by Contributed | Feb 17, 2021 | Technology
This article is contributed. See the original author and article here.
THIS POST NEEDS TO BE BACKDATED TO 2/12/18
Decentralized digital identities and blockchain: The future as we see it – Microsoft 365 Blog
Howdy folks,
I hope you’ll find today’s post as interesting as I do. It’s a bit of brain candy and outlines an exciting vision for the future of digital identities.
Over the last 12 months we’ve invested in incubating a set of ideas for using Blockchain (and other distributed ledger technologies) to create new types of digital identities, identities designed from the ground up to enhance personal privacy, security and control. We’re pretty excited by what we’ve learned and by the new partnerships we’ve formed in the process. Today we’re taking the opportunity to share our thinking and direction with you. This blog is part of a series and follows on Peggy Johnson’s blog post announcing that Microsoft has joined the ID2020 initiative. If you haven’t already Peggy’s post, I would recommend reading it first.
I’ve asked Ankur Patel, the PM on my team leading these incubations to kick our discussion on Decentralized Digital Identities off for us. His post focuses on sharing some of the core things we’ve learned and some of the resulting principles we’re using to drive our investments in this area going forward.
And as always, we’d love to hear your thoughts and feedback.
Best Regards,
Alex Simons (Twitter: @Alex_A_Simons)
Director of Program Management
Microsoft Identity Division
—————————————————
Greetings everyone, I’m Ankur Patel from Microsoft’s Identity Division. It is an awesome privilege to have this opportunity to share some of our learnings and future directions based on our efforts to incubate Blockchain/distributed ledger based Decentralized Identities.
What we see
As many of you experience every day, the world is undergoing a global digital transformation where digital and physical reality are blurring into a single integrated modern way of living. This new world needs a new model for digital identity, one that enhances individual privacy and security across the physical and digital world.
Microsoft’s cloud identity systems already empower thousands of developers, organizations and billions of people to work, play, and achieve more. And yet there is so much more we can do to empower everyone. We aspire to a world where the billions of people living today with no reliable ID can finally realize the dreams we all share like educating our children, improving our quality of life, or starting a business.
To achieve this vision, we believe it is essential for individuals to own and control all elements of their digital identity. Rather than grant broad consent to countless apps and services, and have their identity data spread across numerous providers, individuals need a secure encrypted digital hub where they can store their identity data and easily control access to it.
Each of us needs a digital identity we own, one which securely and privately stores all elements of our digital identity. This self-owned identity must be easy to use and give us complete control over how our identity data is accessed and used.
We know that enabling this kind of self-sovereign digital identity is bigger than any one company or organization. We’re committed to working closely with our customers, partners and the community to unlock the next generation of digital identity-based experiences and we’re excited to partner with so many people in the industry who are making incredible contributions to this space.
What we’ve learned
To that end today we are sharing our best thinking based on what we’ve learned from our decentralized identity incubation, an effort which is aimed at enabling richer experiences, enhancing trust, and reducing friction, while empowering every person to own and control their Digital Identity.
- Own and control your Identity. Today, users grant broad consent to countless apps and services for collection, use and retention beyond their control. With data breaches and identity theft becoming more sophisticated and frequent, users need a way to take ownership of their identity. After examining decentralized storage systems, consensus protocols, blockchains, and a variety of emerging standards we believe blockchain technology and protocols are well suited for enabling Decentralized IDs (DID).
- Privacy by design, built in from the ground up.
Today, apps, services, and organizations deliver convenient, predictable, tailored experiences that depend on control of identity-bound data. We need a secure encrypted digital hub (ID Hubs) that can interact with user’s data while honoring user privacy and control.
- Trust is earned by individuals, built by the community.
Traditional identity systems are mostly geared toward authentication and access management. A self-owned identity system adds a focus on authenticity and how community can establish trust. In a decentralized system trust is based on attestations: claims that other entities endorse – which helps prove facets of one’s identity.
- Apps and services built with the user at the center.
Some of the most engaging apps and services today are ones that offer experiences personalized for their users by gaining access to their user’s Personally Identifiable Information (PII). DIDs and ID Hubs can enable developers to gain access to a more precise set of attestations while reducing legal and compliance risks by processing such information, instead of controlling it on behalf of the user.
- Open, interoperable foundation.
To create a robust decentralized identity ecosystem that is accessible to all, it must be built on standard, open source technologies, protocols, and reference implementations. For the past year we have been participating in the Decentralized Identity Foundation (DIF) with individuals and organizations who are similarly motivated to take on this challenge. We are collaboratively developing the following key components:
- Decentralized Identifiers (DIDs) – a W3C spec that defines a common document format for describing the state of a Decentralized Identifier
- Identity Hubs – an encrypted identity datastore that features message/intent relay, attestation handling, and identity-specific compute endpoints.
- Universal DID Resolver – a server that resolves DIDs across blockchains
- Verifiable Credentials – a W3C spec that defines a document format for encoding DID-based attestations.
- Ready for world scale:
To support a vast world of users, organizations, and devices, the underlying technology must be capable of scale and performance on par with traditional systems. Some public blockchains (Bitcoin [BTC], Ethereum, Litecoin, to name a select few) provide a solid foundation for rooting DIDs, recording DPKI operations, and anchoring attestations. While some blockchain communities have increased on-chain transaction capacity (e.g. blocksize increases), this approach generally degrades the decentralized state of the network and cannot reach the millions of transactions per second the system would generate at world-scale. To overcome these technical barriers, we are collaborating on decentralized Layer 2 protocols that run atop these public blockchains to achieve global scale, while preserving the attributes of a world class DID system.
- Accessible to everyone:
The blockchain ecosystem today is still mostly early adopters who are willing to spend time, effort, and energy managing keys and securing devices. This is not something we can expect mainstream people to deal with. We need to make key management challenges, such as recovery, rotation, and secure access, intuitive and fool-proof.
Our next steps
New systems and big ideas, often make sense on a whiteboard. All the lines connect, and assumptions seem solid. However, product and engineering teams learn the most by shipping.
