by Contributed | Feb 19, 2021 | Technology
This article is contributed. See the original author and article here.
By Luke Ramsdale – Service Engineer | Microsoft Endpoint Manager – Intune
This is the first in a five-part series about using BitLocker with Intune. The series will review basic concepts and recommended approaches to deploying BitLocker using Intune. Upcoming posts will describe simple and advanced troubleshooting techniques.
This post covers the concepts, requirements, and configurations needed for a successful deployment.
Intune basics
Intune is a cloud-based service that focuses on mobile device management (MDM) and app protection policies (APP also known as MAM). It helps administrators manage enrolled devices through policies. You use a policy to enable and configure BitLocker on Windows 10 devices.
Intune uses the Windows configuration service provider (CSP) to read, set, modify, or delete configuration settings on Windows devices enrolled into Intune using Synchronization Markup Language (SyncML) or Wireless Application Protocol (WAP) protocols. BitLocker Intune uses the BitLocker CSP.
BitLocker basics
BitLocker is a built-in Windows data protection feature. It encrypts, drives, and prevents the theft of data from lost, stolen, or decommissioned computers. BitLocker provides the most protection when used with a Trusted Platform Module (TPM), version 1.2 or later.
Hardware requirements for BitLocker
It is important to understand that BitLocker has specific hardware requirements and that some methods of enabling BitLocker are dependent on those conditions. Silent encryption, for example, requires TPM on a device.
Hardware requirements include:
- For TPM 2.0 devices, you must have native Unified Extensible Firmware Interface (UEFI) configured. (Secure boot is not required but adds another layer of security.)
- BIOS or UEFI firmware must support USB mass storage.
- You must partition the hard disk into an operating system drive formatted with NTFS and a system drive with at least 350 MB formatted as FAT32 for UEFI and NTFS for BIOS.
Note
We highly recommended that the device you are encrypting has a supported TPM chip (version 1.2 and higher).
BitLocker recovery
If BitLocker enters recovery mode when starting the operating system, there are ways to restore access. Choose one of the following options to restore access to the protected drive:
- Manual option: Retrieve the 48-digit recovery password from a stored location (printed or USB).
- Automated option: An administrator can obtain the recovery password from Microsoft Azure Active Directory (Azure AD) or Active Directory Domain Services (Azure AD DS).
Note
A data recovery agent (DRA) is someone authorized to decrypt data on a Windows operating system. The agent can use their credentials to unlock the drive. However, Intune doesn’t support DRA certificates so the process would have to occur outside the Intune environment.
Intune BitLocker configuration processes
Before you configure a BitLocker encryption policy, consider the following options:
- How much do you want users involved in the BitLocker configuration process? Do you want them to interact with the process, be silent, or both?
If you have multiple requirements, you might need to configure multiple policies.
- Do all your devices meet the hardware prerequisites? Do you have a subset of devices that do not have a TPM?
If you have older devices without TPM, you will not be able to encrypt them silently. This might mean configuring multiple policies.
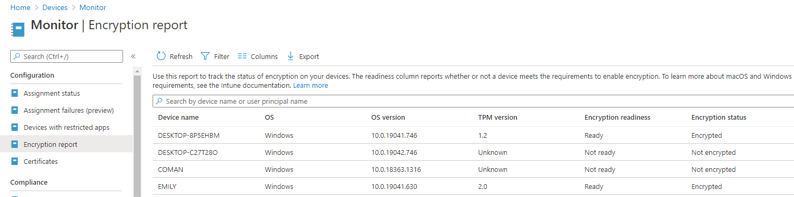
The Microsoft Intune encryption report, located in the Microsoft Endpoint Manager admin center, can help you understand the TPM status and encryption readiness of your enrolled devices. To view the report, select Devices > Monitor > Encryption report.
 BitLocker Encryption Report in the MEM admin console
BitLocker Encryption Report in the MEM admin console
- Where do you want to store the recovery key?
You can store the recovery key in on-premises Active Directory (if hybrid joined), in Azure AD, or manually. Most administrators store the key in Azure AD, which works for both Azure hybrid services and Azure AD joined devices.
