Our Latest News
Optimizing Your Marketing Efforts with Google Analytics
Utilizing Google Analytics for your website is crucial if you want to know where your audience is coming from, what keywords they used to arrive at your website, and what they are looking for when they arrive. Google Analytics is an invaluable marketing tool. It is...
Microsoft Compliance – Paint By Numbers Series (Part 5) – Advanced eDiscovery
Disclaimer This document is not meant to replace any official documentation, including those found at docs.microsoft.com. Those documents are continually updated and maintained by Microsoft Corporation. If there is a discrepancy between this document and...
New pricing for Microsoft 365
Today we are announcing changes to our commercial pricing for Microsoft 365—the first substantive pricing update since we launched Office 365 a decade ago. The post New pricing for Microsoft 365 appeared first on Microsoft 365 Blog.
WARNING: Email from FTC Chair Lina Khan about Coronavirus money is fake
Scammers are impersonating FTC Chair Lina Khan in a new phishing scheme. The email says the FTC wants to send you Coronavirus relief funds and tells you to send some personal information, like your name, address, and date of birth. The FTC is not distributing...
WARNING: Email from FTC Chair Lina M. Khan about Coronavirus money is fake
Scammers are impersonating FTC Chair Lina M. Khan in a new phishing scheme. The email says the FTC wants to send you Coronavirus relief funds and tells you to send some personal information, like your name, address, and date of birth. The FTC is not distributing...
ISC Releases Security Advisory for BIND
The Internet Systems Consortium (ISC) has released a security advisory that addresses a vulnerability affecting multiple versions of the ISC Berkeley Internet Name Domain (BIND). A remote attacker could exploit this vulnerability to cause a denial-of-service...
Cisco Releases Security Updates for Multiple Products
Cisco has released security updates to address vulnerabilities in multiple Cisco products. An attacker could exploit some of these vulnerabilities to take control of an affected system. For updates addressing lower severity vulnerabilities, see the Cisco Security...
An Overview of Sign Language: Clearing Up Misconceptions
A common misconception about Sign Language is that all deaf & hard-of-hearing individuals and learners use only one universal version of Sign Language. But did you know that there are over 200 different Sign Languages? Sign Language...
PetitPotam? Microsoft Defender for Identity has it covered!
If you didn’t grow up in the '90s in France like yours truly, you probably wouldn’t be familiar with the animated kids show named Petit Potam, which was based on the books of the same name by Christine Chagnoux. While I could talk about the TV series for days,...
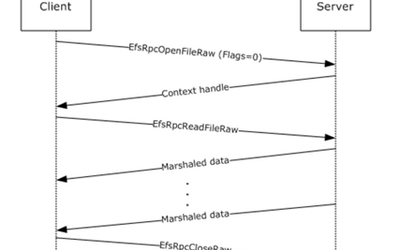
Use Azure Storage Table REST API with AAD token via PostMan
You can refer to below steps for scenarios in which you have an application special requirement and need to call raw Storage table REST API from your dev environment via Postman. It consists of two main HTTP requests: first, to authenticate directly using AD security...
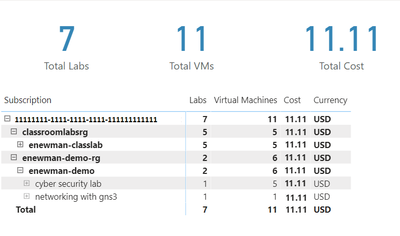
Power BI Reports for Azure Lab Services – Part 1: Visualizing Cost Management Data
Azure Lab Services costs are integrated with Cost Management on the lab account level. However, sometimes it’s useful to create a custom report for your team. We can do this using the line item data from Cost Management. In this blog post we will use...
Four essentials to collaborate as one business, everywhere
Across every industry, we're all navigating the new world of hybrid work. Together, we're building a blended model that enables more flexibility in when, where, and how people work, and that model is here to stay. But organizations can't let flexibility turn into...







Recent Comments