by Scott Muniz | Aug 5, 2020 | Uncategorized
This article is contributed. See the original author and article here.
Hello everyone and welcome to our mind-blowing series of blogs we have lined up to show you the significant impact of the Azure Active Directory Security Features had for one of our SMC customer.
This blog is a cumulative effort from the Mission Critical Team (Altug, Morne, Nibin & Zoheb).
We will be showcasing in detail what efforts our Identity experts in the Mission Critical Team have gone through for one of our customers in MEA. As a result, we achieved an immense overall improvement in their identity security posture.
Let us start first by introducing ourselves:
Morne: I am an Identity Customer Engineer and have been in Microsoft for 2 years. My primary focus is enablement of the Microsoft hybrid cloud and securing Cloud identities along with the optimization and production remediation of Directory Services. I work as a Designated Support Engineer for this customer.
Zoheb: I am an Azure/Identity Solution Engineer and have been in Microsoft for 7 years in different roles (Microsoft Support, PFE & presently SMC) and working as a SMC lead for this customer.
Nibin: I am an Azure/Identity Sr Solution Engineer and have been in Microsoft for 13 years in different roles (Microsoft Support, PFE & presently SMC) and working as a SMC lead for this customer.
Altug: I am a Sr Solution Engineer specializing in the Manageability and Operations realm. I have been in Microsoft for almost 15 years in different roles (Microsoft Support, PFE & presently SMC).
Before we go in more details, we would like to share some Background on the Microsoft Mission Critical methodology that will enable you to better understand this blog series and the way we work.
|
Microsoft SMC (Support for Mission Critical) Team is the ultimate personalized support experience from Microsoft. Each SMC customer will have designated team that:
· Knows you and knows what your solution means to your enterprise
· Works relentlessly to find every efficiency to help you get ahead and stay ahead
· Advocates for you and helps ensure get you the precise guidance you need 24×7.
|
How the Microsoft Mission Critical team helped secure AAD
To come back to our valuable SMC customer. This customer has an environment of about 25,000 users, was new to Azure Active Directory and ultimately was in the process of exploring as many new features as possible.
The ‘What’
Historically they had to deal with various Security incidents in their environment, which resulted in Identity compromise, phishing, malware attacks etc. They had challenges to Protect, Detect and Respond proactively to these varying levels of compromise.
As our customer’s footprint grew in AzureAD they started observing many similar attack trends in AAD like described below:
- Hundreds of Risky Sign ins reported every day
- More than 1 million incorrect username and password attempts in a month (Password Spray attacks)
- M365 team were detected many phishing emails
- Many impossible travel alerts detected
- Many attempts detected from legacy Browser using weak authentication
The ‘How’
Being part of the Microsoft Solution team, we always go above and beyond to support our customers. The first step is always to quickly resolve the reactive issue, subsequently identify the Root Cause, and finally through our Proactive Delivery Methodology making sure this does not happen again.
Below you will now find the chronological flow of our approach to fix some of the issues over a period.
Each topic described will have a separate blog as all these Individual topics require in depth discussion.
- Risky Sign in’s Process Improvements : We observed that there are hundreds of Risky Sign ins reported every day and our customer wanted to add restrictions which could help secure their users’ Identity.
- Force MFA by Location: All the users were located only in 1 country but were receiving Authentication attempts from across the globe. Considering this risk, we forced MFA for any authentication attempts for Non-Trusted IP users. (Blog link will be updated once posted)
- Eliminating weak passwords for organization: They received more than 1 million bad password attempts in a month. We wanted to protect them against this and one of the remediations we followed was to implement Azure AD Password Protection.
Before enforcing this, they wanted to evaluate the impact, for which we created a custom dashboard that helped them to analyze weak passwords usage in the environment. (Blog link will be updated once posted)
- Reduction in Privileged Identity Users: This is a basic for any Identity platform to implement the least privilege administration model. We reduced the numbers of High Privileged users from 30 to 9, this will further be improved post implementation of PIM. (Blog link will be updated once posted).
