by Contributed | Feb 25, 2021 | Technology
This article is contributed. See the original author and article here.
Hi everyone, we have added a new video tutorial to the Advanced OSD series. This tutorial highlights the ability to bootstrap a task sequence during client installation. This was introduced in ConfigMgr current branch 2002 and refined in ConfigMgr current branch 2006. The video demonstrates how to use this option when the client is installed on-prem, directly on the internet using the CMG, and through Autopilot. While not specifically part of client bootstrapping, the tutorial also demonstrates and discusses the various authentication options the client can use including self-signed certs, PKI certificates, Azure AD token authentication and new in ConfigMgr 2002, the Bulk Registration Token.
The video linked below was prepared by @Steve Rachui, a Principal Customer Engineer focused on manageability technologies.
Posts in Advanced OSD.
Go straight to the Advanced OSD playlist
For an overview of the entire series see OSD with Configuration Manager Video Tutorial Series Overview.
by Contributed | Feb 25, 2021 | Technology
This article is contributed. See the original author and article here.
In this series, Microsoft identity team members share their reasons for loving passwordless authentication (and why you should too!). Today, Tarek Dawoud, principal program manager, continues this series.
Since we announced our Public Preview of passwordless credential management, we have met with hundreds of customers to discuss the passwordless promise and how to get there. If there’s one consistent theme we’ve heard from customers over the past two years, it’s been that going passwordless makes sense. That’s what I love about passwordless. They absolutely believe in the promise, the technology, and the standards backing it. They see that it’s the right investment to truly rely on enterprise security for user accounts and credentials.
The other theme we’ve also heard is that customers need guidance and help on how to plan their passwordless journey. Since passwords have been around since the inception of computing, this is a new undertaking for most customers and with the passwordless journey being closely tied to the cloud journey, many customers are seeking a blueprint or roadmap.
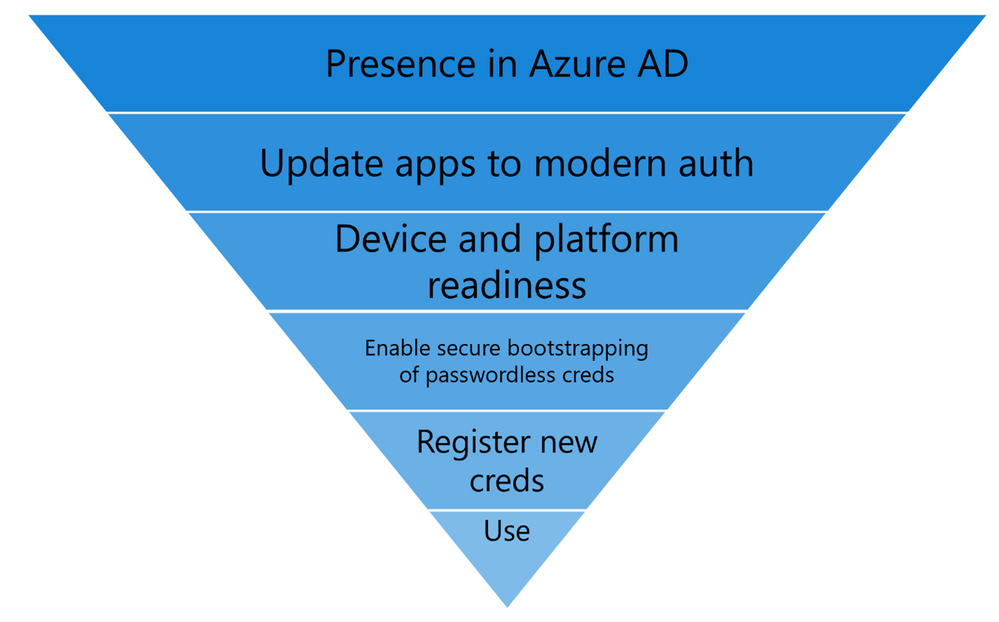
I am here to share more about the journeys that some of our most successful passwordless customers, including Microsoft ourselves, have taken, and what we have learned from them. The first step on the journey is to understand and start planning for the “Passwordless Funnel” as illustrated in the image below:

Passwordless Funnel:
- Presence in Azure AD: Recognize that the cloud is where passwordless innovation is happening, whether it’s WebAuthN or enhancements in token protection, the modern protocols and standards are where the battle can be won. Trying to go passwordless while relying on on-premises legacy technologies that have the password embedded in their fabric is counter-productive. While legacy applications will be around (and the solution should allow them to continue to work), the speed of the cloud is so much more suited for iterating on passwordless than hoping for server products to keep up.
