
by Contributed | Nov 9, 2020 | Technology
This article is contributed. See the original author and article here.

We want to hear from you and answer your questions around using Microsoft Planner! We will be hosting an “Ask Microsoft Anything” (AMA) session on Tuesday, November 17th at 9 AM Pacific Time, here, on the Tech Community. Save the date!
To join, simply, visit the Planner AMA space on date and time Pacific Time and click “Start a New Conversation” to post your question. This event is open to all Tech Community members and we’ll have members of the Microsoft product and engineering teams standing by to provide answers.
In the meantime, if you haven’t already, be sure to join the Planner Community.
We look forward to answering your questions!
by Contributed | Nov 9, 2020 | Technology
This article is contributed. See the original author and article here.
We recently received a customer support case where the App Protection Policy (APP also known as MAM) was not being delivered to the device due to a missing IP address exemption. If your organization uses a firewall or network protection system which targets or restricts reachable IP addresses, we recommend that you update your network configuration to allow network traffic to and from all MAM IP ranges as outlined in Network endpoints for Microsoft Intune, in case you run into the same issue.
For Windows devices, if you use a Defender Firewall profile to configure your IP address settings, below are the steps you can use to update these:
- Log in to Microsoft Endpoint Manager
- Go to Devices > Configuration profiles
- Select the Windows 10 and later with a Profile Type listed as Endpoint protection
- Select Properties and click edit next to Configuration settings
- Click Microsoft Defender Firewall
- Scroll down to Firewall rules and edit the rule to update the IP address settings
For more information about firewall settings, see the following documents:
Let us know if you have any additional questions on this by replying to this post or by tagging @IntuneSuppTeam out on Twitter.
by Contributed | Nov 9, 2020 | Technology
This article is contributed. See the original author and article here.
Having the right tools can help improve your productivity as you build applications and try to get day-to-day tasks done efficiently. The CLI is the predominantly preferred by developers as a tool for performing everything from one-time tasks to creating automated scripts. To help developers work more efficiently and maximize their productivity, we’ve made many improvements to the Azure Database for MySQL Flexible Servers (Preview) CLI experience.
For example, the new experience includes:
- Refined output to ensure that you’re informed about what’s going on behind the scenes.
- A single command for creating a secure server inside a virtual network.
- The ability to use contextual information between CLI commands to help reduce the number of keystrokes for each command.
See all Azure Database for MySQL Flexible Server CLI commands to get started.
Local context support
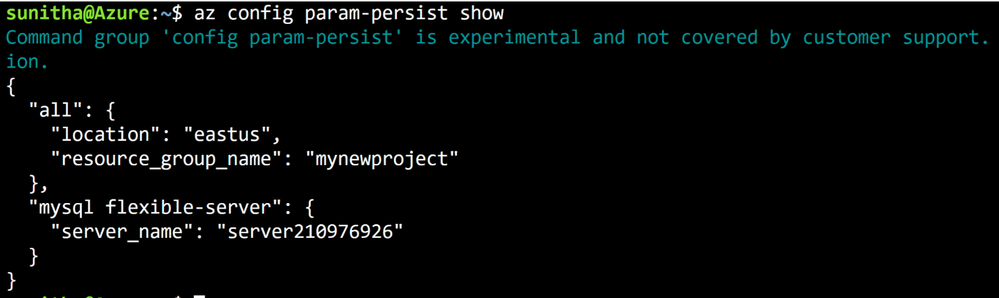
Flexible Server CLI commands support local context with the az config param-persist command, which locally stores information such as region, resource group, subscription ID, resource name, etc., for every sequential CLI command you run. You can easily turn on local context to store information by using the az config param-persist on command. If local context is turned on, you can see the contextual information by using the az config param-persist show command. You can always turn off local context by using the az config param-persist off command.
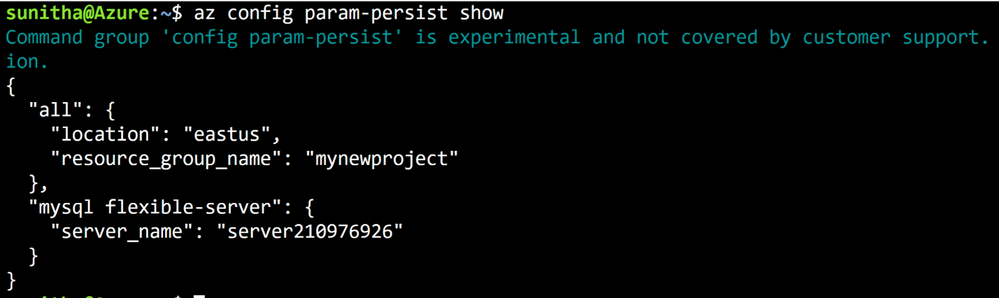
Figure 1: Run az config param-persist show to view what information is stored.
