by Contributed | Jan 18, 2021 | Technology
This article is contributed. See the original author and article here.
Now we let the cat out of the bag that we’re putting on an event on Feb 2nd, 2021 – it’s time to go a little deeper. How about some information about the AWESOME content we have lined up that is being created RIGHT NOW, just for you. In case you missed the previous post where I talked about the concept of what we’re trying to do, make sure you go back and read it before continuing.
Our focus for this iteration of IT Ops Talks is “All Things Hybrid”. We took some time to debate this out as a team and vet it with some folks in the community and in our internal networks. We’re challenging folks creating this first round of content with how their technical session will be relevant to a Hybrid world of on-prem and in the cloud – but also with its relevancy for making your on-prem world better. This post is going to cover the top level details of what specific topics will be covered AND who we’ve lined up from the engineering teams to create / deliver them! Think of this as your initial content catalogue of what to expect on the 2nd with even more details to come.
I have to give a shout out and say THANK YOU to the Experts / Engineers and everyday Microsofties who are trusting us to help them share their content in this format on such short notice. This list is our first cut at assembling the bulk of the content being created for YOU in this new format. Have a read through to the end of the post and let us know what you think!
Securing your Hybrid environment Part 1 – Azure Security Center
Sarah Young (@_sarahyo) – Sr. Program Manager
Now more than ever, organizations are challenged with keeping their employees productive working remotely and interacting with their customers over digital channels. At the same time there has been an increase in evolving digital security threats as bad actors recognize an opportunity to disrupt your business. Moreover, security resources are stretched, and prioritization is important.
Securing your Hybrid environment Part 2 – Azure Sentinel
Sarah Young (@_sarahyo) – Sr. Program Manager
Sit down with Azure Sentinel Sr. PM Sarah Young to discuss new features, functionality, and best practices on harnessing the AI enabled security solution.
Securing SMB from within and without
Ned Pyle (@nerdPyle) – Principal Program Manager
Learn specific strategies to secure SMB from lateral movement and external interception attacks! Watch interesting demos of the steps you can take to protect your organization! See the often unpredictable Ned Pyle struggle to be professional on camera!
Virtualized and Hybrid Backup Deep Dive (to be confirmed)
Ben Armstrong (@vBenArmstrong) – Principal Program Manager
Ben Armstrong does a deep dive on Virtualized and Hybrid Backup
How to be an AD Hybrid Health Hero
Mark Morowczynski (@markmorow) – Principal Program Manager
Grace Picking – Program Manager
Once you’ve connected your identity to Azure AD, how do you ensure it continues to function as expected? In this session, you’ll learn how to keep your hybrid identity environment healthy, across different Active Directory and Azure Active Directory scenarios.
Windows Server Hybrid Deep Dive (to be confirmed)
Jeff Woolsey (@WSV_GUY)- Principal Program Manager
Jeff goes in-depth with how Windows Server works in hybrid scenarios with Azure integration.
Windows Authentication Internals in a Hybrid World
Steve Syfuhs (@SteveSyfuhs) – Senior Software Engineer
Have you ever wondered what happens when you type your password into Windows? With the cloud becoming a major part of our world, we find ourselves having to talk to both on-premises and cloud-native resources, which dramatically affects what happens when you do type your password into Windows. Follow along as Steve Syfuhs gives a guided tour of how Windows handles logons internally and secures your authentication in a hybrid world.
Getting started with Azure Kubernetes Service (AKS) on Azure Stack HCI
Matt McSpirit (@mattmcspirit) – Senior Program Manager
In this session, you’ll learn about the new Azure Kubernetes Service on Azure Stack HCI, how you can use it to run your containerized Windows and Linux apps, how it integrates with Azure, and how it provides the best platform to run additional Azure services, including Arc-enabled Data Services. This will help you to modernize your existing applications on our Azure Stack HCI Hybrid Cloud Platform
Windows Virtual Desktop Road Map Deep Dive
Tom Hickling (@tomhickling) – WVD Global Black Belt
Dive into the forthcoming WVD roadmap and how it can help be part of your hybrid cloud strategy.
