:
# Create ANF backend
# Credits to https://github.com/seanluce/ANF_Trident_AKS
subscription_id=$(az account show –query id -o tsv)
tenant_id=$(az account show –query tenantId -o tsv)
trident_backend_file=/tmp/trident_backend.json
cat <<EOF > $trident_backend_file
{
“version”: 1,
“storageDriverName”: “azure-netapp-files”,
“subscriptionID”: “$subscription_id”,
“tenantID”: “$tenant_id”,
“clientID”: “$sp_app_id”,
“clientSecret”: “$sp_app_secret”,
“location”: “$anf_location”,
“serviceLevel”: “Standard”,
“virtualNetwork”: “$vnet_name”,
“subnet”: “$anf_subnet_name”,
“nfsMountOptions”: “vers=3,proto=tcp,timeo=600”,
“limitVolumeSize”: “500Gi”,
“defaults”: {
“exportRule”: “0.0.0.0/0”,
“size”: “200Gi”
}
}
EOF
tridentctl -n $trident_ns create backend -f $trident_backend_file
After this, we need a way for OpenShift to use this backend, through standard Kubernetes constructs as any other OpenShift storage technology: with a storage class.
# Create Storage Class
# Credits to https://github.com/seanluce/ANF_Trident_AKS
cat <<EOF | kubectl apply -f –
apiVersion: storage.k8s.io/v1
kind: StorageClass
metadata:
name: azurenetappfiles
provisioner: netapp.io/trident
parameters:
backendType: “azure-netapp-files”
EOF
So OpenShift now will have now 2 storage classes: the default one, which leverages managed Azure Premium disks, plus the new one that has been created to interact with ANF:
$ kubectl get sc
NAME PROVISIONER RECLAIMPOLICY VOLUMEBINDINGMODE ALLOWVOLUMEEXPANSION
azurenetappfiles csi.trident.netapp.io Delete Immediate false
managed-premium (default) kubernetes.io/azure-disk Delete WaitForFirstConsumer true
And here the magic comes: when a Persistent Volume Claim is created and associated to that storage class, an ANF volume will be instantiated too, matching the parameters specified in the PVC. To create the PVC I will stick to Sean’s example, with a 100 GiB volume:
# Create PVC
# Credits to https://github.com/seanluce/ANF_Trident_AKS
cat <<EOF | kubectl apply -f –
kind: PersistentVolumeClaim
apiVersion: v1
metadata:
name: azurenetappfiles
spec:
accessModes:
– ReadWriteMany
resources:
requests:
storage: 100Gi
storageClassName: azurenetappfiles
EOF
The PVC is now visible in OpenShift:
$ kubectl get pvc
NAME STATUS VOLUME CAPACITY ACCESS MODES STORAGECLASS AGE
azurenetappfiles Bound pvc-adc0348d-5752-4e44-82c2-8205f39c376d 100Gi RWX azurenetappfiles 8h
And sure enough, you can use the Azure Portal to browse your account, pool, and the newly created volume:

The Azure CLI will give us as well information about the created volume. The default output was a bit busy and didn’t fit in my screen width, so I created my own set of options that I was interested in:
$ az netappfiles volume list -g $rg -a $anf_name -p $anf_name -o table –query ‘[].{Name:name, ProvisioningState:provisioningState, ThroughputMibps:throughputMibps, ServiceLevel:serviceLevel, Location:location}’
Name ProvisioningState ThroughputMibps ServiceLevel Location
——————————————————– ——————- —————– ————– ———–
anf5550/anf5550/pvc-adc0348d-5752-4e44-82c2-8205f39c376d Succeeded 1.6 Standard northeurope
Interestingly enough, I couldn’t see the volume size in the object properties, but it can be easily inferred: the volume is Standard, and from the Azure NetApp Files performance tiers we know that Standard means 16 MiB/s per provisioned TiB. Hence, 1.6 MiB/s means 100 GiBs: Maths still work!
