by Scott Muniz | Sep 11, 2020 | Uncategorized
This article is contributed. See the original author and article here.
Microsoft needs your help creating our learning and exam content. To facilitate this, we’ve created the SME Profile database where you can provide us with information about your skills and abilities. With the SME Profile database program, we can connect with SMEs who are passionate about Microsoft’s training and credentialing efforts. Through the program, participants can take part in exam and learning development activities such as courseware authoring, exam item writing, acting as technical reviewers, and participating in research. Perhaps the best benefit is getting special invites to participate in beta exams. SMEs in the database receive a special beta exam discount code that, while limited to a set number of seats, is only provided to that group. Being a member has its privileges.
Here are the basic steps:
- The SME Profile database is hosted as an engagement under the Microsoft Collaborate developer program. Joining requires a Microsoft account and registration to the developer site, so you’ll need to make sure you have an account.
- Join the Worldwide Learning SME Profile engagement on Microsoft Collaborate and complete your profile survey.
That’s it! OK, there are a few more steps required, but this is the basic gist. For step-by-step instructions (and lots of screen captures), download the attached PDF called Joining the SME Profile engagement on Microsoft Collaborate.
Many people on Microsoft’s Worldwide Learning team use the database to search for SMEs who can assist with content development—from creating courses to reviewing them to writing exam content to reviewing items and setting the passing score (really!)—and participating in research designed to define the direction we head as a learning organization. As an active participant in the SME Profile database program, you can have a say in what we teach, how we evaluate skills, and the future of our program. Not too shabby. But, I suspect that the reason you’ll join is because those in our SME database get a unique code to participate in beta exams (one that is not posted here), increasing the likelihood of getting a seat in that beta exam that you really want to take. Join today!
Joining the SME Profile engagement on Microsoft Collaborate_v2.pdf
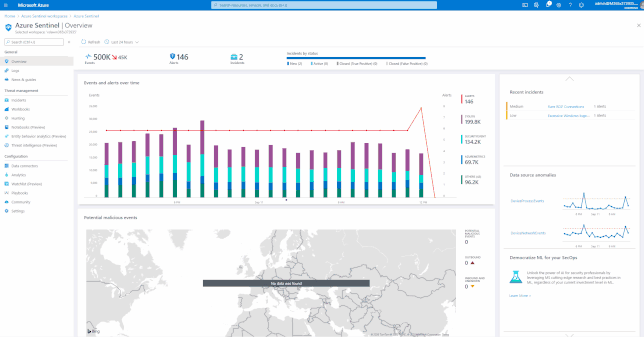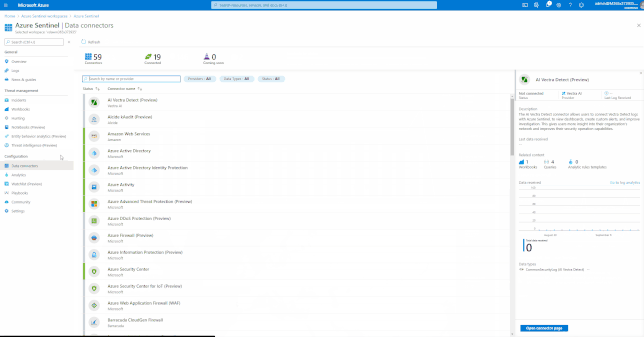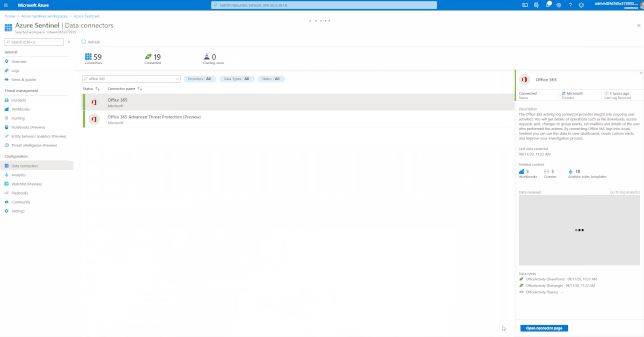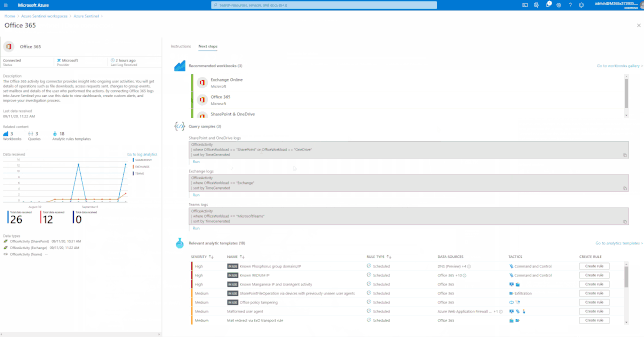
by Scott Muniz | Sep 11, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
Special thanks to “Clive Watson” and “Ofer Shezaf” that collaborating with me on this blog post.