Today, the Microsoft Authenticator app is already used by millions of people to prove their identity every day. As a next step we will experiment with Decentralized Identities by adding support for them into to Microsoft Authenticator. With consent, Microsoft Authenticator will be able to act as your User Agent to manage identity data and cryptographic keys. In this design, only the ID is rooted on chain. Identity data is stored in an off-chain ID Hub (that Microsoft can’t see) encrypted using these cryptographic keys.
Once we have added this capability, apps and services will be able to interact with user’s data using a common messaging conduit by requesting granular consent. Initially we will support a select group of DID implementations across blockchains and we will likely add more in the future.
Looking ahead
We are humbled and excited to take on such a massive challenge, but also know it can’t be accomplished alone. We are counting on the support and input of our alliance partners, members of the Decentralized Identity Foundation, and the diverse Microsoft ecosystem of designers, policy makers, business partners, hardware and software builders. Most importantly we will need you, our customers to provide feedback as we start testing these first set of scenarios.
This is our first post about our work on Decentralized Identity. In upcoming posts we will share information about our proofs of concept as well as technical details for key areas outlined above.
We look forward to you joining us on this venture!
Key resources:
Regards,
Ankur Patel (@_AnkurPatel)
Principal Program Manager
Microsoft Identity Division
by Contributed | Feb 17, 2021 | Technology
This article is contributed. See the original author and article here.
This blog post covers a new feature of the Azure Sentinel entity pages: four new UEBA-related insights to the insights panel.
When you encounter any entity (currently limited to users and hosts) in a search, an alert, or an investigation, you can select the entity and be taken to an entity page, a datasheet full of useful information about that entity. The types of information you will find on this page include basic facts about the entity, a timeline of notable events related to this entity, and insights into the entity’s behavior.
Entity pages consist of three parts:
- Entity info – located in the left-side panel, contains the entity’s identifying information, collected from data sources like Azure Active Directory, Azure Monitor, Azure Security Center, and Microsoft Defender.
- Activity timeline – The center panel shows a graphical and textual timeline of notable events related to the entity, such as alerts, bookmarks, and activities.
- Insights – The right-side panel presents behavioral insights on the entity. These insights help to identify anomalies and security threats quickly.
We’ve added four UEBA-related insights to the insights panel that this post will describe.
Spoiler (Highlight to read)
* To benefit from these insights, UEBA must be enabled and a timeframe of at least 4 days.
* To benefit from these insights, UEBA must be enabled and a timeframe of at least 4 days.
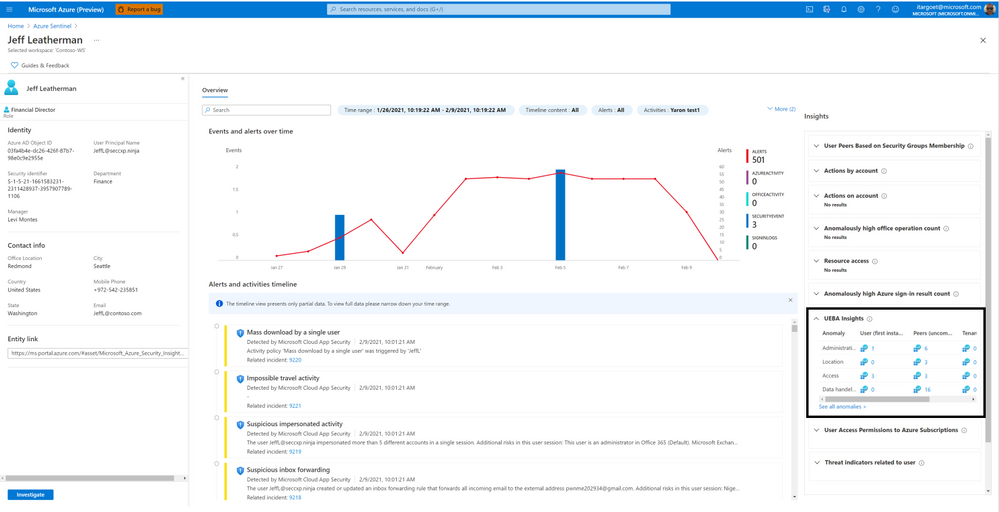
UEBA Insights
This insights section summarizes anomalous user activities – across geographical locations, devices, and environments; across time and frequency horizons (compared to user’s own history); compared to peers’ behavior, and compared to organization’s behavior.
Clicking on “See all anomalies” will present you with the specific anomalies associated with the user and the evidence.
 UEBA Insights
UEBA Insights
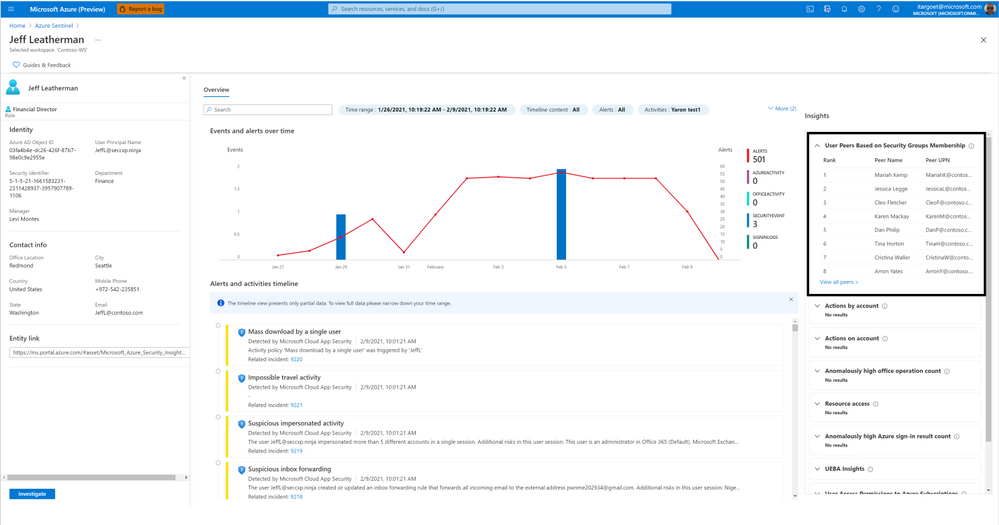
User Peers Based on Security Group Membership
This insight presents the user’s peers based on Azure AD Security Groups membership. This provides the SecOps analysts with visibility to other users who share similar permissions as the user.