Learn the 5 key areas to consider for your hybrid workloads
David Kurth (@TheDaveKurth) – Senior Product Marketing Manager
In this whiteboard session (after a few slides for context), we will discuss the 5 key areas of any hybrid cloud workload, connectivity, application, data, identity, security & management.
Azure Stack HCI Hybrid is built-in: How does it really work?
Kerim Hanif (@kerimhanif) – Senior Program Manager
Ready to deploy Azure Stack HCI, the new hyperconverged infrastructure operating system delivered as an Azure service? Join this session to learn everything you need to know about how Azure Stack HCI’s hybrid connectivity works. Is it hard to register? (Hint: no.) Is there an agent? (Hint: no.) Does Azure see my VMs and their data? (Hint: no.) Do I need to open my firewall to freely allow Internet traffic? (Hint: no.) All these answers and more.
From WS2008 to Azure with containers – An Ops view on how to modernize existing applications with Windows Admin Center
Vinicius Apolinario (@vrapolinario) – Senior Program Manager
ITPros around the globe are trying to figure out how to modernize existing applications. End of Support for Windows Server 2008, how to move applications to the cloud, and how to leverage new technologies such as Kubernetes have become a daunting process for Ops teams. In this session we will cover how to containerize existing applications from the perspective of an ITPro. We will use tools that you are used to – such as Windows Admin Center to jumpstart your modernization process and show how to move an application from Windows Server 2008 to Azure Kubernetes Service.
Governing baselines such as STIG in hybrid server environments using Azure Policy Guest Configuration
Michael Greene (@migreene) – Principal Program Manager
Learn to use services in Azure to audit the state of servers across private and public clouds and upcoming plans to expand capabilities in this area.
Log Analytics workspace design deep dive
Meir Mendelovich (@MMendelovich) – Principal Program Manager
in this session we will cover
- Proper Workspace design: resource-centric and RBAC.
- Resource-centric alerts.
- Enterprise features: Dedicated cluster, high scale, AZ, DE, CMK
- OneAgent, Query Packs and infrastructure as code
- Workspace data Export and proper data placement
- Workspace Optimization
Monitoring and Responding to alerts in hybrid environments using Azure Monitor
Erik Namtvedt (@ErikN_MSFT) – Senior Service Engineer
A deep dive of the framework Microsoft Retail has leveraged over the last 3-4 years to monitor all their on-prem system, including in-store Video walls and others. It’s based on Azure Public-Offering technologies. It leverages Application Insights, OMS (SCOM too), Log Analytics, Azure Storage (Blob/Tables), Azure Automation, and PowerShell.
PowerShell Deep dive
Joey Aiello (@joeyaiello) – Senior Program Manager
We will use this time to take a deep dive on migratingadapting old PowerShell scripts from previous versions and making them work in PowerShell 7 and PowerShell Core.
We’ll also take a serious look at secret management with PowerShell to avoid the ever annoying problem of hardcode creds or use prompts.
Deep dive on Onboarding customers into Lighthouse
Archana Balakrishnan (@Archun0505) – Principal Program Manager
In this session we will demystify the intricacies of onboarding customers in Azure Lighthouse from a service provider’s perspective
Databases are cattle too! Running highly available databases consistently on any infrastructure using Arc data services
Travis Wright (@radtravis) – Principal Group Program Manager
Have you heard people say ‘containers or Kubernetes is not for databases’? Let me show you how that is definitely not the case in 2021. Kubernetes provides an abstraction layer over any infrastructure and an orchestration engine that powers Arc enabled data services so DevOps, DBAs, and developers can provision and manage highly available SQL and PostrgreSQL database instances on any infrastructure – on-prem, AWS, or Google. In this session, I’ll dive deep into the technical weeds with nearly 100% demos that show you exactly how it all works and you can manage it all with GUI, CLI, Azure-native tools, or Kubernetes-native tools.