- Do you want to enable recovery password rotation?
This option will refresh the recovery password after it is used and prevent further use of the same password, enhancing security. Prerequisites include Windows 10 1909, having Intune enrolled, Azure AD, or Azure hybrid services joined.
- What algorithm strength do you want to use?
For OS volumes and fixed drives: XTS-AES 128-bit is the Windows default encryption method and the recommended value.
For removable drives: Use AES-CBC 128-bit or AES-CBC 256-bit if the drive will be used in other devices that are not running Windows 10, version 1510 or earlier.
Note: For Autopilot devices, please read Setting the BitLocker encryption algorithm for Autopilot devices | Microsoft Docs to avoid devices from automatically encrypting when Azure AD joining with a different encryption algorithm to the one configured in the policy.
Best practices for configuring BitLocker for Intune
Here are best practices and recommended processes for using BitLocker with Intune.
- Use a device with TPM for maximum security.
- Create the BitLocker policy using an Endpoint security policy. This workflow is the most recent method of deploying BitLocker settings. If you are currently using a device configuration profile, consider migrating to an Endpoint security policy.
Sign into the Microsoft Endpoint Manager admin center.
Select Endpoint security > Disk encryption > Create Policy.
In the Platform list, choose Windows 10 and later.
Under Profile, select BitLocker.
Select Create.
Note
To avoid conflicts, avoid assigning more than one BitLocker profile to a device and consolidate settings into this new profile.
- Use the encryption report to inventory your enrolled devices (Devices > Monitor > Encryption report). It reveals the encryption status and helps you understand the TPM presence and version distribution among your enrolled devices.
- If BitLocker is not enabled on a device after deploying a policy, check the encryption report to see if the device meets the prerequisites.
More info and feedback
For further resources on this subject, please see the links below.
BitLocker Overview and Requirements FAQ
BitLocker recovery guide (Windows 10)
Manage BitLocker policy for Windows 10 in Intune
Encryption report for encrypted devices in Microsoft Intune
Configure endpoint protection settings in Microsoft Intune
The next post in this series will describe troubleshooting approaches for BitLocker encryption. Stay tuned!
Let us know if you have any additional questions by replying to this post or reaching out to @IntuneSuppTeam on Twitter.
by Contributed | Feb 19, 2021 | Technology
This article is contributed. See the original author and article here.
As you know, Microsoft Cloud App Security can help protect several SaaS applications. It gives you control over the actions carried out by your users and to the data they decide to store in the cloud. SaaS app protection is indeed critical, but that should not come at the cost of neglecting the protection of your Infrastructure as a Service (IaaS).
For that purpose, Cloud App Security can integrate with your AWS platform and detect risky behavior, control data sharing and help review best practice recommendations.
Note: While this blog is specific to AWS, Cloud App Security can also help you secure your Azure and Google Cloud Platform environments in the same way.
Why Connect AWS?
Microsoft Cloud App Security will help your protecting your AWS infrastructure in the following ways:
Benefit
|
Description
|
Feature or policy
|
Cloud Security Posture Management
|
A large portion of security issues we see daily are related to:
– Accidental or malicious configuration changes
– Lack of compliance to products’ best practices
MCAS can help in both of these areas.
Policies can be configured to alert you when a configuration is modified in a way that may impact security.
Best practices for AWS (as well as for other IaaS platforms) are reported in MCAS, making it a single pane of glass for your cloud security recommendations.
|
Get security configuration recommendations for AWS | Microsoft Docs
Activity policy templates: “IAM Policy Change”, “Security Group Configuration changes”, Network ACL changes”, etc.
|
Compromised account or insider threat
|
As for most applications, when AWS is connected, the applicable build-in threat detection policies will apply automatically. Some are standard and apply to all apps, some are tailored for IaaS.
|
Built-in policies such as “Multiple delete VM activites”, “Multiple VM creation activities”, “Impossible Travel”, “Activity from infrequent country”, “Connection from Risky IP”. Etc.
|
Data leakage protection
|
Many of the security incident we’ve seen in the news in the past few months/years are often due to improperly shared documents or folders.