 User Peers Based on Security Group Membership
User Peers Based on Security Group Membership
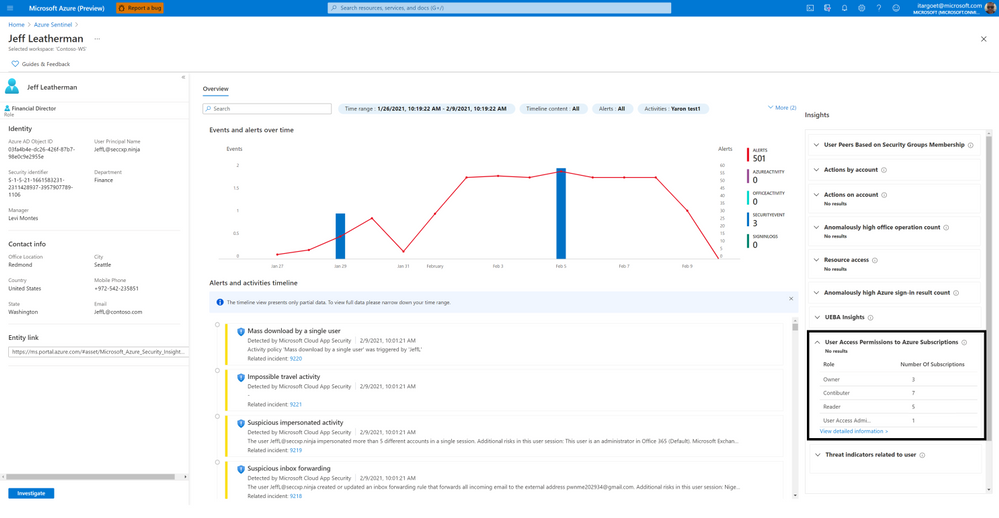
User Access Permissions to Azure Subscription
This insight shows a user’s access permissions to the Azure subscriptions that it can access directly or transitively (via Azure AD groups or service principals). Clicking on “View detailed information” will present the Azure subscriptions’ names and the access method (directly or via which group/service principal).
 User Access Permissions to Azure Subscription
User Access Permissions to Azure Subscription
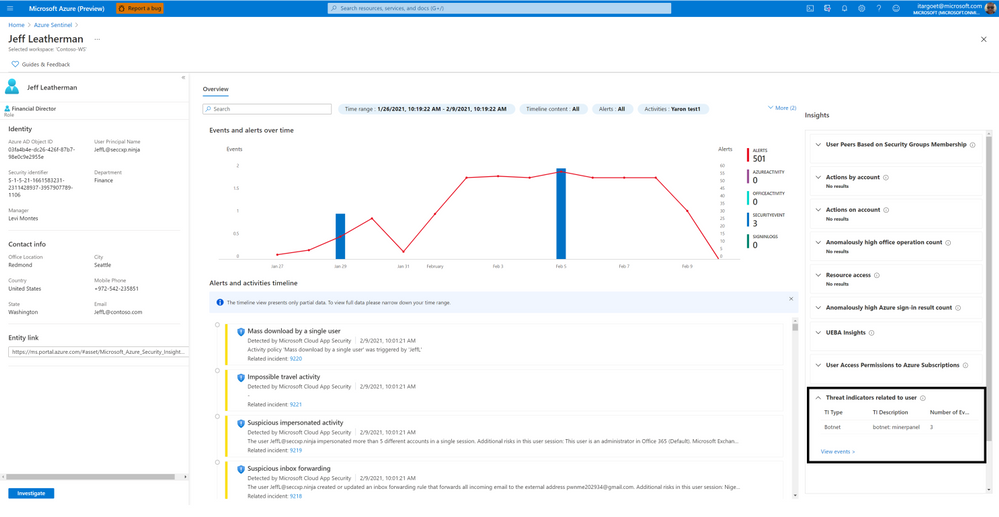
Threat Indicators Related to The User
This insight shows the collection of known threats by threat type and family and enriched by Microsoft’s threat intelligence service, relating to IP addresses represented in the user’s activities.
 Threat indicators related to the user
Threat indicators related to the user
Going Forward
Try out the new insights provided by Sentinel UEBA and let us know your feedback using any of the channels listed in the Resources. We’re working on surfacing more interesting insights that will help you investigate entities faster. 
Many thanks to Payal Rani & Rajvardhan Oak for contributing to the insights work

by Contributed | Feb 17, 2021 | Technology
This article is contributed. See the original author and article here.

In this blog post I want to explain how you can send an Adaptive Card with CLI Microsoft 365. I will guide you from zero to hero :rocket:, so even if you don’t know anything about the CLI Microsoft 365 or about Adaptive cards, don’t stop reading, you will be able to do that in a few minutes- I promise!
What is CLI Microsoft 365?
Lets first get us all on the same page and clarify, what CLI Microsoft 365 is and why we should use it: It is a CLI (Command Line Interface) which let’s us manage Microsoft 365 from any kind of OS: It doesn’t matter if we work on Windows, MacOS or Linux. Previously, some configurations were only possible by PowerShell for Windows, which limited a lot of admins. But even if you work on Windows and are pretty fine with using PowerShell, CLI might be a nice alternative to try out.
How to use CLI Microsoft 365
I will now describe your first steps:
Install Node.js
To use the CLI Microsoft 365, you will need to install Node.js – Please follow these steps:
* go to https://nodejs.org/en/
* download the LTS version of Node.js
* install Node.js
If in doubt, if you have the correct version installed or if you need to use different versions of Node.js, please read Use Node Version Manager to develop your SPFx apps by Toni Pohl
Install CLI Microsoft 365
Now that you have Node.js installed, we can continue with installing the CLI Microsoft 365. You can choose any shell you like: If you want to, you can use PowerShell or PowerShell in the Terminal in Visual Studio Code or whatever makes you happy. I like to use the PowerShell terminal in Visual Studio Code, because links render to be clickable and this saves me copy/pasting links into a new browser tab. But if you like to any other shell, that is perfectly fine as well. To install CLI Microsoft 365, run the command:
npm i -g @pnp/cli-microsoft365
In case you wonder:
* the `i` is an alias for `install`
* the `-g` means that we want to install this package globally
* it will take about 2 minutes
Login
Now that we installed CLI Microsoft 365, it’s time to actually do something here. But before we can get or post anything, we will need to log into our tenant. Pro Tip: You can use your your Developer tenant for this. If you don’t know, what this is, please go read What is a “Dev Tenant” and why would you want one? by Julie Turner
Run the following command:
m365 login
In response you will be asked to open a web browser and login with a code. If you are using Visual Studio Code, you can click on the link, please copy the code upfront.

