Our Latest News
APT Actors Exploiting CVE-2021-44077 in Zoho ManageEngine ServiceDesk Plus
Summary This joint Cybersecurity Advisory uses the MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK®) framework, Version 9. See the ATT&CK for Enterprise framework for referenced threat actor techniques and for mitigations. This joint...
NSA and CISA Release Part III of Guidance on Securing 5G Cloud Infrastructures
CISA has announced the joint National Security Agency (NSA) and CISA publication of the third of a four-part series, Security Guidance for 5G Cloud Infrastructures. Part III: Data Protection examines security during all phases of the data lifecycle—in...
Azure Marketplace new offers – Volume 177
We continue to expand the Azure Marketplace ecosystem. For this volume, 115 new offers successfully met the onboarding criteria and went live. See details of the new offers below: Get it now in our marketplace Accelario DataOps Platform for MySQL Databases: Accelario...
Unlock hidden insights in your Finance and Operations data with data lake integration
You chose Dynamics 365 for your enterprise to improve visibility and to transform your business with insights. Is it a challenge to provide timely insights? Does it take too much effort to build and maintain complex data pipelines?If your solution includes using a...
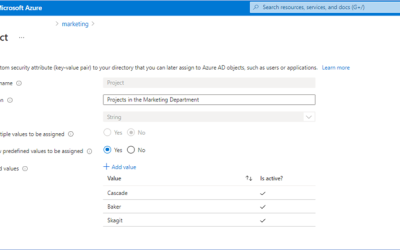
Introducing Azure AD custom security attributes
This public preview of Microsoft Azure Active Directory (Azure AD) custom security attributes and user attributes in ABAC (Attribute Based Access Control) conditions builds on the previous public preview of ABAC conditions for Azure Storage. Azure AD custom security...
New Microsoft Teams Essentials is built for small businesses
Perhaps no one has been hit harder over the past 20 months than small businesses. To adapt and thrive in this new normal, small businesses need comprehensive solutions that are designed specifically for them and their unique needs. The post New Microsoft Teams...
CISA Adds Five Known Exploited Vulnerabilities to Catalog
CISA has added five new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence that threat actors are actively exploiting the vulnerabilities listed in the table below. These types of vulnerabilities are a frequent attack vector for...
Ignite 2021 – The do not miss list for app developers
Microsoft Ignite 2021 took place online November 2-5. This fall edition was full of dev news, and if you don’t want to miss anything related to App development and innovation, keep reading! Session Highlights What does it take to build the next...
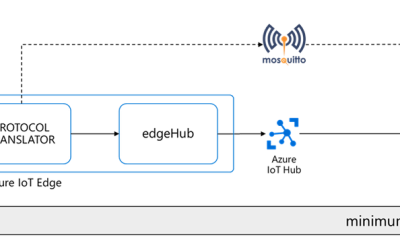
Stretching the IoT Edge performance limits
I had a customer streaming messages at a high-rate (up to 2000 msg/s - 1KB each) from a protocol translator running on an x86 industrial PC to a cloud-based Mosquito MQTT broker. That edge device evolved quickly into a more capable and secure intelligent edge...
How to defend against advanced attacks
This fall, we released Decoding NOBELIUM, a four-part video series that pulls back the curtain on the world of threat detection and showcases the incredible efforts and insights from defenders who responded to the most sophisticated nation-state attack in history....
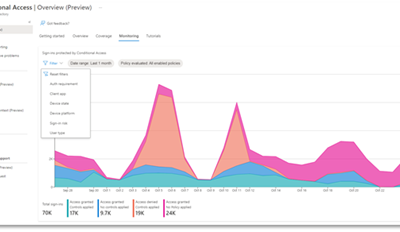
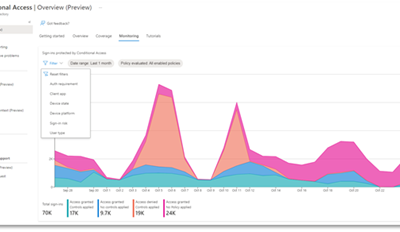
Deep Dive on Azure Active Directory Identity Protection
We hope you enjoyed Ignite 2021! We loved hearing from you and learning how you’re using Azure Active Directory to implement Zero Trust to protect users and applications from threats. Many of you have asked for more empowering and easier to use tools for protection...
Deep Dive on Azure Active Directory Identity Protection
We hope you enjoyed Ignite 2021! We loved hearing from you and learning how you’re using Azure Active Directory to implement Zero Trust to protect users and applications from threats. Many of you have asked for more empowering and easier to use tools for protection...



Recent Comments