
by Contributed | Nov 11, 2020 | Technology
This article is contributed. See the original author and article here.
Welcome to the MCAS Ninja Training!

Check out the MCAS Ninja Training video introduction here!
Have you been wanting to secure your cloud resources? Do you have agreements with non-Microsoft cloud applications? Do you want to share your cloud security knowledge and experience with others? Wait no longer, the Microsoft Cloud App Security (MCAS) Ninja training is here!
I am very pleased to introduce my MCAS Ninja training to you. MCAS has hundreds of amazing videos out there and it can sometimes be overwhelming with determining where to start and how to progress through different levels. Over the last few months, I’ve gone through all these and created this repository of training materials in an ascending order… all in one central location! Please let me know what you think in the comments.
In terms of overall structuring, the training sessions are split into three different knowledge levels:
· Beginner (Fundamentals)
· Intermediate (Associate)
· Advanced (Expert)
Module
|
Description
|
1. Level 1: Beginner (Fundamentals)
|
Introduction to Microsoft Cloud App Security, licensing, portal navigation, policy basics, and overall definitions.
|
2. Level 2: Intermediate (Associate)
|
Capability demos, automatic governance, overall deployment, and integrations.
|
3. Level 3: Advanced (Expert)
|
Power automate, 3rd party IdP integration, and advanced use case scenarios.
|
In addition, after each module/level, there will be a knowledge check based on the training material you’d have just finished! Since there’s a lot of content, the goal of the knowledge checks is to help you determine if you were able to get some of the major key takeaways. Lastly, there’ll be a fun certificate issued at the end of the training: Disclaimer: This is not an official Microsoft certification and only acts as a way of recognizing your participation in this training content.
Lastly, this training will be updated on a quarterly basis to ensure you all have the latest and greatest material!
Let us know what you think!
P.S I wanted to give my colleague, @DanEdwards, a huge kudos for helping me automate the certificate app and knowledge check! Thank you, Dan!
Legend/Acronyms
|
(D)
|
Microsoft Documentation
|
(V)
|
Video
|
(B)
|
Blog
|
MCAS
|
Microsoft Cloud App Security
|
RBAC
|
Role-based access control
|
MDATP
|
Microsoft Defender Advanced Threat Protection
|
AATP
|
Azure Advanced Threat Protection
|
ATP
|
Advanced Threat Protection
|
AIP
|
Azure Information Protection
|
ASC
|
Azure Security Center
|
AAD
|
Azure Active Directory
|
CASB
|
Cloud Access Security Broker
|
MTP
|
Microsoft Threat Protection
|
GCC
|
Government Community Cloud
|
GCC-H
|
Government Community Cloud High
|
Note: Threat protection product names from Microsoft are changing. Read more about this and other updates here. We’ll be updating names in products and in the docs soon.
Microsoft 365 Defender (previously Microsoft Threat Protection)
Microsoft Defender for Endpoint (previously Microsoft Defender Advanced Threat Protection)
Microsoft Defender for Office 365 (previously Office 365 Advanced Threat Protection)
Microsoft Defender for Identity (previously Azure Advanced Threat Protection)
MCAS Ninja Training
Level: Beginner (Fundamentals) (Video Introduction)
- Community Information
- MCAS Tech Community
- This is a Microsoft Cloud App Security (MCAS) Tech Community space that provides an opportunity to connect and discuss the latest news, updates, and best practices with Microsoft professionals and peers.
- Understanding CASBs
- Top 20 Use Cases for CASBs (D)
- This document provides use cases which can be leveraged as a starting point during a proof of concept (POC), or as you’re getting ready to deploy your CASB solution looking for ways to prioritize your deployment component.
- MCAS Best Practices (D)
- This article provides best practices for protecting your organization by using Microsoft Cloud App Security. These best practices come from our overall experience working with Cloud App Security and from the experiences from customers like you.
- MCAS Introduction
- MCAS Licensing (V)*subject to change*
- Questions on MCAS licensing? Contact your Microsoft reseller or Microsoft Partner.
- MCAS License Datasheet (D)
- Differences between MCAS and OCAS (D)
- Differences between MCAS and CAD (D)
- Microsoft Cloud App Security Introduction (V)
- This is an introductory video presentation of Microsoft’s Cloud Access Security Broker (CASB): Microsoft Cloud App Security (MCAS).
- Initial Settings
- Configure IP Addresses (V)
- This video shows you how to add your organization’s IP address ranges to remove complexities from policy creation, investigation, and improve the accuracy of your alerts.
- For more information, check out this article. (D)
- Import User Groups (V)
- This video shows you how to important user groups into MCAS to help create relevant policies.
- For more information, check out this article. (D)
- Configure Admin Roles (V)
- In this video, we show you how to configure admin roles and setup role-based access controls.
- For more information, check out this article. (D)
- Configure MSSP Access (V)
- The above video walks you through adding Managed Security Service Provider (MSSP) access to MCAS.
- Cloud Discovery
- Dashboard Basics (D)
- The above article gives an overview on how to work with MCAS daily while providing a few tips on how to navigate the portal.
- Discovered Apps (D)
- The above article provides guidance on how to work with discovered apps and the steps to take to dive deep into what the dashboard offers.
- App Risk Scoring (V)
- This video provides an overview on how MCAS evaluates the risk over discovered SaaS apps in your environment.
- For more information, check out this article. (D)
- MCAS App Connectors (V)
- This video provides a brief introduction on MCAS 3rd party SaaS connectors.
- For more information, check out this article. (D)
- Using the Cloud App Discovery Feature (V)
- This is a video overview of MCAS and its discovery functions.
- Information Protection and Real-time Controls
- Connect Office 365 (V)
- This video demonstrates how to connect Office 365 to Microsoft Cloud App Security and enable our powerful capabilities across DLP, Threat Protection, and more.
- Configure AAD with MCAS Conditional Access App Control (V)
- In this video, we walk you through how to configure real-time monitoring and control across your cloud apps leveraging our powerful, native integration with Azure AD Conditional Access.
- What is Conditional Access App Control? (V)
- In this video, we explore what Conditional Access App Control is, how to deploy and configure it, and testing of a scenario (Microsoft Teams).
- Block Sensitive Information Downloads (D)
- The above article walks you through a tutorial on how to create a session policy to block the download of sensitive information.
- Threat Detection
- Threat Detection Overview (V)
- The above video walks you through MCAS’s threat detection capabilities that allow you to identify advanced attackers and insider threats.
- User and Entity Behavior Analytics (V)
- This video provides a brief overview on User & Entity Behavior Analytics (UEBA) in MCAS.
- Discover and Mange risky OAuth applications (V)
- This video discusses how MCAS can help you identify when users authorize OAuth apps, detect risky apps, and revoke access to risky apps.
Level: Beginner (Fundamentals) Knowledge Check
Level: Intermediate (Associate) (Video Introduction)
- Overview
- Microsoft Cloud App Security: Overview (V)
- This is an overview video discussing the different pillars and configuration steps for MCAS with a demo.
- Cloud Discovery
- Cloud Discovery Interactive Guide (V)
- This interactive guide walks you through discovering, protecting, and controlling your apps.
- Cloud Discovery Policies (D)
- The above article walks you through creating cloud discovery policies within your MCAS environment.
- MCAS and MDATP Integration (V)
- This video walks through the process of Integrating MDATP and MCAS and how simple the integration is—without requiring extra agents or proxies.
- For more information, check out this article. (D)
- Log Collector Configuration (V)
- An overview on using the log collector to enable cloud discovery and a walk-through on deployment.
- For guidance on log collector deployment, choose your deployment mode here and follow the accompanying steps. (D)
- Integrate with Zscaler (D)
- If you work with both Cloud App Security and Zscaler, you can integrate the two products to enhance your security Cloud Discovery experience.
- Integrate with iboss (D)
- If you work with both Cloud App Security and iboss, you can integrate the two products to enhance your security Cloud Discovery experience.
- Integrate with Corrata (D)
- If you work with both Cloud App Security and Corrata, you can integrate the two products to enhance your security Cloud Discovery experience for mobile app use.
- Information Protection and Real-Time Controls
- Protecting Storage Apps and Malware Detection (V)
- This video shows you how MCAS can help you protect your cloud storage apps and ensure that they are not infected with malware.
- For more information, please see this article. (D)
- Configuring a read-only mode for external users (V)
- This video walks you through one of the many use-cases focused on external users using Conditional Access App Control, our reverse proxy solution.
- Block unauthorized browsers form accessing corporate web apps (V)
- A video detailing the policy configuration required to block unauthorized browsers from accessing corporate web applications.
- Using Admin Quarantine to investigate files (D)
- The above article is a tutorial helping you use admin quarantine to protect your files.
- Automatically apply labels to your sensitive files (D)
- The above article is a tutorial walking you through applying a label to a sensitive file.
- Information Protection Policies (D)
- The above article walks you through creatin information protection policies within your MCAS environment.
- Threat Detection
- Threat Policies (D)
- The above article walks you through creatin threat protection policies within your MCAS environment.
- Azure Advanced Threat Protection Integration
- How Azure ATP integrates with MCAS (D)
- The above article is designed to help you understand and navigate the enhanced investigation experience in MCAS with Azure ATP.
- Detect Threats and Manage Alerts (V)
- The interactive guide above walks you through the steps of managing threats and alerts.
- Malware Hunting and Automatic Remediation (V)
- This video provides a brief overview of Malware Hunting in SaaS Apps using MCAS.
Level: Intermediate (Associate) Knowledge Check
Level: Advanced (Expert) (Video Introduction)
- Power Automate Blog Series (B)
- Triage Infrequent Country Alerts using Power Automate and MCAS (V)
- A video walk- through on creating a new Power Automate Flow to automate the triage of Infrequent Country alerts in MCAS (Threat Protection Pillar).
- Request user validation to reduce your SOC workload (V)
- A vide walk-through on using Power Automate Flow to request user validation for file sharing (Data Protection Pillar).
- Request for Manager Action (V)
- This video walks you through using Power Automate Flow to request manager validation for their team.
- Step-by-step guidance (B)
- Auto-disable malicious inbox rules using MCAS & Power Automate (V)
- This video walks you through a new Power Automate Flow on how to remove malicious inbox rules detected in your cloud environment.
- 3rd Party IdP Configuration
- PingOne (D)
- This document walks you through integrating PingOne with MCAS for Conditional Access App Control using Salesforce as an example.
- ADFS (Coming soon!)
- Okta (Coming soon!)
- Conditional Access App Control steps for non-Microsoft SAAS applications
- Workplace for Facebook (V)
- Box (V)
- Slack (V)
- SIEM Integrations
- Connect Azure Sentinel (V)
- This video details how to connect Azure Sentinel (Microsoft’s SIEM + SOAR product) to MCAS.
- Azure Sentinel Entities Enrichment (Users) (V)
- This video looks at how you can use the provided playbooks to enrich your impacted user profiles, and then consume it in Sentinel, ServiceNow, or Postman.
- Microsoft CAS Infrequent Country triage with Azure Sentinel and Logic Apps (V)
- This video walks you through the deployment of a playbook to using it to triage your Azure Sentinel incidents.
- Connect a 3rd Party SIEM (V)
- This video details how to connect a third party SIEM to MCAS.
- Advanced Scenarios and Guidance
- Indicators of Compromise (V)
- This video walks you through how to create custom Indicators of Compromise in MCAS.
- MCAS and Microsoft Threat Protection (V)
- A video guide on how Microsoft is unifying our threat products.
- MCAS API Documentation (D)
- The above article describes how to interact with Cloud App Security over HTTPS.
- Configuring a Log Collector behind a Proxy (D)
- The above article walks you through further configuration to ensure your log collector works when behind a proxy.
- Ninja Training Blog Series (B)
- This blog series dives into partner specific topics (such as ideas for managed services, reporting dashboards, playbooks, and more) that you can use to help your clients be successful with Microsoft Cloud App Security.
- MCAS Data Protection Blog Series (B)
- This blog goes through different data protection scenarios based on questions the CxE team has received from customers.
- Securing Administrative Access to Microsoft Cloud App Security and Defender for Identities (B)
- This blog provides guidance on how to configure Azure AD Conditional Access to secure administrative access to Microsoft Cloud App Security (MCAS) and Defender for Identities (formerly Azure ATP).
- Limiting Inherited Roles from Azure Active Directory in MCAS (B)
- This blog goes over a customer scenario for MCAS and the steps that can be taken to meet their requirements on limiting inherited AAD roles’ accesses in MCAS.
- Important Announcements
- Unified Data Loss Prevention Post Announcement (B)
- This blog details all the latest and greatest information protection improvements including the new changes for MCAS.
