Our Latest News
OpenAI and Microsoft Sentinel Part 4: What does the future hold?
Welcome to the conclusion of our series on OpenAI and Microsoft Sentinel! Back in Part 1, we introduced the Azure Logic Apps connector for OpenAI and explored the parameters that influence text completion from the GPT3 family of OpenAI Large Language Models (LLMs)...
Revolutionize customer service with next-generation AI
We're entering the era of next-generation AI that is driving new levels of productivity and efficiency, unleashing new innovations in the customer service space. AI is profoundly changing how customers engage with businesses and how agents provide exceptional service...
Converting X12 EDI Health Insurance Claims to FHIR
Processing health insurance claims can be quite complex. This complexity is driven by a few factors, such as the messaging standards, the exchange protocol, workflow orchestration, all the way to the ingestion of the claim information in a standardize and scalable...
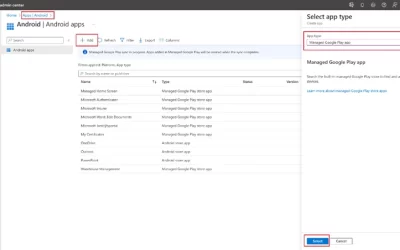
How to mass deploy Dynamics 365 Warehouse Management – Mobile App
Automating the deployment and configuration of Warehouse Management can be more efficient for big-scale deployments if you have a lot of devices to manage. One solution for this is using a mobile device management (MDM) solution such as Microsoft Intune, but not...
Create inclusive content with the new Accessibility Assistant in Microsoft 365
Inaccessible content is everywhere in the digital world. Today, we’re introducing Accessibility Assistant in Microsoft 365 to help creators produce more accessible content with less effort, all in the flow of work. The post Create inclusive content with the new...
Delivery Optimization report now generally available
Start monitoring Delivery Optimization usage and performance across your organization today! Following the Windows Update for Business reports announcement back in November 2022, we are excited to announce the general availability of the Delivery Optimization Windows...
Crypto investment scammers are targeting your community groups
Microsoft Bookings now integrates with Webex using Power Automate
One of the most common pain points of scheduling online meetings, especially with people outside your organization, is the back-and-forth messages. Microsoft Bookings now makes it simple to avoid that back and forth, with Power Automate you can seamlessly integrate...
What to know about the U.S. Census Bureau’s American Community Survey
Outlook Mac for All
Today we have an exciting announcement to share about the evolution of Microsoft Outlook for macOS. Don’t have Outlook on your Mac yet? Get Outlook for Mac in the App Store. An image demonstrating the user interface of Outlook for Mac. Outlook for Mac is now free to...
Introducing Microsoft Dynamics 365 Copilot, bringing next-generation AI to every line of business
Introducing the world's first AI copilot in both CRM and ERPToday we announced Microsoft Dynamics 365 Copilot, providing interactive, AI-powered assistance across business functionsfrom sales, service, and marketing to supply chain. With Dynamics 365 Copilot, we're...




Recent Comments