by Scott Muniz | Sep 3, 2020 | Uncategorized
This article is contributed. See the original author and article here.
Today, we are proud to announce the general availability of the Lists app in Teams for all our commercial and GCC customers. As you might already know, Microsoft Lists, which we announced at Build 2020 is a Microsoft 365 app that helps you track information and organize your work. Lists are simple, smart, and flexible, so you can stay on top of what matters most to your team. Track patients, loans, issues, assets, routines, contacts, inventory and more using customizable views and smart rules and alerts to keep everyone in sync. With ready-made templates, you can quickly create lists from directly within Teams and access them on the Teams mobile app by accessing the Lists tab you added as a channel.
Introducing the Lists app in Teams
The vision of the Lists app in Teams is to bring all the collaboration and communication modalities to lists and list items, so it is easy to get work done.
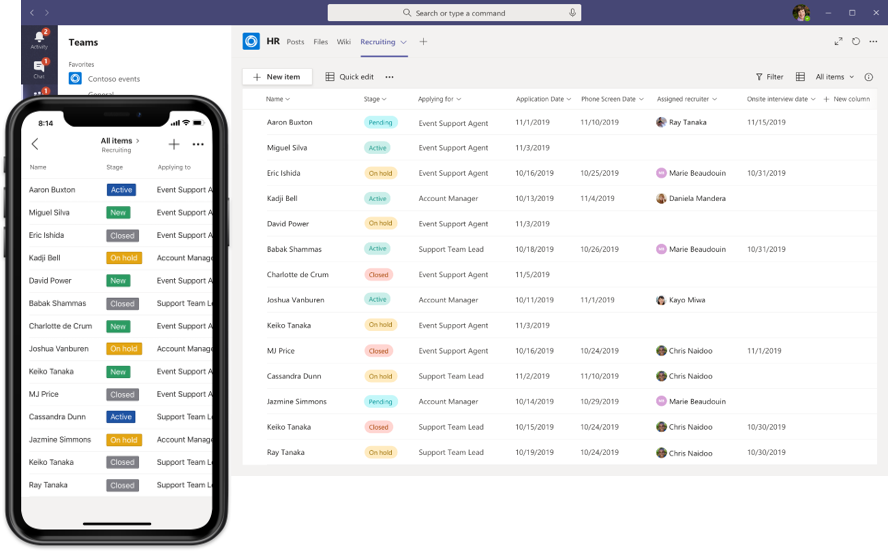
 The new Lists app experience in Microsoft Teams, for mobile on the left and for Web and desktop on the right.
The new Lists app experience in Microsoft Teams, for mobile on the left and for Web and desktop on the right.
Lists in Teams is supported as a team based tab app built on top of the Microsoft Teams platform and supports the following features:
- New list creation from scratch, from templates (8 standard templates and 3 industry specific ones: Patients, Loans, and Incidents), from Excel table data and from an existing list.
- Importing existing team lists as new tabs.
- All standard list features that you can access in SharePoint web: column types, view formatting, Quick Edit, exporting to Excel, sorting, filtering, etc.
- The ability to have a channel conversation about a list item (see below for more details).
- All user actions on the list are audited and available in the Security and compliance center audit logging.
How do I get started?
To get started, simply go to any channel where you would like to start tracking a list and hit the “+” button to explore the tab gallery and select the Lists app. Once the tab is added you can either create a new list or bring in an existing list (from another team or an older SharePoint site, but not a personal list from Lists home) into the channel as a new tab.