To help you limit these risks, MCAS can detect publicly shared AWS S3 buckets and alert you, or automatically make them private.
Note: MCAS does not inspect the content of files stored in AWS S3 buckets, only their sharing status.
|
File policy template: “Publicly accessible S3 buckets”
Activity policy template: “S3 Bucket Activity”
|
How to Connect AWS to Microsoft Cloud App Security?
Let’s start with connecting AWS and Cloud App Security. Several steps need to be accomplished in this connection: Cloud App Security needs to gather (1) all the activities happening at the AWS level, like it does for other apps, and (2) some of the configuration settings and best practice guidance to review the account’s security configuration. In order to get the activities and security recommendations, the connection of AWS to Cloud App Security is two-fold:
- You must connect Microsoft Cloud App Security with AWS for Security Auditing: this will provide you with all the activities happening in your AWS environment, as well as the sharing status of your S3 buckets.
This is demonstrated in the video below.
- You need to connect Microsoft Cloud App Security to AWS for Security Recommendations: this will provide you with best practice security recommendations regarding your AWS environment directly in your Cloud App Security console.
The video below shows how to establish this connection, as well as how to leverage Security recommendations from the Cloud App Security console.
A step-by-step procedure to establish these connections is also available here.
Protect AWS – Threat detection
Once AWS is connected, the built-in threat detection policies listed here are in place analyzing the activities of taking place in AWS.
Let’s note the policies below that are specific to IaaS platforms and apply only to AWS and Azure:
Policy name
|
Description
|
Unusual multiple storage deletion activities (preview)
|
This policy profiles your environment and triggers alerts when users perform multiple storage deletion or DB deletion activities in a single session with respect to the baseline learned, which could indicate an attempted breach.
|
Multiple delete VM activities
|
This policy profiles your environment and triggers alerts when users perform multiple delete VM activities in a single session with respect to the baseline learned, which could indicate an attempted breach.
|
Unusual multiple VM creation activities (preview)
|
This policy profiles your environment and triggers alerts when users perform multiple create VM activities in a single session with respect to the baseline learned, which could indicate an attempted breach.
|
Unusual region for cloud resource (preview)
|
This policy profiles your environment and triggers alerts when a user performs suspicious creation activities in a cloud region that was not recently, or was never, accessed. This may indicate that an attacker is creating cloud resources to run malicious activities like crypto mining.
|
Quick Config – Quick Value!
In addition to the built-in threat detection policies there are a number of file and activity policy templates specifically for AWS activities, that you can use as a starting point to create your own policies.
The list is available here:
Template
|
Description
|
Publicly accessible S3 buckets (AWS)
|
Alert when an S3 bucket in AWS is publicly accessible.
|
Virtual Private Network (VPC) changes (AWS)
|
Alert on any API calls made to create, update, or delete an Amazon VPC, an Amazon VPC peering connection, or an Amazon VPC connection to classic Amazon EC2 instances.
|
IAM Policy changes (AWS)
|
Alert on any API calls made to change IAM policy
|
Console Sign-in Failures (AWS)
|
Alert of multiple sign-in failures to AWS console.
|
CloudTrail changes (AWS)
|
Alert on any API call made to create, update, or delete a CloudTrail trail, or to start or stop logging a trail.
|
EC2 Instance changes (AWS)
|
Alert on any API call is made to create, terminate, start, stop, or reboot an Amazon EC2 instance.
|
Network Gateway changes (AWS)
|
Alert on API call made to create, update, or delete customer’s internet gateway.
|
Network Access Control List (ACL) changes (AWS)
|
Alert on any configuration changes involving Network ACLs.
|
S3 Bucket Activity (AWS)
|
Alert when AWS S3 API call is made to PUT or DELETE bucket policy, bucket lifecycle, bucket replication, or to PUT a bucket ACL. The alert will also cover Cross-origin resource sharing PUT bucket and DELETE bucket events.
|
Security Group Configuration changes (AWS)
|
Alert on configuration changes which involve security groups.
|
When you create a new policy from a template the default behavior is to create an alert, so you can be notified of a match to the policy. This does not have any impact on the users or environment. After reviewing the policy matches you can decide to configure governance actions to be taken when there is a policy match. For example, a policy that is created from the Publicly accessible S3 buckets (AWS), you can decide to “Make private” or “Remove a collaborator”.
