by Contributed | Jan 17, 2021 | Technology
This article is contributed. See the original author and article here.
We are excited to announce that we are about to increase our customers’ protection by upgrading the default automation level of our Microsoft Defender for Endpoint customers who have opted into public previews from Semi – require approval for any remediation to Full – remediate threats automatically.
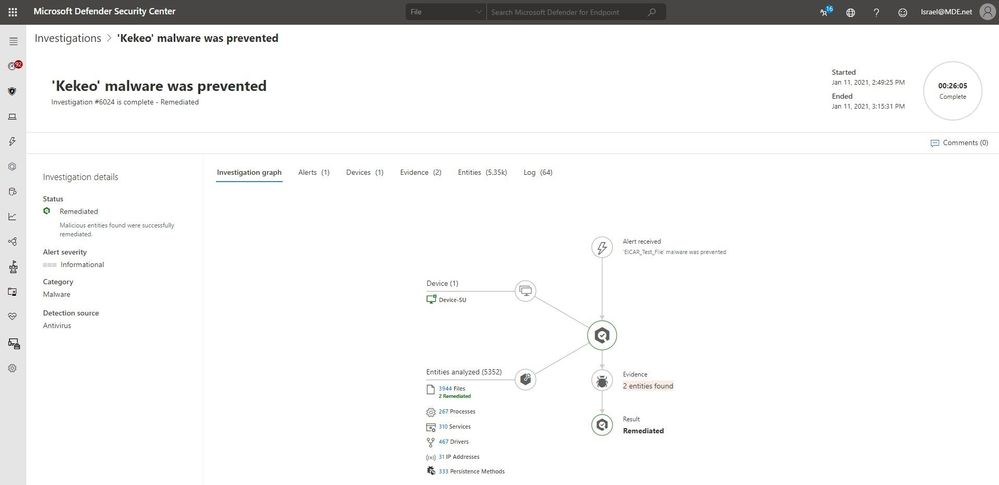
Auto investigation and remediation overview
When an alert is raised in Microsoft Defender for Endpoint, an automated investigation immediately starts running on the machine where the suspicious activity was detected. It begins with an analysis of the malicious entities that are part of the alert and continues with collection and examination of other entities associated with it. The automated investigation inspects files, processes, services, registry keys, and any area that may contain threat-related evidence.
The result of an automated investigation started by an alert is a list of related entities found on a device and their verdicts (malicious, suspicious, or clean). For any malicious entity, the investigation will create a remediation action, an action that, when approved, will remove or contain a malicious entity that was found in the investigation. These actions are defined, managed, and executed by Microsoft Defender for Endpoint without the security operations team having to remotely connect to the device.

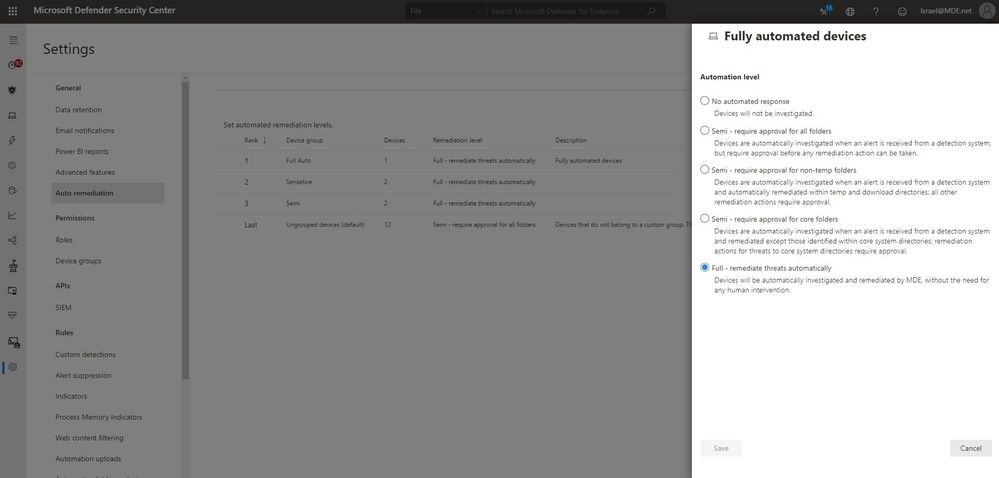
Remediation actions are approved or declined according to the device automation level. When it is set to ‘Full’, the remediation action will be approved automatically, without further waiting. When it is set to ‘Semi’, the action will wait for manual approval, which may lead to losing valuable time in which the malware may cause damage and spread to other devices.