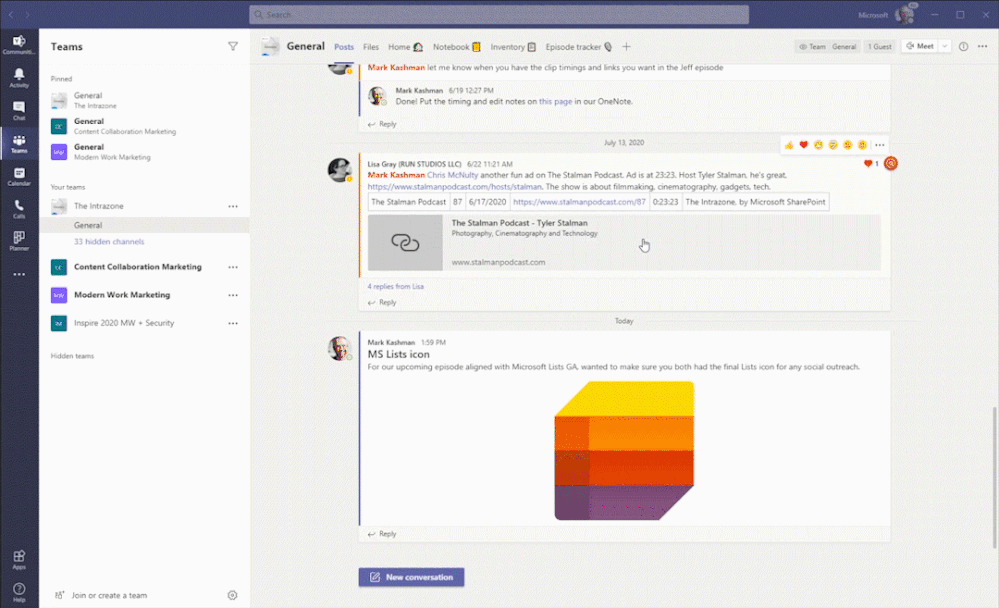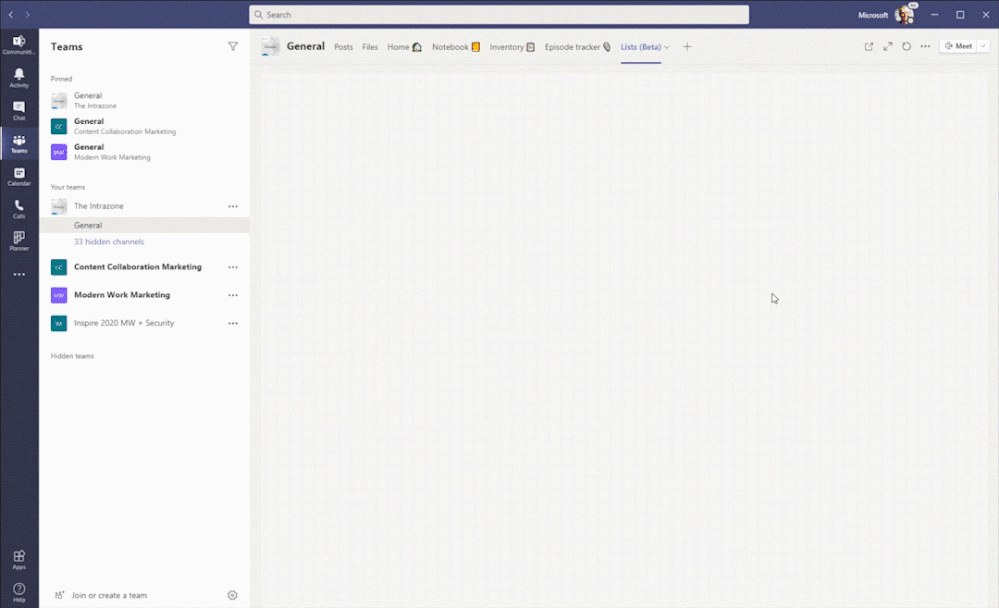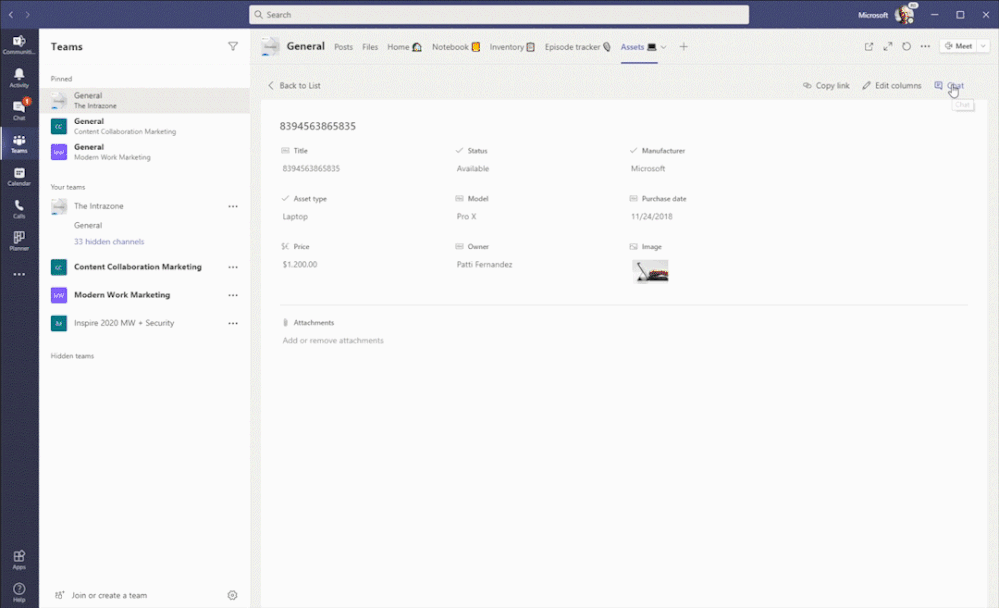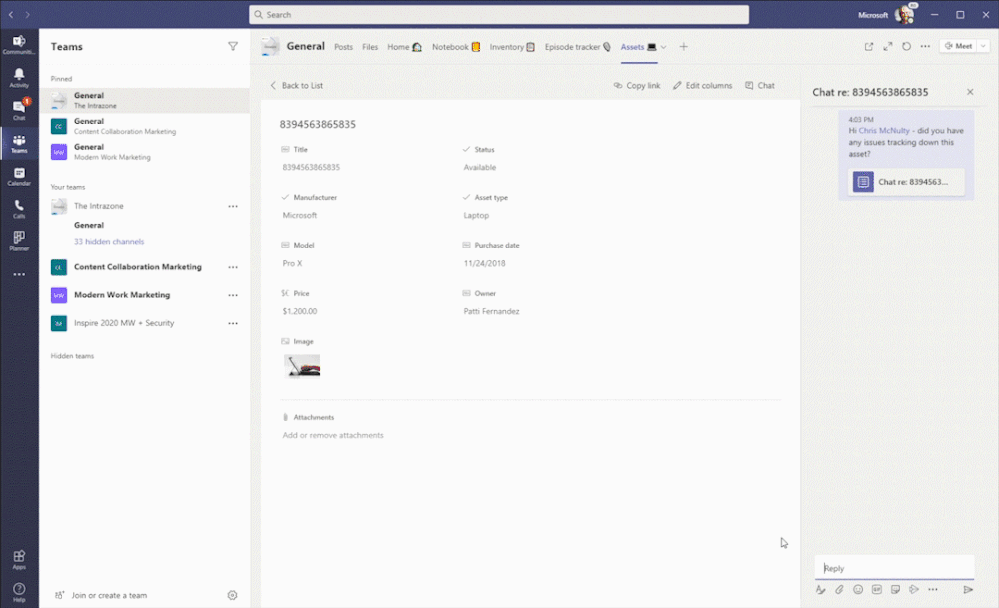 Create a new list inside Teams with conversations side-by-side. The above shows using the Asset manager template.
Create a new list inside Teams with conversations side-by-side. The above shows using the Asset manager template.