- MFA Registration for all users: One of the core pillars of our strategy for Identity protection was MFA, we enrolled all users for MFA in quick time which helped us further strengthen the policies. It was critical to ensure that MFA registration happens only from trusted IP’s. (Blog link will be updated once posted)
- Reducing number of Users synced to AAD: They had more than 60,000 users synced with AAD comparing to the active users which were less than 25,000. This was mainly due to Inactive/Disabled accounts in the On-Premises AD. We collaborated with customers Messaging & Identity team to identify and clean many stale accounts. (Blog link will be updated once posted)
- PIM for Azure Identity roles: PIM enables you to manage, control, and monitor access to important resources in your organization. We used PIM to Provide just-in-time approvals for privileged access to the Azure AD. (Blog link will be updated once posted)
- Enabling Internal Application access through Supported Platforms only: We found that legacy browsers were being used to exploit vulnerabilities and to use weak Authentication methods.
In order to mitigate this concern, we restricted company applications access only through supported Browsers/Apps. (Blog link will be updated once posted)
NOTE: The features and guidelines implemented in this case was specific to this customers requirements and environment, so this is not a “General” guideline to enable any of the mentioned features.
Hope this helps,
Altug, Morne, Nibin & Zoheb
by Scott Muniz | Aug 4, 2020 | Uncategorized
This article is contributed. See the original author and article here.
The 6th cumulative update release for SQL Server 2019 RTM is now available for download at the Microsoft Downloads site. Please note that registration is no longer required to download Cumulative updates.
To learn more about the release or servicing model, please visit:
Starting with SQL Server 2017, we are adopting a new modern servicing model. Please refer to our blog for more details on Modern Servicing Model for SQL Server
by Scott Muniz | Aug 4, 2020 | Alerts, Microsoft, Technology, Uncategorized
This article is contributed. See the original author and article here.
There are many benefits of having domain joined lab VMs in Azure Lab Services, including allowing the students to connect to the VM using their domain credentials. Each VM can be joined to the domain manually, but this is tedious and doesn’t scale when domain joining multiple VMs. To help with this, we have put together some Windows 10 Powershell scripts that a lab owner can execute on the so that every VM started in the lab is automatically joined to the domain and the student is added as a Remote Desktop user.
The scripts use Windows’ task scheduler to automatically run a script when the student VM starts up. The first script, which the lab owner executes on the template VM, registers a scheduled task that will run another script at VM start up. The script then publishes the template VM to create the students’ lab VMs. When a student’s lab VM is started the first time, the script that executes the domain join will automatically run. I would recommend that the VM start and domain join occur before the students need to login as this may take several minutes. If you increase the lab capacity later, those VMs will use the same configuration from the template VM and will be domain joined when they are started the first time. However, if you change the template VM, such as by adding more software or changing the configuration, the first script will need to be run again to set up the scheduled tasks.
The script will need a user, with password, that has permissions to join the domain, you may need to work with your IT department to get the necessary information.
The Azure Lab Service team will be building this functionality directly into the product, in the meantime these scripts will allow you to move forward with Lab Services.
Environments
These scripts work on the following configurations:
- On-premise Active Directory domain
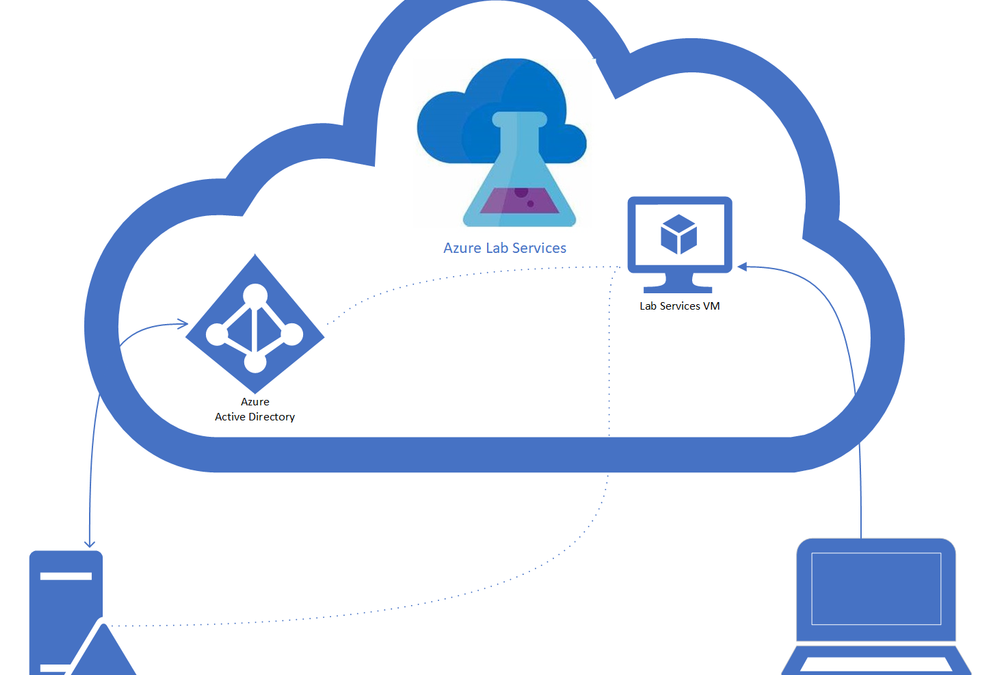
- Hybrid Active Directory domain – An on-premise AD which is connected to an Azure Active Directory through Azure AD Connect. AD Domain Services is installed on an on-premise server, see the diagram below. Applies also to federated domains.