Event Hub on Azure Stack Overview
Manoj Prasad () – Program Manager
Javier Fernandez (@JavierF08160601) – Senior Program Manager
Provide an overview of Event Hub on Azure Stack and highlight why Event Hub is a great offering on Azure Stack for customers.
Modernize how you manage hybrid servers with Azure Arc
Ryan Puffer () – Senior Program Manager
Think the cloud is just for things that are…in the cloud? Come learn how you can use Azure Arc to simplify IT operations across your entire fleet, no matter where your servers run. We’ll start with a deep dive into the architecture and benefits of Azure Arc followed by a demonstration of how Azure Arc can help you monitor, secure, and simplify management of a multi-tier on-premises application.
Like the sound of all that? How do you get to the content?!
Part of our content plan is to release a full length detailed blog post for EACH of these sessions that will contain specific “deep links” to all the resources, links to docs, links to Microsoft Learn modules so you can dive in and learn even more about the topics and possibly setup some hands on experiences for yourself. When each session goes live – it will have details on how to interact with the presenters and other experts from the community who are interested in the topic with a special “hallway conversation” area on our teams Discord Server.
To find the blog posts for all of these sessions, keep an eye on https://aka.ms/ITOpsTalks on our Feb 2 release date.
Want to get started earlier and talk about this event? Join our work friendly IT Ops Talk Discord server today!
by Contributed | Jan 18, 2021 | Technology
This article is contributed. See the original author and article here.
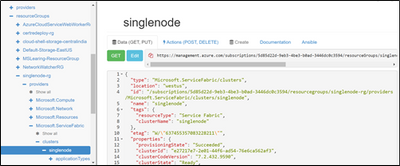
Steps to recreate/rebuild SF cluster by retaining others resources(Eg: Load balancer, Public IP, Vnet and So on…) in the Resource Group when cluster state is lost due to some unsupported operations.
Step 1: Go to Resource Explorer, navigate to SF resource and copy the configuration content of SF resource from the right plane

Step 2: Delete the SF resource in the Resource group:
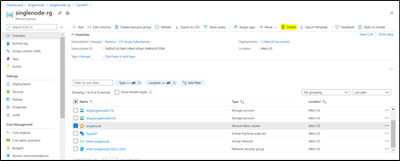
Step 3: Deploy a Custom Template:
Paste the copied SF configuration in Step 1 under the “resource : [ // Please copy here]
Remove below properties:
Add the API version under the type and modify the UpgradeMode to “Manual”
- “apiVersion”: “2018-02-01”,
- “upgradeMode”: “Manual”
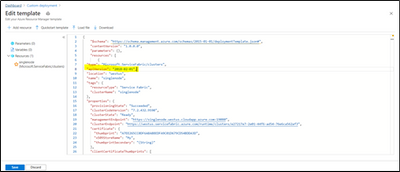
Save and Create the Resource, Post which SF resource gets created under Resource group.
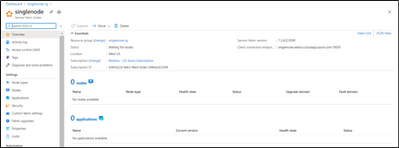
Step 4: Copy the new Cluster Id from Resource Explorer -> SF resource:
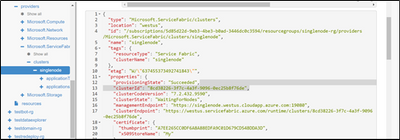
Navigate to VMSS resource -> Replace the Cluster ID in ClusterEndpoint
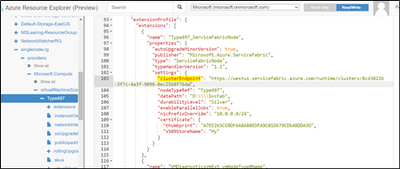
However VMSS update may result in below failure, Please ignore the Error.
