by Scott Muniz | Sep 15, 2020 | Uncategorized
This article is contributed. See the original author and article here.
We’re pleased to announce simplified options for registering Surface devices to your Azure AD tenant for Windows Autopilot deployment. Beginning today, customers and partners can submit registration requests directly to Microsoft Support.
The streamlined process means customers no longer need to harvest their own hardware hashes. Instead, they just open a ticket and get the hashes or request Microsoft to register their Surface devices on their behalf, reducing the cost and time hit, especially for customers without dedicated IT resources. This registration by Microsoft also enables Device Firmware Configuration Interface (DFCI) on those devices, allowing customers to make their devices more secure.
Getting started
Before submitting requests, you’ll need to have some basic information about your Azure AD environment and the devices you want to register including:
- Azure Active Directory Tenant ID
- Azure Active Directory Domain Name
- Proof of ownership
- Device serial numbers
For complete details, go to Surface Registration Support for Windows Autopilot.
Zero-touch provisioning
We hope this new initiative will enable more customers to take advantage of zero touch provisioning for full lifecycle management. If you’re not familiar with Windows Autopilot, registration for new or recycled devices allows IT admins to configure Autopilot profiles that can automatically be applied to those devices. Devices are then delivered directly to an end user who needs only to power the device on, connect to a network, and enter their organization credentials. The device will be provisioned into a fully business ready state — secured and managed with all the apps that they need to be productive.
To learn more, check out Windows Autopilot and Surface devices and visit Windows Autopilot – Microsoft 365.

by Scott Muniz | Sep 15, 2020 | Uncategorized
This article is contributed. See the original author and article here.
We are officially one week away from our first ever digital Microsoft Ignite, and Microsoft Teams is bringing you an amazing lineup of content all-digital event experience. Given we’re doing things a little bit differently this year, we want to walk you through what your journey will look like. We’ve created over 40 sessions that span the breadth of Teams so you can hear about the newest product capabilities, get your questions answered, and learn how to create a resilient, inclusive, and connected workplace with Microsoft Teams.

Sessions
For a full list of sessions, check out the Teams digital brochure embedded at the bottom of this blog and bookmark this brochure link for future reference.
Featured Sessions
To kick off the 48 hours of continuous learning, we will be presenting our Modern Work and Teams keynotes. Join sessions from Teams executives and get a detailed view of our vision for Teams, the latest capabilities, and product roadmap.
- The Future of Modern Work – Jared Spataro, Corporate Vice President, Modern Work
- Creating a resilient and hybrid workplace with Microsoft Teams – Nicole Herskowitz, General Manager, Microsoft Teams Marketing
- Enabling collaboration, communication, and knowledge sharing with Microsoft Teams, SharePoint, Project Cortex, and more – Jeff Teper, Corporate Vice President, Microsoft Teams, SharePoint, OneDrive
Digital Breakouts
Next, dive deep into specific Teams topics by attending our 30-min digital breakouts. Digital breakout sessions will cover Teams Meetings, Calling, and Devices; Teams Core and Collaboration; Teams platform and Microsoft 365 platform; Security, Compliance, and Management; and Firstline Worker.
Ask the Experts
If you’re looking to engage with Teams product and engineering experts, join an “Ask the Expert” session following our digital breakouts. “Ask the Experts” are the perfect place to get your Teams questions answered and hear from subject matter experts that are closest to the product. Space is limited in Ask the Expert sessions so make sure you add those to your schedule ASAP.
Resources
Below is a list of resources you can take a look at now to learn more and bookmark to reference later:
- Register for Microsoft Ignite and start building your event schedule with Teams sessions.
- Access the Virtual Hub for deep-dive technical training for IT pros, developers, and community champions available on September 22nd and get access to interactive guides, community resources and more.
- Check out the Microsoft Tech Community Video Hub launching on September 22nd to view videos and join conversation.
- Follow Microsoft Teams on Twitter to stay up to date with the latest Teams @ Ignite news.
Teams Virtual Photo Booth
Staying true to an all-digital theme, we’re very excited to offer a Teams Virtual Photo Booth where you can share your Teams spirit with a selfie! The photo booth will be available from Friday, September 18 at 8:00am PDT to Thursday, September 24.
Come back on Friday to start sharing selfies and what you’re learning at Ignite on your favorite social media platforms. Don’t forget to use the #MicrosoftTeams and #MSIgnite hashtags so we can see what your Teams @ Ignite 2020 experience looks like.