- MCAS is removing non-secure cipher suites (B)
- This blog provides an update on the non-secure cipher suites no longer supported by MCAS and the steps to take to prepare for this change.
- Unified Labeling is now generally available in GCC and GCC-H environments (B)
- This blog provides an update that information protection is available in our government tenants.
Level: Advanced (Expert) Knowledge Check
Once you’ve finished the training and the knowledge checks, please go to our attestation portal to auto-generate your certificate (Coming Soon!).
by Contributed | Nov 11, 2020 | Technology
This article is contributed. See the original author and article here.
Imagine you build an API only to realize later down the road, your documentation for it isn’t kept up to date and you are now spending more time trying to figure how it works than it took to build. Sound familiar? This is one of the common pitfalls of a code-first approach to APIs. There are two key approaches to building APIs:
- Code-first: coding the API directly from the requirements and then generating an API definition document
- Design-first: defining an API first and then implementing backend services based on the agreed API design
If you were to follow a design-first approach, you can design your API in API Management and export it to an OpenAPI specification file, which could be used to bring organizational alignment and serve as a guidance for implementing backend services that support the API logic and client applications that consume the API.
To support the design-first approach, we recently released an update to our Azure Functions and API Management Visual Studio Code extensions that lets you generate Azure Function apps by importing an OpenAPI specification. The same functionality is available via the command line.
Functions provide not only ready-made scaffolding for writing an API but all the necessary hosting.
Functions allow your API to dynamically scale up or down depending on the number of requests. Since it is consumption-based, you’re only charged when an HTTP endpoint is called, and you aren’t paying for idle resources as you would if you were using a VM as a host.
Example Scenario
Imagine a scenario where you are creating an API for a food delivery service. After gathering the business requirements, you begin developing the API. Once the API is built, dependent teams start testing, documenting, and providing feedback. But while gathering feedback you realize you need to pivot and rewrite a significant portion of your API which is going to push back the project. That’s where the code-first approach falls short.
What if instead of developing the API, you started with an API description to establish a shared understanding of how the API is supposed to function. During the process of creating the description you start asking questions like: What functionality will the API have? What will the developer experience be like? What data will it expose and in what format? How will we add new functionality in the future? To answer some of these questions you need to bring in other teams to provide input. You can now get earlier validation on the API functionality from various stakeholders while the cost of making changes are low.
In addition to gathering feedback earlier in the API development process, teams that are consumers of the API can begin testing and integration before the business logic is complete. Dependent teams are not blocked by another team’s progress and can work in parallel during API development process.
Which approach should I use?
Determining what approach to use will depend on your business needs and use case. The code-first approach is a more traditional approach to building APIs, but the popularity of API definition formats has led to the growing support of the design-first methodology.
Design-first allows consumers to better understand of how to use your API and ensures consistency across APIs.
Key benefits of a design-first approach are:
- Accelerates API development by establishing key details in the design phase and allowing development teams to work in parallel
- Results in a transparent API documentation to stakeholders
- Let’s you focus on the API consumer experience and the business logic that the API fulfills, detaching it from the technical implementation
- Helps to create a strong foundation for the API, which may reduce the number of breaking changes in future
Building a REST API in three steps
In three easy steps you can design and build your API’s without writing a bunch of lines of code and documentation.
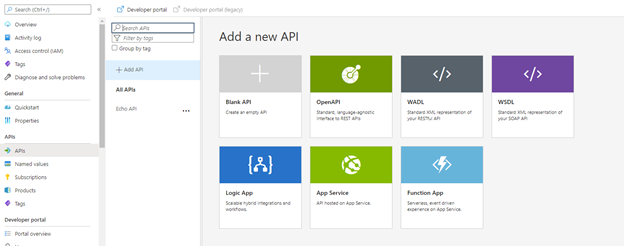
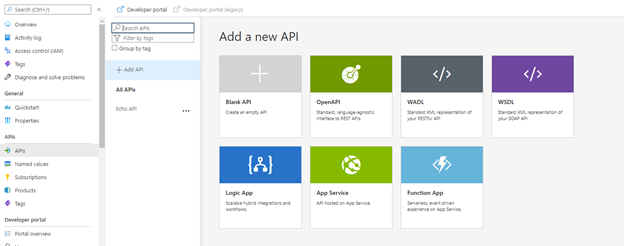
Step 1: Create an API definition using API Management
In API Management, choose API’s from the left menu, and then select OpenAPI.
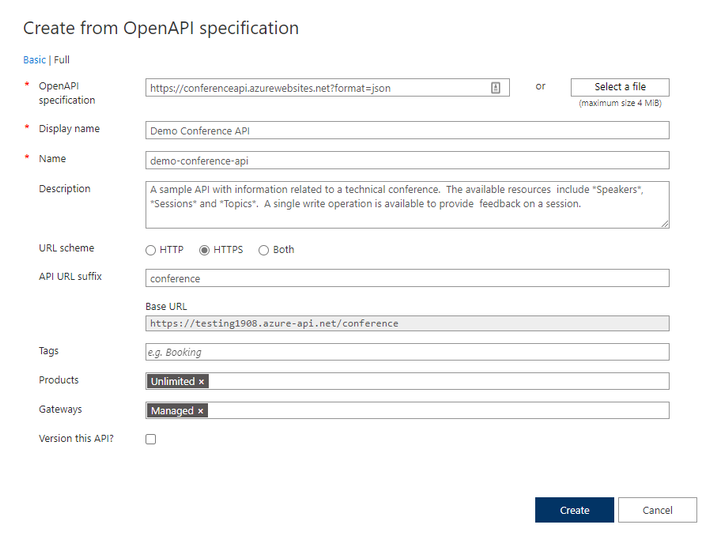
In the Create from OpenAPI specification window, select Full. Fill in your API values in the necessary fields and select create. Here is a sample Open API file you can use.
Step 2: Generate function apps from Open API Specifications
Now that you have created an OpenAPI specification file you can import the specification via the API Management or Azure Functions VS Code extensions to create the scaffolding for your API.
Getting started with VS Code
Before you get started there’s a few things you will need:
- Visual Studio Code
- Latest version of the Azure Functions extension or API Management Extension
- You will need the correct language runtimes installed for the type of function app you want to create. The languages we currently support are C#, Python, TypeScript, and Java. Support for JavaScript and PowerShell coming in the near future.
- AutoRest (Microsoft’s OpenAPI specification generator)
From API Management Extension
In your VS code settings make sure you enable the API Management extension to create Functions.
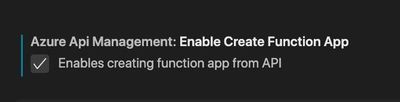
In the API management VS code extension right click on the API definition you would like to use and select scaffold Azure Functions.
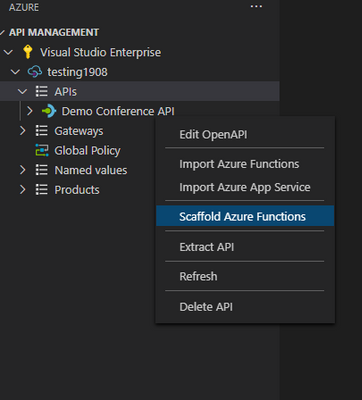
Select your language of choice and where you would like to create the functions.
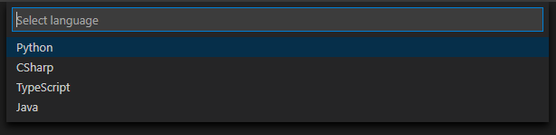
Watch as it starts to generate function apps from your specification file!
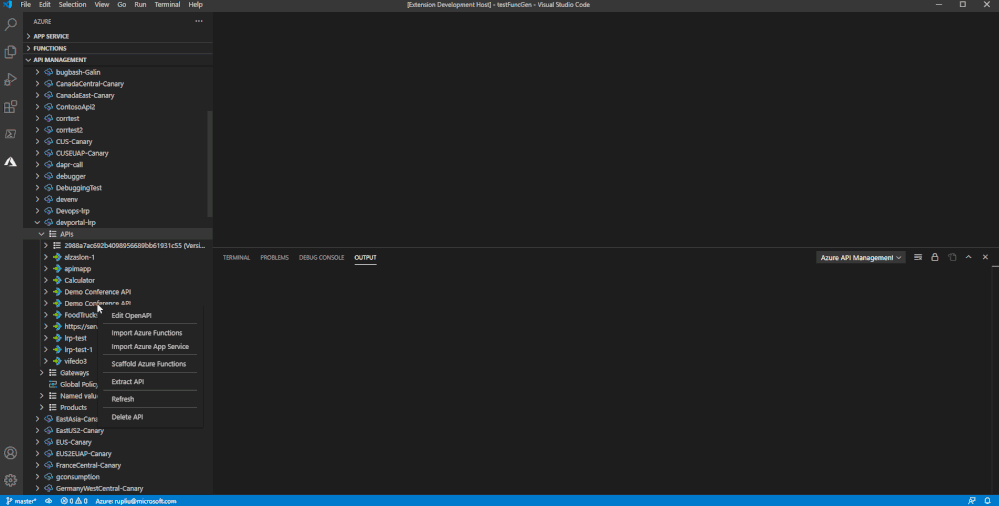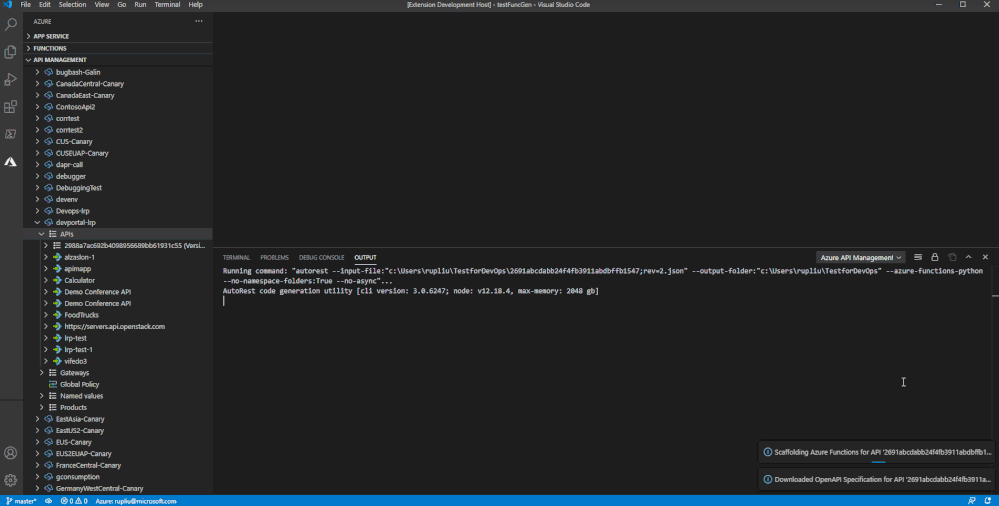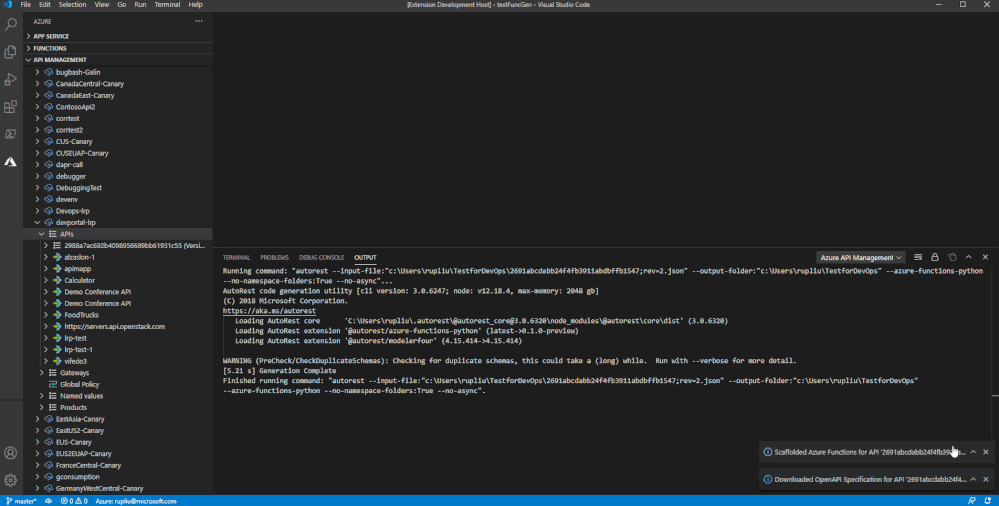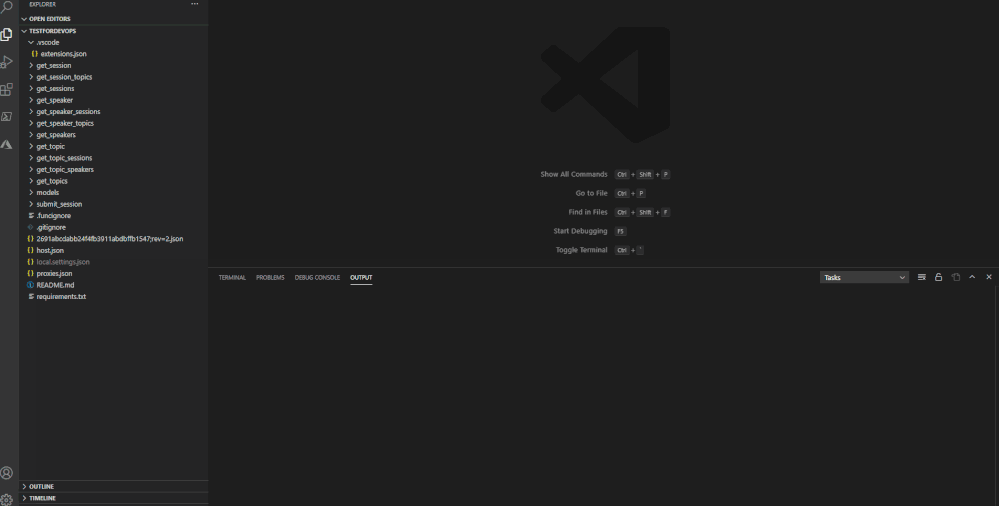
From Azure Functions Extension
You can also use the Azure Functions extension to import a specification to create the scaffolding for your API.