Due to the COVID-19 crisis, the usage of Office 365 has increased which introduces new security monitoring challenges for SOC teams. Increase usage means that the service should be more focal for defenders.
Over the past few mounts I have been working with my customers, on approaches to onboard Office 365 and related services into Azure Sentinel and the benefit of built-in solutions that a Cloud based Security Information and Event Management (SIEM) and Security Orchestration, Automation and Response (SOAR) bring, such as these use cases.
This blog post is built as a checklist and covers the following topics:
- Required data sources for Office 365 and related workloads
- Onboarding of data sources
- Visualizing data
- Using of out of the box Analytics Rules templates
- Hunting with Azure Sentinel
- Integration of 3rd party Threat Intelligence (TI)
- Data enrichment capabilities
- Automation with SOAR capabilities
- Integration with Ticketing Systems
- Integration with 3rd party SIEMs
Required data sources for Office 365 and related workloads
Choosing the right telemetry for Office 365 and related workloads depends on the enterprise’s security model. For instance, if an enterprise which follow the Zero Trust approach from Microsoft would focus on different telemetry than an enterprise with a classical security approach.
The following data sources should be the minimum onboarded to monitor Office 365:
In addition, the sources below are optional as they depend on additional licenses. Azure Sentinel can benefit from these expert systems and it is recommended to onboard if licensed or consider adding these to aid with detection and use cases.
