Security Controls in Azure Security Center: Enable Endpoint Protection
This article is contributed. See the original author and article here.
With this article, which is part of our recent Azure Security Center (ASC): Secure Score Blog Post Series, we are diving into the Enable Endpoint Protection security control. This security control contains up to 11 recommendations, depending on the resources you have deployed within your environment, and it is worth a maximum of 2 points that count towards your Secure Score. More information about Secure Score can be found here.
Why enabling endpoint protection?
After making sure that your VMs’ management ports are protected, as Kerinne explained in her article, you have already made a huge step towards securing your infrastructure from unauthorized access. However, malware cannot only be downloaded or installed by unauthorized actors, but also inadvertently by legitimate users who are supposed to access your machines. Once a machine is compromised, it could start downloading malware, sending SPAM, execute crypto mining activities, and so on. So, protecting network endpoints is an important step towards enhancing your security posture, but it is not the only security feature that needs to be implemented. With an Endpoint Protection solution, you make sure that if malicious code is found, you have a higher likelihood that it will be detected.
You can find more details about supported endpoint protection solutions here.
Recommendations within the Enable Endpoint Protection security control
The Enable Endpoint Protection security control contains the following 11 recommendations, depending on your environment and agent status:
- Install endpoint protection solution on virtual machines
- Install endpoint protection solution on your machines
- Endpoint protection solution should be installed on virtual machine scale sets
- Endpoint protection health failures should be remediated on virtual machine scale sets
- Endpoint protection health issues should be resolved on your machines
- Monitoring agent should be installed on virtual machine scale sets
- Monitoring agent should be installed on your machines
- Monitoring agent should be installed on your virtual machines
- Log Analytics agent should be installed on your Windows-based Azure Arc machines (Preview)
- Log Analytics agent should be installed on your Linux-based Azure Arc machines (Preview)
- Monitoring agent health issues should be resolved on your machines
The screenshot below shows an environment in which only 7 of those 11 recommendations are within the scope of the Enable endpoint protection security control.
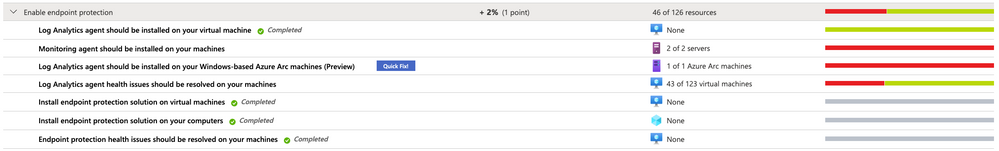
This is because recommendations which do not apply to any resource within your environment do not appear. Basically, the recommendations that can be part of the control can be reduced to four main categories:
Category #1: Install the Log Analytics agent
Azure Security Center relies on the Log Analytics agent to gain information about a server’s current operating system status, events, logfiles, but it is also used to check if a supported endpoint protection solution has been installed on a machine. So, having the monitoring agent installed is mandatory for making sure that your machines are fully monitored and taking advantages of the Azure Security Center Threat Protection for VMs. For the installation, you can use different approaches, depending on what best fits your needs.
The following recommendations belong to this category:
- Monitoring agent should be installed on your virtual machines. This recommendation applies to VMs running in Azure.
- Monitoring agent should be installed on your machines applies to servers which are not running in Azure.
- Monitoring agent should be installed on virtual machine scale sets applies to VM scale sets in Azure
- Log Analytics agent should be installed on your Windows-based Azure Arc machines (Preview) applies to Windows-based Azure Arc machines
- Log Analytics agent should be installed on your Linux-based Azure Arc machines (Preview) applies to Linux-based Azure Arc machines
Category #2: Install one of the support endpoint protection solutions
Besides having the Log Analytics agent installed, of course you want to make sure to have one of the supported endpoint protection solutions installed on your machines. Once you have installed the solution, the particular recommendation that applies to your machine will no longer appear. Only the Microsoft Azure Antimalware solution can be installed directly from the ASC portal. The others need to be installed manually, but then are discovered by Azure Security Center. The following recommendations are part of this category:
- Install endpoint protection solution on virtual machines applies to VMs running in Azure.
- Install endpoint protection solution on your machines applies to machines outside of Azure
- Endpoint protection solution should be installed on virtual machine scale sets applies to VM Scale Sets in Azure.
Category #3: Make sure to resolve Log Analytics Agent health issues
This basically is a single recommendation that is aimed to showing you that one of your machines’ Log Analytics agent is no longer sending data to Azure. This could be an issue with the agent, like the process is no longer running and/or cannot be (re)started, or the machine itself might no longer be working as expected or is switched off. This category is made up of only one recommendation:
- Monitoring agent health issues should be resolved on your machines
We have published more information on possible Log Analytics agent health issues and how to troubleshoot them in the Azure Security Center Troubleshooting Guide.
Category #4: Make sure to resolve health issues with the endpoint protection solution
Besides health issues with the Log Analytics agent, Azure Security Center will also report health issues with the endpoint protection solution itself. Health issues include (but are not limited to) out of date signatures and misconfigured real-time protection, as shown in the following screenshot:
Figure 2 – Remediate endpoint protection health issues
The following recommendations belong to this final category:
- Endpoint protection health failures should be remediated on virtual machine scale sets
- Endpoint protection health issues should be resolved on your machines
Next steps
As with all security controls, you need to make sure to remediate all recommendations within the control that apply to a particular resource in order to gain credit towards your secure score. That means, that both, the Log Analytics agent, and the respective endpoint protection solution you want to use are installed, running, and securely configured. Now, go ahead and remediate the Enable endpoint protection security control in your environment!
Reviewer
Thank you to @Yuri Diogenes, Principal Program Manager in the CxE ASC Team for reviewing this article.


Recent Comments