Teams Digital Brochure
by Scott Muniz | Sep 15, 2020 | Uncategorized
This article is contributed. See the original author and article here.
While using Windows Updates for Business (WUfB) is not for everyone, its simplicity and familiar end-user experience make it quite attractive to many organizations. One thing that WUfB does not provide today is updates for third-party products. For that, you need to continue to use an on-premises solution like Microsoft Endpoint Manager Configuration Manager to complement WUfB.
Ultimately, deploying third-party updates when using WUfB is no different than deploying them using Configuration Manager by itself. Enabling third-party updates with WUfB requires the following three things:
- Enable and configure WUfB.
To enable WUfB, configure any WUfB related policy or setting using one of the following methods:
- Configure and enable software updates in Configuration Manager.
See Plan for software updates in Configuration Manager if necessary.
- Configure and enable third-party updates in Configuration Manager.
Do this using a handful of different methods, including the following:
- System Center Update Publisher (SCUP).
- The third-party updates feature set built into Configuration Manager.
- A tool from a third-party.
So, how does Configuration Manager work with WUfB to deliver third-party updates? The answer is dual-scan. Note that although dual-scan did cause some confusion in the past that resulted in the unintended installation of updates, you should not be afraid of it once you see how it works (as described in this post).
Dual-scan
Dual-scan is a feature of the Windows Update (WU) client. It enables the WU client to use WUfB and an on-premises WSUS instance to scan for update applicability and compliance. When you enable dual-scan, the WU client uses WUfB (and only WUfB) for Windows product updates and WSUS for non-Windows updates.
To enable dual-scan, enable a WUfB deferral policy on a system with a local WSUS server configured. This can be a WSUS server integrated into and automatically configured by, Configuration Manager (the scenario discussed here) or a stand-alone WSUS server. That’s all there is to it.
If you don’t want dual-scan, don’t enable any WUfB deferral policies. This is where a disconnect usually happens, as these policies are for WUfB only. They have no effect or purpose if another solution for deploying Windows updates is used, like Configuration Manager or WSUS, but they enable dual-scan.
See Using ConfigMgr With Windows 10 WUfB Deferral Policies for further details on dual-scan and explicitly stopping it.
Results
To prove out deploying third-party updates using Configuration Manager with WUfB enabled, I used one of the existing co-managed systems in my lab. The name of this system is ELKWIN2.
WUfB Configured
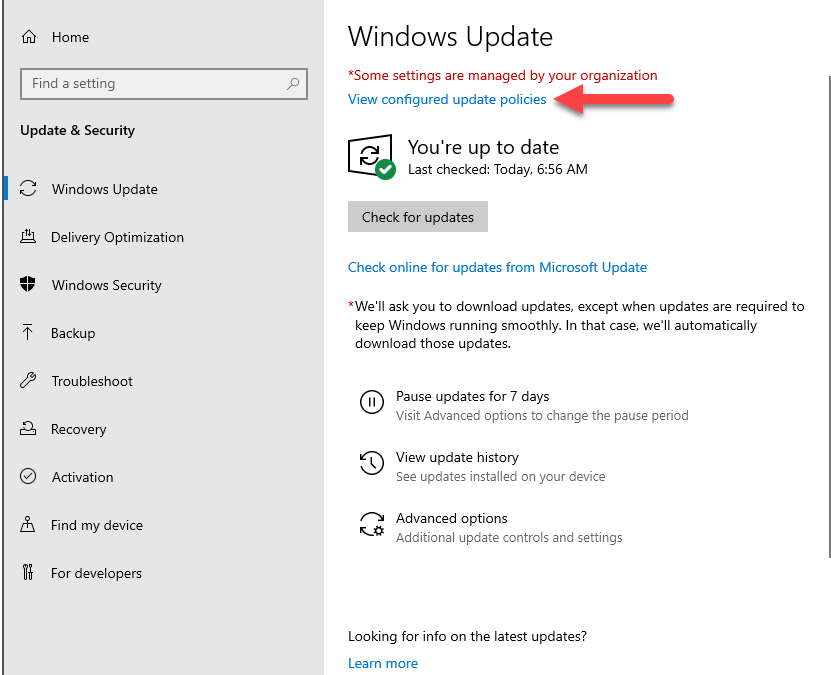
ELKWIN2 started life as a Windows 10 1909 system and was updated to 2004 using WUfB; it continues to receive quality updates from WUfB. You can see the Windows Update configuration in the following two screenshots from ELKWIN2, confirming the WUfB configuration.