Create a new function app and choose your language of choice (TypeScript, Python, C#).
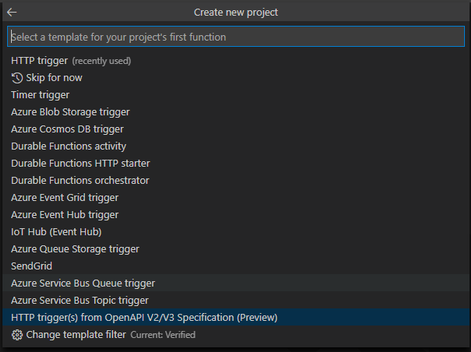
Select the HTTP trigger(s) from OpenAPI V2/V3 Specification template.
Select your OpenAPI specification file (You can find some samples to try here).
Step 3: Add your business logic
Once it completes you will see it has automatically generated all the necessary functions for your API, preconfigured based on the OpenAPI specification. All you need to do now is add your business logic to each function/route and deploy to Azure.
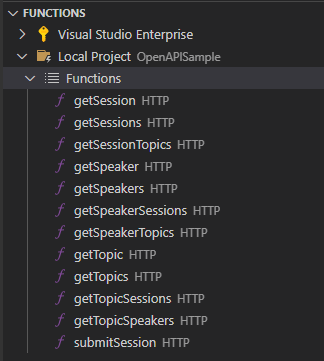
Getting started with CLI
You can also use the CLI as well to create the scaffolding for your API’s.
autorest --azure-functions-csharp
--input-file:/path/to/spec.json
--output-folder:./generated-azfunctions
--version:3.0.6314
--namespace:Namespace
Check out the GitHub repo for more information on how to get started.
Summary
The design-first approach to building APIs comes with many benefits, saving you time and effort in bringing your APIs to market. Now you can reap the benefits even more by generating the Azure Functions scaffolding for your APIs from OpenAPI definition in Visual Studio Code. If you have an existing API hosted on Azure and you’re interested in exploring a serverless architecture or consumption-based billing model, this new capability is a fast track for getting started with Azure Functions.
To learn more about building serverless APIs with Azure Functions and Azure API Management, check out a new workshop we recently published on GitHub.
by Contributed | Nov 11, 2020 | Technology
This article is contributed. See the original author and article here.
We are delighted to announce the initial release of solutions to run Oracle WebLogic Server (WLS) on the Azure Kubernetes Service (AKS) developed with the WebLogic team as part of a broad-ranging partnership between Microsoft and Oracle. The partnership includes joint support for a range of Oracle software running on Azure, including Oracle WebLogic, Oracle Linux, and Oracle DB, as well as interoperability between Oracle Cloud Infrastructure (OCI) and Azure.
WLS is a key component in enabling enterprise Java workloads on Azure. This initial release certifies that WebLogic is fully enabled to run on AKS and includes a set of instructions, samples, and scripts intended to make it easy to get started with production ready deployments. Evaluate the solutions for full production usage and reach out to collaborate on migration cases.
Solution Details and Roadmap
WLS on Azure Linux Virtual Machines solutions were announced in September covering several important use cases, such as base image, single working instance, clustering, load-balancing via Azure App Gateway, database integration, and security via Azure Active Directory. This current release enables basic support for running WebLogic clusters on AKS reliably through the WebLogic Operator, offering a wider set of options for deploying WLS on Azure.
WebLogic Server clusters are fully enabled to run on Kubernetes via the WebLogic Kubernetes Operator. The Operator simplifies the management and operation of WebLogic domains and deployments on Kubernetes by automating manual tasks and adding additional operational reliability features. Alongside the WebLogic team, Microsoft has tested, validated and certified that the Operator runs well on AKS. Beyond certification and support, Oracle and Microsoft provide detailed instructions, scripts, and samples for running WebLogic Server on AKS. These solutions, incorporated into the Operator itself, are designed to make production deployments as easy and reliable as possible.
The WLS on AKS solutions allow a high degree of configuration and customization. The solutions will work with any WLS version that supports the Operator, such as 12.2.1.3 and 12.2.1.4, and use official WebLogic Server Docker images provided by Oracle. Failover is available via Azure Files accessed through Kubernetes persistent volume claims, and Azure Load Balancers are supported when provisioned using a Kubernetes Service type of ‘LoadBalancer’.
The solutions enable a wide range of production-ready deployment architectures with relative ease, and you have complete flexibility to customize your deployments. After deploying your applications, you can take advantage of a range of Azure resources for additional functionality.
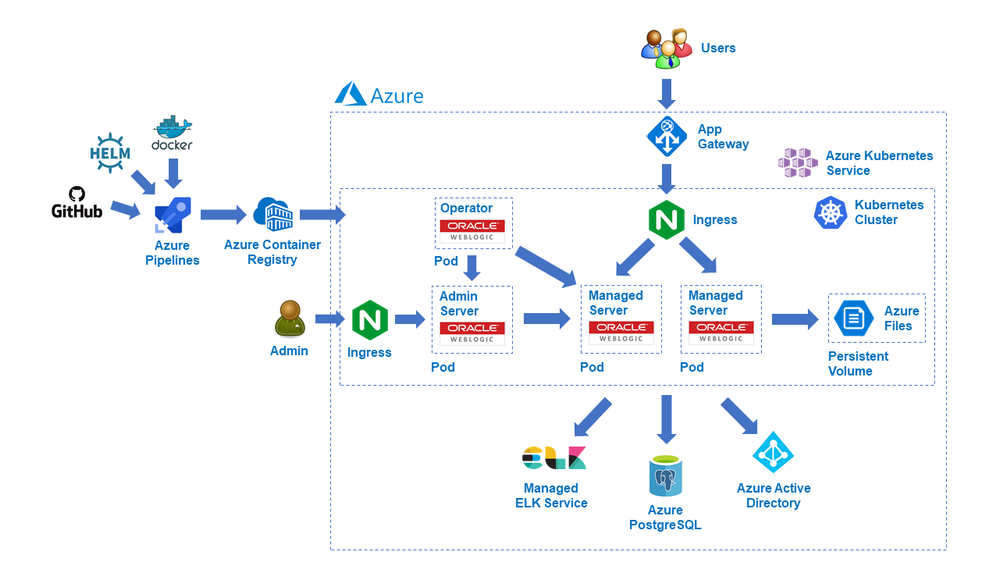
The solutions currently assume deploying the domain outside the Docker image and using the standard Docker images from Oracle; we will enable custom images with your domain inside a Docker image in the next few months. Further ease-of-use and Azure service integrations will be possible next year via Marketplace offerings mirroring the WSL on Azure Virtual Machines solutions.
These offers are Bring-Your-Own-License. They assume you have already procured the appropriate licenses with Oracle and are properly licensed to run WLS on Azure. The solutions themselves are available free of charge as part of the Operator.
Get started with WLS on AKS
Explore the solutions, provide feedback, and stay informed of the roadmap. You can also take advantage of hands-on help from the engineering team behind these offers. The opportunity to collaborate on a migration scenario is completely free while the offers are under active initial development.
by Contributed | Nov 11, 2020 | Technology
This article is contributed. See the original author and article here.
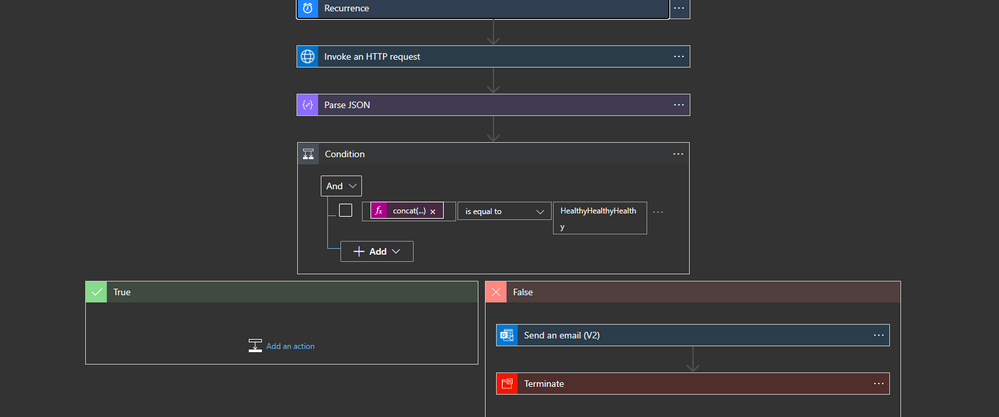
Currently, the ISE does not provide any alert in case of any events that led to having unhealthy subnet(s)
the provided logic app will call HTTP management endpoint from azure
How to build the logic app
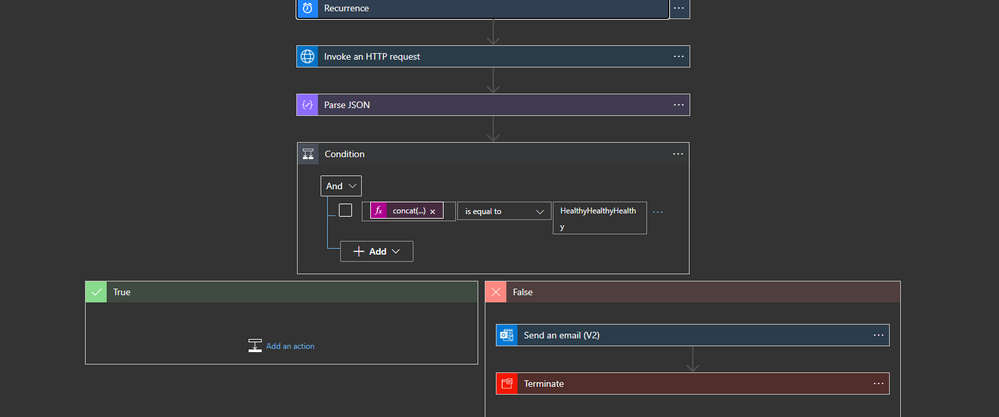
the logic app will run periodically and get the content of the endpoint
https://management.azure.com/subscriptions/../resourceGroups/../providers/Microsoft.Logic/integrationServiceEnvironments/../health/network?api-version=2018-07-01-preview
I am using the action HTTP with Azure AD
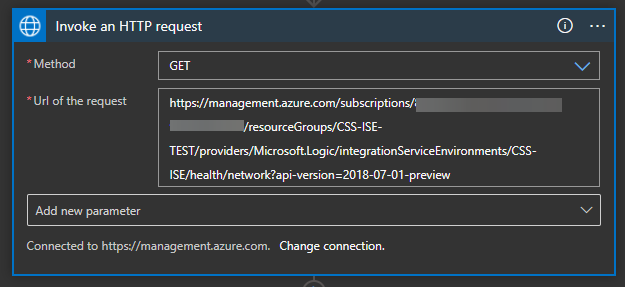
the action will get a JSON content that shows the net health status
{
"CSS-ISE-Sub4": {
"networkDependencyHealthState": "Healthy",
"outboundNetworkDependencies": [
{
"category": "AzureStorage",
"displayName": "Azure Storage",
"endpoints": [
{
"domainName": "bvzkkzolbtymq00by.blob.core.windows.net",
"ports": [
"80",
"443"
],
"accessibility": "Available"
},
{
"domainName": "bvzkkzolbtymq00by.queue.core.windows.net",
"ports": [
"80",
"443"
],
"accessibility": "Available"
},
{
"domainName": "bvzkkzolbtymq00by.table.core.windows.net",
"ports": [
"80",
"443"
],
"accessibility": "Available"
},
{
"domainName": "bvzkkzolbtymqregby.blob.core.windows.net",
"ports": [
"80",
"443"
],
"accessibility": "Available"
},
{
"domainName": "bvzkkzolbtymqregby.queue.core.windows.net",
"ports": [
"80",
"443"
],
"accessibility": "Available"
},
{
"domainName": "bvzkkzolbtymqregby.table.core.windows.net",
"ports": [
"80",
"443"
],
"accessibility": "Available"
},
{
"domainName": "bvzkkzolbtymqaftsby.blob.core.windows.net",
"ports": [
"80",
"443"
],
"accessibility": "Available"
},
{
"domainName": "bvzkkzolbtymqaftsby.queue.core.windows.net",
"ports": [
"80",
"443"
],
"accessibility": "Available"
},
{
"domainName": "bvzkkzolbtymqaftsby.table.core.windows.net",
"ports": [
"80",
"443"
],
"accessibility": "Available"
}
]
},
{
"category": "AzureActiveDirectory",
"displayName": "Azure Active Directory",
"endpoints": [
{
"domainName": "graph.windows.net",
"ports": [
"80",
"443"
],
"accessibility": "Available"
}
]
},
{
"category": "SSLCertificateVerification",
"displayName": "SSL Certificate Verification",
"endpoints": [
{
"domainName": "ocsp.msocsp.com",
"ports": [
"80",
"443"
],
"accessibility": "Available"
},
{