Ease of provisioning and deprovisioning
When creating a MySQL server using our managed database service on Azure, you’ll probably want to get started quickly, especially if you’re just trying things out. With the new and improved Azure CLI for Flexible Server on Azure Database for MySQL, you can quickly create a MySQL server inside a virtual network. If you prefer, you can also easily provision a server with firewall rules in a single step. You can also view the progress visually as CLI commands to keep informed about what’s going on behind the scenes.
Create a MySQL Flexible Server inside a new virtual network
Rather than using separate commands to create a resource group, a virtual network, and a subnet, you can use the az mysql flexible-server create command as shown below to create a secure MySQL Flexible Server inside a new virtual network and have a new subnet delegated to the server.
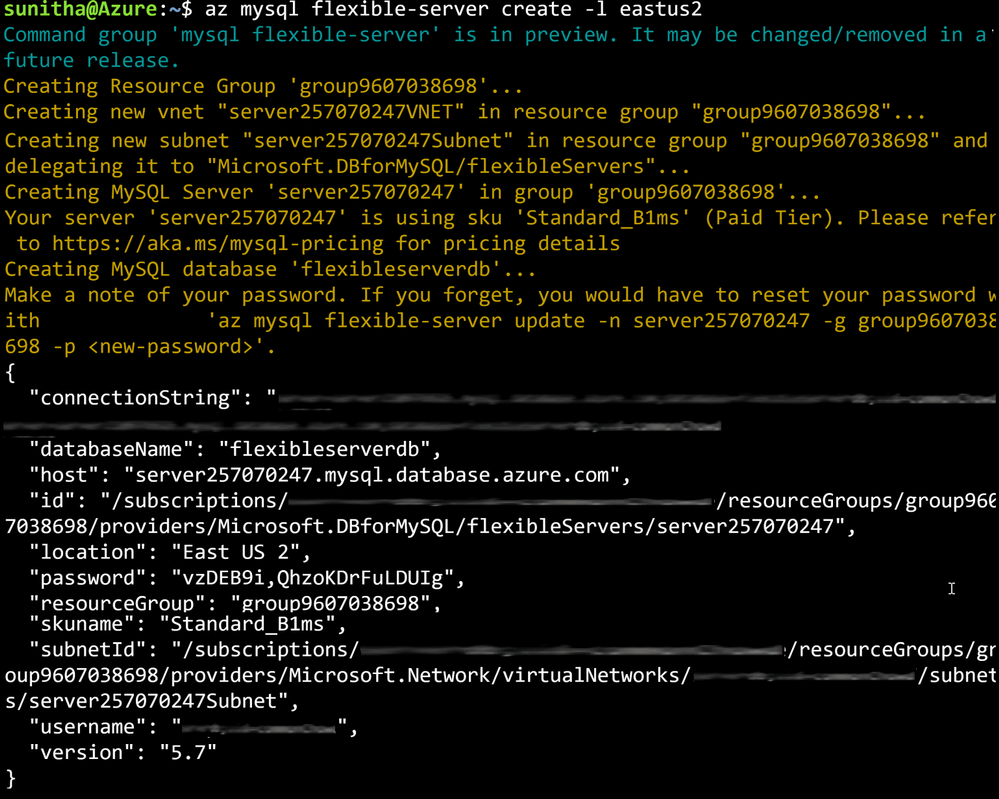
Figure 2: Run az mysql flexible-server create to provision a secure server in a virtual network
Create a MySQL Flexible Server with public access to all IPs
Use the az postgres flexible-server create –public-access all command to create a publicly accessible MySQL server. A publicly accessible server can be accessed from any client computer using the correct username and password.
To restrict access only to your IP set, use the –public -access argument to scope it either your <IP – address> or a range of IP addresses, <Start IP address – End IP address>.
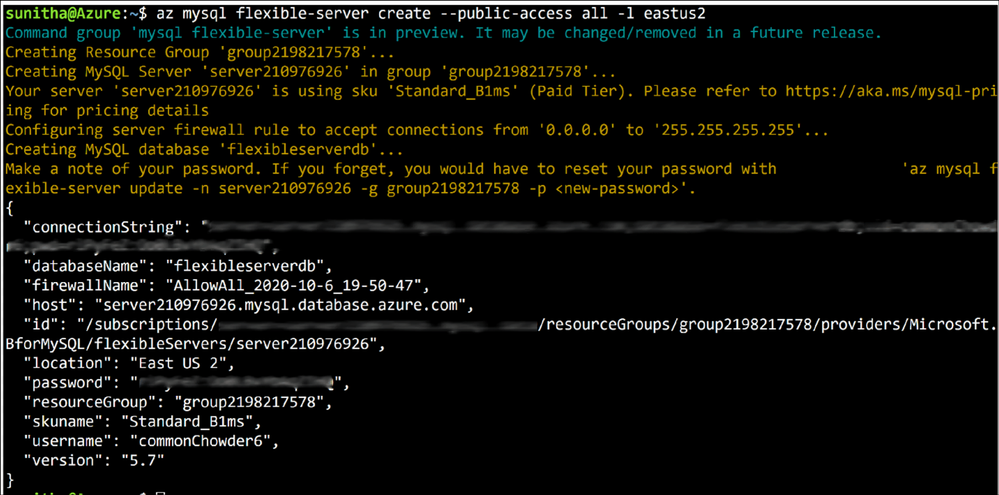
Figure 3: Run az postgres flexible-server create –public-access all to provision a publicly accessible server.