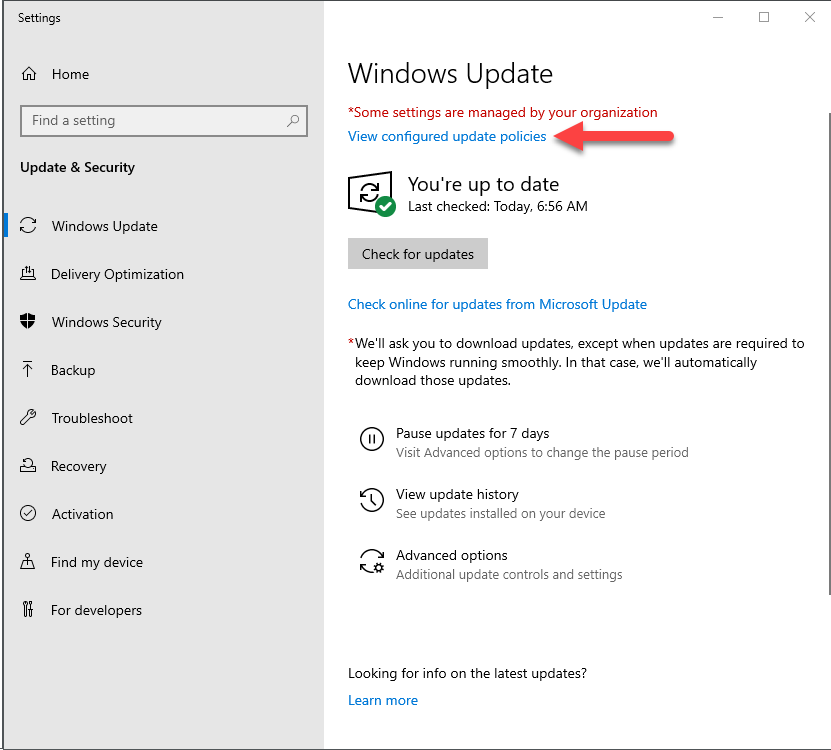 Windows Update settings
Windows Update settings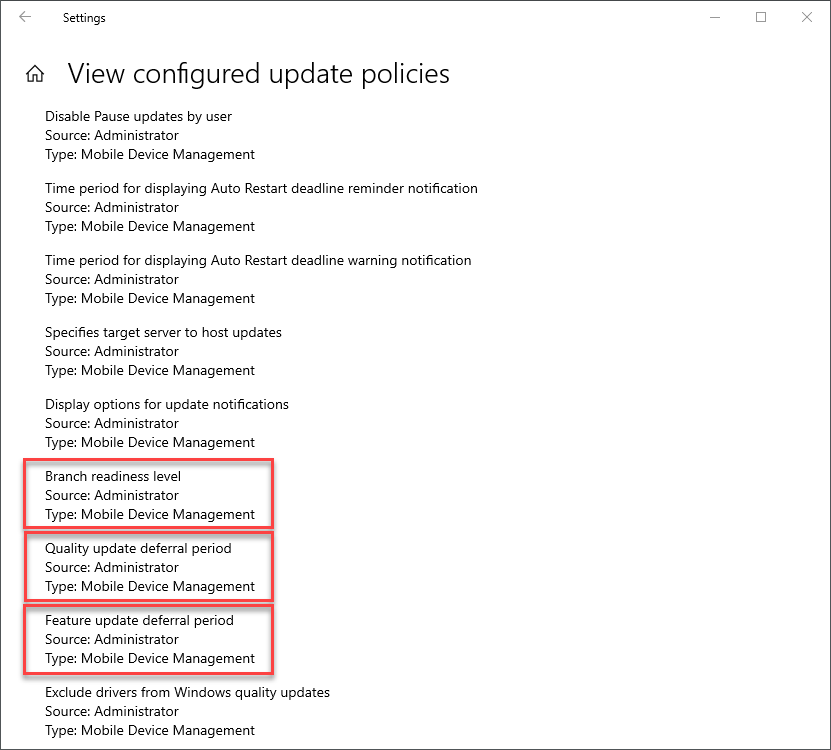 Configured update policies
Configured update policies
Software Updates Configured
Even though WUfB is configured on ELKWIN2 using Intune, the Configuration Manager Software Updates configuration is still targeted to the system and still applies to the system. Since ELKWIN2 is configured for WUfB and has a local WSUS server configured, dual-scan is also enabled. The following two screenshots show the WSUS server configuration and local group policies configured by the Configuration Manager agent.
