Our Latest News
CISA and CNMF Analysis of SolarWinds-related Malware
CISA and the Department of Defense (DoD) Cyber National Mission Force (CNMF) have analyzed additional SolarWinds-related malware variants—referred to as SUNSHUTTLE and SOLARFLARE. One of the analyzed files was identified as a China Chopper webshell server-side...
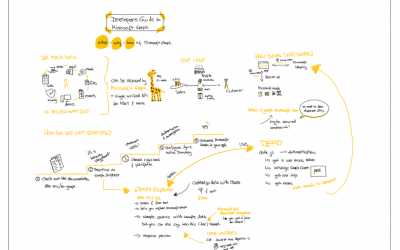
LearnTogether: Build Apps with Microsoft Graph ?
This week, I had the great pleasure to attend Microsoft's Learn Together: Build apps for Microsoft Graph event. I also did sketchnotes of the event, you may find high resolution files (images, gifs and mp4) are available here on GitHub. Call to action: Learn...
Seize the deal and build for real
Sure, being a student comes with homework, exams, and other harsh realities. But while you’re in school, you also have a rare and beautiful gift: student discounts. As the Audience Evangelism Manager on the Azure for Students team at Microsoft, Ryan Mendenhall...
NSA-CISA-FBI Joint Advisory on Russian SVR Targeting U.S. and Allied Networks
Official websites use .govA .gov website belongs to an official government organization in the United States. Secure .gov websites use HTTPS A lock () or https:// means you've safely connected to the .gov website. Share sensitive information only on official, secure...
FTC and DOJ bring first case under new COVID-19 consumer protection law
There are no supplements proven to treat or prevent COVID-19. But that doesn’t stop some companies from making these kind of unsubstantiated claims, or even false claims that their products work as well — or better — than available COVID-19 vaccines. If you see claims...
Google Releases Security Updates for Chrome
Google has updated the stable channel for Chrome to 90.0.4430.72 for Windows, Mac, and Linux. This version addresses vulnerabilities that an attacker could exploit to take control of an affected system.CISA encourages users and administrators to review the Chrome...
Juniper Networks Releases Security Updates
Juniper Networks has released security updates to address vulnerabilities in multiple products. An attacker could exploit some of these vulnerabilities to take control of an affected system.CISA encourages users and administrators to review the Juniper Security...
NAME:WRECK DNS Vulnerabilities
Cybersecurity researchers from Forescout and JSOF have released a report on a set of nine vulnerabilities—referred to as NAME:WRECK—affecting Domain Name System (DNS) implementations. NAME:WRECK affects at least four common TCP/IP stacks—FreeBSD, IPNet, NetX, and...
Experiencing Data Access Issue in Azure portal for Log Analytics – 04/15 – Investigating
Initial Update: Thursday, 15 April 2021 10:22 UTCWe are aware of issues within Log Analytics and are actively investigating. Some customers may experience data access, data gaps, data latency and missed or delayed alerts in UAE Central region..Work Around: NoneNext...
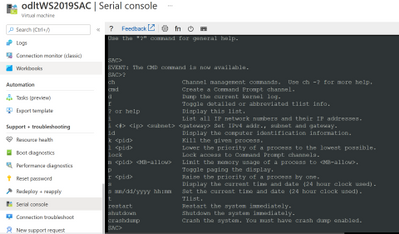
Using the Serial Console on Windows IaaS VMs
If you make a mistake when configuring operating system firewall rules that block you from accessing the VM, or a service is stopping an IaaS VM from booting, or some other configuration problem such as a newly installed application is stopping you from accessing a...
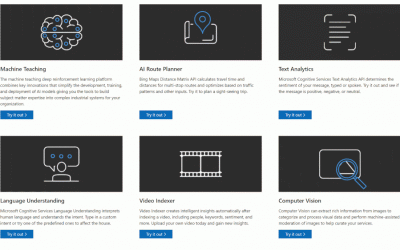
Integrating AI: Best Practices and Resources to Get Started with Azure Cognitive Services
We use AI (Artificial Intelligence) integrated applications daily, from search engines optimized to find the most relevant content, to recommendation engines for streaming or shopping. During AI’s early...
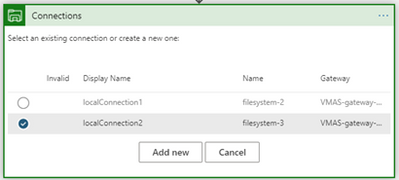
Find out which On-premises Data Gateways are used by which API connection resources
API connections resources work as the bridges for Logic App to communicate with other services. While most of them are used to connect to cloud resources, a few of them leverage On-premises Data Gateways to connect local data sources to Azure....


Recent Comments