Automated investigation and remediation supports queuing of remediation actions for devices that are not available, so that when they become available, the actions will be triggered immediately. All remediation actions, whether pending, running, or completed, can be viewed in the Action Center. If you’ve determined that a detected device or a file is not actually a threat, you can undo remediation actions that were taken for a specific device or across the entire organization.
Empowering defenders with automation by default
When our automated investigation and remediation capabilities were first introduced, the default automation level was set to semi – require approval for any remediation. Since then, we have increased our malware detection accuracy, added the option to undo remediation actions, and improved our automated investigation infrastructure. Throughout this time, we have seen thousands of cases where organizations with fully automated tenants have successfully contained and remediated threats, while other companies, left with the default ‘semi’ level, have remained at high risk due to lengthy pending time for approval of actions.
Data collected and analysed over the past year shows that organizations who are using full automation have had 40% more high-confidence malware samples removed than customers using lower levels of automation. Full automation also frees up our customers’ critical security resources so they can focus more on their strategic initiatives.
In light of the significant benefits of using automatic approval of remediation actions, and after changing the default automation level for new customers, starting February 16, 2021, tenants who have opted in for public previews in the Microsoft Defender for Endpoint will be automatically upgraded to the new default automation level: Full-remediate threats automatically.
The new default automation level can be kept (this is recommended) or changed according to your organizational needs. This change does not impact or override device group definitions that were previously set to control automation level.
To get started with Microsoft Defender for Endpoint public preview capabilities, we encourage customers to turn on preview features in Microsoft Defender Security Center.
If you’re not yet taking advantage of Microsoft’s industry leading optics and detection capabilities, sign up for a free trial of Microsoft Defender for Endpoint today.
Additional resources:
Create and manage device groups
Automation levels in automated investigation and remediation capabilities
Review and approve remediation actions following an automated investigation
by Contributed | Jan 17, 2021 | Technology
This article is contributed. See the original author and article here.
Hey there…
Whilst 2009 fixed many issues, we discovered there was a couple of issues affecting OneDrive and CCD. Pleased to say these have now been addressed.
You can find the HF at this location :
FSLogix Apps 2009 HF_01 (2.9.7654.46150)
You should no longer use FSLogix 2009 (2.9.7621.30127)
by Contributed | Jan 17, 2021 | Technology
This article is contributed. See the original author and article here.
Hey there….
This is Phil here from the FSLogix Team. I recently came across an interesting topic the other day and I thought i would share it with you .
When using VHDlocations and have 2 or more locations set in the string , whether this is a Multi_SZ or Reg_SZ, it may be perceived that if the first location in the string is not accessible then we will fall back to the second location or the third and so on to create and /or access the VHD(X) container.
This is not the correct interpretation.
When using VHD locations, only one VHD location can be accessed at any one time
- This feature is NOT created as a fail-over option; using 2 or more VHD locations does not offer any form of HA or resiliency compared to CCD ( Cloud Cache)
- The list of locations in VHDLocations was created to allow a customer to control where the VHD is placed and to be able to control which VHDs are created on which location using Share Permissions
- VHDLocations with a list expects all the locations to be available at all times.
- Storage locations for user data are not supposed to be unavailable.
So what happens if the first location is not available as a result of the Server being physically unavailable ?
FSlogix has built-in logic to determine that the first location is not available and will not proceed to create another disk on the next server in the list .
If the opposite were true and the VHD Locations were allowed to proceed in creating new VHDs then we would end up with a scenario of a user having multiple VHDs in different locations ; this would result in Profile data not be available for that current user session . It would then be an arduous task to merge all that data from the multiple disks to one disk.
Caveat: If one of the servers in the list is down then, it would prevent people from logging on.