- Azure Activity Directory Identity Protection alerts
- Office 365 Advanced Threat Protection and Threat Investigation and Response alerts
- Microsoft Cloud App Security alerts
Lastly, the following data sources are optional and would unlock more value by correlating different data sources using SIEM and SOAR capabilities.
- Logs from Domain Controllers and Azure Advanced Threat Protection alerts
- Telemetry from client devices
- Logs and alerts from Proxies and Firewalls
- 3rd Party Threat Intelligence feeds
Onboarding of data sources
Azure Sentinel comes with a several built-in and custom connectors to onboard Office 365 and related workloads.
GIFT Demonstration – Enable the Office 365 data connector:
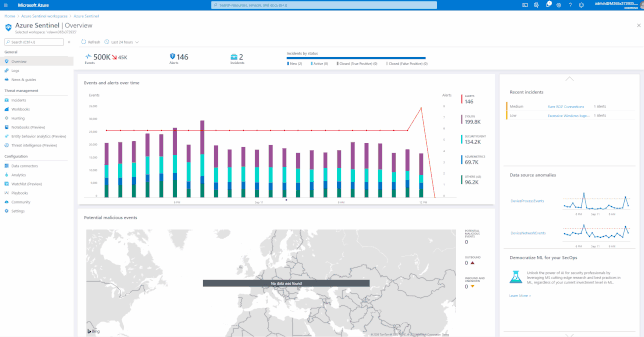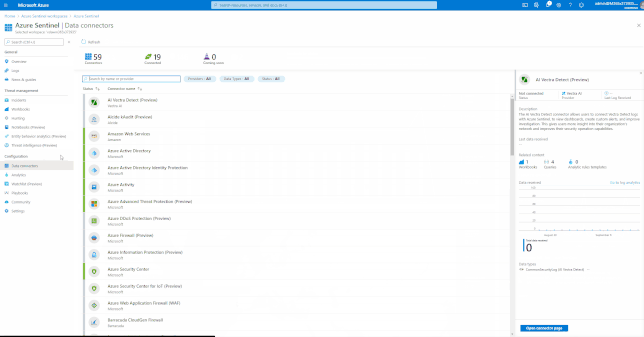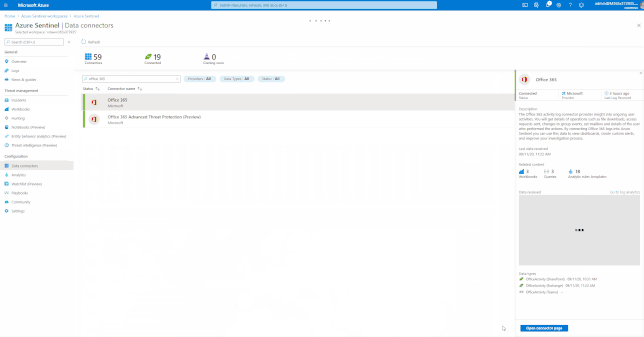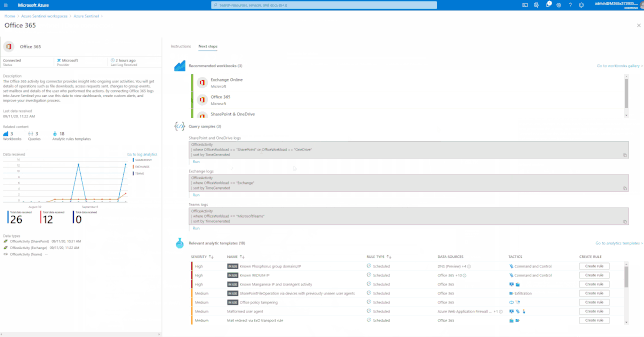
For a full list, please see, the Azure Sentinel Grand List.
Visualizing data
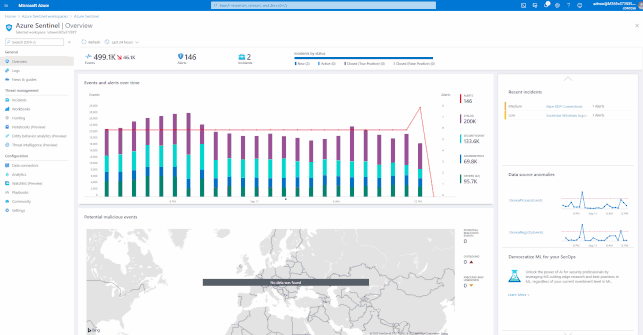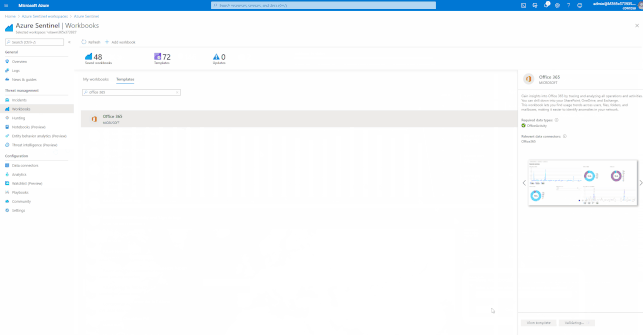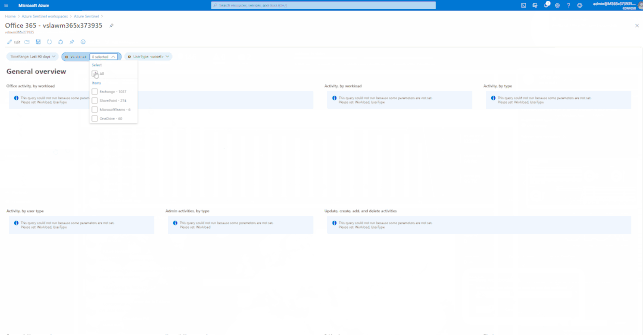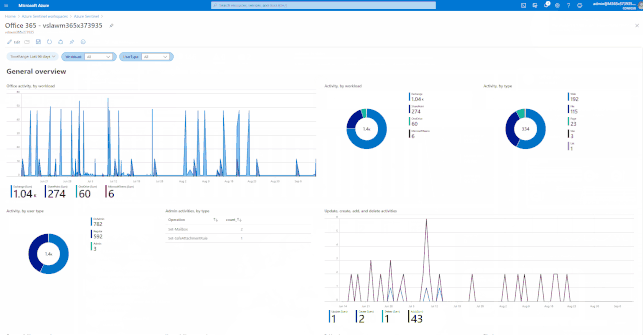
Azure Sentinel has many built-in workbooks that provide extensive reporting capabilities analyzing your connected data sources to let you quickly and easily deep dive into the data generated by those services. The built-in workbooks can be changed and customized as needed. The Workbooks are provided by Microsoft, our data connector partners and the community.
