Our Latest News
Lesson Learned #169: Bulk Insert using Python in Azure SQL
Today, I worked in a very interesting case where our customer wants to insert millions of rows using Python. We reviewed two alternatives to import the data as soon as possible: Using BCP command line and using executemany command. Following I would like to share my...
Microsoft 365 PnP Community Spotlight: Mikael Svenson
Which community project do you maintain? PnP Modern Search How does it help people? Coming from classic SharePoint many customers were used to the flexible search web parts available. In modern SharePoint there is a gap between...
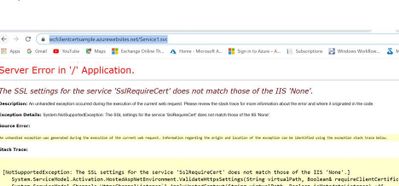
Setting up Client Certificate Authentication for WCF Service hosted as an Azure Web App
Recently I worked on a scenario where we had to set up client cert authentication for WCF service hosted as an App service in Azure: We followed the below steps to achieve the same and was able to parse the client certificate in service end using custom certificate...
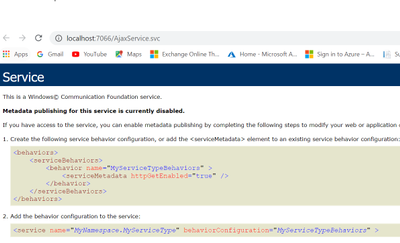
Disable proxy output for /jsdebug or /js endpoint of WCF service consumed using Javascript or Ajax
Recently I worked on a scenario where we had to disable the proxy output for /jsdebug or /js endpoint for security concerns: We were able to achieve the same using following steps: When we consume a Wcf service or Webservice using Java script client or...
De-risk your lateral movement paths with Microsoft Defender for Identity
Microsoft Defender for Identity is focused on protecting on-premises identities and allowing security analysts to pinpoint vulnerabilities before an attack can occur. A key feature that allows analysts to achieve this is by viewing the evidence relates to lateral...
WordPress Releases Security and Maintenance Update
Official websites use .govA .gov website belongs to an official government organization in the United States. Secure .gov websites use HTTPS A lock () or https:// means you've safely connected to the .gov website. Share sensitive information only on official, secure...
Announcing the iOS/iPadOS Security Configuration Framework
As mobile usage becomes more prevalent, so does the need to protect your work or school data on those devices. In March 2020, we introduced the App Protection Policy Data Protection Framework to help organizations determine which Intune app protection policy settings...
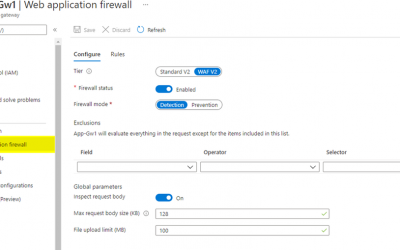
Azure Web Application Firewall: WAF config versus WAF policy
What is Web Application Firewall (WAF) config? WAF config is the built-in method to configure WAF on Azure Application Gateway, and it is local to each individual Azure Application Gateway resource. When you create an Azure Application Gateway with either the WAF or...
HMI review: building more agile factories with Azure IoT and Windows IoT
Today wraps up Hannover Messe 2021, one of the world’s leading industrial trade shows. This annual event attracts more than 200,000 visitors and highlights the latest in technology across six topic areas: Automation, Motion & Drive, Digital Ecosystems, Logistics,...
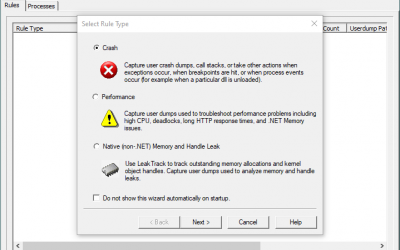
Collect memory dumps for a first-chance exception, when it occurs
The following two procedures guide on how to properly collect a memory dump to study a process crash. This post complements my article about how exceptions are handled and how to collect memory dumps to study them. Both tools below - ProcDump and...
Friday Five: Azure Key Vault, Teams Tips, More!
Step by Step Manage Windows Server in Azure with Windows Admin Center Robert Smit is a EMEA Cloud Solution Architect at Insight.de and is a current Microsoft MVP Cloud and Datacenter as of 2009. Robert has over 20 years experience in IT with experience in the...
Security baseline for Microsoft Edge, version 90
We are pleased to announce the enterprise-ready release of the security baseline for Microsoft Edge, version 90! We have reviewed the new settings in Microsoft Edge version 90 and determined that there are no additional security settings that require...




Recent Comments