I used my sqlapi image, which includes a rudimentary I/O performance benchmark tool based on this code by thodnev, to verify those expected 1.6 MiB/s:
# Deployment
name=api
cat <<EOF | kubectl apply -f –
apiVersion: apps/v1
kind: Deployment
metadata:
name: $name
labels:
app: $name
deploymethod: trident
spec:
replicas: 1
selector:
matchLabels:
app: $name
template:
metadata:
labels:
app: $name
deploymethod: trident
spec:
containers:
– name: $name
image: erjosito/sqlapi:1.0
ports:
– containerPort: 8080
volumeMounts:
– name: disk01
mountPath: /mnt/disk
volumes:
– name: disk01
persistentVolumeClaim:
claimName: azurenetappfiles
—
apiVersion: v1
kind: Service
metadata:
labels:
app: $name
name: $name
spec:
ports:
– port: 8080
protocol: TCP
targetPort: 8080
selector:
app: $name
type: LoadBalancer
EOF
And here the results of the I/O benchmark (not sure about why the read bandwidth is 10x, I might have a bug in the I/O benchmarking code or there is some caching involved somewhere, I will update this post when I find out more):
❯ curl ‘http://40.127.231.103:8080/api/ioperf?size=512&file=%2Fmnt%2Fdisk%2Fiotest’
{
“Filepath”: “/mnt/disk/iotest”,
“Read IOPS”: 201567.0,
“Read bandwidth in MB/s”: 1574.75,
“Read block size (KB)”: 8,
“Read blocks”: 65536,
“Read time (sec)”: 0.33,
“Write IOPS”: 13.0,
“Write bandwidth in MB/s”: 1.62,
“Write block size (KB)”: 128,
“Write time (sec)”: 315.51,
“Written MB”: 512,
“Written blocks”: 4096
}
When you delete the application from OpenShift, including the PVC, the Azure NetApp Files will disappear as well, without anybody having to log to Azure to do anything.
So that concludes this post, with a boring “it works as expected”. Thanks for reading!
by Contributed | May 21, 2021 | Technology
This article is contributed. See the original author and article here.
It’s the week before Microsoft Build and there is a lot of news to share. Items covered this week includes VNet Peering and Azure Bastion now generally available, Windows Admin Center version 2103.2 preview is now available, Internet Explorer 11 retirement announcement, IT tools update to support Windows 10 version 21H1 and a hybrid focused Microsoft Learn Module of the week.