The video below will details how to create and configure these policy templates:
Custom policy
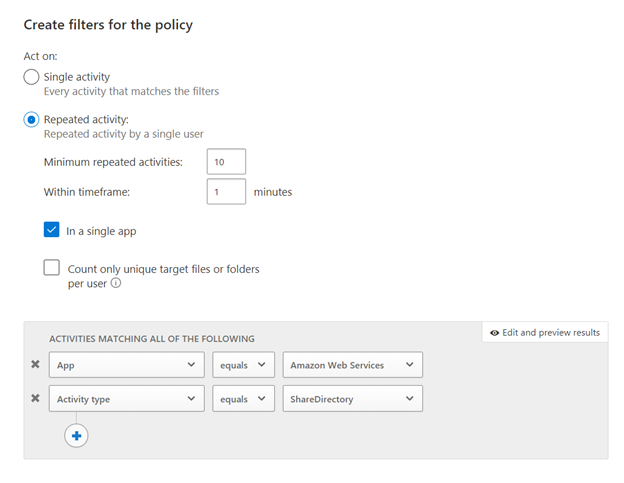
All the templates we discussed above are great best practices and apply to most customers. However, they may not capture the uniqueness of your environment. For that, you can configure custom policies. Here are a few best practices when configuring these:
- Single or repeated activity?
- That would be depending on your needs. For example, we can imagine that a case where a number of S3 buckets would become public in a short amount of time would be suspicious. On the other side, changing a critical security setting would only need to happen once to show a risk.
- Activity Filters: filters will help define the criteria for your new policy to trigger. You can filter but app, user, client type, etc. Here are a few relevant filter examples you may want to consider
- App: always start with the app you are creating the policy for. This will limit the number of entries when applying a filter on the Activity Type.
- Activity Type: every activity policy should have an activity type filter: they will define when the policy triggers. For AWS it could be a configuration change, or a sharing change in an AWS bucket.
- Other filters can bring additional value, and they should be reviewed as needed.
And now, a real-life example. The policy below will alert when a large number of S3 buckets are shared within a minute:

Reviewing and addressing AWS Security Config recommendations in Microsoft Cloud App Security
Microsoft Cloud App Security can also help you verify and ensure that your AWS environment configuration complies with Amazon’s best practices recommendations. Our official documentation, here, describes how to get started. Once you navigate through the page, you can start reviewing the recommendations.
Note: these recommendations showing up in your environment do not necessarily mean that a security incident has happened, but rather that the environment is not following security best practices.
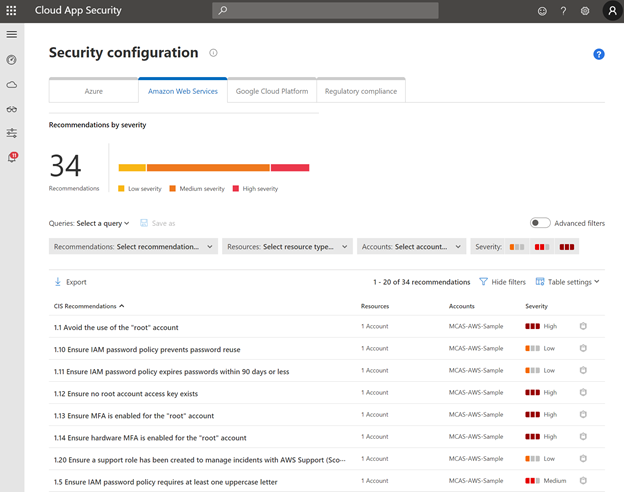
The filters in this page can be used to prioritize high severity recommendations, or specific AWS accounts in your environment. As an example, let’s review the first item from the list above.
One of the critical recommendations is to avoid the use of the “root” account in AWS. By clicking on the recommendation, Microsoft Cloud App Security automatically redirects you to the AWS portal, where you can take action.