"domainName": "mscrl.microsoft.com",
"ports": [
"80",
"443"
],
"accessibility": "Available"
},
{
"domainName": "crl.microsoft.com",
"ports": [
"80",
"443"
],
"accessibility": "Available"
},
{
"domainName": "www.microsoft.com",
"ports": [
"80",
"443"
],
"accessibility": "Available"
},
{
"domainName": "crl3.digicert.com",
"ports": [
"80",
"443"
],
"accessibility": "Available"
},
{
"domainName": "ocsp.digicert.com",
"ports": [
"80",
"443"
],
"accessibility": "Available"
},
{
"domainName": "cacerts.digicert.com",
"ports": [
"80",
"443"
],
"accessibility": "Available"
},
{
"domainName": "www.thawte.com",
"ports": [
"80",
"443"
],
"accessibility": "Available"
}
]
},
{
"category": "DiagnosticLogsAndMetrics",
"displayName": "Diagnostic Logs And Metrics",
"endpoints": [
{
"domainName": "az-prod.metrics.nsatc.net",
"ports": [
"443"
],
"accessibility": "Available"
}
]
},
{
"category": "IntegrationServiceEnvironmentConnectors",
"displayName": "Integration Service Environment Connectors",
"endpoints": [
{
"domainName": "flow-bvzkkzolbtymq-by-apim-runtime.westus.environments.microsoftazurelogicapps.net",
"ports": [
"443"
],
"accessibility": "Available"
}
]
}
],
"outboundNetworkHealth": {
"state": "Healthy"
}
},
"CSS-ISE-Sub2": {
"networkDependencyHealthState": "Healthy",
"outboundNetworkDependencies": [
{
"category": "SQL",
"displayName": "SQL",
"endpoints": [
{
"domainName": "apirpsql2ez4bajpcjjlkmaa.database.windows.net",
"ports": [
"1443"
],
"accessibility": "Available"
}
]
},
{
"category": "RecoveryService",
"displayName": "Recovery Service",
"endpoints": [
{
"domainName": "https://global.metrics.nsatc.net/",
"ports": [
"1886"
],
"accessibility": "Available"
}
]
},
{
"category": "RecoveryService",
"displayName": "Recovery Service",
"endpoints": [
{
"domainName": "https://prod3.metrics.nsatc.net:1886/RecoveryService",
"ports": [
"1886"
],
"accessibility": "Available"
}
]
},
{
"category": "AzureStorage",
"displayName": "Azure Storage",
"endpoints": [
{
"domainName": "apimstufsse40dnm8wl2aozs.blob.core.windows.net",
"ports": [
"443"
],
"accessibility": "Available"
},
{
"domainName": "apimstufsse40dnm8wl2aozs.file.core.windows.net",
"ports": [
"445"
],
"accessibility": "Available"
},
{
"domainName": "apimstufsse40dnm8wl2aozs.queue.core.windows.net",
"ports": [
"443"
],
"accessibility": "Available"
},
{
"domainName": "apimstufsse40dnm8wl2aozs.table.core.windows.net",
"ports": [
"443"
],
"accessibility": "Available"
},
{
"domainName": "gcs.prod.monitoring.core.windows.net",
"ports": [
"443"
],
"accessibility": "Available"
}
]
}
],
"outboundNetworkHealth": {
"state": "Healthy"
}
},
"CSS-ISE-Sub3": {
"networkDependencyHealthState": "Healthy",
"outboundNetworkDependencies": [
{
"category": "AzureStorage",
"displayName": "Azure Storage",
"endpoints": [
{
"domainName": "blob.core.windows.net",
"ports": [
"80",
"443"
],
"accessibility": "Available"
},
{
"domainName": "queue.core.windows.net",
"ports": [
"80",
"443"
],
"accessibility": "Available"
},
{
"domainName": "table.core.windows.net",
"ports": [
"80",
"443"
],
"accessibility": "Available"
},
{
"domainName": "file.core.windows.net",
"ports": [
"80",
"443"
],
"accessibility": "Available"
}
]
},
{
"category": "SQL",
"displayName": "Azure SQL Database",
"endpoints": [
{
"domainName": "database.windows.net",
"ports": [
"1433"
],
"accessibility": "Available"
}
]
},
{
"category": "AzureManagement",
"displayName": "Azure Management",
"endpoints": [
{
"domainName": "management.core.windows.net",
"ports": [
"443"
],
"accessibility": "Available"
},
{
"domainName": "admin.core.windows.net",
"ports": [
"443"
],
"accessibility": "Available"
},
{
"domainName": "management.azure.com",
"ports": [
"443"
],
"accessibility": "Available"
}
]
},
{
"category": "AzureActiveDirectory",
"displayName": "Azure Active Directory",
"endpoints": [
{
"domainName": "graph.windows.net",
"ports": [
"443"
],
"accessibility": "Available"
}
]
},
{
"category": "RegionalService",
"displayName": "Regional Service",
"endpoints": [
{
"domainName": "gr-prod-bay.cloudapp.net",
"ports": [
"443"
],
"accessibility": "Available"
},
{
"domainName": "az-prod.metrics.nsatc.net",
"ports": [
"443"
],
"accessibility": "Available"
}
]
},
{
"category": "SSLCertificateVerification",
"displayName": "SSL Certificate Verification",
"endpoints": [
{
"domainName": "ocsp.msocsp.com",
"ports": [
"80",
"443"
],
"accessibility": "Available"
},
{
"domainName": "mscrl.microsoft.com",
"ports": [
"80",
"443"
],
"accessibility": "Available"
},
{
"domainName": "crl.microsoft.com",
"ports": [
"80",
"443"
],
"accessibility": "Available"
},
{
"domainName": "www.microsoft.com",
"ports": [
"80",
"443"
],
"accessibility": "Available"
},
{
"domainName": "crl3.digicert.com",
"ports": [
"80",
"443"
],
"accessibility": "Available"
},
{
"domainName": "ocsp.digicert.com",
"ports": [
"80",
"443"
],
"accessibility": "Available"
},
{
"domainName": "cacerts.digicert.com",
"ports": [
"80",
"443"
],
"accessibility": "Available"
},
{
"domainName": "www.thawte.com",
"ports": [
"80",
"443"
],
"accessibility": "Available"
}
]
}
],
"outboundNetworkHealth": {
"state": "Healthy"
}
}
}
lots of information can be obtained from this JSON but we will be only interested in networkDependencyHealthState
After parsing the JSON we need to check the health of the three subnets
{
"and": [
{
"equals": [
"@concat(body('Parse_JSON')?['CSS-ISE-Sub2']?['networkDependencyHealthState'],body('Parse_JSON')?['CSS-ISE-Sub3']?['networkDependencyHealthState'],body('Parse_JSON')?['CSS-ISE-Sub4']?['networkDependencyHealthState'])",
"HealthyHealthyHealthy"
]
}
]
}
you can use multiple “Ands” as well
BTW parsing the JSON is not necessary
Last step
the last step will be sending an email and terminate the flow
by Contributed | Nov 11, 2020 | Technology
This article is contributed. See the original author and article here.
Welcome to the October update of Java Azure Tools! This is the first blog post for a new monthly update series for all the Azure tooling support we are providing for Java users, covering Maven/Gradle plugins for Azure, Azure Toolkit for IntelliJ/Eclipse and Azure Extensions for VS Code. Follow us and you will get more exciting updates in the future blogs.
In this update, you will see the brand new experience creating/deploying Azure Web Apps and Functions with IntelliJ. We will show you how to diagnose Web Apps with log streams, SSH, remote file explorer and profiling tools. Finally, we’d also like to show you the JBoss EAP support and Gradle project support. On to the update.
New experience in IntelliJ for Web Apps and Functions
The Azure Toolkit for IntelliJ 3.45.0 release brings major improvements on the Azure Web Apps and Azure Functions create and deploy workflow. Check out the example below for Web Apps:
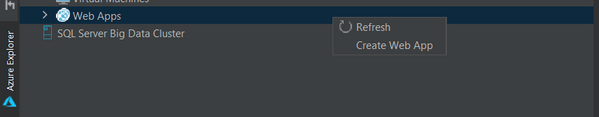
New entries from Azure Explorer
Now you can right click on Web Apps in Azure Explore and select Create Web App to open the app creation wizard, which was hidden in “Deploy to Azure Web Apps” wizard before.
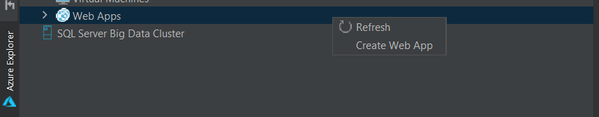
You can also right click on a existing Web App in Azure Explorer and select Deploy to open the deployment wizard. You now have the option to select projects or pre-built artifacts as you wish.
Simple mode, hints and validator in Web App creation
We are aiming at providing a more user friendly getting started experience for new Azure Web Apps Java users. As result when you click Create Web App you will only see 2 settings now: Name and Platform. You can accept default or select More Settings to configure details including resource group , pricing tier and so on. With validators on settings like app name, you no longer need to wait a deployment failed after minutes telling you that the app name is already taken. You can also hover on the question marks to learn more about what those settings mean.