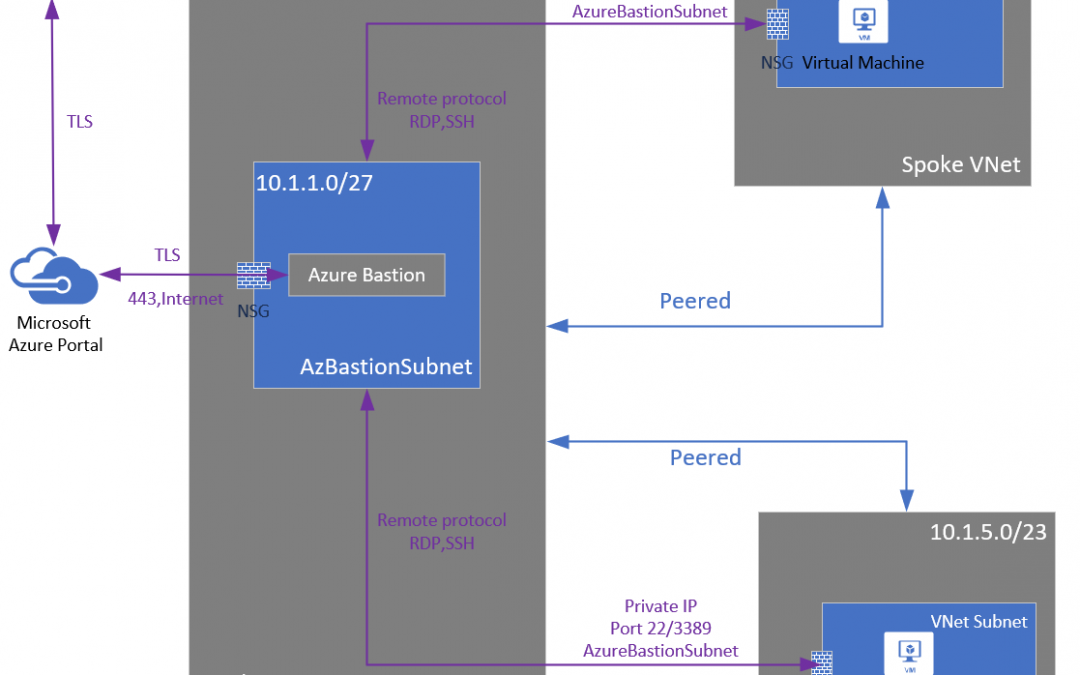
VNET peering support for Azure Bastion reaches general availability
Azure Bastion and VNet peering can now officially be used together. When VNet peering is configured, organizations no longer have to deploy Azure Bastion in each peered VNet. If you have an Azure Bastion host configured in one virtual network (VNet), it can be used to connect to VMs deployed in a peered VNet without deploying an additional Bastion host.
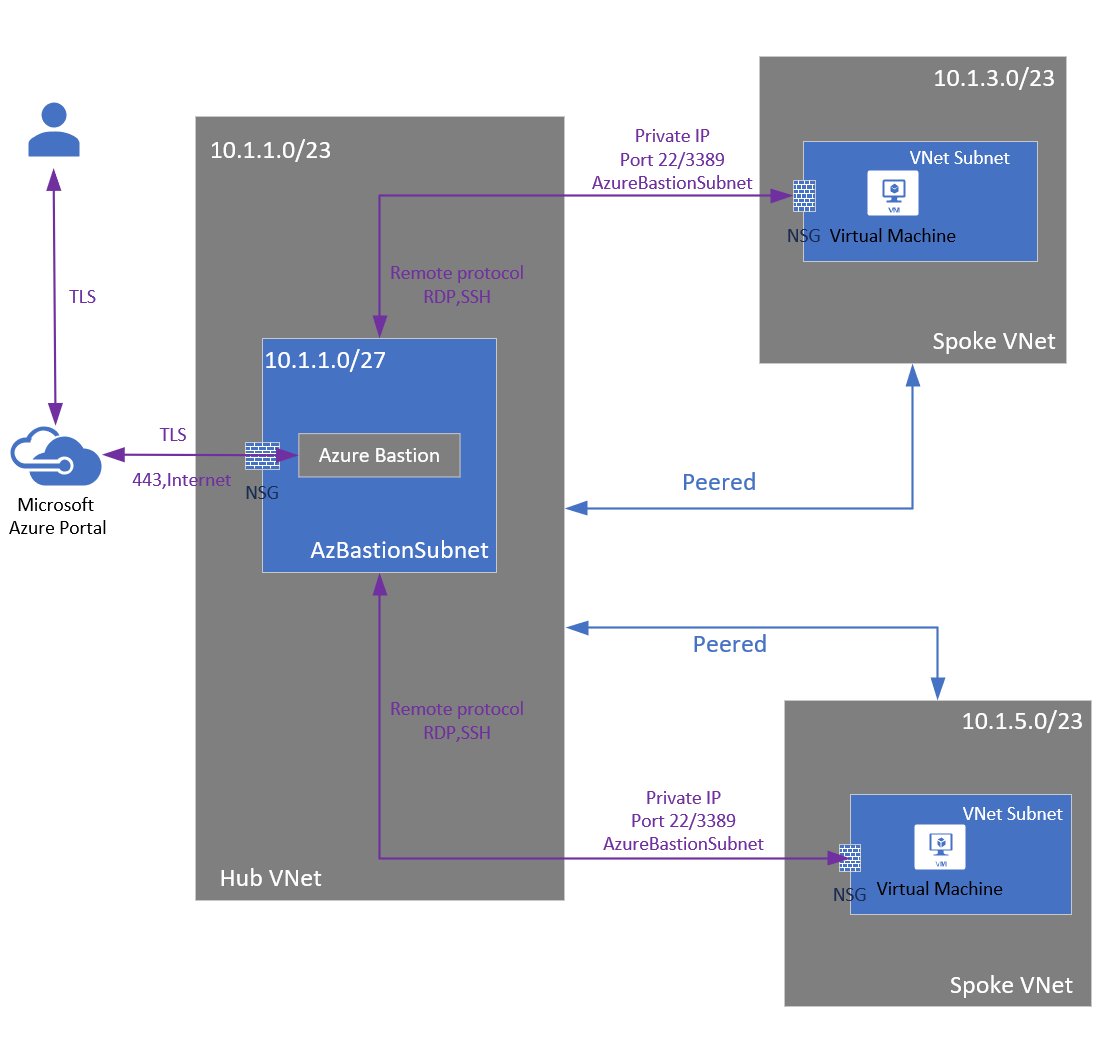
Learn more here: VNet peering and Azure Bastion
Windows Admin Center version 2103.2 is now available in preview
This version of Windows Admin Center includes key bug fixes and feature updates to the Azure sign in process, support for Azure China, as well as additional updates to the Events and Remote Desktop tool experience. Windows Admin Center also continues to value the collaboration efforts Microsoft has with thier partners. Since the 2103 release in March, five of Microsoft’s partners have released new or updated versions of their extensions.
Be sure to also provide your feedback reguarding this latest update of Windows Admin Center. Learn more and download today
Internet Explorer 11 desktop app retirement
Microsoft Edge with IE mode is officially replacing the Internet Explorer 11 desktop application on Windows 10. As a result, the Internet Explorer 11 desktop application will go out of support and be retired on June 15, 2022 for certain versions of Windows 10. This will also include Internet Explorer 11 found on Windows Virtual Desktop being replaced by Microsoft Edge. Here is a quick video on the announcement:
In-market Windows 10 LTSC and Windows Server are out of scope (unaffected) for this change.
Microsoft has also created an FAQ to address any questions you may have which can be found here: Internet Explorer 11 desktop app retirement FAQ
