
by Contributed | May 25, 2021 | Technology
This article is contributed. See the original author and article here.
The 19th annual Imagine Cup brought together thousands of students from 163 countries across the globe reimagining tech solutions to impact their communities. With projects submitted in four social good categories – Earth, Education, Healthcare, and Lifestyle – the competition advanced through Online Semifinals and World Finals rounds. As winners of each category, the top four teams were selected to pitch their projects at the World Championship during Microsoft Build for the chance to take home the 2021 trophy.
Congratulations to Team REWEBA from Kenya, who won the grand prize for their IoT-based infant monitoring solution, which remotely analyzes infant parameters during post-natal screening and serves as an early warning intervention system. The team won USD75,000, a mentoring session with Microsoft CEO Satya Nadella, and a USD50,000 Microsoft Azure Grant.
The 2021 World Championship was judged by Jocelyn Jackson, Enhao Li, and Toni Townes-Whitley – innovation and industry experts spanning a variety of technology, diversity, start-up, and social impact backgrounds that align to the core of Imagine Cup’s mission. Hosts Tiernan Madorno, Microsoft Business Program Manager, and Donovan Brown, Microsoft Partner Program Manager, kicked off the show, introducing each of the judges tasked with selecting the World Champion. The top four teams then gave an in-depth presentation on their solutions, which were assessed for their technology, diversity, originality, and innovative design. Watch the show to experience the moment when Team REWEBA is crowned champion!
Meet the 2021 World Champion
 From left to right, team members Dharmik Karania, Jeet Gohil, Khushi Gupta, and Abdihamid Ali
From left to right, team members Dharmik Karania, Jeet Gohil, Khushi Gupta, and Abdihamid Ali
Team REWEBA, Kenya – Healthcare category
After meeting at the United States International University in Kenya, the team started working together on a graduate project aimed at solving a major problem within their community. Members of the team had interned at a local hospital, learning first-hand the challenges that mothers can face traveling long distances for infant screenings. Lack of healthcare access in marginalized communities, compounded by the effects of COVID-19, contributes to a high infant mortality rate. Team member Khushi Gupta says, “Sub-Saharan Africa remains the region with the highest under-5 mortality rate in the world. We can solve this problem using REWEBA, a remote infant monitoring system that can be used in marginalized areas thus giving everyone equal access to healthcare.” They realized how beneficial it could be to apply IoT to create a remote monitoring solution, and their project was born.
REWEBA (Remote Well Baby) is an early warning system that digitally monitors babies’ growth and health parameters and sends them to doctors for timely intervention. It combines Machine Learning, IoT, Analytics, and more to provide innovative functionalities for infant screening, mimicking the process of post-natal screening in a hospital. Team member Jeet Gohil shared that “There’s a lot of technologies that we came to discover {through building our project}, for example Azure DevOps, IoT, and Functions. We learned a lot about how to build IoT systems.”
Kushi Gupta stated the driving factor for the team’s solution was enabling equal access to healthcare services and saving infants from fatal diseases: “Africa has the highest number of {infant mortalities}, highlighting the gap in healthcare services. REWEBA is the only remote healthcare solution that provides regular growth monitoring for infants from the comfort of the home, while also giving direct access to doctors for immediate intervention.”
Looking to the future, Team REWEBA hope to enhance and scale their project to include additional infant screening factors and a postnatal screening device for mothers. The team would like to launch a start-up in Kenya to enable even better access to healthcare services in marginalized areas. When asked how winning the 2021 Imagine Cup will impact their project, the team responded, “The winning prize and the Azure grants will take our project up a notch, and we envision saving millions of babies’ lives all around Kenya. We plan to extend throughout Africa and India as well, as these are the countries where infant mortality is really high.”
 Team REWEBA’s winning moment.
Team REWEBA’s winning moment.
————–
Registration for the 2022 competition is now open. Join over two million student competitors worldwide in making an impact in what you’re most passionate about and sign up for Imagine Cup today!
by Contributed | May 25, 2021 | Technology
This article is contributed. See the original author and article here.
While trying to upload files that are bigger than 64 KB, we came across this error: 413 Request Entity Too Large.
The maximum message size quota for incoming messages (65536) has been exceeded. To increase the quota, use the MaxReceivedMessageSize property on the appropriate binding element.
The maximum message size quota for incoming messages (65536) has been exceeded. To increase the quota, use the MaxReceivedMessageSize property on the appropriate binding element.
As the error above mentions, this issue occurs because the request size is bigger than the MaxReceivedMessageSize for WCF.
Solution
Increase MaxReceivedMessageSize value for your web service to solve this issue. However, this may get tricky because there are two different MaxReceivedMessageSize parameters:
- MaxReceivedMessageSize in System.ServiceModel.Configuration.BasicHttpBindingElement
- MaxReceivedMessageSize in System.ServiceModel.Channels.HttpTransportBindingElement
This configuration below will increase the MaxReceivedMessageSize in System.ServiceModel.Configuration.BasicHttpBindingElement
<basicHttpBinding>
<binding name="basicHttpBinding_Portal" maxReceivedMessageSize="2147483647" maxBufferSize="2147483647" maxBufferPoolSize="2147483647">
<readerQuotas maxBytesPerRead="2147483647" maxArrayLength="2147483647" maxStringContentLength="2147483647" maxDepth="2147483647" maxNameTableCharCount="2147483647"/>
</binding>
</basicHttpBinding>
You should increase the MaxReceivedMessageSize in System.ServiceModel.Channels.HttpTransportBindingElement as well:
<customBinding>
<binding closeTimeout="00:10:00" openTimeout="00:10:00" sendTimeout="00:10:00">
<httpTransport maxReceivedMessageSize="2147483647" maxBufferSize="2147483647" useDefaultWebProxy="true" transferMode="Buffered" />
</binding>
</customBinding>
You can also do it in the code as explained in this document.
by Contributed | May 25, 2021 | Technology
This article is contributed. See the original author and article here.
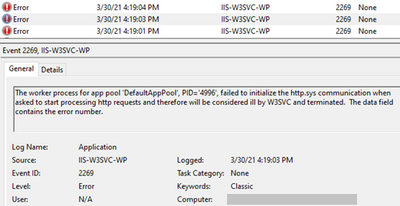
For an issue I worked on, the application pool kept stopping with Event ID 2269, 5139, and 5002. The errors and warnings I saw in Event Viewer are below.
Event 2269
The worker process for app pool 'DefaultAppPool' failed to initialize the http.sys communication when asked to start processing http requests
Event 5139
A listener channel for protocol 'http' in worker process serving application pool 'DefaultAppPool' reported a listener channel failure.
Event 5002
Application pool 'DefaultAppPool' is being automatically disabled due to a series of failures