After you pasted the code,
* click Next
* pick an account out of the list of accounts
You will be seeing this message and can close this browser tab- we won’t need it anymore.
Yay! You successfully logged in! You don’t believe that? Let’s check with CLI Microsoft 365 and run this command to get your status:
m365 status
and it will get your status for you:

If you want some inspiration, what you could do now, run this command:
m365 help
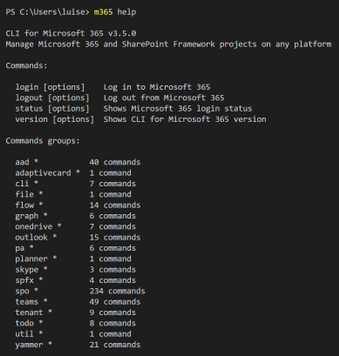
which gives you a list of things you can try, these are called command groups, as each of them can contain several commands. When you now choose one of the command groups and run for example this one:
m365 outlook
you will get the commands, that are available to you in this command group. Sometimes, you can go several levels deep-Just try them out!
What are Adaptive Cards?
Next thing we need to know is, what are Adaptive Cards and why would we want to use them? When we look at adaptivecards.io we can read the definition Adaptive Cards are platform-agnostic snippets of UI, authored in JSON, that apps and services can openly exchange. When delivered to a specific app, the JSON is transformed into native UI that automatically adapts to its surroundings. It helps design and integrate light-weight UI for all major platforms and frameworks. This means, that we get a nice method to share and display information without needing to know how to use HTML/CSS to render them correctly in different host applications. If you like to know more, please read Get started with Adaptive Cards by Tomasz Poszytek
How do we send an Adaptive Card with CLI Microsoft 365?
Now that we know what is an Adaptive Card, let’s have a look on how we get this sent by CLI. The documentation provides us with a sample and this sample needs to have a URL. Where do we get this from? This depends on where you want to send this Adaptive Card to. In this example, I want to use Microsoft Teams as host application and therefore we will need to create an incoming webhook in Teams.
Create the Webhook
If you have no clue what is a webhook, no problem, Rabia Williams got you covered with How to configure and use Incoming Webhooks in Microsoft Teams
* Open Microsoft Teams
* Click the ellipsis icon on the Teams channel that you want to send the Adaptive Card to
* Click Connectors
* Search for ‘webhook’

* Click Add
* Click Add (yes, yet again)
* Give your webhook a name
* If you like to, you can upload a picture- messages sent via this webhook (our Adaptive Card) will have this image then as Profile Pic – this step is optional.
* Click Create
* Copy the generated URL
* Click Done
This URL is the URL we will need in the command later – If you want to, paste it into a notepad or similar.
Author your Card
Now it’s time to author your card. You can do this in a lot of editors, I use either the Adaptive Cards Designer or the Adaptive Cards Viewer Extension in Visual Studio Code, but recently also found Adaptive Card Studio. You can also use one of the provided samples and use them as-is or adjust them to your needs.
If you feel like authoring your Card in Designer or Visual Studio Code is fine for you right now, go ahead with this, otherwise you can also use the examples that are provided in the documentation of CLI Microsoft 365. I used the last one, ‘Send custom card with card data’.
For everyone not very familiar writing and understanding code: We can make more sense of the snippet by copy/paste this into Visual Studio Code, and then press Alt+z to soft-wrap this and then separate the Adaptive Card from the rest:
* Select JSON in Language Mode
* Insert somenew lines right before the first `{`
* Delete the `’` at the beginning and the end of the snippet
* Format with Shift + Alt + f
Now go ahead and adjust the sample to work in your environment:
* replace the URL in the code with the URL that we copied when we added the webhook connector to Teams
* copy the whole code
* run it
!! Turned out, that there are some differences how to use quotes `’` or `”` – please consider which shell you are using before you copy/paste the code from CLI Microsoft 365 documentation.
Congratulations :rocket:- you sent your first adaptive Card with CLI.
## Feedback and what’s next?
I hope you liked this little post on how to get started with CLI Microsoft 365 and learning how to send an Adaptive Card with it. I would like to learn, for which use cases you would do this? Please comment below!
by Contributed | Feb 17, 2021 | Technology
This article is contributed. See the original author and article here.
Gauge the performance of your team and detections using our new out-of-the-box workbooks
Building a Security Operations Center (SOC) from scratch or revamping one is a daunting challenge. We have developed a “Toolkit” to help SOC managers and analysts improve performance. The toolkit is a powerful set of 3 workbooks, all customizable and easily accessible, that help you gauge the most fundamental metrics. With these workbooks, you can measure analysts’ efficiency, detection coverage, alert performance, and more.
We have enhanced the workbooks to provide cross-workspace support allowing for an effective single pane of glass view even in multi-workspace use cases. Each workbook gauges specific performance metrics.
The three workbooks are;
- Detection efficiency
- SOC efficiency
- Incident overview
Detection efficiency
The modern SOC handles multiple data sources and needs to detect threats and provide insights to the analyst. Since SOC resources are limited, a delicate balance must be struck between maximizing the detection of threats and minimizing the occurrence of false positives.
In the detection efficiency workbook, we try to provide different perspectives on detections.