The Lists app in Teams includes 3 new industry-specific templates – Patients, Loans and Incidents. Team members start managing and tracking these key entities. Here are some examples of how these templates can be leveraged.
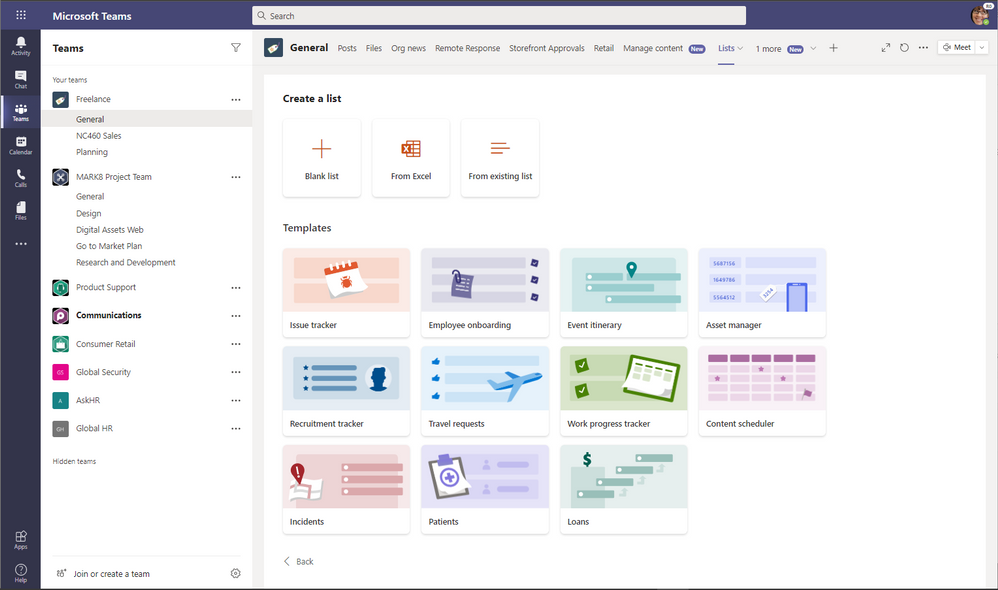 Create a new list from within Microsoft Teams and choose from numerous ready-made templates, including the new industry-specific ones.