These built-in Workbooks are available in Azure Sentinel for Office 365 and related workloads.
For more information and instructions on how to use Azure Sentinel Workbooks, please see:
Visualize your data using Azure Monitor Workbooks in Azure Sentinel | Microsoft Docs
In case you prefer to use Power BI for analytics and visualization:
Import Azure Monitor log data into PowerBI:
https://docs.microsoft.com/en-us/azure/azure-monitor/platform/powerbi
GIFT Demonstration – How to enable and use the Office 365 Workbook:
Using out of the box Analytics Rule Templates
Once you have connected your required data sources, you can use the Analytics Rule templates available in Azure Sentinel to generate incidents when certain criteria are matched. The Analytics Rules can be changed and customized as needed.
These Analytics Rule templates are available in Azure Sentinel for Office 365 and related workloads.
Tip: You see the related Analytics Rules (and required data) that match the connector on the “Next Steps” page of the “Add Connector” wizard.
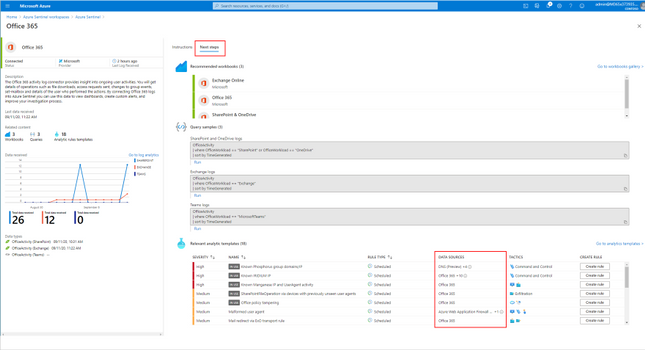
Hunting with Azure Sentinel
Azure Sentinel has built-in Hunting Queries to look proactively for new anomalies that you are not yet detecting with your Analytics Rules. You can use these Hunting Queries and Live Stream to create interactive sessions that let you test newly created queries as events occur, get notifications from the sessions when a match is found, and launch investigations if necessary. You can quickly create a livestream session using any Log Analytics query.
- Test newly created queries as events occur
- You can test and adjust queries without any conflicts to current rules that are being actively applied to events. After you confirm these new queries work as expected, it’s easy to promote them to custom alert rules by selecting an option that elevates the session to an alert.
These Hunting Queries are available in Azure Sentinel for Office 365 and related workloads.
GIFT Demonstration – Using the Built-In Hunting Queries for Office 365:
Integration with 3rd Party Threat Intelligence
Azure Sentinel lets you import you own threat intelligence indicators, which can enhance your security analysts’ ability to detect and prioritize known threats.
You can stream threat indicators to Azure Sentinel by using one of the integrated threat intelligence platform (TIP) products listed in the next section, connecting to TAXII servers, or by using direct integration with the Microsoft Graph Security tiIndicators API.
The Threat Intelligence data connector includes out of the box Analytics Rules and Hunting Query templates for Office 365 and related workloads.
Threat Intelligence Analytics Rules
Threat Intelligence Hunting Queries
Data enrichment capabilities
Data enrichment is key to associating data in context of enterprises. For instance, data enrichment would add additional information or context to the ingested logs to make it more valuable.
For Office 365 and related workloads Azure Sentinel provides these enrichment use cases:
Automation with SOAR capabilities
Azure Sentinel has built-in SOAR capabilities to orchestrate and automate common and complex tasks. Azure Sentinel uses Azure Logic App and Azure Function Apps for automation. Both services are built-in in Azure. The SOAR use cases are published here: GitHub, and can be deployment via ARM-Templates.
Using automation can save time, improve efficiency and help you improve your SOC (Security Operations Center) metrics and reduce the workload for the Securtity analyts.
https://docs.microsoft.com/en-us/azure/sentinel/manage-soc-with-incident-metrics
Azure Sentinel includes these automation solutions for Office 365 and related workloads:
GIFT Demonstration – How to enable the “Block Azure Active Directory User” Playbook:
Integration with Ticketing Systems
As part of the SOAR capabilities, Azure Sentinel support integration with ticketing systems. You can also just send a simple email or Teams message with the same data if you prefer (or do this in parallel with your Ticket).