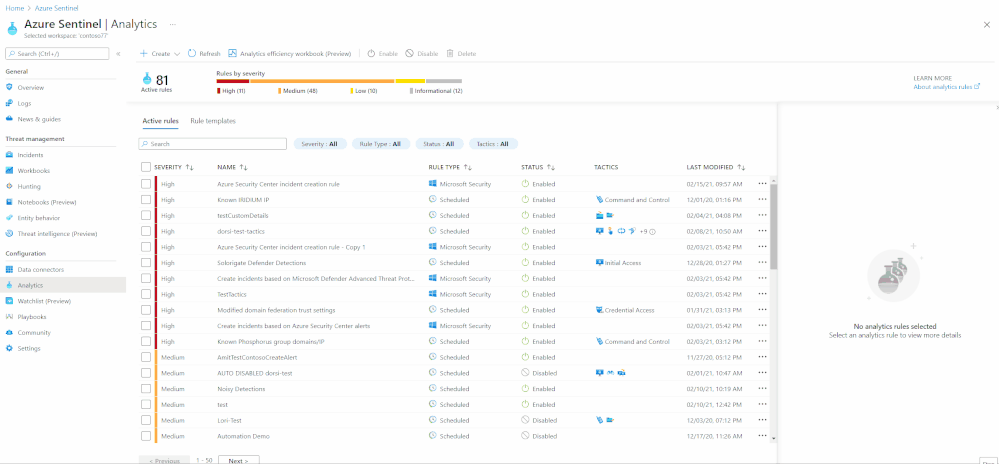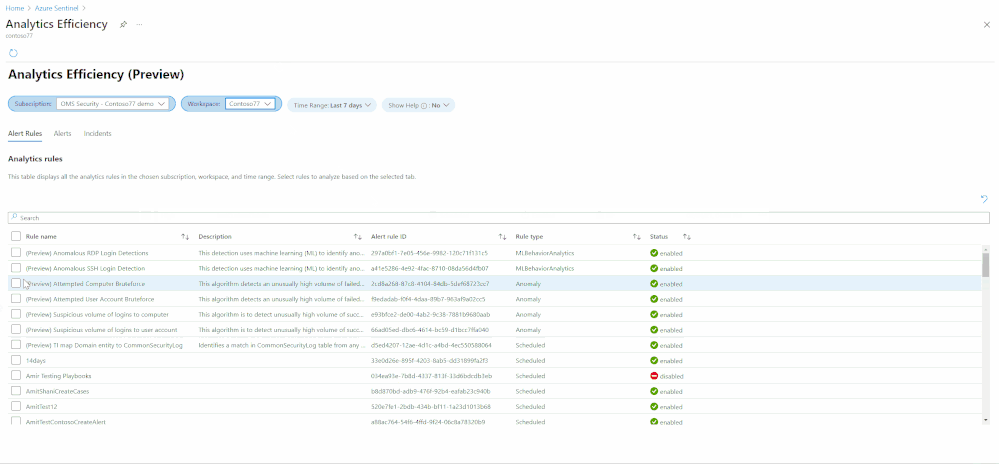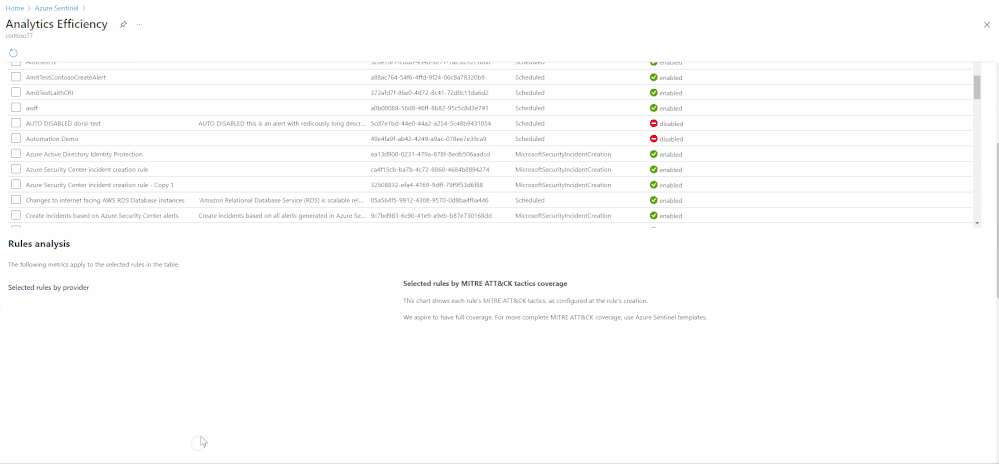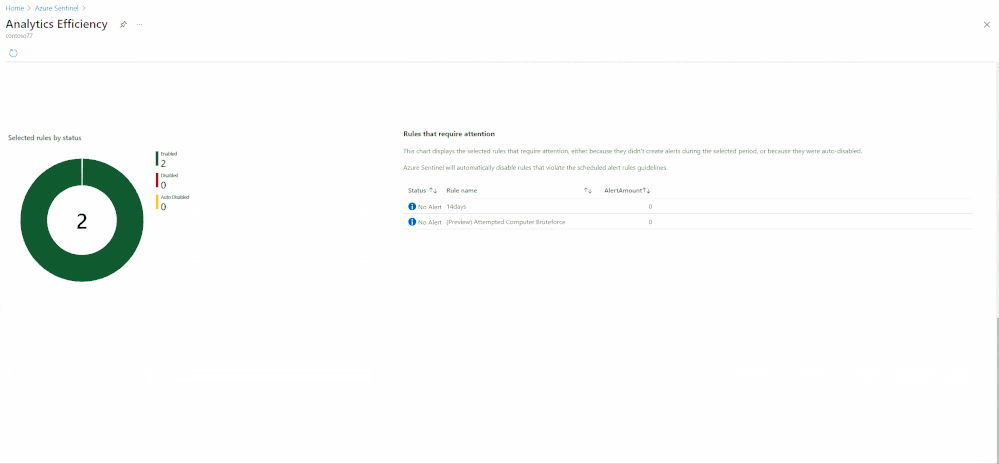
- Alert rules – a holistic view of our detections provides us with insights into the detections’ overall coverage. In this section, we can see our MITRE ATT&CK framework coverage, overall rules status, rules that require attention, and a view of the detections suite.
- Alerts – in this view, we will look at the alerts created from our detections. Since not all rules will create incidents, we can monitor the noisiness of the detections and see which ones require tuning. In the alerts insights section, we provide insights into detections that are not firing and might require attention and track the load from different providers.