Create a new list from within Microsoft Teams and choose from numerous ready-made templates, including the new industry-specific ones.
- Healthcare organizations can use the Lists app in Teams to support patient rounding, multi-discplinary huddles and discharge planning. The Patients template is an easy way for all health teams to track patient progress and keep in touch with their peers. If you have questions about storage of PHI in Teams, Lists, or Office 365, please see more documentation here.
- Government agencies can use the Lists app in Teams to track incidents and coordinated incident response. The Incidents template helps people quickly setup a list and get started.
- Loan officers at a morgtage broker or bank can use the Lists app to track a set of loans and informally collaborate on advancing a them to approval. The Loans template helps them get started with plenty of scope for further customization.
How do I start a conversation alongside a list item?
Once you have configured the tab and have a list with list items, you can start a conversation about an individual list item. Go to the details view (or form) for the list item by clicking into the title field and then click on conversation to start a conversation about the list item on the channel. With this feature, you can collaborate with your team about the list item (your key business entities) and get work done, faster.
Since the conversation is a channel message in Teams, all the messaging features like @mentions, rich text, giphies, stickers, emojis, mentions, tagging, and attachments are available for use! The conversation shows up in the right rail for the list item and also on the channel for those who might not have viewed the list as yet.
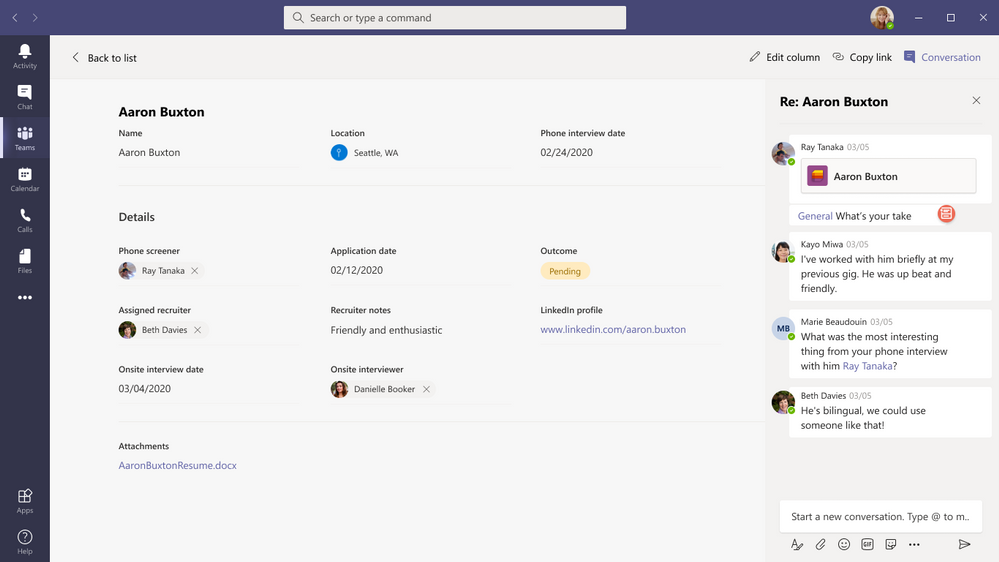 You can chat side-by-side individual list items within Teams.
You can chat side-by-side individual list items within Teams.
See more about getting started with the Lists app in Teams “Create a list in Microsoft Teams” click-thru demo. And do not forget to try the Lists app experience in the Teams mobile app to track your lists within Teams on the go. Just go to your Teams android or iOS mobile apps and go to the channel where you have added the Lists app and click on more and tap on the tab name to open up the list.