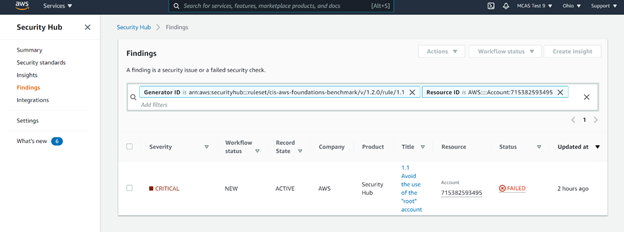
Note: not only will the security recommendation page show security configuration best practices for AWS, but also for Azure and Google Cloud Platform, should you use these. This will make Microsoft Cloud App Security your “one stop shop” to review your Cloud Platform Security Posture (CSPM).
Share your use case!
Now that you know all you need to get started with protecting AWS using Microsoft Cloud App Security, please share with us your thoughts and your use cases. We would love to hear your feedback on our AWS integration.
Blog by @Gershon Levitz , Idan Basre and @Yoann Mallet
by Contributed | Feb 19, 2021 | Technology
This article is contributed. See the original author and article here.
Initial Update: Friday, 19 February 2021 21:06 UTC
We are aware of issues within Application Insights in Japan West region and are actively investigating. Some customers may experience delayed or missed Log Search Alerts and Data Latency.
- Work Around: None
- Next Update: Before 02/19 22:30 UTC
We are working hard to resolve this issue and apologize for any inconvenience.
-Jeff
by Contributed | Feb 19, 2021 | Technology
This article is contributed. See the original author and article here.
Today, I worked on a service request that our customer reported that a query that they are using is taking more time if they execute the same in SQL Server Management Studio.
Besides too many things that could impact in the execution of the query, I would like to share another thing that could impact also in the execution.
I saw that in many applications, that customer code tries to parametrize the values that it is a good idea, but, you need to review that the parameter type that your application is using.
For example, if your application is running the following query:
SET STATISTICS TIME ON
SET STATISTICS IO ON
DECLARE @Param as nvarchar(200) = 'AnyValue'
select * from PerformanceVarcharNVarchar where TextToSearch =@Param
The results as you could see would be:
SQL Server Execution Times:
CPU time = 0 ms, elapsed time = 1633 ms.
SQL Server parse and compile time:
CPU time = 0 ms, elapsed time = 0 ms.
SQL Server Execution Times:
CPU time = 0 ms, elapsed time = 0 ms.
Completion time: 2021-02-19T19:39:58.8536169+01:00
But, if I run the same execution running the following query:
SET STATISTICS TIME ON
SET STATISTICS IO ON
select * from PerformanceVarcharNVarchar where TextToSearch ='AnyValue'
SQL Server Execution Times:
CPU time = 0 ms, elapsed time = 0 ms.
SQL Server parse and compile time:
CPU time = 0 ms, elapsed time = 0 ms.
SQL Server Execution Times:
CPU time = 0 ms, elapsed time = 0 ms.
Completion time: 2021-02-19T19:42:27.2848682+01:00
Why? Well, the reason, is that application is using unicode parameter that SQL Server needs to perform an implicit conversion to unicode if the column is not Unicode. In this situation, the column TextToSearch is a varchar and the parameter datatype is unicode. Sometimes, the time is slighty different between executions with/without unicode but if your application executes multiple times having this difference or reading a lot of rows that might cause parallelism in the execution impacting too much in your environment.
So, please, remember to use the same parameter datatype that your database has in your application.
Enjoy!
by Contributed | Feb 19, 2021 | Technology
This article is contributed. See the original author and article here.
Microsoft commissioned Forrester Consulting to conduct a Total Economic Impact™ (TEI) study and examine the potential return on investment enterprises may realize from deploying Surface Hub. The purpose of this study is to provide readers with a framework to evaluate the potential financial impact on their organizations of using Surface Hub.
https://cdn.techcommunity.microsoft.com/assets/Surface/forrester-tei-microsoft-surface-hub.pdf
This browser does not support PDFs. Please download the PDF to view it: Download PDF.
BitLocker Encryption Report in the MEM admin console


Recent Comments