- Incidents – The load on the SOC is determined by the number of incidents we create. Here we can monitor which detections created incidents and the reasons incidents are closed. When looking at the incident load and the closing reason, we can deduce which detections require attention and tuning.
Iterating on all 3 views in a repetitive process will improve our detection efficiency, SOC performance, and, ideally, the organization’s detection suite. This continuous process should adapt our detections to the ever-changing security threat landscape.

There are two ways to access this workbook –
- The workbooks gallery – You can find this new workbook template by choosing Workbooks from the Azure Sentinel navigation menu and selecting the Templates tab. Choose Detection efficiency from the gallery and click one of the View saved workbook and View template buttons.
- The Analytics pane – You can find the new workbook in the Alert rules action panel at the top of the pane. If a saved workbook were created from the workbook template, the button would lead to the saved workbook. If not, it will lead to the workbook template. More details can be found in the documentation.
SOC efficiency
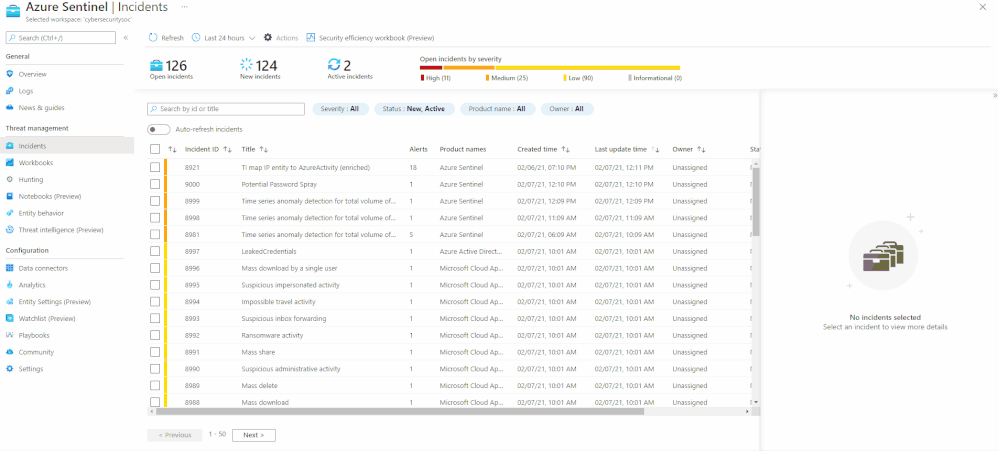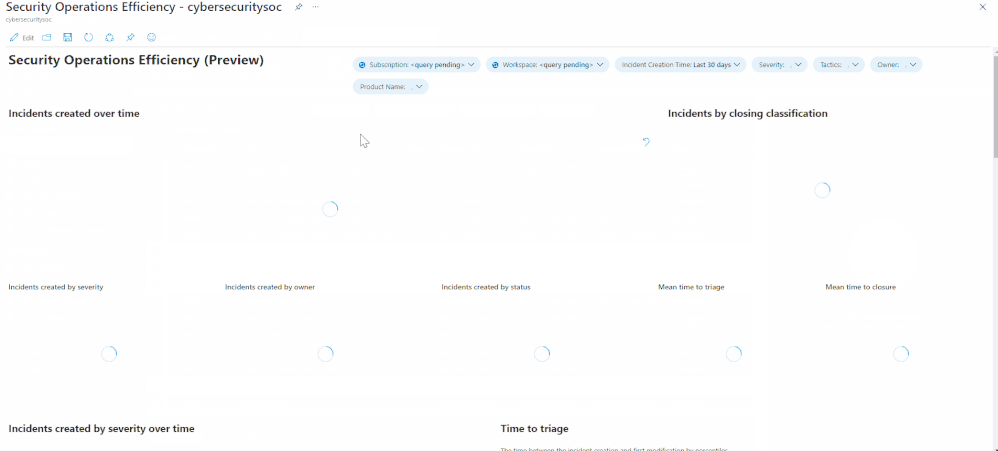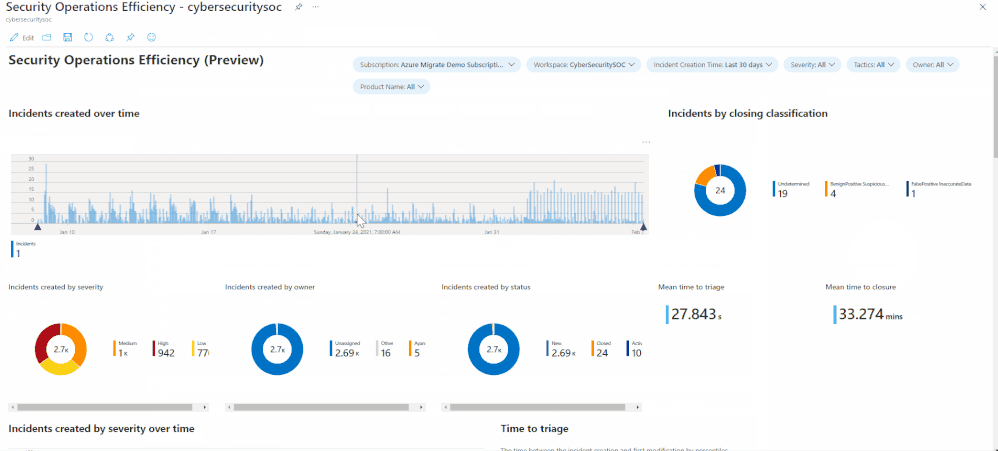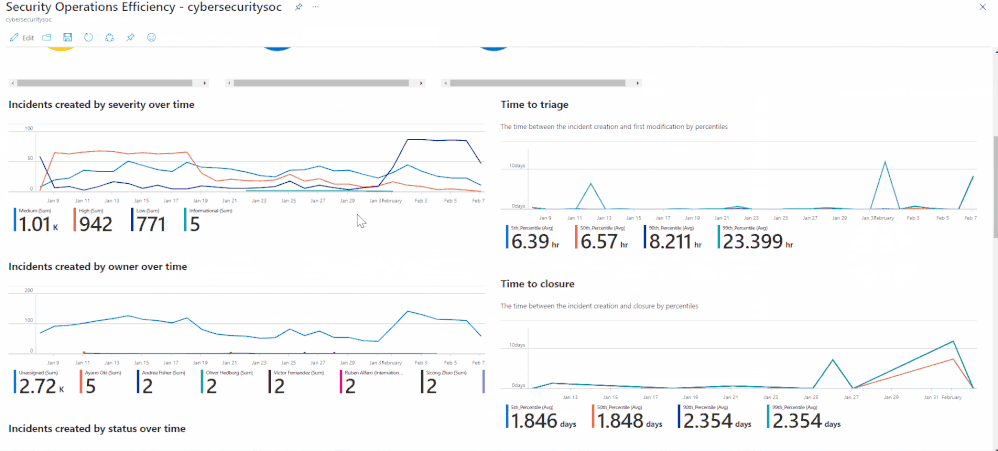
With the out-of-the-box security operations efficiency workbook template, you can monitor your SOC operations. The workbook contains the following metrics:
- Incident created over time.