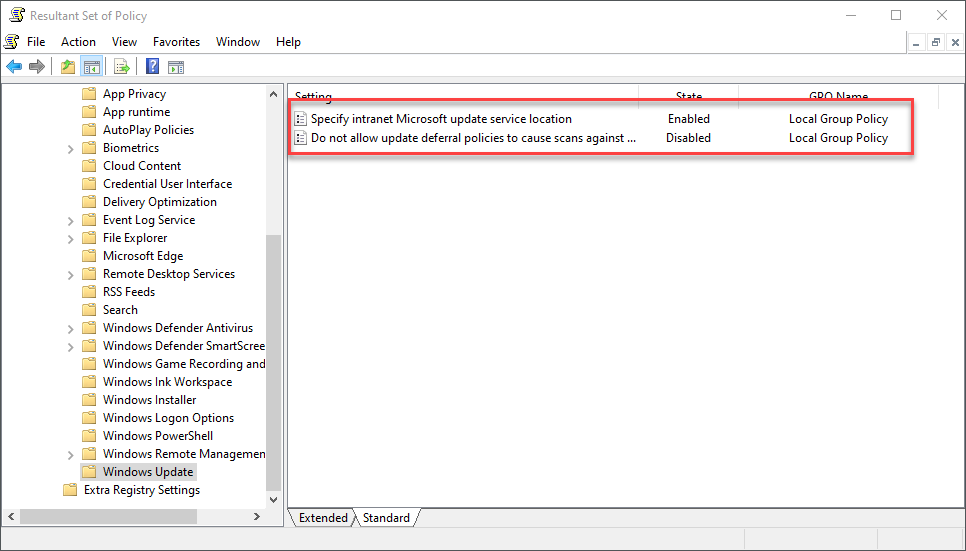 Resultant Set of Policies
Resultant Set of Policies
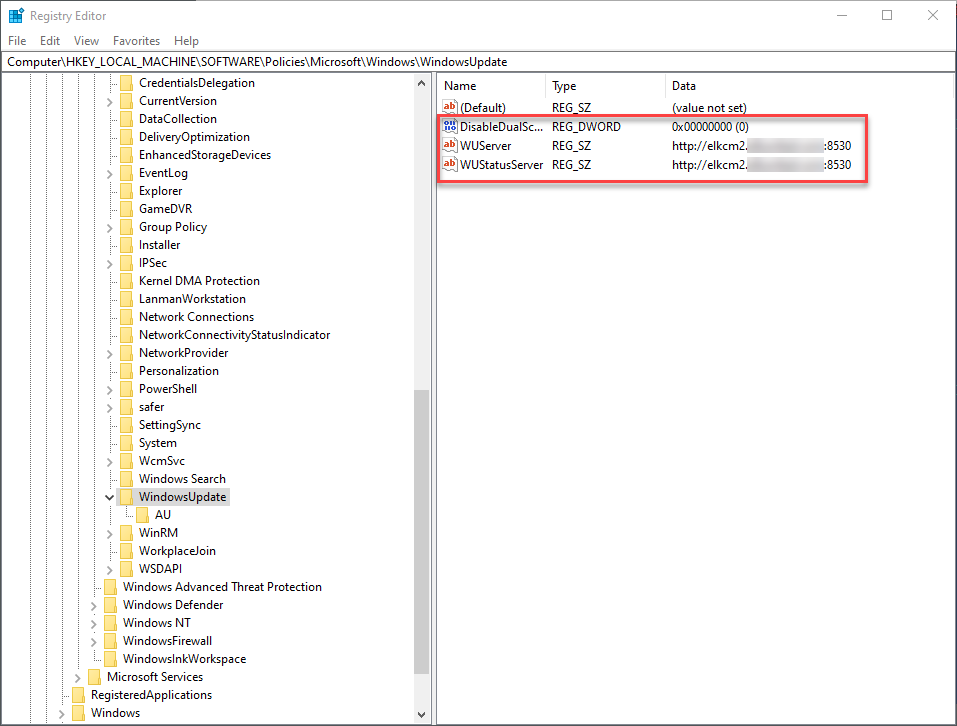 Registry
Registry
Third-party Updates Configured
For this, I created a custom update (for a custom application) in SCUP and published it to the Windows Server Update Services (WSUS) server integrated with the Configuration Manager site in my lab. After synchronizing the update catalog in Configuration Manager, the update showed up in the All Software Updates view, ready for compliance scanning and deployment.