The only time that a another location is made available is when the share permissions on the server containing the VHD has changed and the share is no longer accessible. FSlogix will then look at the next server in the list and if the share is accessible then it will create the VHD on that share.
To prevent another VHD from being created on another share location, you should ensure that you always specifically set the permissions so that only one location was writeable for specific user(s) or groups and thus preventing any of the other share locations having another profile and /or ODFC disk for that user.
And if its HA /Resiliency you are looking for then Cloud Cache is the solution here.
Until next time ……..
by Contributed | Jan 17, 2021 | Technology
This article is contributed. See the original author and article here.
Final Update: Sunday, 17 January 2021 12:03 UTC
We’ve confirmed that all systems are back to normal with no customer impact as of 01/17, 11:00 UTC. Our logs show the incident started on 01/17, 10:00 UTC and that during the 1 hour that it took to resolve some of customers may experience missing of misfired alerts when using Azure Metric Alert Rules.- Root Cause: The failure was due to a recent deployment task .
- Incident Timeline: 1 Hour – 01/17, 10:00 UTC through 01/17, 11:00 UTC
We understand that customers rely on Alerts as a critical service and apologize for any impact this incident caused.-Soumyajeet

by Contributed | Jan 16, 2021 | Technology
This article is contributed. See the original author and article here.
The importance of online accessibility has become even more pronounced for Office Apps & Services MVP Susan Hanley.
In the past four years, the consultant and author specializing in successful collaboration and knowledge management solutions turned 60, became a grandmother, and attended her 40th college reunion.
“These personal milestones are a stark reminder that even though I feel a lot younger and can do a lot more physically than many of my much younger friends, I’ve noticed personally, as people age, they may experience changes in their abilities,” Susan says.
“As an information architect, I care enormously about organizing and presenting information. As a business analyst, I care enormously about generating business value. For the past few years, my professional learning journey has been driven by some personal and professional experiences that have caused me to think a lot about time, or the lack thereof, and inclusion.”
Susan, who is dedicated to creating easier-to-consume SharePoint sites and pages, says one of those instructive professional experiences came in the form of the Intrazone podcast ‘Accessibility from The Start’ and guest Lauren Back, a usability engineer at HCL Technologies who happens to be blind.
In the 2019 episode, Lauren discussed how she imagined that someone who is not blind could quickly scan a webpage to get a sense of what the page is all about. However, Lauren uses a screen reader and, depending on how the page author created the page, she might have to listen to every single word on a page.
“Lauren got me thinking about other things I should be doing to make my SharePoint pages not just more organized and readable, but also more accessible,” Susan says.
There remains an accessibility awareness gap for many information architects and business analysts, Susan says, but it is one which can be overcome with better education and training.
“For example, I think people know in general that it’s good to add alt-text for images, but many people aren’t aware of what exactly you should put in alt-text,” she says. “I took the Accessibility fundamentals courses in Docs.microsoft.com and learned for the first time about the accessibility checker in PowerPoint. I am still working through all of my PowerPoint slide decks to make sure that they are more accessible!”
Ensuring accessibility is an ongoing process, and Susan shares the following three tips in making SharePoint pages and news accessible to all.
First, write content “upside down.” People scan web pages, they don’t read them, Susan says. To make pages more “scannable” for all readers, put the key information that readers must have to be successful at the top of the page. Try to write more like a journalist with the key points early on the page and less critical information next. Put your conclusion first, instead of at the end.
Second, make sure all images have ‘alt text.’ Susan notes that all images and graphics need alternative text descriptions that allow people who use a screen reader to understand what they represent. Alt text also shows in browsers when images don’t load, so it is helpful for slow internet connections as well.
Third, Susan suggests using headings to make pages easy to navigate. This means using the built-in H1, H2, and H3 styles in text web parts. This allows readers to jump from section to section using keyboard shortcuts such as the Tab key. Heading styles also allow for the creation of “table of contents” for pages using page anchors (bookmarks).
For more tips, check out Susan’s article on Sharepoint accessibility on the Humans of IT Blog.

Image: Office Apps & Services MVP Sue Hanley and her granddaughter.


Recent Comments