- Incidents created by closing classification, severity, owner, and status
- Mean time to triage
- Mean time to closure
- Incidents created over time by severity, owner, status, product, and tactics.
- Time to triage percentiles
- Time to closure percentiles
- Mean time to triage per owner
- Recent activities
- Recent closing classifications
There are two ways to access this workbook –
- The workbooks gallery – You can find this new workbook template by choosing Workbooks from the Azure Sentinel navigation menu.
- The incidents pane: You can find the new workbook in the Incidents action panel at the top of the pane. If a saved workbook was created from the workbook template, the button would lead to the saved workbook. If not, it will lead to the workbook template. More details can be found in the documentation.
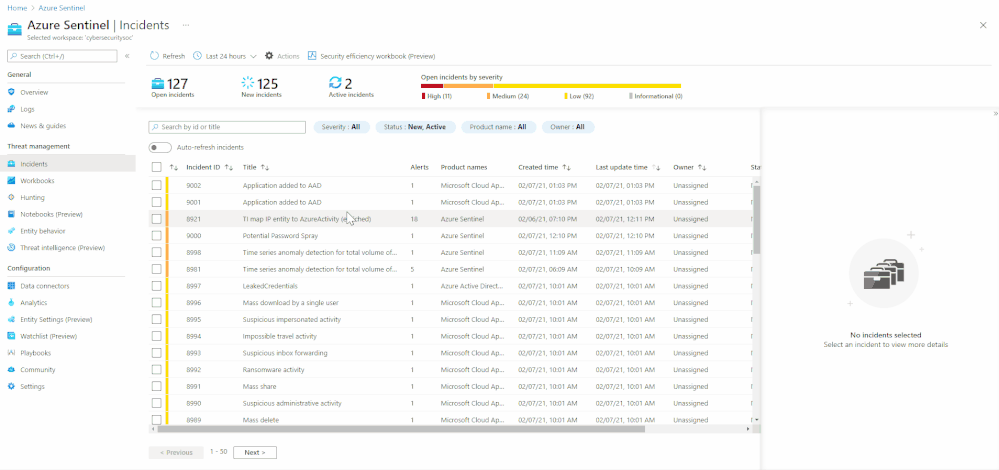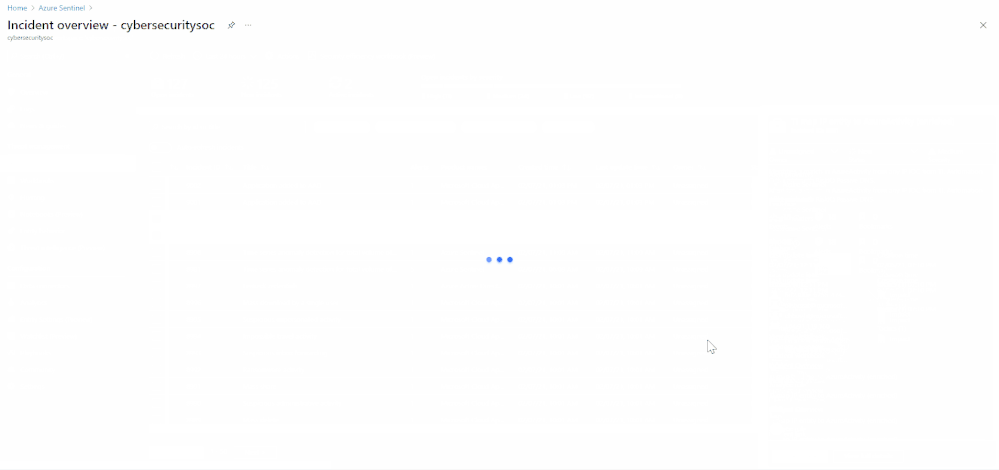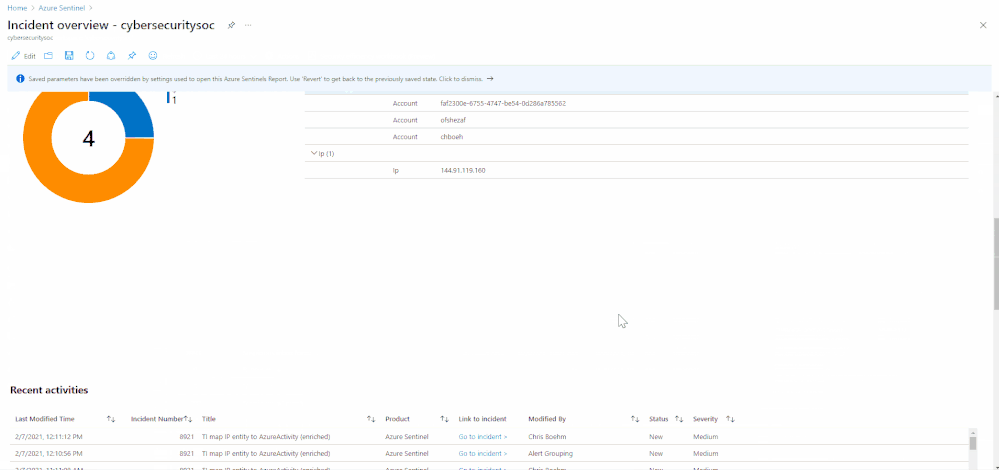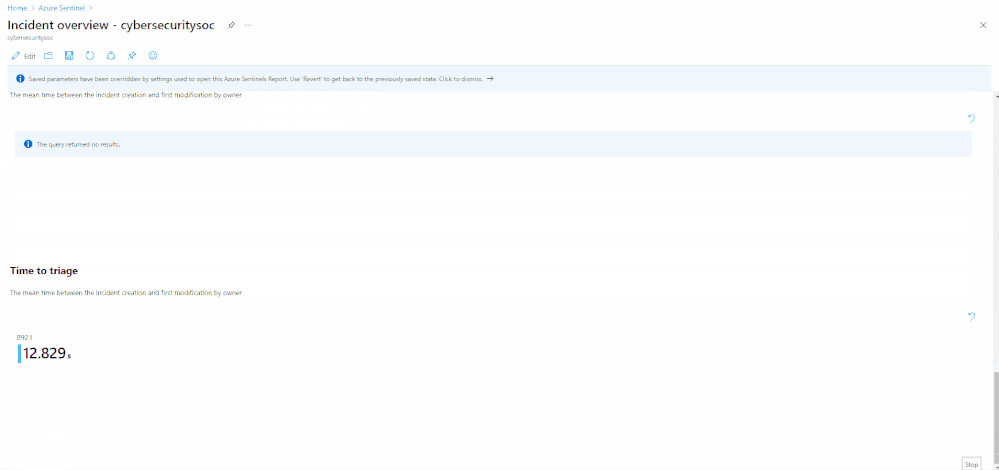
Incident overview
With this out-of-the-box Incident overview workbook template, you can customize the data your analysts get on a given incident, including a view of auditing data, recommendations, and more on a given incident. The workbook contains the following metrics:
- Incident’s title, alerts, status, bookmark, severity, owner, etc.