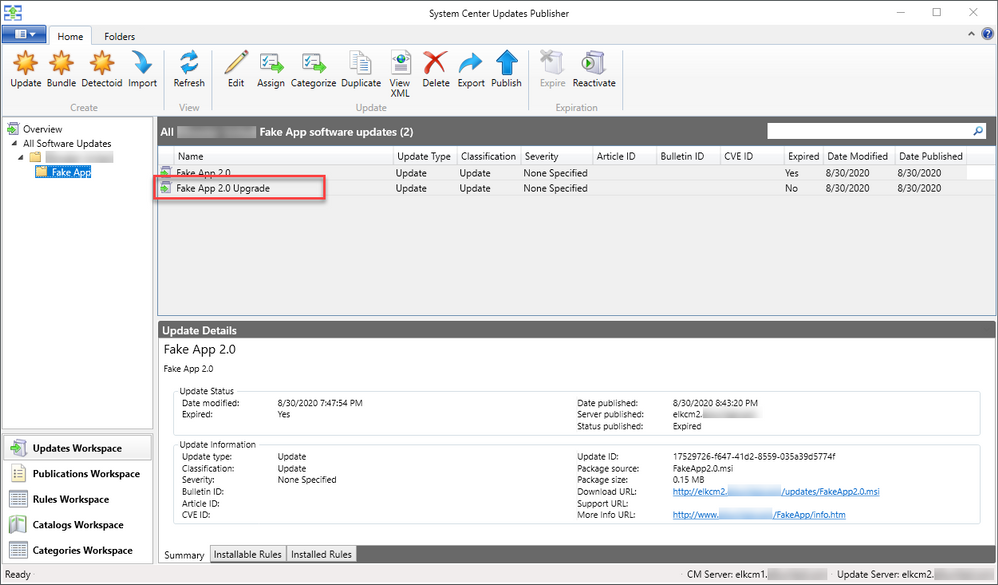 FakeApp 2.0 in System Center Updates Publisher
FakeApp 2.0 in System Center Updates Publisher
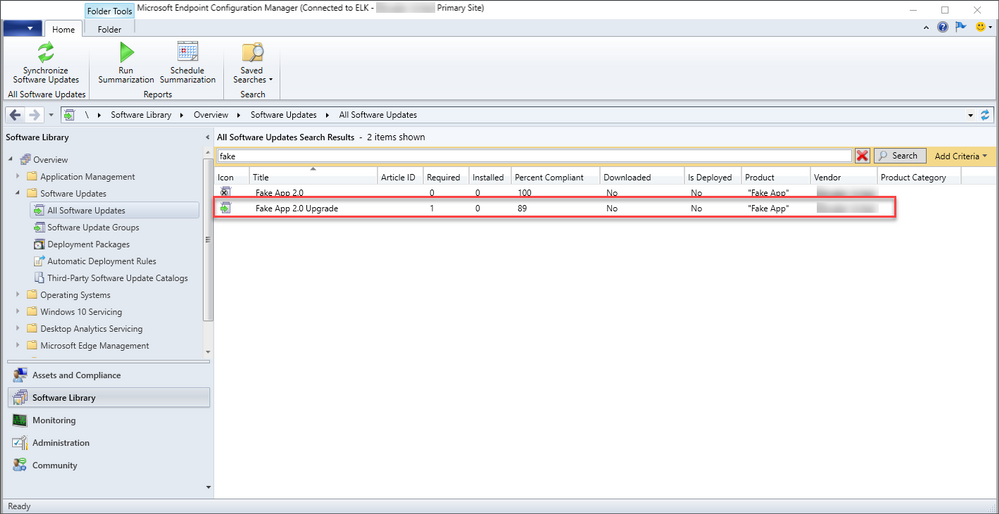 FakeApp 2.0 Upgrade in Configuration Manager
FakeApp 2.0 Upgrade in Configuration Manager
I then initiated a Software Update Scan Cycle from the Actions tab in the Configuration Manager Control Panel applet on ELKWIN2. Finally, I forced ELKWIN2 to send all queued state messages to the site and checked the reports.