Learn more about the Lists app in Teams
If you are unable to see the Lists app in your channel, please contact your Teams Admin because applications in the Teams app store can be disabled or enabled by app permission policies. For more information, see the Manage the Lists app in Teams article. If you are looking for more resources and guidance, please review the help article here. For general help content and resources on Microsoft Lists, check out the Microsoft Lists resource center.
Note: Users of the existing SharePoint tab app in Teams that have pinned a list will see their experience inside the tab get upgraded to the latest Lists in Teams experience. This change will be rolling out today as well.
Millions of people use SharePoint lists and libraries every month in Microsoft 365 to track issues, manage inventory, report status, onboard new hires, build out event agendas, manage FAQs, and more. With flexible columns, forms, and views, you can build your own solution to meet your specific needs without knowing how to code. All these great capabilities now come to you inside the Lists app in Teams.
As always, thanks for taking the time to read about Lists in Teams! We’d love to hear any feedback or ideas you might have. Do submit suggestions on user voice. We are listening!
by Scott Muniz | Sep 3, 2020 | Uncategorized
This article is contributed. See the original author and article here.
For the pilot episode of the Power Healthcare Hour, Tail Wind Informatics previews an upcoming Sept 8th 2020 webinar “Data Strategy for Healthcare Systems.” Andy Walz and Ross McNeely review common challenges, strategic frameworks, and general advice for Healthcare industry data initiatives. For the second half of the show, opportunities to get more value out of Power BI licensing will be discussed. Learn more about Tail Wind Informatics’ webinar at this link. Follow the Power Healthcare Hour by subscribing to the YouTube channel or following the Twitter account https://twitter.com/PowerHealthcare.
by Scott Muniz | Sep 3, 2020 | Uncategorized
This article is contributed. See the original author and article here.
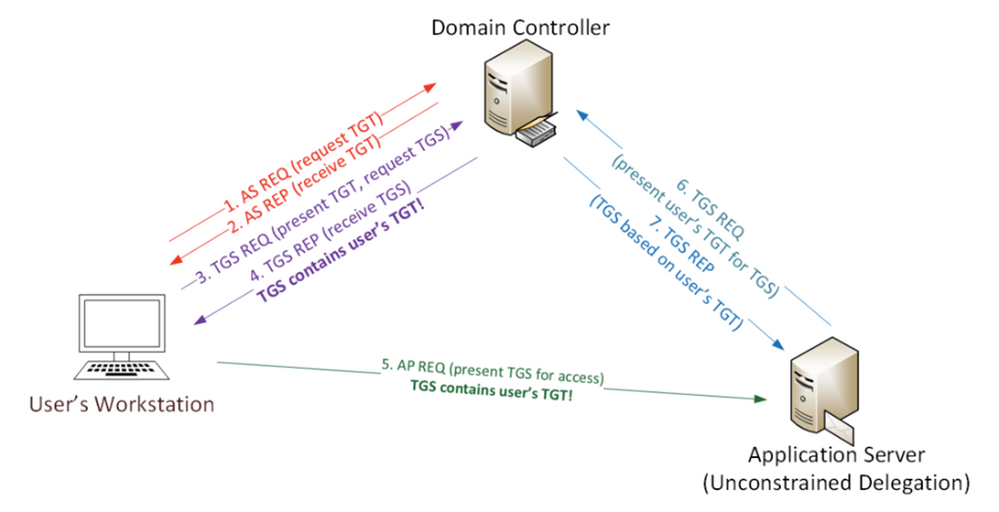
Imagine the following scenario, after a successful phishing campaign, an attacker finds themselves with an active shell on one of your non-sensitive employee’s devices. Using Living-off-the-Land (LotL) tactics (employing built in tools and commands), the attacker starts identifying their next targets and configuration weaknesses to leverage to comprise them. One such vulnerability might be the infamous print spooler bug.
The print spooler bug…
As published on the security conference DerbyCon at (2018), the print spooler bug is a way to gain elevated credentials (a sensitive computer account Kerberos ticket in this case) by exploiting two distinct configurations.
- A privileged device with the “print spooler” service running.
- A victim device configured for Unconstrained Kerberos delegation.
Using these two configurations in tandem, an attacker can “request” the sensitive device Kerberos ticket using the print spooler service through the victim’s device; and because unconstrained Kerberos delegation is enabled, that request will contain the highly sought-after Kerberos authentication ticket (TGT) that allows the attacker to impersonate the domain controller computer account – pretty bad, right?