Integration with 3rd Party SIEM
In case you are approaching Side-by-Side along with your exiting SIEM.
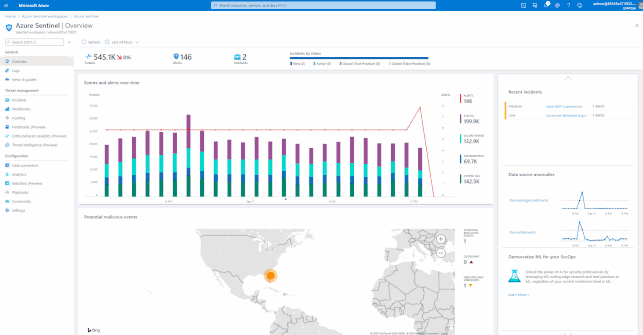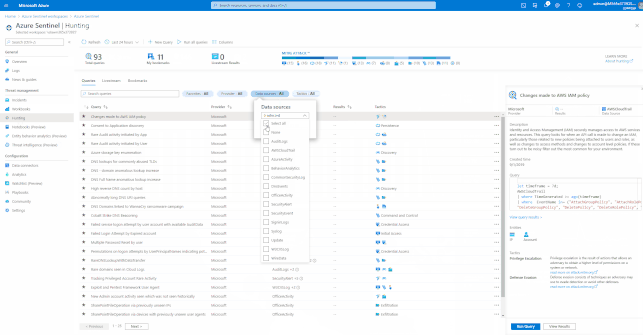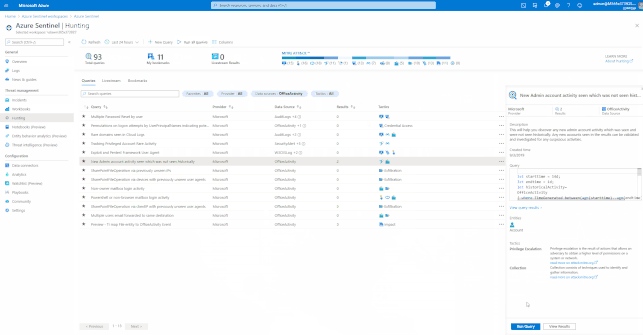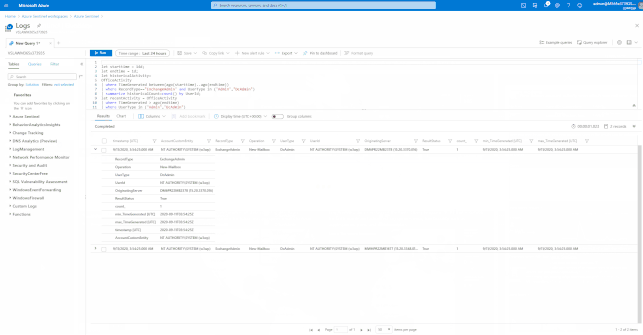
Summary
Ingesting of Office 365 alert logs are free, Azure Sentinel comes with a lot of use cases which help organizations to monitor and protect Office 365 workload, as well allows easy integration into existing SOC environment.
In this post we have covered the basics, looking at the data required, how to on-board connectors, how to manage Alerts, how to Hunt and automate responses to the results, and also connecting to 3rd party ticketing or SIEM solutions.
by Scott Muniz | Sep 11, 2020 | Uncategorized
This article is contributed. See the original author and article here.
Today, I worked on a service request that our customer needs to avoid that some users could retrieve some rows depending on a specific role. In this situation, we are going to use Is_RoleMember function.
For example, we have an Azure Active Directory group called MyAADGroup that contains all the users that we will have access to the data.