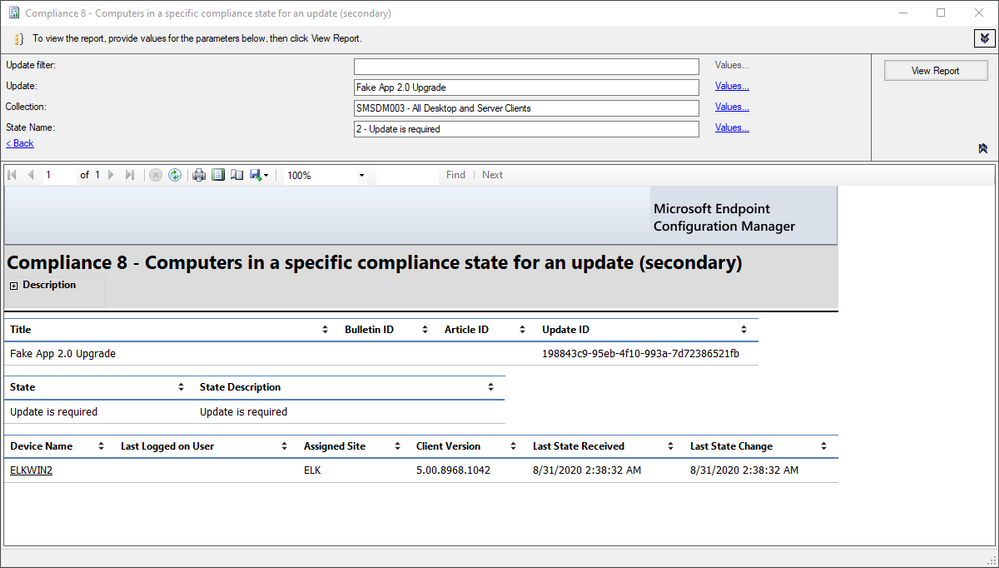 Specific compliance state for an update (FakeApp 2.0 Upgrade)
Specific compliance state for an update (FakeApp 2.0 Upgrade)
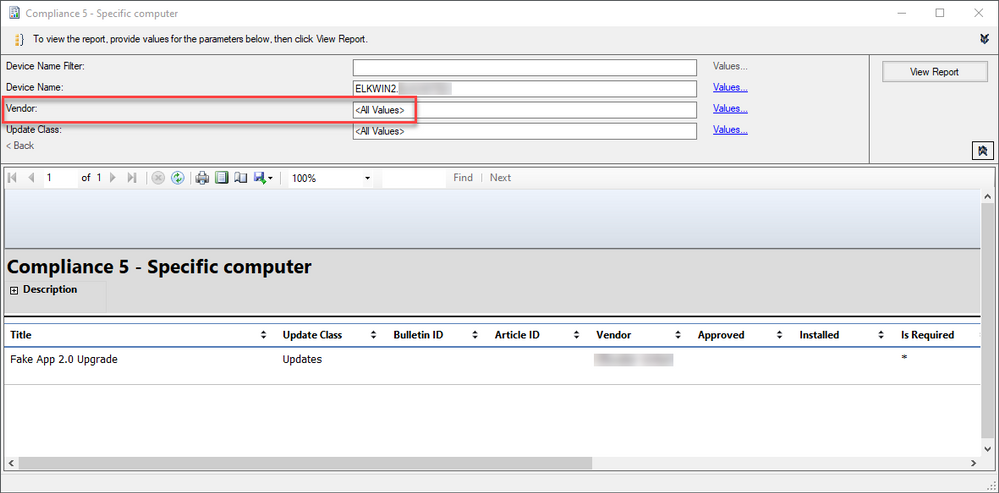 Compliance state for a specific computer (ELKWIN2)
Compliance state for a specific computer (ELKWIN2)
As the reports show, ELKWIN2 requires the FakeApp 2.0 Upgrade. Also, note that no Windows updates show at all for ELKWIN2. That’s dual-scan at work. All that is necessary now is to download and deploy the update or configure an Automatic Deployment Rule to do this for us.
Conclusion
Even though WUfB doesn’t support third-party updates, it’s still possible to deploy and manage them using the ever-faithful Configuration Manager and the built-in Windows dual-scan functionality.
by Scott Muniz | Sep 15, 2020 | Azure, Technology, Uncategorized
This article is contributed. See the original author and article here.
By: Trevor Davis @tredavis and Carlos Villuendas @CarlosV
Challenge
ExpressRoute is the preferred method to connect the customer’s on-premises environment to Azure VMware Solution (AVS), but what happens if you do not have access to ExpressRoute?
Solution
Connect your on-premises site to AVS using VPN and Azure Virtual WAN.
Azure Virtual WAN allows transit connectivity between VPN and ExpressRoute. This implies that VPN-connected sites can communicate with ExpressRoute-connected sites.
Reference: https://docs.microsoft.com/en-us/azure/virtual-wan/virtual-wan-about#transit-er
NOTE: Azure VMware Solution (AVS) is connected to the Azure backbone via an ExpressRoute.