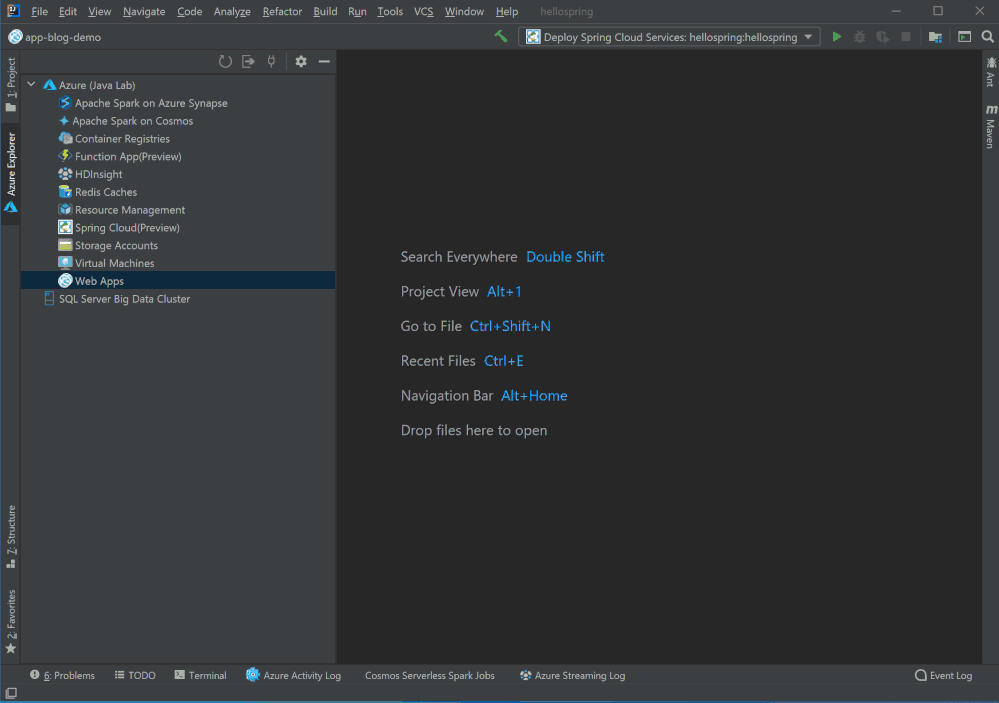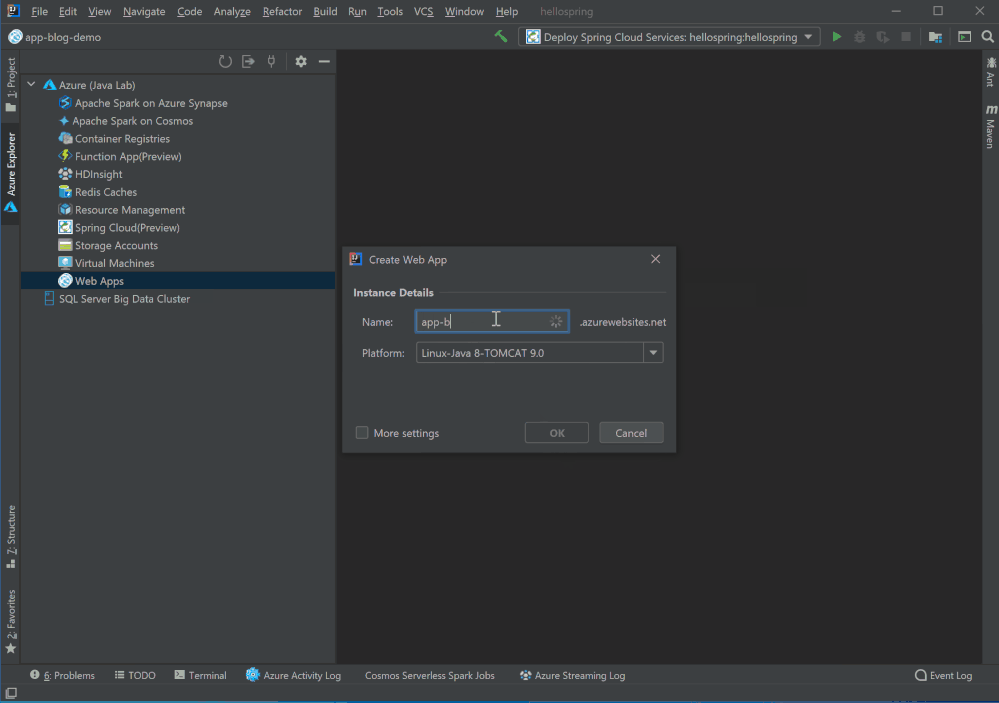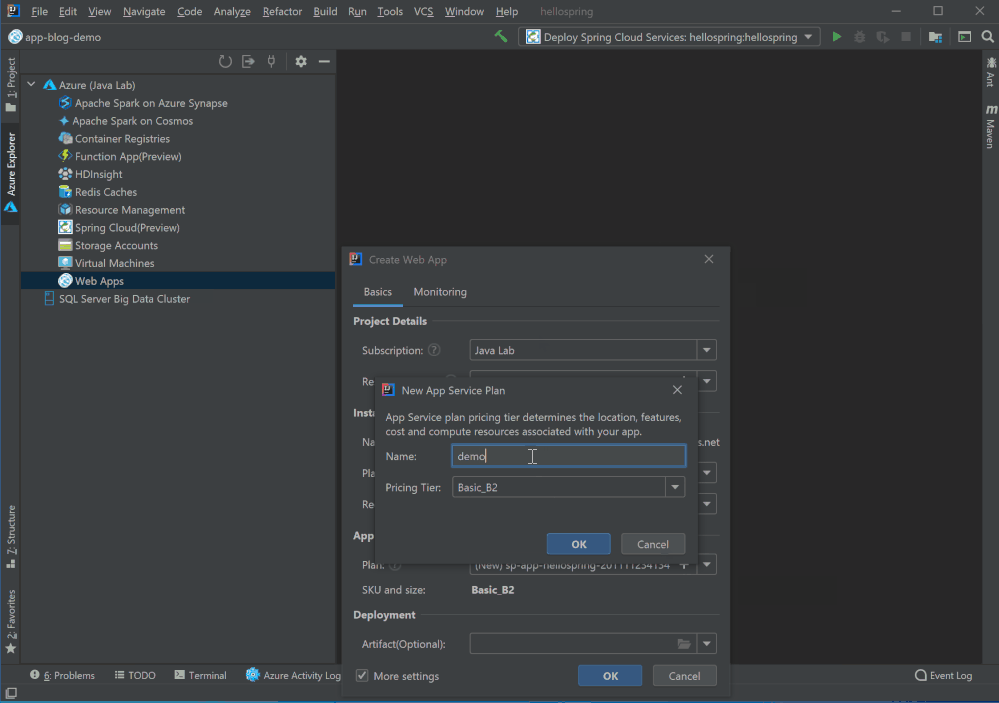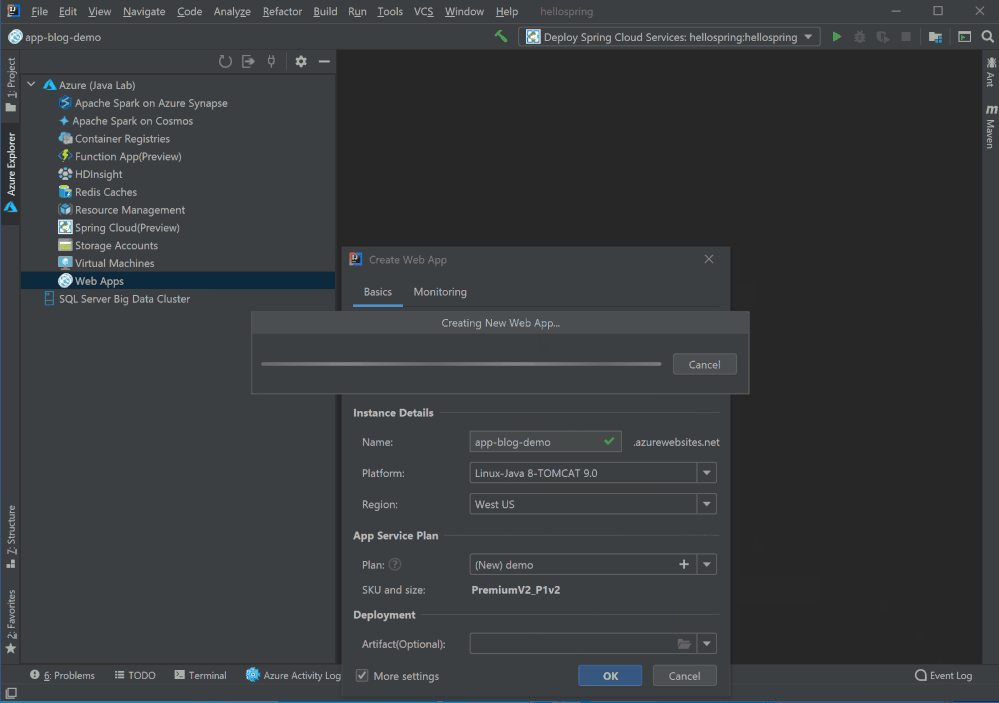
Web App Diagnostic
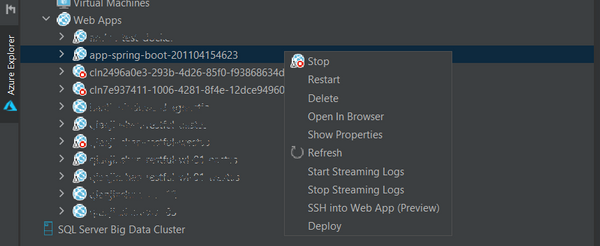
We are glad to announce the full diagnostic experience for Azure Web Apps starting from Azure Toolkit for IntelliJ v3.45.0. You can now easily troubleshoot your Web App on Azure with powerful features added recently:
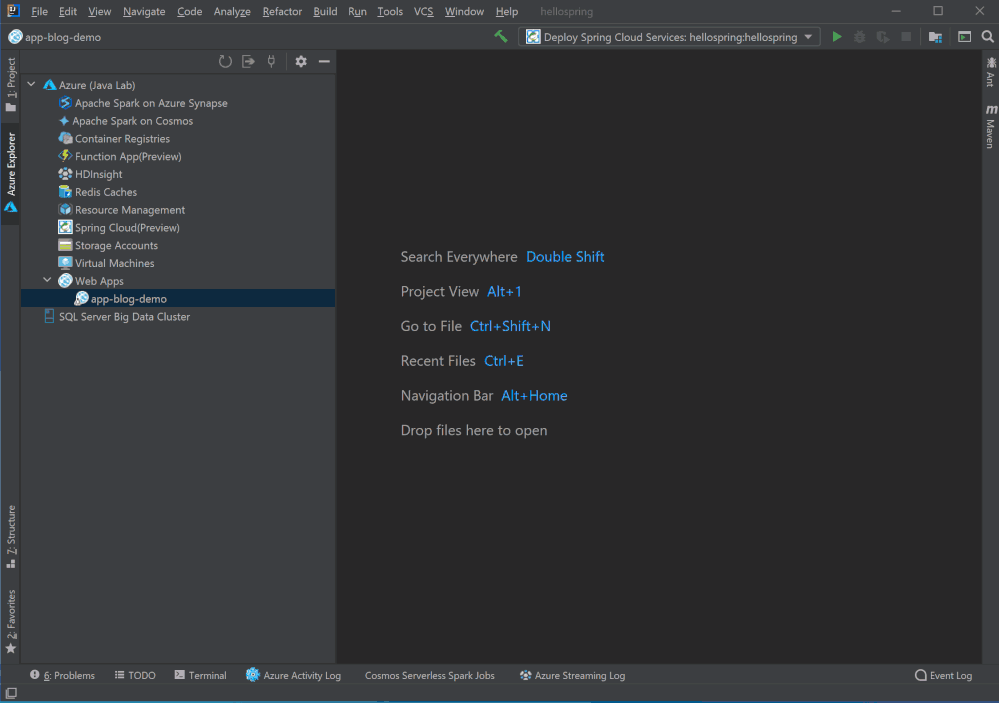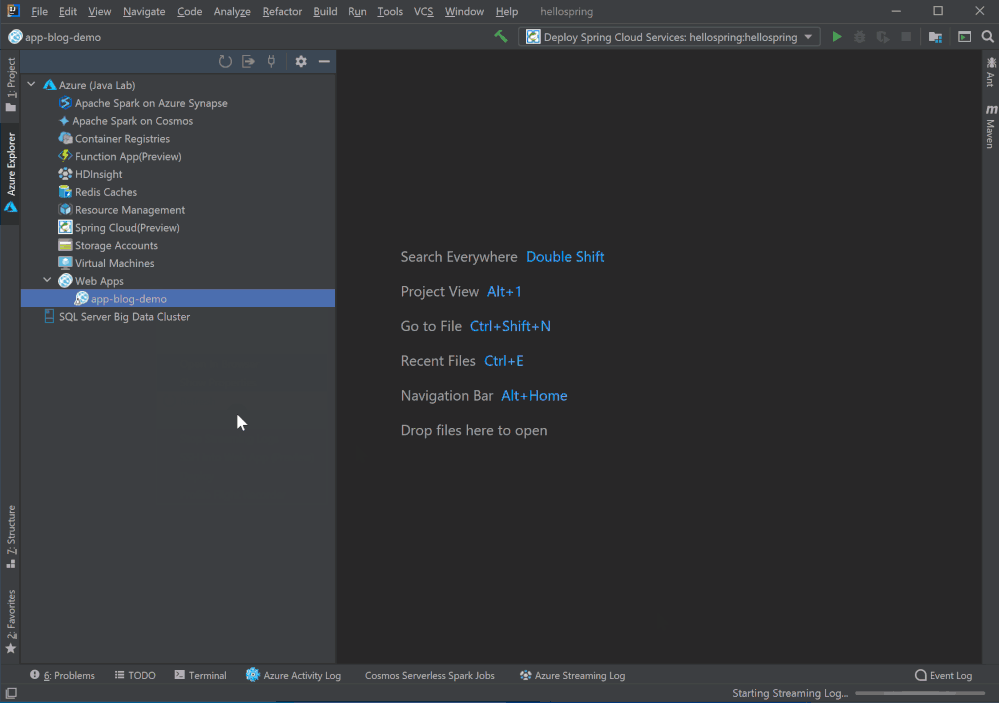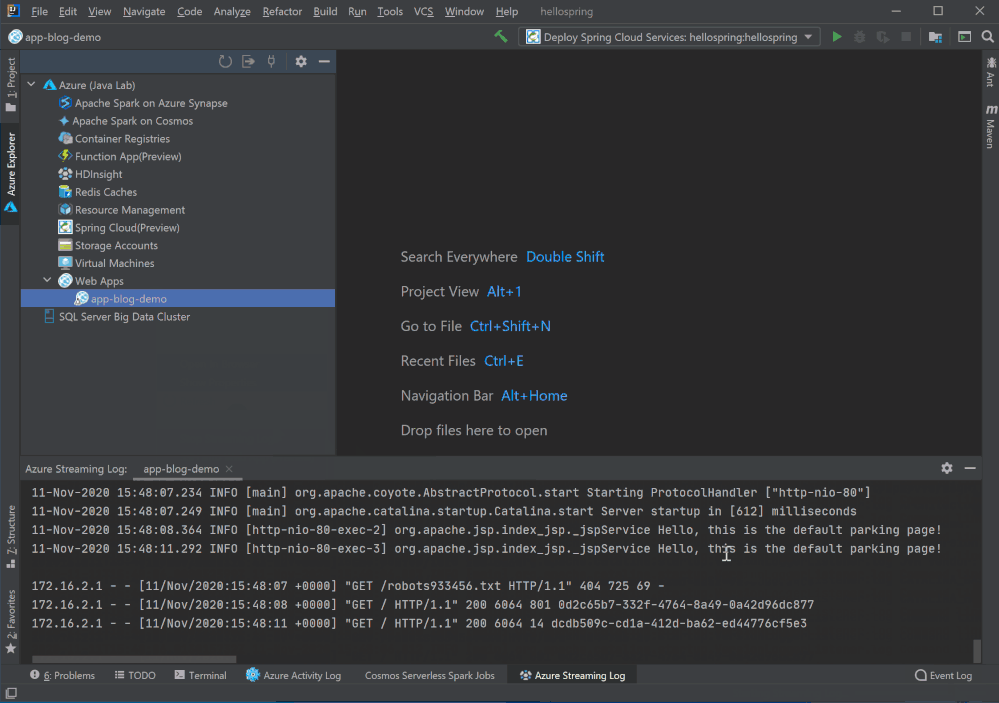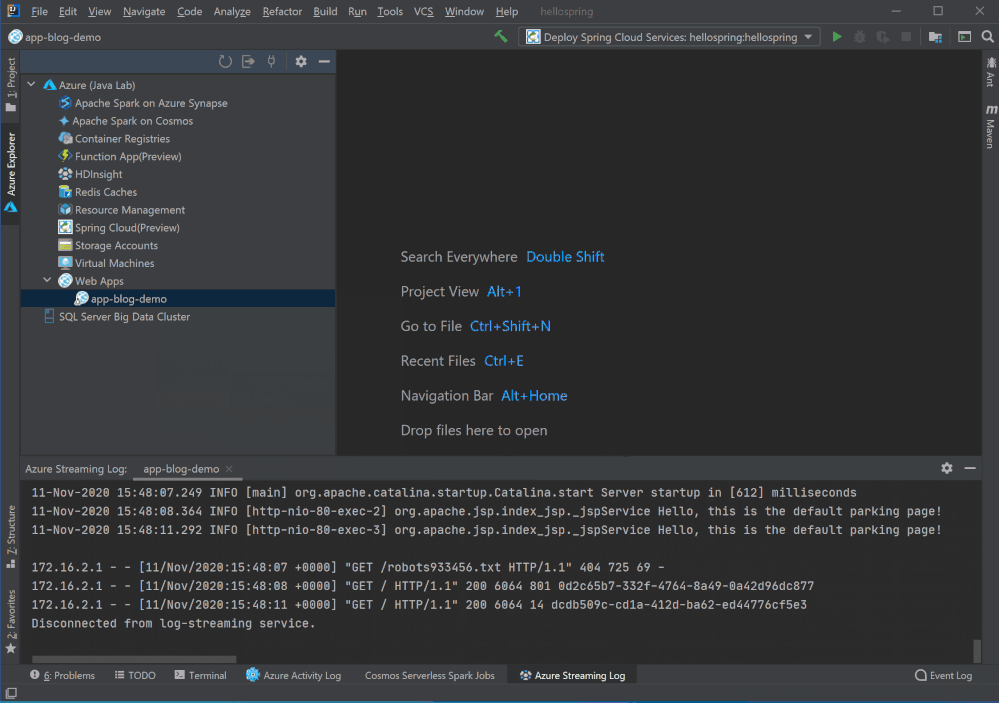
Log streaming
Right click on the Web App in Azure Explorer and select Start Streaming Logs and you will see real time logs showing up in IntelliJ. You can stop it by select Stop Streaming Logs.
One-click SSH