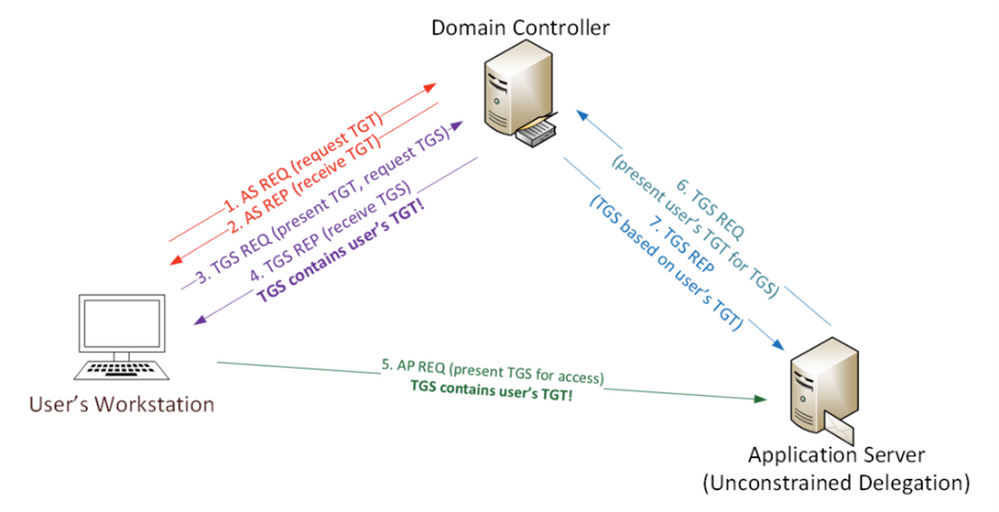
*Image from https://adsecurity.org/?p=4056
What can you do?
As part of Azure ATP, we introduced the Identity Security Posture assessment that automatically looks for these kinds of risky configurations in your on-premises environment. This assessment and the recommendation are now integrated in Microsoft Secure Score, makes creating a mitigation plan for these recommended actions easier than ever. To view the recommendations you can use the following steps:
- Go to the Microsoft Secure Score portal.
- Use filters to show the relevant product or tags.
- Locate the relevant improvement actions for mitigating the print spooler bug, create an action plan using the built–in options or click “Manage” to find out which entities have risky configurations and what actions are needed to re-configure them to remediate the issue.
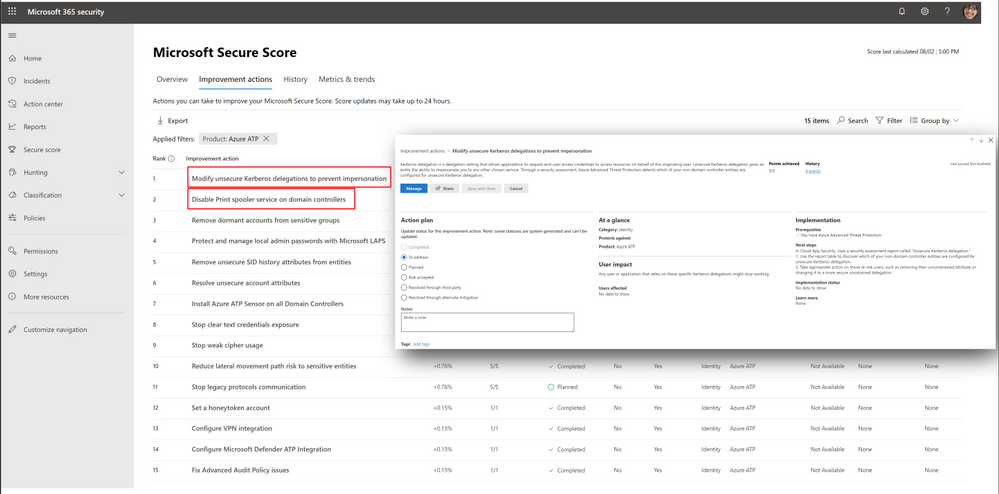
Once mitigated, Microsoft Secure Score will reflect the actions taken by increasing your score and mark these improvement actions as “Completed”.
Now, let’s consider another scenario.