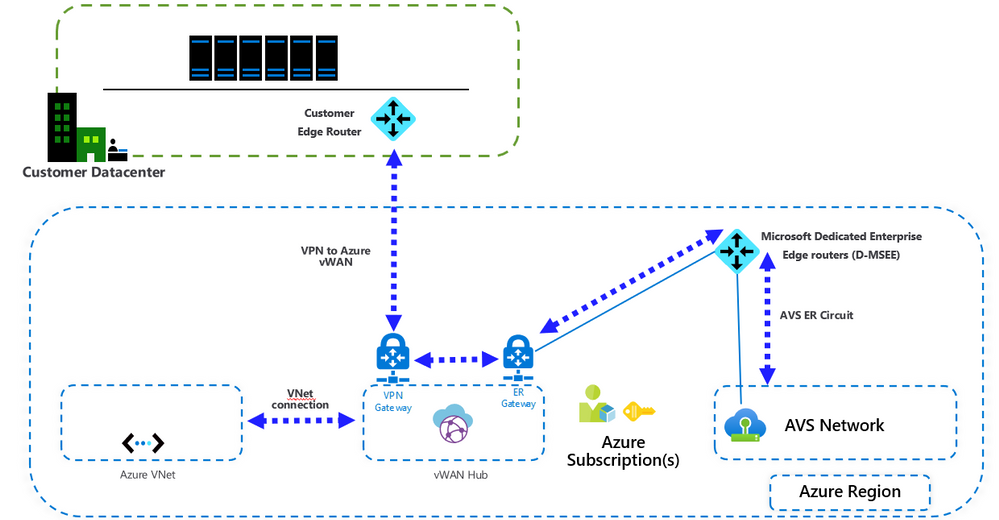
Architecture
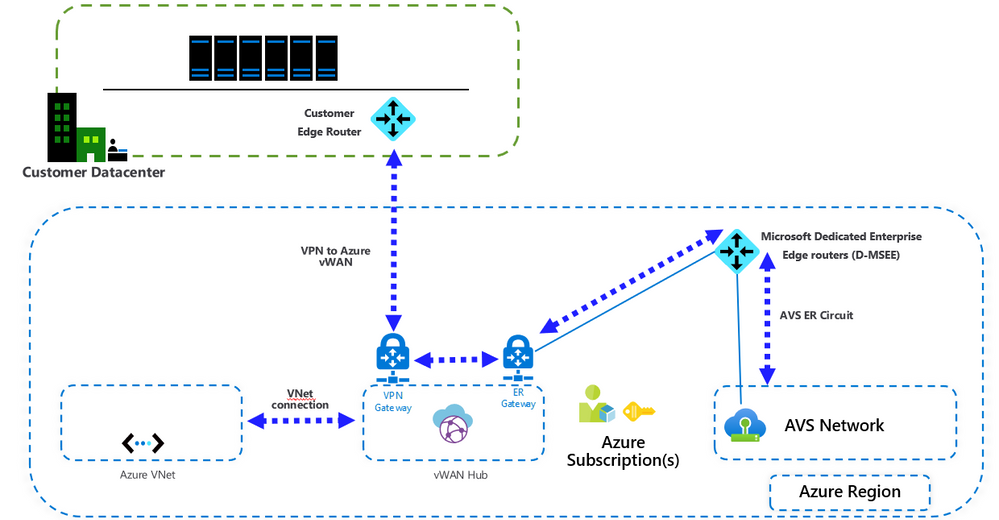
Important points
- VMware HCX is not supported by VMware over VPN. If the customer intends to migrate workloads from on-premises to Azure VMware Solution (AVS), another migration tool needs to be used.
- This configuration requires the standard Azure Virtual WAN type. Check this article for more details.
- When connecting Azure Virtual WAN to a virtual network, make sure that the virtual network does not have any virtual network gateways. This is very important when planning the connection to an existing Azure environment. More details here.
Installation
After Azure VMware Solution is deployed, you can connect your on-premises environment to Azure VMware Solution (AVS) using VPN and Azure Virtual WAN following these steps.
- Create an Azure Virtual WAN.
- Create a hub.
- Create a site.
- Connect a VPN site to a hub.
- Connect a Vnet to a hub (if needed)
- Connect the ExpressRoute circuit to a hub.