- Azure AD DS Domains – For full-cloud AD (Azure AD + Azure AD DS) or Hybrid AD with secondary Domain Services on Azure.
Lab account and Lab setup
This section focuses on configuring your lab account and lab so that it is connected to your on-premise domain controller. You may need to work with your IT department to get the necessary information and permissions to get the configuration properly setup.
1.) Either option will work:
– Wire up your on-prem Domain Controller on-prem network to an Azure VNet, either with a site-to-site VPN gateway or ExpressRoute.
– Create a secondary managed domain on top of your on-prem one with Azure AD DS (PaaS).
2.) Peer the Lab Account with the connected Virtual Network (VNet).
WARNING: The lab account must be peered to a virtual network before the lab is created.
3.) Create a new lab, with the option enabled to use the same password for all virtual machines.
Where are the scripts
The scripts are available on the along with a readme that has all the details about running the scripts. The scripts require a domain user that can add VMs to the domain, you may need to contact your IT department to get the necessary information.
The scripts are designed to be modular. The first script that is run on the template VM is the Join-AzLabADTemplate.
- Join-AzLabADStudent_RenameVm which renames the VM to a unique name.
- Join-AzLabADStudent_JoinVM which joins the VM to the appropriate domain to an optional organizational unit.
- Join-AzLabADStudent_AddStudent which adds the student that the VM is registered to, to the Remote User group so they can login. If the VM isn’t registered to a user the task is skipped.
Here are two additional scripts that aren’t part of the domain-join process that will help manage the VMs.
- Set-AzLabCapacity, which allows you to change the capacity of the lab from the template VM.
- Set-AzLabADVms, which starts all the VMs from the template VM. This script can be run to get all the VMs domain-joined instead of having the domain-join occur when the students start the VM.
If you have any questions, feel free to post them at the community forum. For issues with the scripts, add an issue to the GitHub repository.
Thanks
Roger Best
by Scott Muniz | Aug 4, 2020 | Uncategorized
This article is contributed. See the original author and article here.
Privacy is a fundamental human right. “We are committed to providing products, information, and controls that let you choose how your data is collected and used.” Brad Smith, President & Chief Legal Officer
In May (skip below to read the announcement) we announced our plans to provide more granular privacy controls with the Microsoft Graph.
The hundreds of millions of users of Microsoft 365 cloud services form part of the core of Microsoft Graph. The users’ data is carefully managed, protected, and with proper authorization, made available by Microsoft Graph services to drive productivity and creativity in businesses. As ubiquitous the user’s data is in Microsoft Graph, data derived from the user’s social interactions is particularly interesting. It provides intelligent insights that can answer questions such as the following:
- “Who should this user contact for information on this topic?”
- “Which documents are most interesting to this person?”
For administrators who wish to enable granular control over where intelligent insights are available to their employees, these new controls provide you the ability to configure the visibility of Graph-derived insights, between users and other items in the Graph (such as documents or sites) across apps and services in Microsoft 365. Learn more about Graph-based insights at https://docs.microsoft.com/en-us/graph/social-intel-concept-overview?view=graph-rest-1.0#why-integrate-with-document-based-insights.
Learn more about how to configure the new Microsoft Graph privacy controls at https://docs.microsoft.com/en-us/graph/insights-customize-item-insights-privacy?view=graph-rest-1.0.