Windows 10, version 21H1 IT tools update
Windows 10, version 21H1 offers a scoped set of improvements in the areas of security, remote access, and quality. Windows 10 version 21H1 will be delivered via an enablement package to devices running version 2004 or version 20H2. Those updating to Windows 10, version 21H1 from Windows 10, version 1909 and earlier, will experiance a similar process to previous updates. Updates to security baseline and admin templates are also now available.
Full details surrounding all IT tool updates can be found here: IT tools to support Windows 10, version 21H1
Community Events
- Microsoft Build – Explore what’s next in tech and the future of hybrid work. Join us May 25-27, 2021 at Microsoft Build.
- Testing in Production – Producer Pierre and Sound Guy Steve are back to share thier livestream learnings
- Hello World – Special guests, content challenges, upcoming events, and daily update
MS Learn Module of the Week

Introduction to Azure hybrid cloud services
This module provides an introductory overview of hybrid cloud technologies and how you can connect an on-premises environment to Azure in a way that works best for your organization.

Modules include:
- Describe the elements of an Azure hybrid cloud deployment.
- Explain methods of connecting on-premises networks to workloads in Azure.
- Understand how to use the same set of identities in hybrid environments.
- List the types of compute workloads for hybrid clouds.
- Explain the application infrastructure of hybrid clouds.
- Describe the services that support files and data in hybrid clouds.
- Explain technologies that support the security of hybrid clouds.
Learn more here: Introduction to Azure hybrid cloud services

Let us know in the comments below if there are any news items you would like to see covered in the next show. Be sure to catch the next AzUpdate episode and join us in the live chat.









Recent Comments