- Moving your Apps to Azure AD: The majority of users day-to-day apps should be modernized apps that do OAuth2.0 or SAML authentication and authorization. This is true for all Microsoft 365 apps, but we also want you to The more apps under Azure AD, the more bang for your passwordless buck. For developers, we now have guidance on how to make sure your apps are passwordless ready.
- Device and platform readiness: This is one area that customers may overlook. To enable Windows Hello for Business with the best feature set for passwordless integration, we recommend Windows 20H1 or higher. Customers will likely need time to get on a current build of Windows. Customers using FIDO2 keys need to also get themselves familiar with the Azure AD FIDO2 Supportability matrix for operating system and browser support. Device readiness also includes what FIDO hardware you may need, and which vendors provide the functionality and features customers may need. This matrix is an ever evolving page as more software and hardware vendors add support for FIDO2, so watch this space.
- Enable secure bootstrapping of Passwordless: A strong credential created with a single weak credential compromises the overall credential. As your users onboard to passwordless credentials (Windows Hello for Business – WHFB, Passwordless Phone Sign in or FIDO2 keys) they must use strong authentication to register these credentials. Today, this means they must be registered for Azure AD MFA following our best practices . Soon, we’ll add a way for employees to register a passwordless credential without needing a traditional MFA method first. To keep up with the newest updates keep following this series.
- Registering the new passwordless credentials: Create campaigns and awareness to enroll targeted user groups into the new credentials. Today, we have over 4 million users actively using WHFB as their primary credential on Azure AD. WHFB, enrollment can be completed on existing devices or simply by acquiring a new device. For FIDO2 and Passwordless Phone Sign in, you can scope rollout campaigns using the guidance in our deployment guide.
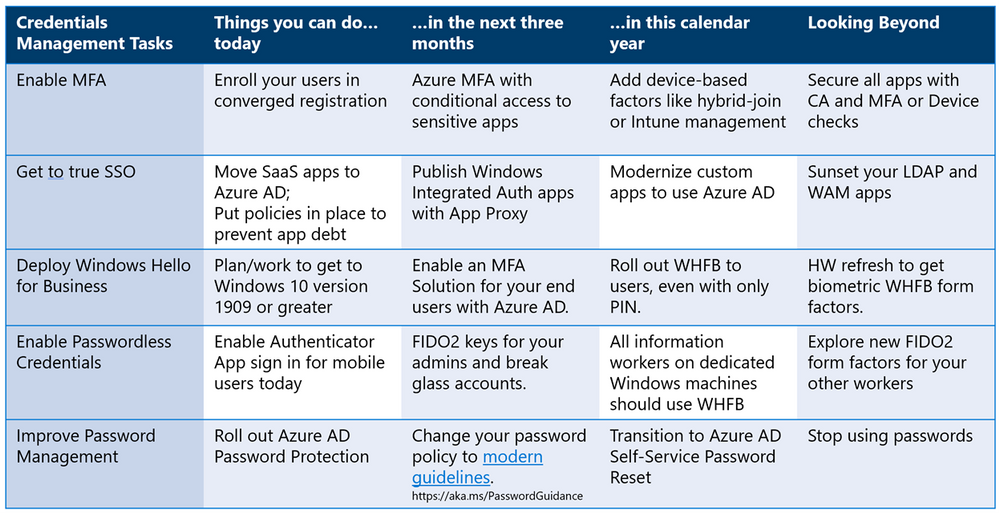
Putting it all together
So, as you start your passwordless journey… What can you do today? What can you start in a month? And what do you have to start working on this year? This journey map (shown below) is built based on our deployment journey at Microsoft as well as hundreds of passwordless deployments with our customers, we hope you will find it valuable.