Solution
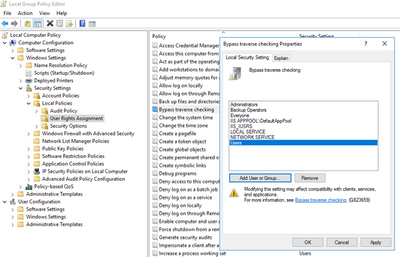
Check if the application pool identity has “Bypass traverse checking” permission. This is group-policy permission to determine which users can traverse folders even if they don’t have permission on folders.
To give “Bypass traverse checking” permission:
- Go to “Start > Run”, type “gpedit.msc”
- Follow “Computer Configuration > Windows Settings > Security Settings > Local Policies > User Rights Assignment”
- Right click “Bypass traverse checking” and click “Properties”
- Click “Add User or Group”. Add these users and groups: Everyone, Users, IIS_IUSRS, IIS AppPoolDefaultAppPool
- Restart the server
- Open the same window and make sure the users/groups you added are still there
- Test the application
If this doesn’t work, use “netstat” and see if there are port conflicts. There might be network and file structure related issues as well
Note: With the steps above, we added more users than we should. This is for testing only. You can later harden this configuration.
by Contributed | May 25, 2021 | Technology
This article is contributed. See the original author and article here.
When you run a penetration test on your web application, the report may point out BREACH as a high-risk vulnerability. BREACH attack works by trying to guess the secret keys in a compressed and encrypted response. Attacker makes many requests and try to figure out the encrypted information byte-by-byte using the pattern in responses.
Here is an example vulnerability test report that mentions the BREACH:
'id' : 'BREACH',
'port' : '443',
'severity' : 'HIGH',
'finding' : 'potentially VULNERABLE, uses gzip HTTP compression - only supplied '/' tested'
Mitigations
Common recommendations:
- Disabling HTTP compression
- Separating secrets from user input
- Randomizing secrets per request
- Masking secrets (effectively randomizing by XORing with a random secret per request)
- Protecting vulnerable pages with CSRF
- Length hiding (by adding a random number of bytes to the responses)
- Rate-limiting the requests
My comments about these mitigations:
- The first option (disabling HTTP compression) will mitigate this vulnerability. However, this may have a performance effect
- Recommendations #2 to #5 are related to the coding of the application. They can help preventing this attack. They are also best practices for development
- Recommendations #6 and #7 are hosting-related. You may need to talk to your hosting company to make these changes
The question is how the scan tool is determining to raise this vulnerability? Is it just checking if the compression is enabled? If that’s the only check it does, then recommended mitigations from #2 to #7 won’t make this vulnerability disappear from the report.
My recommendation would be to keep the compression enabled but implementing the other recommendations (from #2 to #7).
by Contributed | May 25, 2021 | Technology
This article is contributed. See the original author and article here.
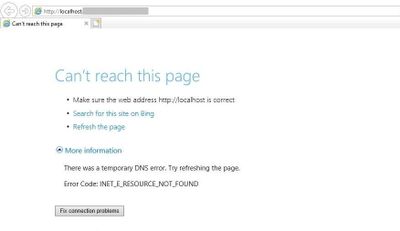
You may come across this error message when you access your website: “Can’t reach this page. There was a temporary DNS error. Error code: INET_E_RESOURCE_NOT_FOUND”

Solution
As the error mentions, there might be a problem with the DNS record of your application. However, for the issue I worked on, the root cause was the corruption in the IE registry setting.
We renamed the Connections container in the registry key below. After a server restart, a new Connections container was created and the application started working.
HKEY_LOCAL_MACHINE > Software > Microsoft > Windows > CurrentVersion > Internet Settings > Connections
My guess is that an Windows update or another system-level change can cause this issue.

 From left to right, team members Dharmik Karania, Jeet Gohil, Khushi Gupta, and Abdihamid Ali
From left to right, team members Dharmik Karania, Jeet Gohil, Khushi Gupta, and Abdihamid Ali Team REWEBA’s winning moment.
Team REWEBA’s winning moment.




Recent Comments