Delete the server when using local context
Use the az mysql flexible-server delete command to delete any MySQL Flexible Server identified in the local context. In the example below, the command identifies server210976926 in the local context and then tries to delete that server.
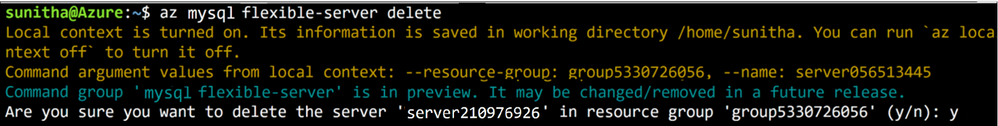
Figure 4: Run az mysql flexible-server delete to delete a publicly accessible server.
Boost your productivity
Tuning MySQL database parameters is important when configuring your server to meet your application’s needs, or even to optimize performance. You can use the parameter set command to easily update server parameters with ease . You can view all the server parameter with parameter list and parameter show commands to view the values of a specific server parameter.
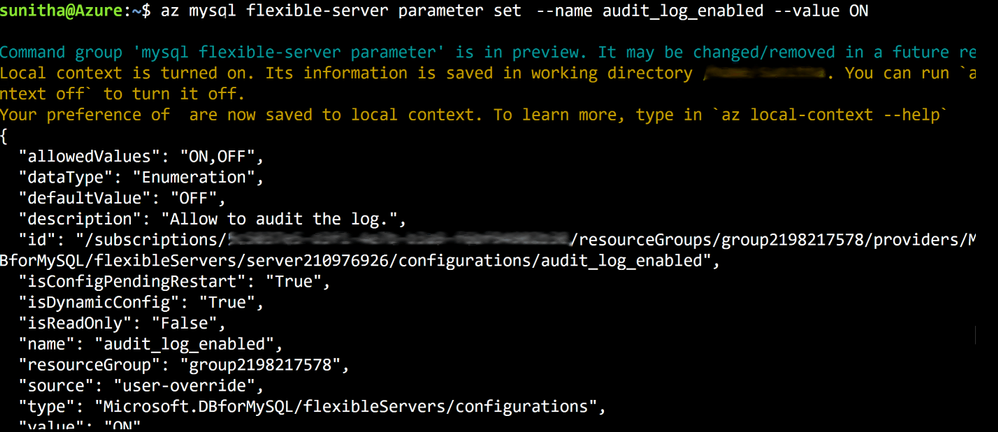
Figure 5: Run az mysql flexible-server parameter set to configure audit logs.
Do more with flexible servers with Azure CLI utilities
Here are few more powerful things that you can do when using the Azure CLI with MySQL Flexible Server:
- Use the az find command to find a specific command.
- Use the –help argument to get a complete list of commands and subgroups of a group.
- Change the output formatting to table or tsv or yaml formats.
- Use az interactive mode, which provides an interactive shell with auto-completion, command descriptions, and examples.
- Use the az upgrade command to update your CLI and extensions.
- Use the az rest command to call your service endpoints to run GET , PUT , PATCH methods in a secure way
These changes have been designed to support the best possible experience for developers when creating and managing their MySQL servers. We’d love for you to try out Azure Database for MySQL Flexible Server CLI commands and share any feedback you might have on the new or existing CLI commands.
by Contributed | Nov 9, 2020 | Technology
This article is contributed. See the original author and article here.
Final Update: Monday, 09 November 2020 20:24 UTC
We’ve confirmed that all systems are back to normal with no customer impact as of 11/9, 18:40 UTC. Our logs show the incident started on 11/9, 13:50 UTC and that during the 4 hours and 50 minute that it took to resolve the issue customers would have experienced data access issues while trying to query their workbooks whose data access calls were routed through the West US or West Europe endpoints.
- Root Cause: The failure was due to a backend dependency.
- Incident Timeline: 4 Hours & 5 minutes – 11/9, 13:50 UTC through 11/9, 18:40 UTC
We understand that customers rely on Application Insights as a critical service and apologize for any impact this incident caused.-Eric Singleton





Recent Comments