After mitigating the print spooler bug , you discover another improvement action called “Stop clear text credential exposure”. After clicking the “Manage” button to access the assessment to view additional details, you discover that a sensitive entity and an accompanying device are authenticating over LDAP simple bind. To make matters even worse, the exposed user is also sensitive (belonging to the Domain admin group)
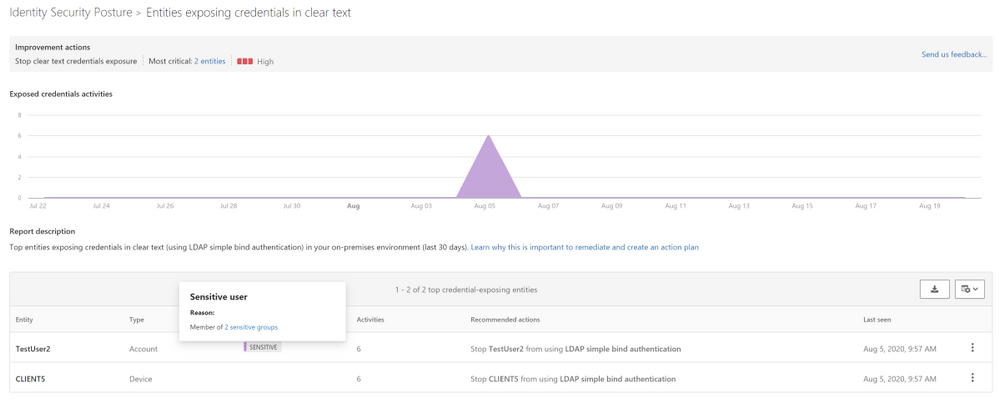
You then realize that if an attacker can get onto your network, they can “sniff” the transmitted credentials that are in clear text and gain elevated credentials.
To further investigate this case, you will need additional details regarding this type of unsecure communication such as:
- What processes are causing this behavior?
- Are any of them part of a critical application?
- What should I do next?
The hunt is on…
To answer these questions, let’s utilize one of MTP’s cool features called Advanced hunting which is now also enriched with Azure ATP activities alongside other security products such as Microsoft Defender ATP, Cloud App Security and Azure AD, and data from Office 365.
We’ll start by going to the Advanced hunting page in the new M365 security portal and from there, we now have access to all the different types of hunting data available for us, including two main tables relevant for this task:
- IdentityLogonEvents – all logon events generated by Azure ATP including the LDAP Cleartext type
- DeviceNetworkEvents – All networking events generated by Microsoft Defender ATP including LDAP queries generated toward the domain controllers using port 389.
To get started, we can write a query, joining detected logon sessions and network events from both these tables, resulting in a consolidated result that includes the all the unsecure logon activities and their initiating process names.
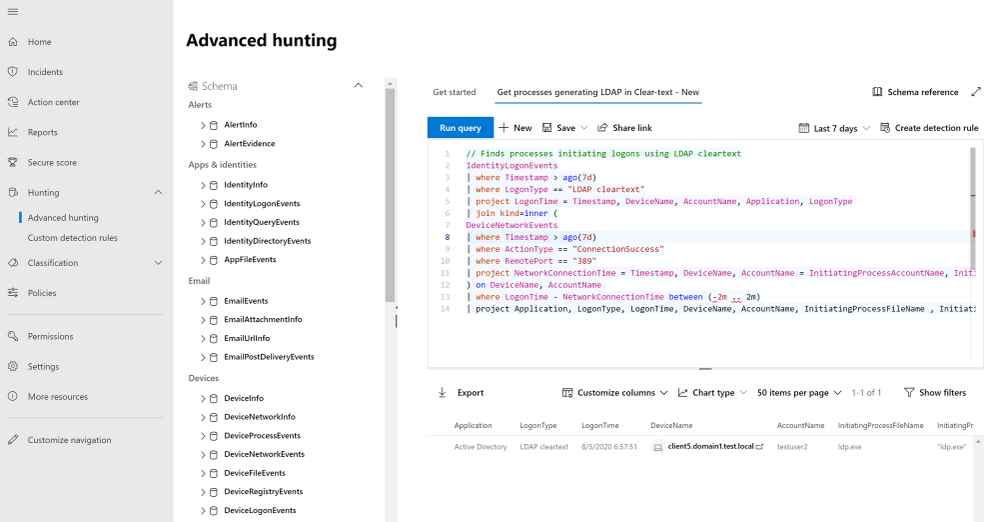
Using the query result, we can construct a cohesive story:
“On Aug 05, Testuser2 used the LDP.exe executable to generate an unsecure authentication using LDAP Simple Bind from Client5.”