1) We are going to create the group in Azure SQL Database, running the following query:
CREATE USER [MyAADGroup] FROM EXTERNAL PROVIDER
2) We’re going to create the role, for example, auditors that will assign to the group MyAADGroup, running the following command:
sp_addrolemember 'auditors','MyAADGroup'
3) The next step, would be to create the security function, running the following command:
CREATE or alter Function [dbo].[fn_securitypredicateOrder] (@UserName sysname)
returns table
with Schemabinding
as
return select 1 as [fn_securityPredicateOrder_result] where IS_ROLEMEMBER('auditors')=1
4) Finally, we need to create the security policy running the following command:
create security Policy fn_securitydata
add Filter Predicate
dbo.fn_securitypredicateOrder(suser_name())
on MyTableDummy
Enjoy!
by Scott Muniz | Sep 11, 2020 | Uncategorized
This article is contributed. See the original author and article here.
Today, I worked on a service request that our customer needs to avoid that some users could retrieve some rows depending on a specific role. In this situation, we are going to use Is_RoleMember function.
For example, we have an Azure Active Directory group called MyAADGroup that contains all the users that we will have access to the data.
1) We are going to create the group in Azure SQL Database, running the following query:
CREATE USER [MyAADGroup] FROM EXTERNAL PROVIDER
2) We’re going to create the role, for example, auditors that will assign to the group MyAADGroup, running the following command:
sp_addrolemember 'auditors','MyAADGroup'
3) The next step, would be to create the security function, running the following command:
CREATE or alter Function [dbo].[fn_securitypredicateOrder] (@UserName sysname)
returns table
with Schemabinding
as
return select 1 as [fn_securityPredicateOrder_result] where IS_ROLEMEMBER('auditors')=1
4) Finally, we need to create the security policy running the following command:
create security Policy fn_securitydata
add Filter Predicate
dbo.fn_securitypredicateOrder(suser_name())
on MyTableDummy
Enjoy!

by Scott Muniz | Sep 11, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.

Project Server Permission Mode Vs SharePoint Permission Mode
Mohamed El-Qassas is a Microsoft MVP, SharePoint StackExchange (StackOverflow) Moderator, C# Corner MVP, Microsoft TechNet Wiki Judge, Blogger, and Senior Technical Consultant with +10 years of experience in SharePoint, Project Server, and BI. In SharePoint StackExchange, he has been elected as the 1st Moderator in the GCC, Middle East, and Africa, and ranked as the 2nd top contributor of all the time. Check out his blog here.

Start your DevOps pipeline in the Azure Cloud
James van den Berg has been working in ICT with Microsoft Technology since 1987. He works for the largest educational institution in the Netherlands as an ICT Specialist, managing datacenters for students. He’s proud to have been a Cloud and Datacenter Management since 2011, and a Microsoft Azure Advisor for the community since February this year. In July 2013, James started his own ICT consultancy firm called HybridCloud4You, which is all about transforming datacenters with Microsoft Hybrid Cloud, Azure, AzureStack, Containers, and Analytics like Microsoft OMS Hybrid IT Management. Follow him on Twitter @JamesvandenBerg and on his blog here.

ASP.NET Core 5: Make your options immutable
Anthony Giretti is a specialist in web technologies with 14 years of experience. He specializes in particular in Microsoft .NET and he is currently learning the Cloud Azure platform. He has twice received the Microsoft MVP award and he is also a certified Microsoft MCSD and Azure Fundamentals. Follow him on Twitter @anthonygiretti.

Starting with FIDO2 security keys With Azure Active Directory
Robert Smit is a EMEA Cloud Solution Architect at Insight.de and is a current Microsoft MVP Cloud and Datacenter as of 2009. Robert has over 20 years experience in IT with experience in the educational, health-care and finance industries. Robert’s past IT experience in the trenches of IT gives him the knowledge and insight that allows him to communicate effectively with IT professionals. Follow him on Twitter at @clusterMVP

Microsoft Flight Simulator 2020 running in Windows Virtual Desktop!
Freek Berson is an Infrastructure specialist at Wortell, a system integrator company based in the Netherlands. Here he focuses on End User Computing and related technologies, mostly on the Microsoft platform. He is also a managing consultant at rdsgurus.com. He maintains his personal blog at themicrosoftplatform.net where he writes articles related to Remote Desktop Services, Azure and other Microsoft technologies. An MVP since 2011, Freek is also an active moderator on TechNet Forum and contributor to Microsoft TechNet Wiki. He speaks at conferences including BriForum, E2EVC and ExpertsLive. Join his RDS Group on Linked-In here. Follow him on Twitter @fberson




Recent Comments