Announced in May 2020
The Microsoft Graph is the gateway to data and intelligence in Microsoft 365, providing a unified programmability model that you can use to access the tremendous amount of data in Microsoft 365, Windows 10, and Enterprise Mobility + Security. Over the next several weeks we’re excited to introduce new innovation to help you achieve more with Microsoft Graph capabilities.
In Microsoft 365 we’re committed to privacy and control – and we’re continuing to invest in those principals with new Microsoft Graph privacy controls of document-based insights.
Across Microsoft 365 applications and services, intelligence is pervasive – whether deep learning or reasoning across activities and relationships – intelligence in Microsoft 365 is designed to help its users achieve more…
At the center of Microsoft 365 is content, such as documents, email messages, conversations, and more. With the amount of data expected to double year over year, information overload is often a reality. This is where the Microsoft Graph shines. Time is something we can’t make more of, but we can make more with it. Document-, email-, calendar-, and user- based insights help save time and boost productivity, helping employees make more of their time.
One of the first applications to deliver these rich insights was Office Delve, powered by the Office Graph – technology which calculated relationships between people and content from Exchange, OneDrive, SharePoint, and more. Along with the Office Graph and Delve, we also delivered shared set of privacy settings, which control both insights and Delve user experience.
As the Office Graph continued to evolve, it has become a more independent, mature, and powerful service, and a part of every Microsoft 365 experience, eventually evolving to the Microsoft Graph. Given this evolution, we’ve disjoined the privacy story for two independent pieces, providing the flexibility to fine-tune item in the Graph and Delve.
Today we’re pleased to announce a set of robust new privacy settings which provides you the ability to configure the visibility of Graph-derived insights, between users and other items in the Graph (such as documents or sites). This new setting will apply similar restrictions as the original Delve settings, but decoupled from Delve. This means that you can disable the Delve app through the existing controls, but allow other insights-based experiences such as Discover in OneDrive and Suggested Sites in SharePoint Home to still provide assistance.
For organizations that need to disable item insights for all its users, we are introducing a new “isEnabledInOrganization” parameter, which allows you to disable item insights across the entirety of your organization; however, if you only need to disable item insights for a subset of employees, we’re introducing an additional “disabledForGroup” setting – an ID of one security or O365 Azure AD group.
This new setting will allow security group administrators more flexible management options using the available tools in Azure Active Directory, disabling item insights for all members of select groups. Both parameters can be configured using new MSGraph methods.
While delivering these new privacy settings we’ll respect both the existing Delve settings and these new item-insights settings, applying the strictest of them. This means that during transition phase a user is considered as opted out if either the user was opt out by Delve controls or item insights settings.
As we continue to provide more granular privacy controls, we’ll also introduce new user level controls, to provide individuals control over the visibility of their own item insights, unless otherwise specified by other admin-facing settings such as “isEnabledInOrganization” or “disabledForGroup”. At the time of release, we will also support migration of pre-existing Delve settings into new user control.
Bookmark this article to keep up to date on our commitment to privacy via the Microsoft Graph.
by Scott Muniz | Aug 4, 2020 | Uncategorized
This article is contributed. See the original author and article here.
We are pleased to announce the final release of the security configuration baseline settings for Windows 10 and Windows Server version 2004.
Please download the content from the Microsoft Security Compliance Toolkit, test the recommended configurations, and customize and implement as appropriate. If you have questions or issues, please let us know via the Security Baseline Community.
This Windows 10 feature update brings very few new policy settings, which we list in the accompanying documentation. Only one new policy meets the criteria for inclusion in the security baseline (described below), and we are removing one setting from the baseline. There are two additional policies we are not including in the baseline because of compatibility concerns, but which you may want to consider for your organization.
LDAP Channel Binding Requirements (Policy updated)
In the Windows Server version 1809 Domain Controller baseline we created and enabled a new custom MS Security Guide setting called Extended Protection for LDAP Authentication (Domain Controllers only) based on the values provided here. This setting is now provided as part of Windows and no longer requires a custom ADMX. An announcement was made in March of this year and now all supported Active Directory domain controllers can configure this policy. The value will remain the same in our baseline, but the setting has moved to the new location. We are deprecating our custom setting. The new setting location is: Security SettingsLocal PoliciesSecurity OptionsDomain controller: LDAP server channel binding token requirements.