Check out the other posts in this series:
Learn more about Microsoft identity:
by Contributed | Feb 25, 2021 | Technology
This article is contributed. See the original author and article here.
This blog is part two of a three-part series focused on business email compromise.
In the previous blog in this series, we described the components of a classic (or single stage) BEC attack and showed how Microsoft Defender for Office 365 helps you protect against them. In this post, we will look at how BEC attacks have evolved and how new capabilities in Defender for Office 365 provide additional security layers to keep your organizations safe against these evolving patterns.
Understanding Evolving BEC Attack Patterns
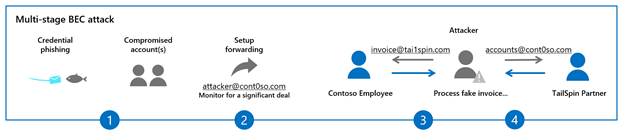
In recent years, we have seen BEC attacks grow more complex and now involve multiple stages. Here is how they work:
- Once the attacker has identified the target organization, they attempt to compromise the email account of the victim through techniques like credential phishing or reusing previously leaked passwords.
- The attacker subsequently sets up a forwarding rule on the victim’s email account. This enables the attacker to conduct reconnaissance on the target and monitor new emails from partners or vendors, typically those that involve a financial exchange.
- Once a transaction of interest is identified, the attacker inserts themselves in the middle of an active email conversation through the tactics we described in our previous blog: using either user or domain impersonation, or a domain spoofing attack. The idea is to dupe the victim into trusting the attacker (who’s posing as the trusted vendor) and taking specific actions. The attacker can carry out multiple parallel conversations posing as one entity to another.
- Finally, the attacker modifies the wire transfer or financial transaction details, leading the victim to process a fake invoice.
 Figure 1: The stages of multi-stage BEC attacks
Figure 1: The stages of multi-stage BEC attacks
In recent months, we have updated Defender for Office 365 in multiple ways to help customers secure themselves against each stage of these evolving attack patterns.
Preventing Credential Phishing & Account Compromise
In the stages we discussed above, the first step is typically account compromise using a tactic like credential phishing. To block credential phishing mails, Defender for Office 365 is constantly updating its multi-layered email filtering stack which includes capabilities such as Safe Links, Safe Attachments and multiple machine learning models that scan and sandbox emails, files, and URLs to detect credential harvesting sites and block them. Additionally, Safe Links provides time-of-click protection for links in emails and is integrated into Office apps like Word, Excel and PowerPoint, to block exposure to malicious sites. Safe Links capabilities are available for both mails that come from outside your organization and internal mails within your organization. Defender for Office 365 is the only solution that can provide internal email protection within the compliance boundary of Office 365. No need to journal mails to external systems or grant mailbox access to external services.
We have also recently updated our machine learning models that detect anomalous account behavior and trigger alerts. You can learn more about how Defender for Office 365 identifies, automatically investigates, and remediates compromised user accounts.
Office 365 customers that leverage Azure Active Directory for identity access management can configure security defaults that enable Multi-Factor Authentication and disable legacy authentication for your Office 365 environment. This eliminates risk of password spray and account compromise in more than 99.9% of cases.
External Email Forwarding in Office 365 Now Disabled by Default
As we move to the next step in the typical multi-stage attack, we must turn our attention to external forwarding. External forwarding allows attackers to establish persistence and learn more about their victims. We have rolled out a new option in the outbound spam policy that disables external forwarding by default. Additionally, to help our customers get to a secure posture, this policy has been retroactively applied to existing Office 365 mailboxes. This has helped disrupt any existing compromised accounts and BEC activities.