We now have the relevant details to create a full remediation plan for this activity, such as simply blocking LDP.exe or configuring the application to require a more secure authentication while blocking insecure authentications at the domain level.
Conclusion
And there you have it! Using Azure ATP’s Identity Security Posture assessment with Microsoft Secure Score and Advanced hunting, we can build a simple mitigation plan for our organization’s security weak spots, making it that much harder for the bad guy the get in
For more information about Identity Security Posture assessments and MTP, see
* Learn more about Identity security posture assessments.
* Learn more about Microsoft Secure Score
* Azure ATP activities in advanced hunting
Or Tsemah, Senior Product Manager, Azure ATP.
by Scott Muniz | Sep 3, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
Initial Update: Thursday, 03 September 2020 10:34 UTC
We are aware of issues with Data Latency within Application Insights and Log Analytics in West Europe region and are actively investigating. Some customers may experience intermittent data latency, data gaps and incorrect alert activation.
- Work Around: None
- Next Update: Before 09/03 14:00 UTC
We are working hard to resolve this issue and apologize for any inconvenience.
-Sandeep
by Scott Muniz | Sep 3, 2020 | Uncategorized
This article is contributed. See the original author and article here.
Azure Data Factory orchestration allows conditional logic and enables user to take different based upon outcomes of a previous activity. In total we allows four conditional paths: Upon Success (default pass), Upon Failure, Upon Completion, and Upon Skip. Using different paths allow users to build robust pipelines and incorporates error handling in their ETL/ELT logic.
Here are two common error handling pattern we see customers use:
- TRY-CATCH block. Define the business logic, and only defines Upon Failure path to catch any error from previous activities
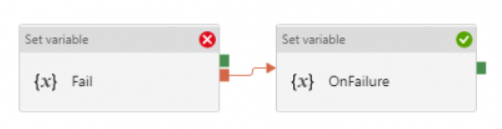
- DO-IF-ELSE block. Define the business logic, and depends on the outcome of the activity, enacts either Upon Success path or Upon Failure path
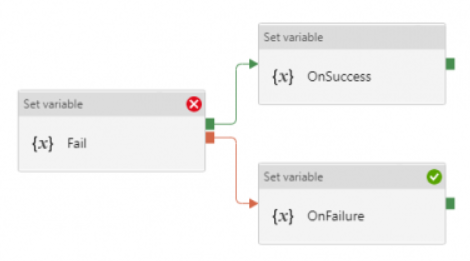
Both are valid ways to incorporate error handling into the pipeline. However, upon pipeline execution, they may show different outcomes. Approach #1, TRY-CATCH, shows pipeline succeeds if Upon Failure path clears, where as approach #2, DO-IF-ELSE show pipeline failed if Upon Failure path is enacted.
Technical reasons for the difference is that, Azure Data Factory defines pipeline success and failures as follows:
- Evaluate outcome for all leaves activities. If a leaf activity was skipped, we evaluate its parent activity instead
- Pipeline result is success if and only if all leaves succeed
Applying the logic to previous examples.
- In approach #1 TRY-CATCH block:
- when previous activity succeeds: the node activity, Upon Failure, is skipped and its parent node succeeds, so overall pipeline succeeds
- when previous activity fails: the node activity, Upon Failure, enacted and overall pipeline succeeds if Upon Failure path succeeds
- In approach #2 DO-IF-ELSE block:
- when previous activity succeeds: one node activity, Upon Success, succeeded, and the other node activity, Upon Failure, is skipped and its parent node succeeds; so overall pipeline succeeds
- when previous activity fails: one node activity, Upon Success, is skipped and its parent node failed; so overall pipeline failed
Here is a table summarizing the difference
| Approach |
Error Handling Defines |
When Activity Succeeds |
When Activity Fails |
| TRY-CATCH |
Only Upon Failure path |
Pipeline shows Success |
Pipeline shows Success |
| DO-IF-ELSE |
Upon Failure and Upon Success paths |
Pipeline shows Success |
Pipeline shows Failure |

Create a new list inside Teams with conversations side-by-side. The above shows using the Asset manager template.
Create a new list from within Microsoft Teams and choose from numerous ready-made templates, including the new industry-specific ones.
You can chat side-by-side individual list items within Teams.




Recent Comments