Right click on the Web App in Azure Explorer and select SSH into Web App and you will get a terminal connected to the app instance on Azure in minutes. You are now free to run any command and play around. Note that this preview feature is only for Linux Web App and requires Azure CLI installed.
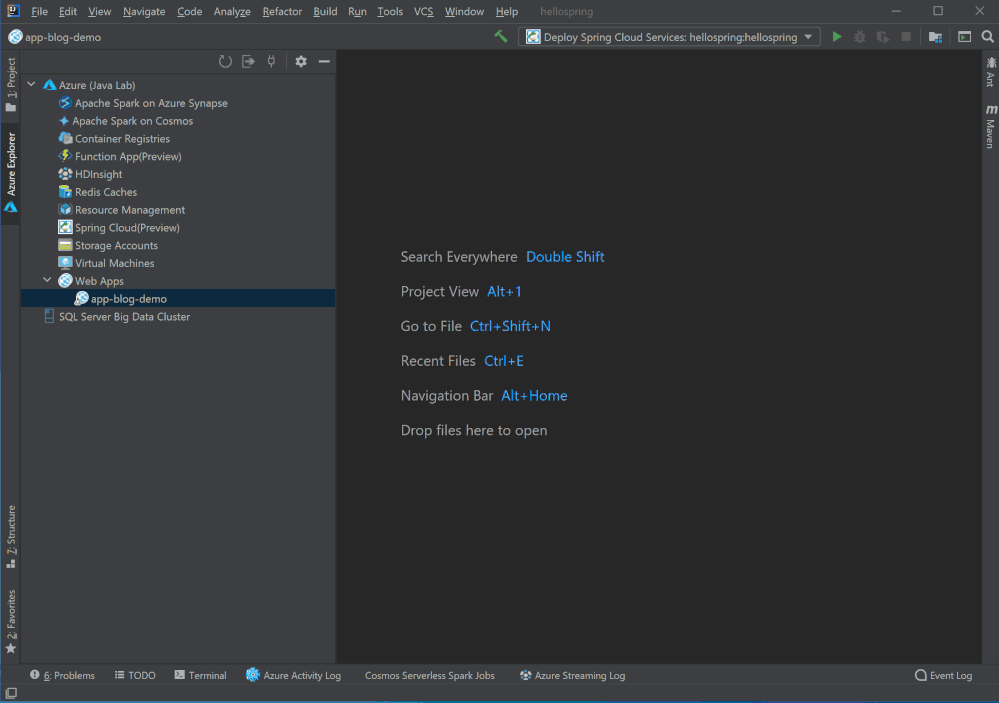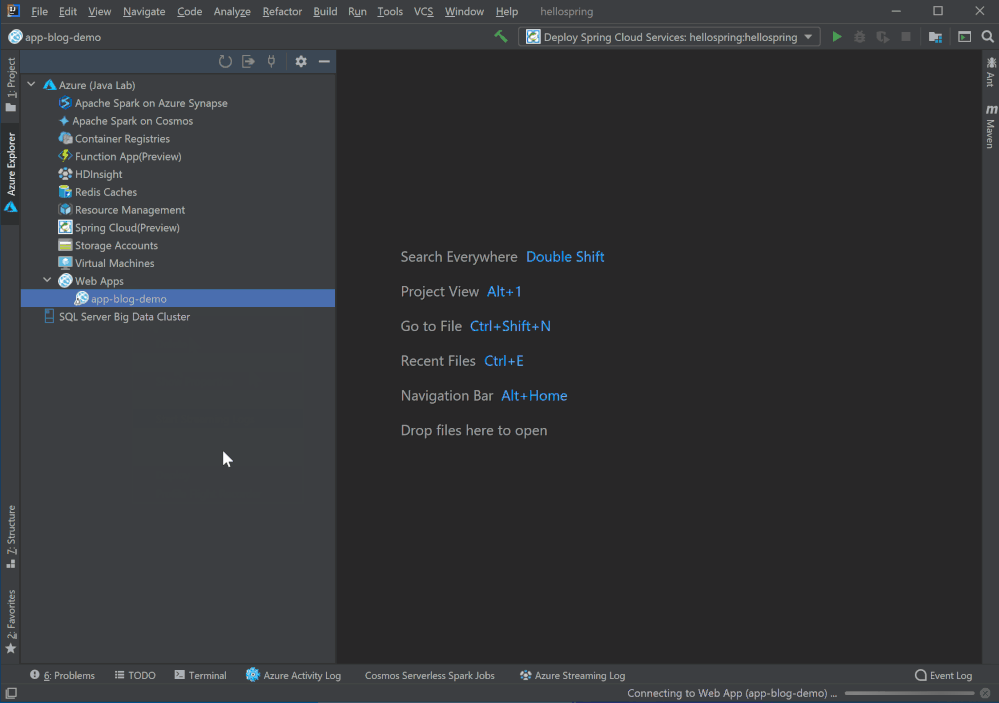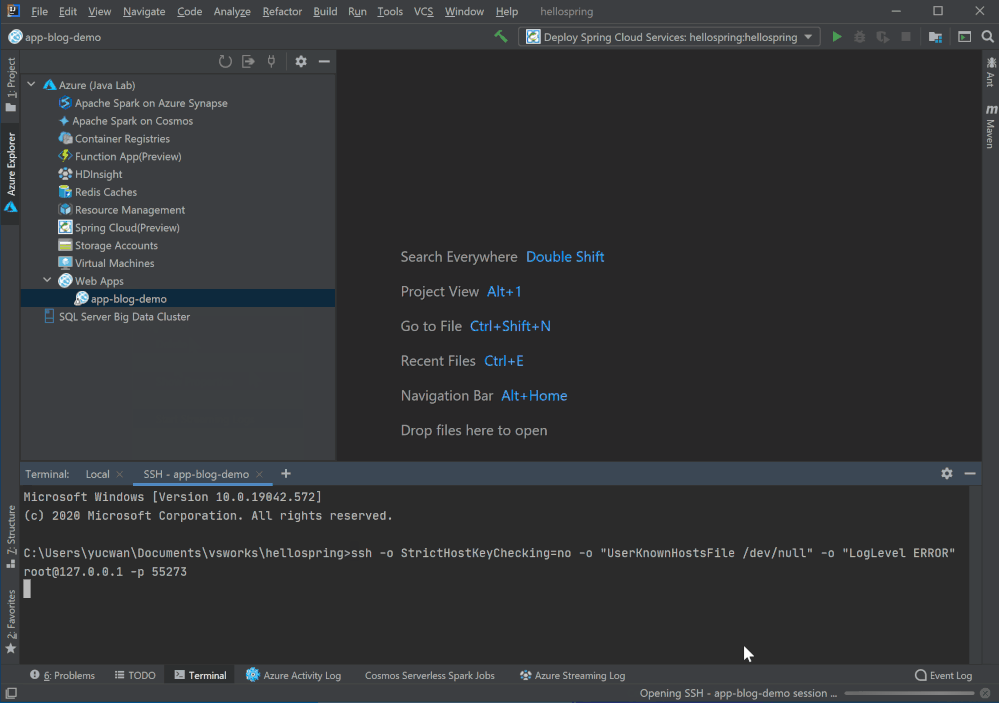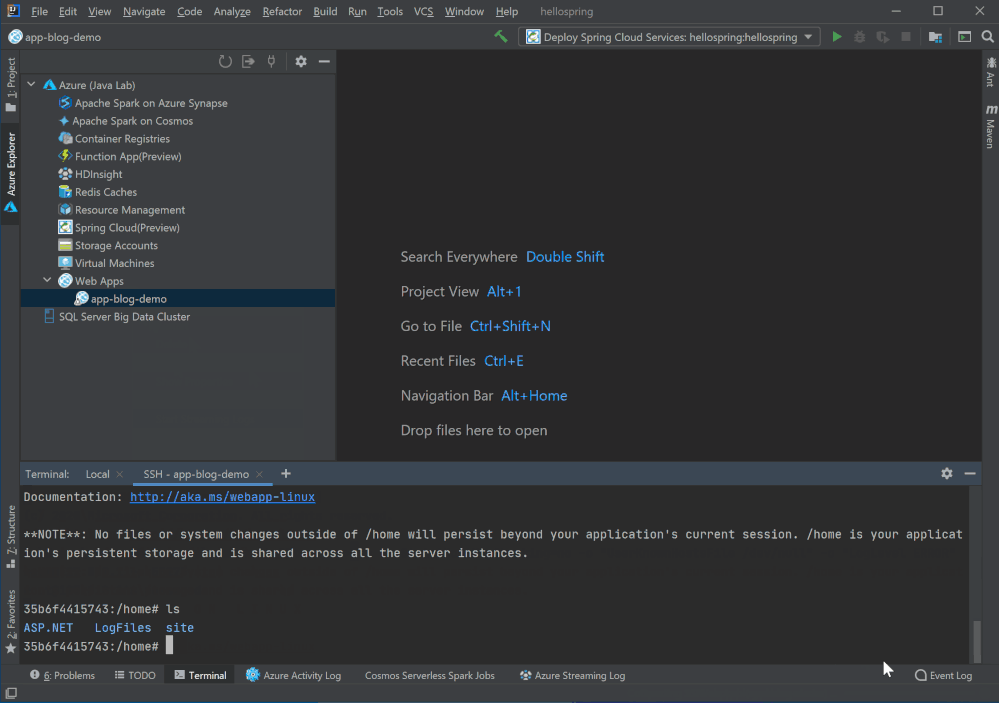
Remote file explorer
Here is the third option to view logs and explore your app! Click on the Web App in Azure Explorer and you will see two folders under the node. Click on the remote folders and explore any files in your Azure Web App instance. For example, you can double click and directly open log files in the editor, or right click on the file to download.