If you go to Resource Group- > VMSS -> ClusterEndpoint will be updated with new Cluster ID
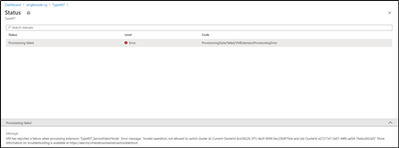
Step 5: Scale the instance count by + 1( In case of Reliability is None, +3 if bronze , +5 if Silver and so on)
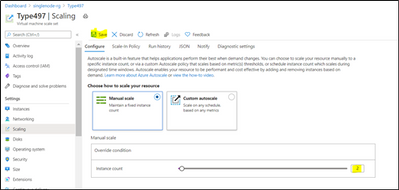
Once Instance is created, SF Status would show as “Deploying” and newly added instances will start showing under Nodes.
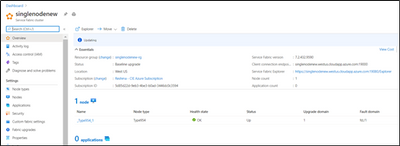
Step 6: Delete the old instance:
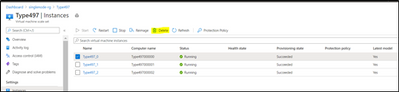
by Contributed | Jan 17, 2021 | Technology
This article is contributed. See the original author and article here.
Export and Import Bacpac file is one of the options available to migrate your database or to create a copy of it, like when you move your data from Azure SQL or Azure managed instance to on prem server, where backupRestore is not supported.
This Article is an illustration of one of the issues when importing a bacpac file, if you face error similar to:
User, group, or role ‘XXX’ already exists in the current database.
Or There is already an object named ‘xxx’ in the database.
Here is the example for same scenario:
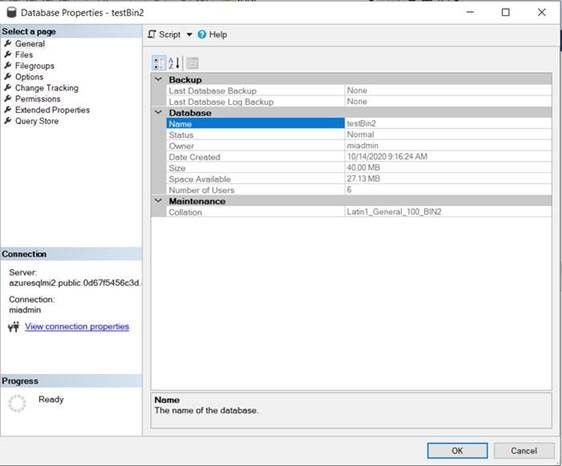
- The bacpac file was exported from a managed instance. the collation of the source database is Latin1_General_100_BIN2:

- I created two logins on Master database with different names (because the managed instance’s Master database has the default Case insensitive collation CI):
use master
go
create login testbin2_1 with password = 'P@ssW0rd123'
go
create login TestBin2_2 with password = 'P@ssW0rd123'
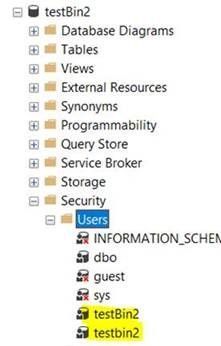
- I mapped the logins with a new users: two users with the same name on my database (creation completed successfully):
use testBin2
go
create user testbin2 for login testbin2_1
go
create user testBin2 for login testbin2_2
- If I create another database with another case sensitive collation like Latin1_General_CS_AI, I also can create the users and the same error will appear during the import process.
.