- Closing reasons of similar incidents
- Recent actions that were taken on the incident
- Incident’s comments
- Time to closure/triage
There are 2 ways to access this workbook –
- The workbooks gallery – You can find this new workbook template by choosing Workbooks from the Azure Sentinel navigation menu.
- The incidents pane – You can find the new workbook in the Incident preview panel on the incidents list’s right side. If a saved workbook was created from the workbook template, the button would lead to the saved workbook. If not, it will lead to the workbook template.
Thanks to all the reviewers @Ofer_Shezaf, @Yechiel_Levin, @mariasvc, @krisquick, and @Sarah_Young, and special thanks to @romarsia for the collaboration

by Contributed | Feb 17, 2021 | Dynamics 365, Microsoft 365, Technology
This article is contributed. See the original author and article here.
Finance leaders are organizations’ linchpins, and during crises such as the pandemic, they take on enormous responsibilities to steer their businesses through the storm while simultaneously preparing for the future. Some of the actions savvy finance leaders are taking during these uncertain times are to continue to reduce costs, mitigate risks, and accelerate their company’s digital transformations.
Our upcoming event, Finance Reimagined, is a free virtual conference. The summit will feature talks from finance leaders, from whom you’ll learn about hard-won lessons and hear valuable insights. Discover the actions your peers and industry leaders are taking to sustain core financial processes through the pandemic and how they’re pivoting to the future amidst continued uncertainties. And engage with thought leadership content, peer-to-peer discussions, and more.
- What: Finance Reimagined virtual CFO summit
- When: February 24, 2021
Capture learnings and best practices
During the summit, for which more than 2,000 finance leaders have registered, successful leaders reveal how they are leading their companies through three key stages: Response, Recovery, and Reimagination.
As Microsoft CEO Satya Nadella explained in the New York Times, response means “responding to the immediate impact through office closures, cost cuts,” etc. Next comes “recovery, which is already underway in many places, and will be more like a ‘dial’ than a ‘switch.'” The critical third phase is “reimagination.” This is where “innovations born of necessity during the previous two phases will emerge, like remote control of manufacturing processes, AI bots helping diagnose patients, and more effective distance-learning technologies.”
The most innovative and renowned finance leaders have used the crises to not only respond and recover but to further embrace the potential of digital transformation and to reimagine the future.
Gain insights from impactful speakers
Hear keynotes from industry leaders, including economist Rebecca Henderson, the John and Natty McArthur University Professor at Harvard Business School, who will share her thoughts on reimagining capitalism and grappling with the future of work, and finance leaders Mark Fowler of AstraZeneca and Ritesh Tiwari of Unilever.
Get a sneak peek of PwC’s CFO Pulse Survey, which provides a vision and practical steps to “the new normal.” This includes how finance is shifting to embrace and enable the modern workplace across cost, risk, and efficiency agendas.
Learn how to embrace the need to move quickly and how doing so requires a modern finance function that is resilient, adaptable, cost-effective, and focused on speed to value in a session with Tony Klimas, partner, Global Finance Practice Leader at Ernst & Young LLP, and Myles Corson, Global and Americas Market Leader, Financial Account Advisory Services at Ernst & Young LLP. They will also reveal findings from the 2020 DNA of the CFO study and share lessons from the front lines.
See how targeted solutions are addressing key challenges
See how finance leaders are overcoming challenges through sessions focused on you and your pain points. For example, learn how to confidently complete a virtual close, provide engaging analytics to support quick decisions, and take a quantitative approach to understand and address employee engagement.
In other sessions, take a deep dive into predictive analytics, and learn how AI is being infused into financial processes to proactively reduce write-offs, improve cash flow, and make accurate, data-driven, and proactive decisions. And see real-world uses of automated SOX control, including how Microsoft leveraged models to automate the processing of payout statements, saving close to 20,000 hours of manual work and bringing the error rate to zero.
Engage with peers and build your network
Engage in peer-to-peer discussions through small-group breakout sessions. Join existing roundtables or create your own and invite peers to discuss challenges related to respond, recover, or reimagine. Connect with thought leaders and advisories, and add these business leaders to your own professional network.
Register today
Benefit from others’ hard-won lessons and prepare for the future. Register now for Finance Reimagined.
The post Join Microsoft at Finance Reimagined: response, recovery, and reimagination appeared first on Microsoft Dynamics 365 Blog.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.





Recent Comments