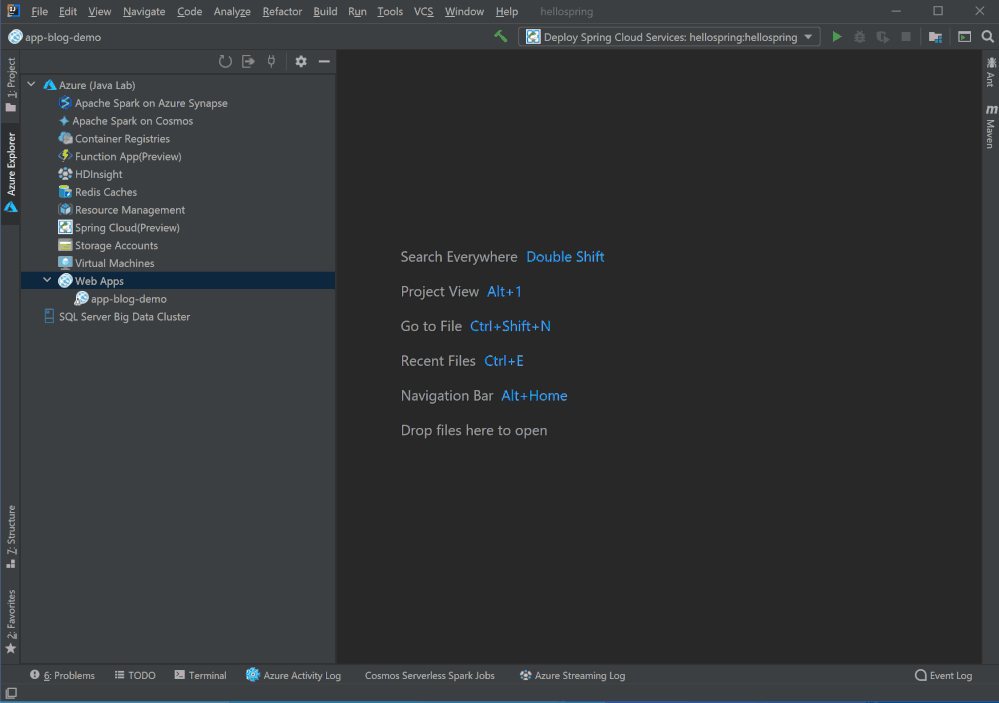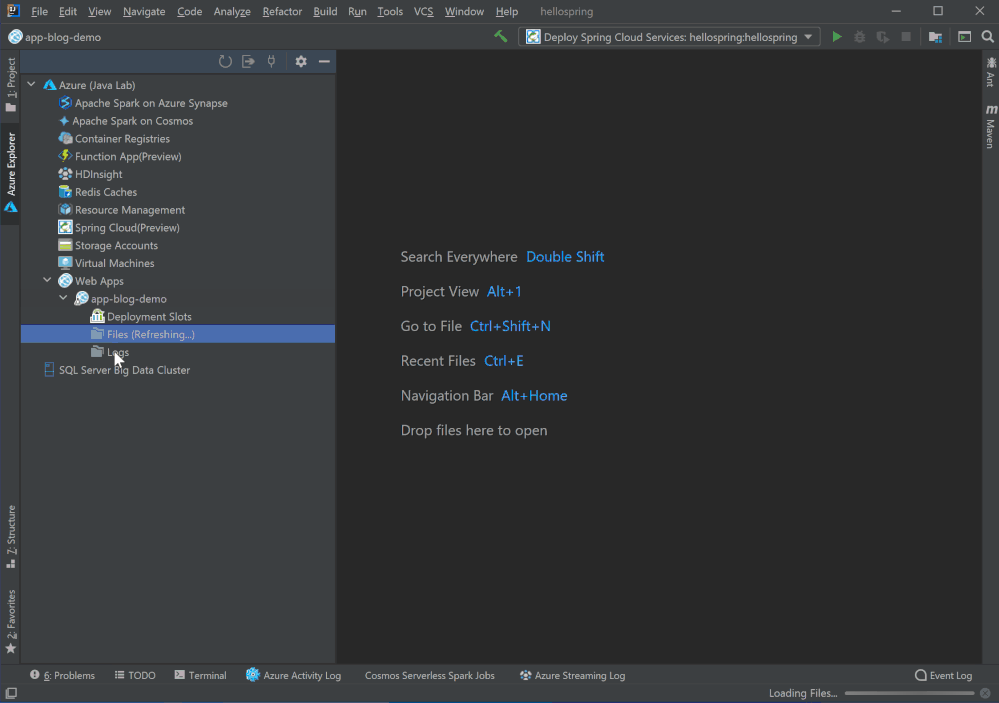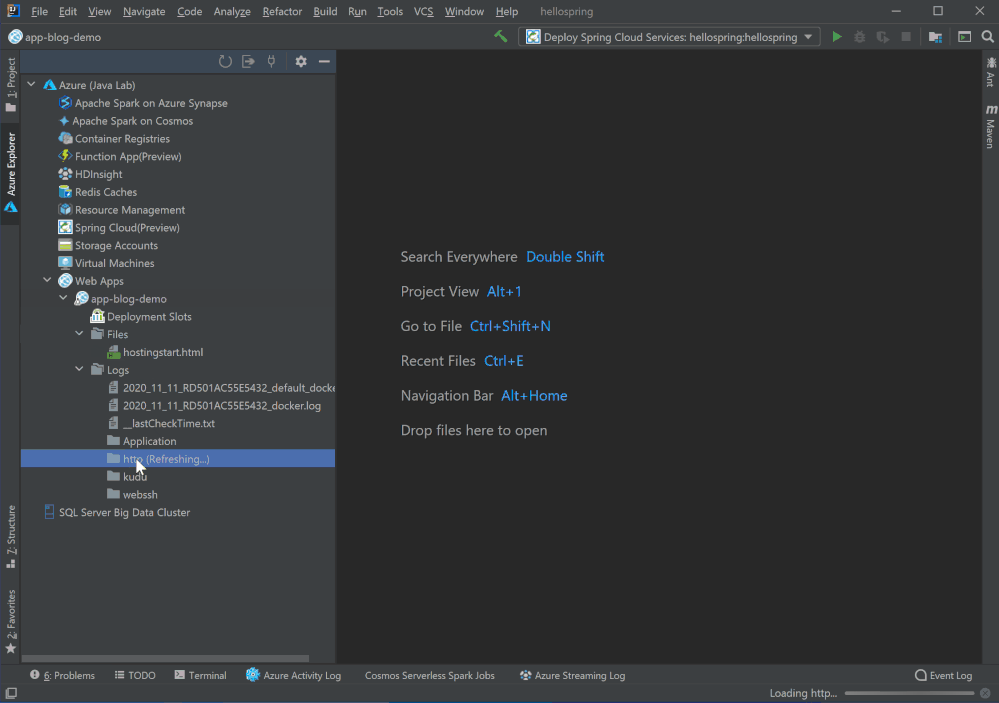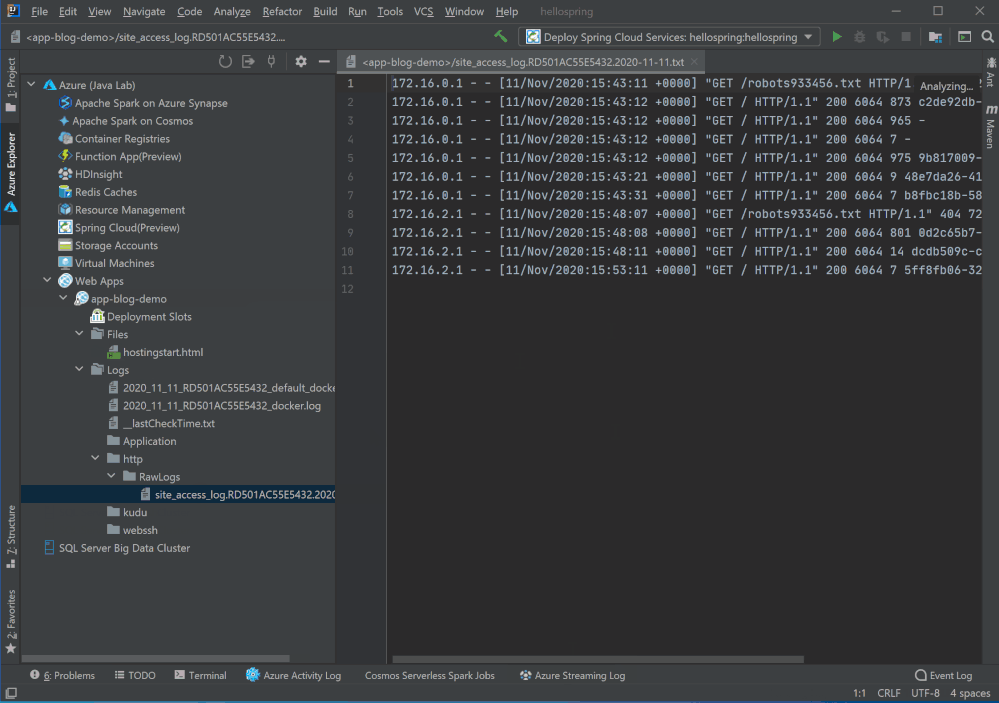
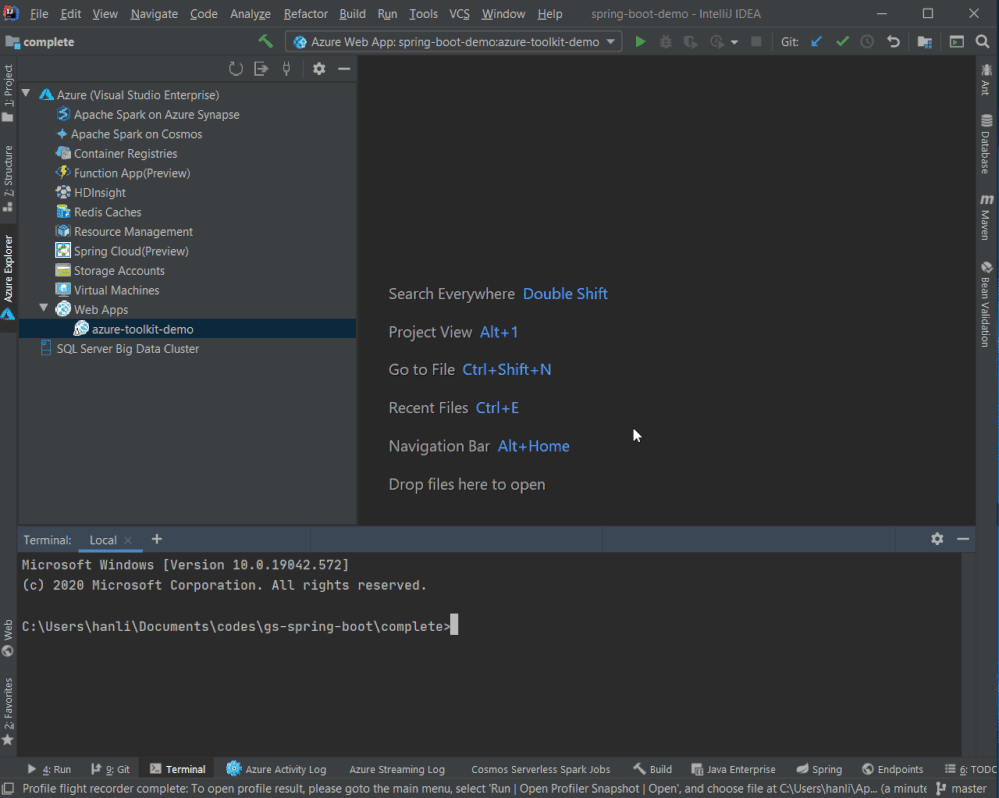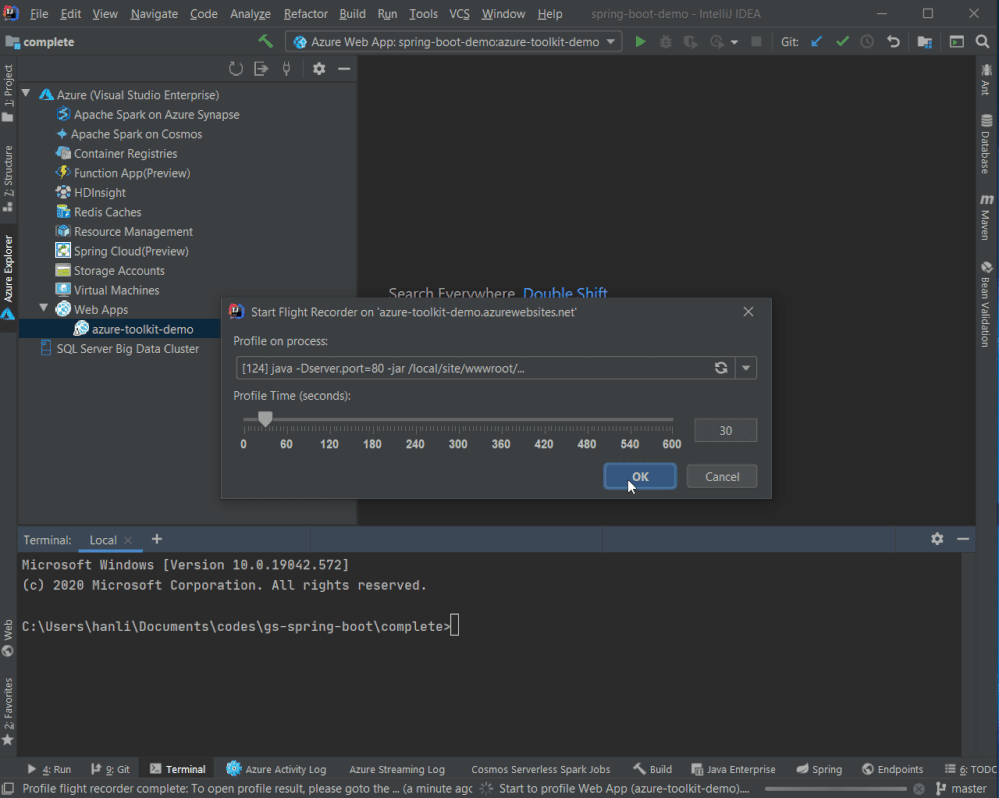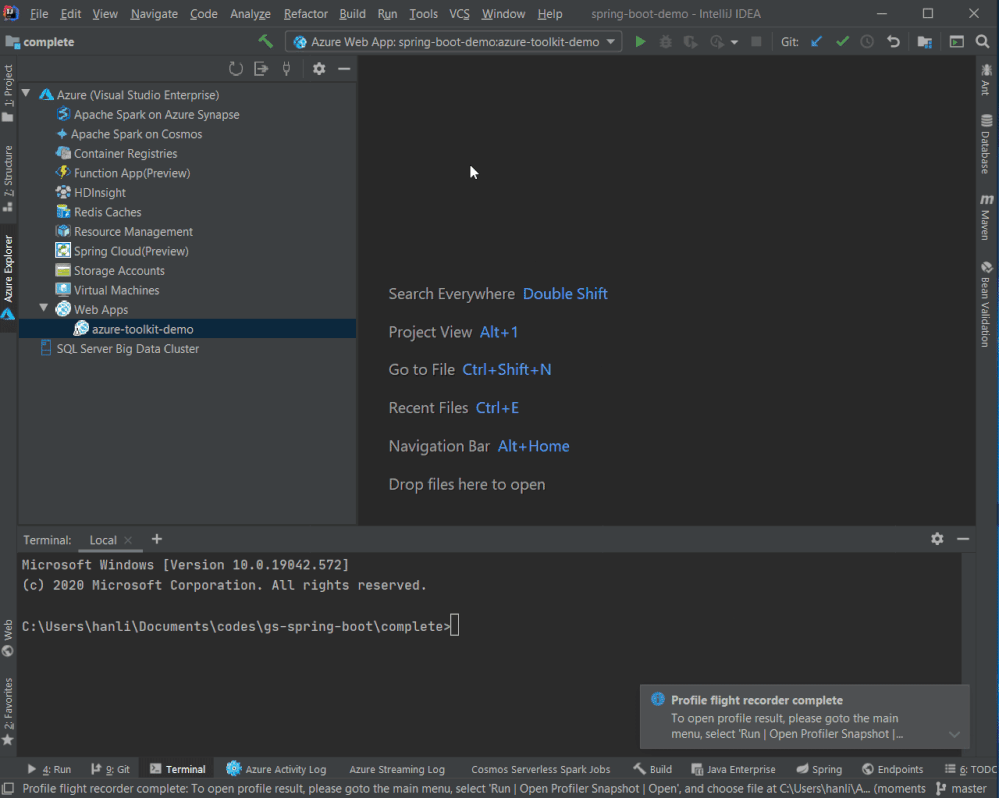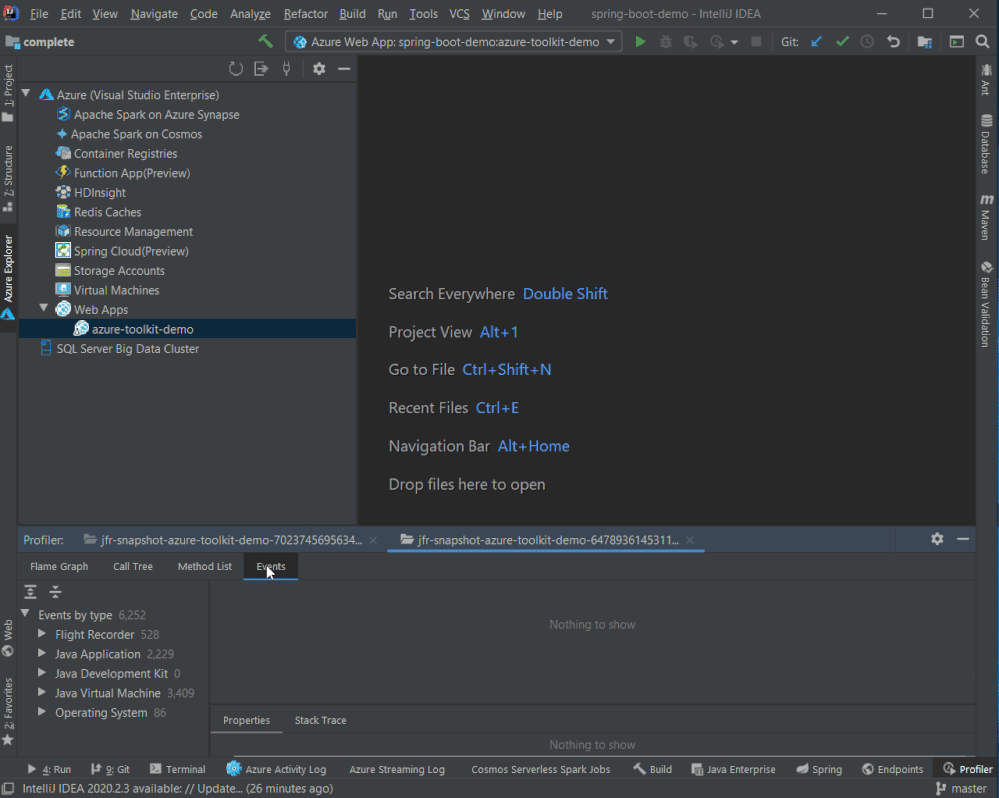
Profiling on the fly
Flight recorder support was also added in the Azure Toolkit for IntelliJ! You can now start profiling your Java Web Apps in Azure explorer by right clicking on the Web App in Azure Explorer and select Profile Flight Recorder and the report in .jfr format will be downloaded automatically. You can then analyze the report with Zulu Mission Control or directly inside IntelliJ if you are using Ultimate (2020.2 or above).
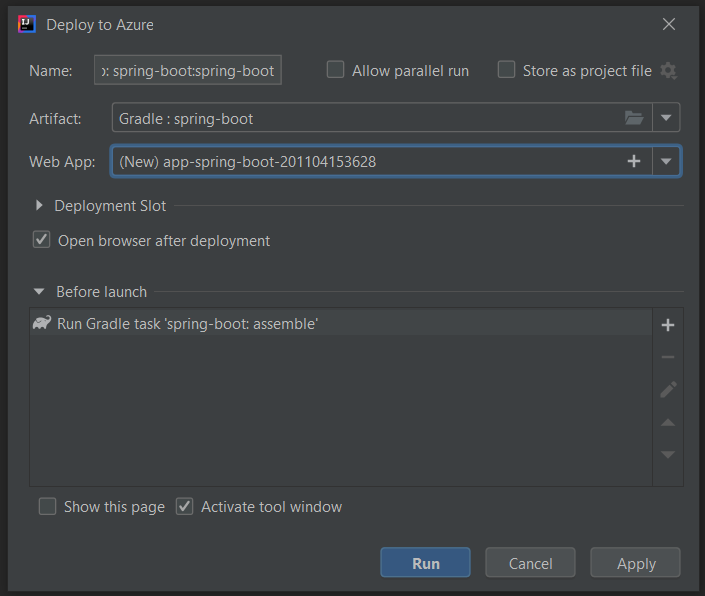
Gradle project support in IntelliJ
Here to mention that Gradle project is now supported in Azure Toolkit for IntelliJ. Now you can add configurations to deploy Gradle projects to Azure Web Apps and Azure Spring Cloud. The toolkit will then pick up the latest build and push to Azure once you hit Run or Shift+F10.
JBoss EAP support for Web Apps
JBoss EAP is now in Public Preview as a new runtime offering for Azure Web Apps and we are adding tooling support for it. Starting from version 1.12.0, you can chose JBoss EAP as runtime stack running the Maven plugin config goal in your project directory:
mvn com.microsoft.azure:azure-webapp-maven-plugin:1.12.0:config
Following is a sample configuration generated, note that both .war and .ear artifacts are supported. Besides Maven plugin, JBoss Web Apps is now supported in Azure Toolkit for IntelliJ as well.
<plugin>
<groupId>com.microsoft.azure</groupId>
<artifactId>azure-webapp-maven-plugin</artifactId>
<version>1.12.0</version>
<configuration>
<schemaVersion>v2</schemaVersion>
<subscriptionId>xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx</subscriptionId>
<resourceGroup>helloworld-1604469657612-rg</resourceGroup>
<appName>helloworld-1604469657612</appName>
<pricingTier>B2</pricingTier>
<region>westeurope</region>
<runtime>
<os>Linux</os>
<javaVersion>Java 8</javaVersion>
<webContainer>Jbosseap 7.2</webContainer>
</runtime>
<deployment>
<resources>
<resource>
<directory>${project.basedir}/target</directory>
<includes>
<include>*.war</include>
</includes>
</resource>
</resources>
</deployment>
</configuration>
</plugin>
Try it out
Please don’t hesitate to give it a try! Your feedback and suggestions are very important to us and will help shape our product in future.







Recent Comments