Steps 1 to 5 are covered in this article: Create a Site-to-Site connection using Azure Virtual WAN
Step 6 is covered in this article: Create an ExpressRoute association using Azure Virtual WAN
Installation notes:
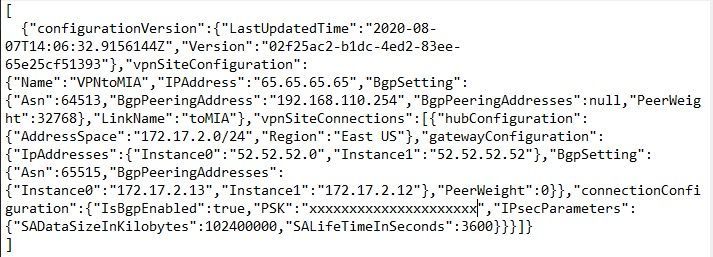
- Format the VPN configuration file to make it more readable.
To configure your on-premises VPN device, you will need to download the VPN configuration from the Azure portal, instructions here. The configuration file will look like the following image. Use VS Code to format the configuration file to look like the example in this article.
- You can connect multiple virtual networks to the virtual WAN hub, even virtual networks from different Azure subscriptions.
by Scott Muniz | Sep 15, 2020 | Uncategorized
This article is contributed. See the original author and article here.
If you are not familiar with the Microsoft 365 Network Connectivity Principles, you should be. Refer to the video Overview of Network Connectivity Principles as a prelude to this topic.
For many companies, providing remote work options was already a rapidly growing movement (+173% since 2005 according to Global Workplace Analytics). That was before the COVID-19 crisis, which has massively accelerated that trend and highlighted a number of remote work problems that require immediate remediation. The need to maintain security without sacrificing performance has generated unprecedented demands on enterprise IT to support work-from-anywhere productivity at a massive scale.
Microsoft 365 is well positioned to help customers fulfill that demand, but high concurrency of users working from home generates a large volume of Microsoft 365 traffic which, if routed through forced tunnel VPN and on-premises network perimeters, causes rapid saturation and runs VPN infrastructure out of capacity. In this new reality, using VPN to access Microsoft 365 is no longer just a performance impediment, but a hard wall that not only impacts Microsoft 365 but critical business operations that still have to rely on the VPN to operate.
For many years enterprises have been using VPNs to support remote experiences for their users. Whilst core workloads remained on-premises, a VPN from the remote client routed through a datacenter on the corporate network was the primary method for remote users to access corporate resources. VPNs, network perimeters, and associated security infrastructure were often purpose built and scaled for a defined volume of traffic, typically with the majority of connectivity being initiated from within the corporate network, and most of it staying within the internal network boundaries.
VPN models where all connections from the remote user device are routed back into the on-premises network (known as forced tunneling) were largely sustainable as long as the concurrent scale of remote users was modest and the traffic volumes traversing VPN were low. The use of forced tunneled VPNs for connecting to distributed and performance sensitive cloud applications is extremely suboptimal. This problem has been growing for a number of years, with many customers reporting a significant shift of network traffic patterns. Traffic that used to stay on premises now connects to external cloud endpoints.
For customers who connect their remote worker devices to the corporate network or cloud infrastructure over VPN, Microsoft recommends that key Microsoft 365 scenarios including Microsoft Teams, SharePoint Online, and Exchange Online are routed over a VPN split tunnel configuration. This becomes especially important as the first line strategy to facilitate continued employee productivity during large scale work-from-home events such as the COVID-19 crisis. The essence of this approach is to provide a simple method for enterprises to mitigate the risk of VPN infrastructure saturation and dramatically improve Microsoft 365 performance in the shortest timeframe possible.
This VPN split tunnel guidance is in alignment with the Microsoft 365 Network Connectivity principles, which are designed to work efficiently for remote users whilst still allowing an organization to maintain security and control over their connectivity. These connectivity principles can also be implemented for remote users very quickly with limited work yet achieve a significant positive impact on the problems outlined above.
Microsoft’s recommended strategy for optimizing remote worker’s connectivity is focused on rapidly alleviating the problems with the traditional approach and providing high performance with a few simple steps. These steps guide you to split tunnel Microsoft 365 traffic for a small number of defined endpoints to bypass bottlenecked VPN infrastructure and leverage cloud-based security services natively available within the Microsoft 365 stack.
For the latest information on how to plan network connectivity for your remote users and provide the best possible cloud experience watch the Network Connectivity for Remote Users video below. This is one video from the 7 part Microsoft 365 Network Connectivity Video Series, which you can find at aka.ms/netvideos.





Recent Comments