- I created the bacpac file from the Managed instance (for both databases it was succeeded):
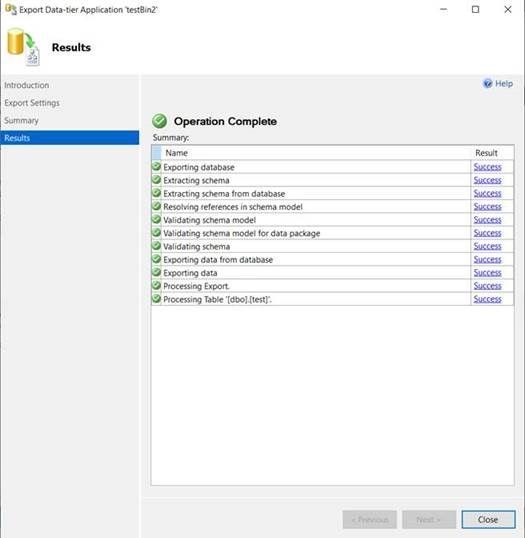
- But if I try to import the file on Azure SQL, it will fail after creation of the destination database, even if it has been created with same case sensitive collation:
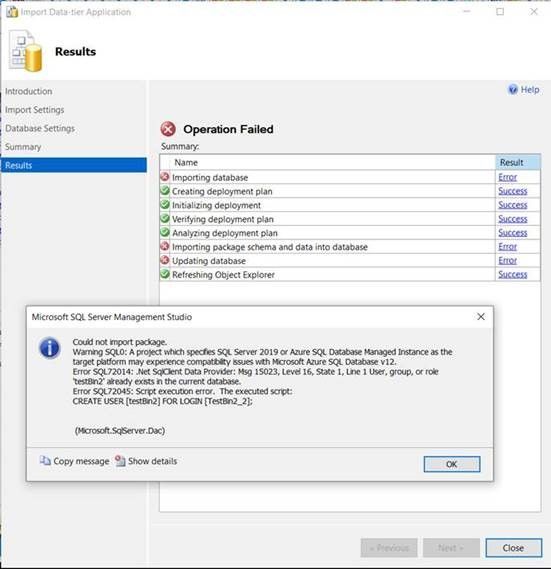
Conclusion
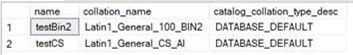
- On SQL Server, if you have a database with case sensitive collation, you can create objects like tables or users with the same name but with different letter case, this default behavior is not including Azure SQL Server,. Because Azure SQL is configured with other setting called “Catalog Collation”:
Catalog collation on Managed instance:
Catalog collation on Azure SQL:
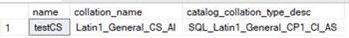
For more information about Catalog collation:
https://docs.microsoft.com/en-us/sql/relational-databases/databases/contained-database-collations?view=sql-server-ver15#contained-databases
https://docs.microsoft.com/en-us/sql/relational-databases/databases/contained-database-collations?view=sql-server-ver15
- Also,you can create a new database with catalog collation on on-prem SQL 2019 Server using the following:
CREATE DATABASE [testdb] COLLATE Latin1_General_100_CS_AS_SC
WITH CATALOG_COLLATION = SQL_Latin1_General_CP1_CI_AS;
But if you try the same on managed instance, creation of the database will fail with Error:
‘CATALOG_COLLATION’ is not supported in this version of SQL Server.
- If you import a Bacpac file to Azure SQL and there were errors like user or table with same name already exists, then you need to check the collation of the source database on on-prem or Managed instance servers.
by Contributed | Jan 17, 2021 | Technology
This article is contributed. See the original author and article here.
Now available: Grant permissions directly to a playbook to operate on Azure Sentinel, instead of creating additional identities.
Azure Sentinel Logic Apps connector is the bridge between Sentinel and Playbooks, serving as the basis for incident automation scenarios. The connector requires an identity on whose behalf it will operate on Azure Sentinel. Until now, you could do one of the following: use an Azure AD user which has been assigned an Azure Sentinel RBAC role, or create a Service Principal (for example, in form of an Azure AD registered application) and grant it the Azure Sentinel RBAC role.
Each one of these options has its advantages, but also limitations: Many would prefer not to authenticate with a user to a tool that generates automated actions. It is harder to audit (for example, using the incident table) which actions have been taken on behalf of a user and which are made by the playbook. It also makes less sense to see, for example, new comments that were generated by a playbook, but appear as if a user is their author. Also, if a user leaves the organization, you need to update all the connections that use its identity.