For legitimate scenarios that require email forwarding, administrators can create custom policies and enable forwarding for select mailboxes, while keeping it disabled for the rest of their users. You can learn more about controlling external forwarding in Defender for Office 365 here.
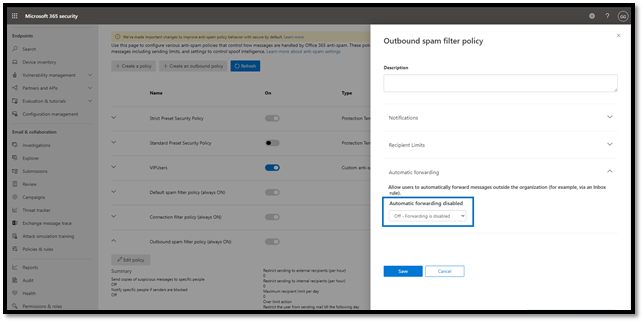 Figure 2: Configure automatic forwarding in the outbound spam policy
Figure 2: Configure automatic forwarding in the outbound spam policy
New and Improved Suspicious Forwarding Alerts
In addition to disabling external forwarding by default, Defender for Office 365 has introduced a new alert that detects suspicious forwarding related activity. The alert can warn administrators when suspicious forwarding activity is detected and enables them to conduct further investigation, remediate the account, and prevent any suspicious wire transfer activities.
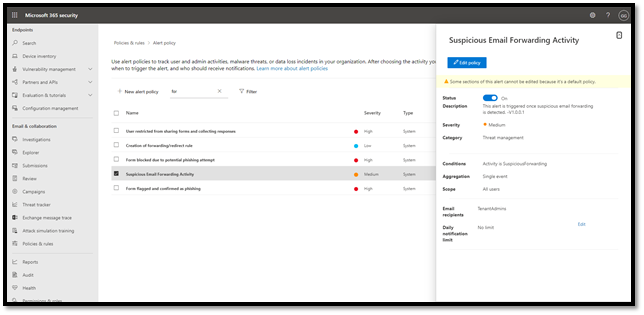 Figure 3: Suspicious email forwarding activity alerts
Figure 3: Suspicious email forwarding activity alerts
Tools to Improve User Awareness
Employees are an organization’s greatest asset, but they are also susceptible to falling prey to these evolving attacks. An important way to strengthen your defenses against all cyber threats is through user awareness.
For awareness programs to be successful, they must offer intuitive learning moments for your employees. What differentiates Microsoft from all other email security vendors is our ability to natively integrate security features into the products like Outlook and Office 365 apps. This integration provides both protection and awareness for your users.
New Safety Tips Options
Defender for Office 365 already provides various safety tips that are shown to end users of an email to enhance user awareness. We recently launched a new safety tip that enables email users to self-detect suspicious emails based on a signal related to first time contact between a sender and recipient(s).
If you receive an email from a sender for the first time or do not often get emails from this sender, you will see a safety tip displayed in your Outlook client as shown below to warn you that this email might be suspicious.
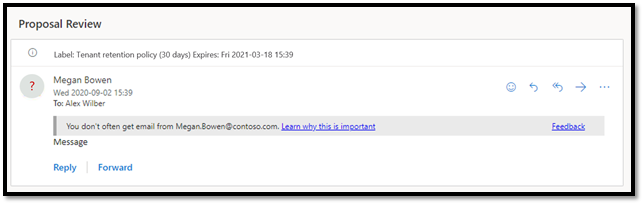 Figure 4: First contact safety tip warns users of suspicious email
Figure 4: First contact safety tip warns users of suspicious email
Imagine being in the middle of an email chain with your business partner or vendor and receiving this warning message. That is a strong indicator of a potential business email compromise attempt. This capability adds an extra layer of security protection and creates awareness for users against such attacks.
You can learn more about configuring first contact safety tips in your Office 365 tenant.