Note: this new policy requires the March 10, 2020 security update. (We assume that, as security conscious baselines users, you are patching!) Details of that patch are here.
Microsoft Defender Antivirus File Hash (Worth considering)
Microsoft Defender Antivirus continues to enable new features to better protect consumers and enterprises alike. As part of this journey Windows has a new setting to compute file hashes for every executable file that is scanned, if it wasn’t previously computed. You can find this new setting here: Computer ConfigurationsAdministrative TemplatesWindows ComponentsMicrosoft Defender AntivirusMpEngineEnable file hash computation feature.
You should consider using this feature to improve blocking for custom indicators in Microsoft Defender Advanced Threat Protection (MDATP). This new feature forces the engine to compute the full file hash for all executable files that are scanned. This can have a performance cost, which we minimize by only generating hashes on first sight. The scenarios where you may want to test more thoroughly for performance include devices where you frequently create new executable content (for example, developers) or where you install or update applications extremely frequently.
Because this setting is less helpful for customers who are not using MDATP, we have not added it to the baseline, but we felt it was potentially impactful enough to call out. If you chose to enable this setting, we recommend throttling the deployment to ensure you measure the impact on your users’ machines.
Account Password Length (Worth considering)
In the Windows 10 1903 security baselines we announced the removal of the account password expiration policy. We continue to invest in improving this experience. With Windows 10 2004, two new security settings have been added for password policies: ‘Minimum password length audit’ and ‘Relax minimum password length limits’. These new settings can be found under Account PoliciesPassword Policy.
Previously, you could not require passwords/phrases greater than 14 characters. Now you can! Being able to require a length of more than 14 characters (maximum of 128) can help better secure your environment until you can fully implement a multi-factor authentication strategy. Our vision remains unchanged in achieving a password-less future, but we also recognize that this takes time to fully implement across both your users and your existing applications and systems.
You should be cautious with this new setting because it can potentially cause compatibility issues with existing systems and processes. That’s why we introduced the ‘Minimum password length audit’ setting, so you can see what will happen if you increase your password/phrase length. With auditing you can set your limit anywhere between 1 and 128. Three new events are also created as part of this setting and will be logged as new SAM events in the System event log: one event for awareness, one for configuration, and one for error.
This setting will not be added to the baseline as the minimum password length should be audited before broad enforcement due to the risk of application compatibility issues. However, we urge organizations to consider these two settings. Additional details about these new settings will be found here, once the new article get published in the coming days.
(NOTE: As of the today the link is not yet live, we are actively working to ensure it gets posted soon!)
As a reminder, length alone is not always the best predictor of password strength, so we strongly recommend considering solutions such as the on-premise Azure Active Directory Password Protection which does sub-string matching using a dictionary of known weak terms, and rejects passwords that don’t meet a certain score.
Turn on Behavior Monitoring (Policy removed)
In keeping with our principals of criteria for baseline inclusion we have found that the following setting does not need to be enforced; there is no UI path to the setting, you must be a privileged account to make the change, lastly we do not feel a mis-informed Admin would change this setting. Based on these principals we are removing Computer ConfigurationAdministrative TemplatesWindows ComponentsMicrosoft Defender AntivirusReal-time ProtectionTurn on behavior monitoring
Tooling updates
Finally, we do have some enhancements for LGPO and Policy Analyzer coming very shortly after this release! We will go into more details on these enhancements in a future blog post!
Baseline criteria
We follow a streamlined and efficient approach to baseline definition when compared with the baselines we published before Windows 10. The foundation of that approach is essentially:
- The baselines are designed for well-managed, security-conscious organizations in which standard end users do not have administrative rights.
- A baseline enforces a setting only if it mitigates a contemporary security threat and does not cause operational issues that are worse than the risks they mitigate.
- A baseline enforces a default only if it is otherwise likely to be set to an insecure state by an authorized user:
- If a non-administrator can set an insecure state, enforce the default.
- If setting an insecure state requires administrative rights, enforce the default only if it is likely that a misinformed administrator will otherwise choose poorly.
For further illustration, see the “Why aren’t we enforcing more defaults?” section in this blog post.
As always, please let us know your thoughts by commenting on this post.





Recent Comments