The service principal connection type allows us to create a registered application and use it as the identity behind the connector. You can define what this app can do, who can access it and what resources can this app access. It’s easy to delete it or replace its credentials if it’s suspected to have been compromised. For these reasons it’s great from a security perspective, but it still requires managing as another identity in the cloud that has credentials and permissions which potentially others can use.
Now, with the availability of Managed Identity for the Azure Sentinel connector, you can give permissions directly to the playbook (Logic App workflow resource), so Sentinel connector actions will operate on its behalf, as if it were an independent object which has permissions on Azure Sentinel. This lowers the number of identities you have to manage and gives the power to give access directly to the resource that operates.
How does it work?
When you turn on this feature in the Logic App, it is registered with Azure Active Directory and represented by an object ID. This identity can be assigned an Azure RBAC role on your Sentinel Workspace. The Azure Sentinel connector is configured to operate on its behalf as the selected API connection referenced by this connector.
How to use it?
To start using this new capability:
Turn on managed Identity in the Logic Apps resource
- In the Logic apps resource page, go to Identity.

- In System assigned tab, turn the status toggle to on.
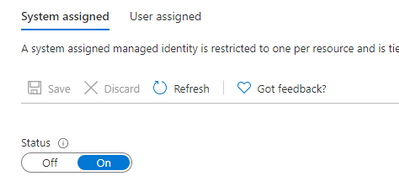
Click on Save.
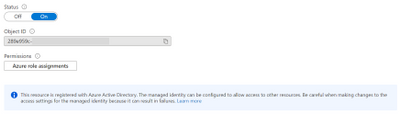
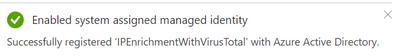
You will get a notification that this playbook was registered with Azure Active Directory:
Also, object ID will appear:
Grant permission
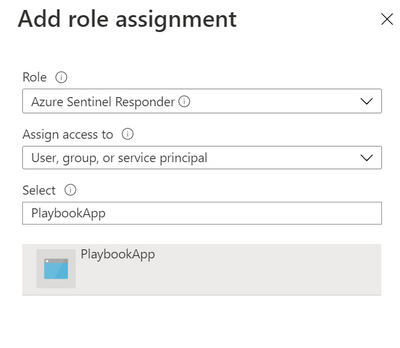
- In Azure Sentinel, go to Settings -> workspace settings -> Access Control (IAM)
- Click on Add -> Add role assignment
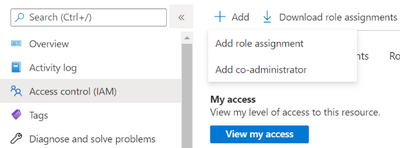
- Choose Azure Sentinel Responder role, and search for the playbook name. Select it and click save.
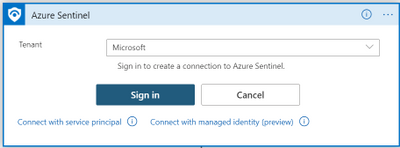
Authenticate to Azure Sentinel Connector
- In Logic Apps designer, in any of the Azure Sentinel connector steps, select Connect with managed identity
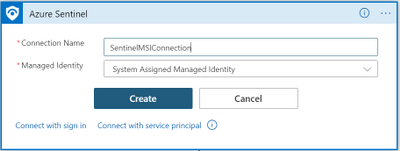
- Choose a name that will be affiliated with this connection, and click on Create
Other connectors supporting managed identity
Thanks to new Azure Logic Apps feature, more Azure AD–based connectors allow this as well. Currently, the following connectors support this feature:
Azure API Management, Azure App Services, Azure Functions, HTTP, HTTP Webhook, Azure Automation, Azure Container Instance, Azure Data Explorer, Azure Data Factory, Azure Data Lake, Azure Event Grid, Azure IoT Central V3, Azure Key Vault, Azure Log Analytics, Azure Monitor Logs, Azure Resource Manager, Azure Sentinel, HTTP with Azure AD.
Learn More




Recent Comments