Native Link Rendering
Phishing trainings usually educate users to verify links in email apps by hovering over these links to reveal their destination. Many email security products rewrite these URLs, making it difficult for users to decipher the destination URL and reducing the value of the training. Safe Links in Defender for Office 365 goes beyond rewriting URLs and natively integrates with Outlook and Office 365 apps. Native link rendering allows users to see the destination URL when they hover over the link, but still protects them from malicious links by evaluating these links at time-of-click. This capability is unique to Defender for Office 365, and its native integrations with Office apps preserve your investments in phishing and user awareness training.
Attack Simulation & Training
It’s critical that your end users are trained to spot suspicious messages and the indicators we’ve discussed so far, and the most effective way to train your users is to emulate real threats with intelligent simulations. In January we announced the general availability of Attack simulation training in Microsoft Defender for Office 365. Rebuilt from the ground up, Attack simulation training enables customers to train their employees to recognize red flags that might indicate a business email compromise attack. Industry-leading training from Terranova Security caters to diverse learning styles, engaging employees in defending the organization. You can learn more about these new capabilities here.
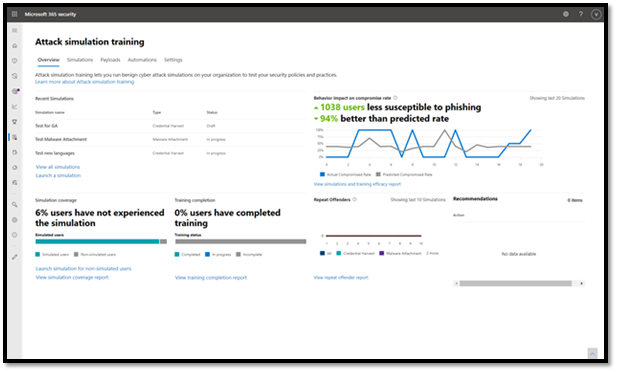 Figure 5: Attack simulation training engages employees in defending the organization
Figure 5: Attack simulation training engages employees in defending the organization
Coming up in Part 3….
In this blog we covered several ways that Microsoft Defender for Office 365 has been updated to help prevent evolving business email compromise attacks. We encourage readers to review these new capabilities and enable them in their environments.
In the next post in this series, we will look at the impact of these protections and the work we are doing outside the product in partnership with other security teams at Microsoft to further secure our customers. We’ll wrap up the series with best practice recommendations to ensure your organization stays protected against business email compromise attacks. Stay tuned!

by Contributed | Feb 25, 2021 | Technology
This article is contributed. See the original author and article here.
Now let’s imagine this. You have the developer tenant from your Microsoft 365 Developer Subscription, and you enrolled the Power Apps Community Plan with it, so you have the full range of possibilities on your dev tenant, right?
Not quite.
Yes, you have access to Dataverse now and yes, you can even use premium connectors and that’s cool. But you can go one step further.

The Power Apps Community Plan gives you a Development Environment and you can add even more Trial Environments on your dev tenant. But you can’t set up new Production Environments.
What are Production Environments and why do you want one?
Production Environments are used for your daily business with production data. If your organization is spread over multiple countries or even continents, it makes sense to give every country its own production environment. Production Environments are backed up frequently to protect your data.
But on your dev tenant you don’t need one, right? Because you’re just testing out and learning things, correct? Well yes, but what if you want to learn how to set up a staging environment for your organization, where you have the recommended environments?
- Development
- Testing
- Production
And imagine you want to learn how to set up the correct security roles in Azure to test things out. You can’t do that on your regular dev tenant, because you are not allowed to set up more environments (especially Production Environments).
Many users are simply not allowed to get full control in the organizations they’re working for, because of security and compliance reasons.
So, what to do?
Wouldn’t it be cool, if you could get a Power Apps Standalone license for your dev tenant? Sure, that costs money but you would have it all:
- A Microsoft 365 E5 license
- Multiple environments to plan out real-life scenarios for your organization
- Dummy users, mailboxes and SharePoint sites to test your flows and apps
- Premium connectors
- Access to Dataverse
And guess what? You can actually purchase a Power Apps standalone license for your dev tenant! You are capable to build a complete safe tenant to test, learn and grow for your organization with just the cost of the Power Apps license.
Here is how you do it
Log into your dev tenant and go to the Admin center. Click on the waffle menu in the upper left corner and click on Admin.

Next, click on Purchase services.
In the category Business apps you find all the Power Platform plans. In this example I highlighted the Power Apps per user plan, but you can also go for the Power Automate per user plan (it’s way cheaper and you have very similar possibilities. Remember, you just want to create different environments and you can do that with both plans. Then click on Details to see, what’s included.
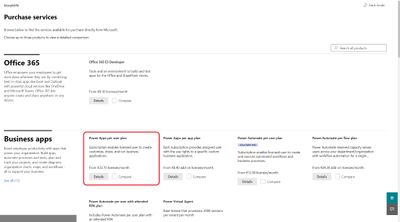
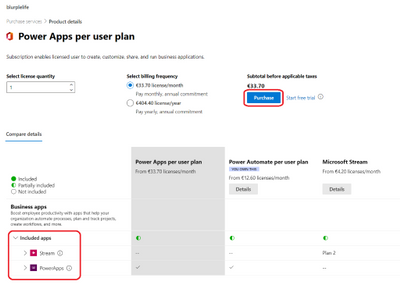
In the next screen you can check all the details. Click on Included apps to see every detail. If you’re happy with it click on Purchase.
Now Now
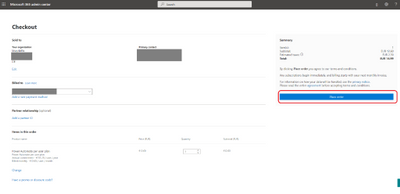
Now you’re almost done. You already are at the Checkout. Fill in your postal address and your billing information. After that click on Place order.
After a few minutes you will get your confirmation mail.
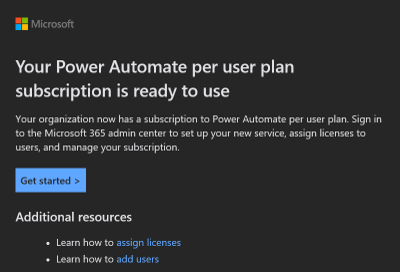
If you click on Get started you will be transferred to the Your products section of the Admin center. Click on Assign licenses.
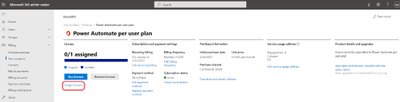
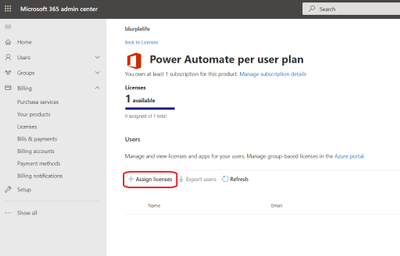
For whatever reasons, you have to click on Assign licenses once again.
After that you can type in a name and click on the chevron icon next to Turn apps and services on or off. Check all the apps and services you want to assign, then finish the process by clicking on Assign again, on the bottom of the page.
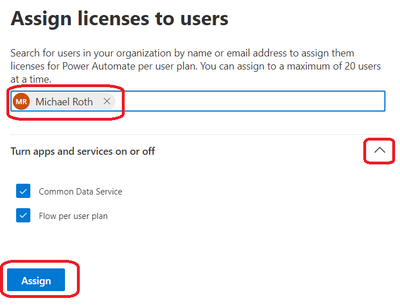
BOOM, there you go.
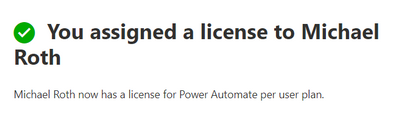
As described in my previous post How to enhance your “dev tenant” to unleash the full potential of the Power Platform, you can now add multiple environments and yes, even Production Environments. Check out the Microsoft documentation about environments to get more details and why and how to use them. Enjoy.


Recent Comments