Our Latest News
How to donate wisely after a disaster
As residents across Kentucky, Illinois, Tennessee, Arkansas, and Missouri begin taking stock following the devastating series of tornadoes that hit their states, you might be looking for ways to help the people and communities affected. Unfortunately, scammers also...
Visualize your team structure with org charts in Microsoft Visio for the web
Organizational charts can be an essential tool for any growing organization, especially now when new hires are trying to figure out their place in the company without actually meeting their colleagues in person. Org charts can help visualize reporting structures and...
Shaping the future of retail with Microsoft Customer Experience Platform
Today, nothing is certain for brands. Standing still means falling behind. Heritage brands are no different. Now more than ever, brands need to find authentic ways to engage with digitally-savvy consumers no matter where they are. How do brands steeped in tradition...
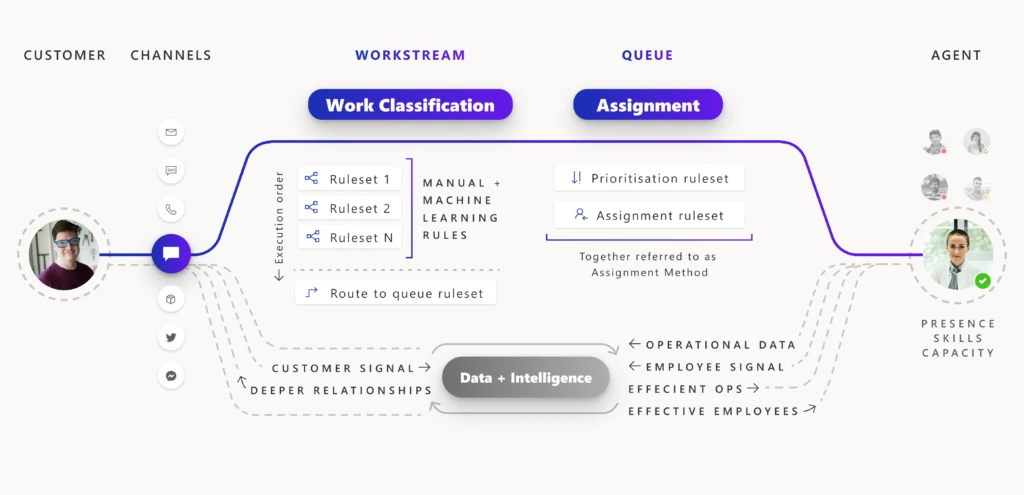
Use diagnostics to optimize unified routing for your call center
When unified routing is running smoothly for your customer service organization, incoming work items are routed to the best agent and the service workload is optimized and efficient. Depending on the needs of your business, the underlying routing infrastructure can...
Apple Releases Security Updates for Multiple Products
Official websites use .govA .gov website belongs to an official government organization in the United States. Secure .gov websites use HTTPS A lock () or https:// means you've safely connected to the .gov website. Share sensitive information only on official, secure...
Simplify your identity provisioning with these new Azure AD capabilities
With the continued evolution and adoption of hybrid work, we know how critical a strong identity and governance control plane is for IT scalability and a seamless user experience. Today, we are excited to share new Azure Active Directory (Azure AD) capabilities and...
How to spot, stop, and report post-disaster scams
If you or someone you know has been affected by the devastating series of tornadoes that roared across Kentucky, Illinois, Tennessee, Arkansas, and Missouri, coping with the aftermath is never easy. But when scammers target people just trying to recover, it can be...
Make your donation count by avoiding end-of-year charity scams
The season of giving is here. If you celebrate Christmas, you might be about to fill some stockings. But, for many, holiday giving includes supporting charitable causes. Charities in need of support will be making year-end appeals by phone, mail, email, and social...
Help us shape Kusto data exploration experience
Please take this short survey (8 questions, 4 mins) ADX short survey to help us shape ADX data exploration experiences.
Extracting SAP data using OData – Part 5 – Filter and Select
Before implementing data extraction from SAP systems please always verify your licensing agreement. Over the last five episodes, we’ve built quite a complex Synapse Pipeline that allows extracting SAP data using OData protocol. Starting from a single activity...
CISA Adds Thirteen Known Exploited Vulnerabilities to Catalog
CISA has added thirteen new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence that threat actors are actively exploiting the vulnerabilities listed in the table below. These types of vulnerabilities are a frequent attack vector for...
Why is Az 7 an important release for Azure PowerShell?
The Azure PowerShell team is proud to announce a new major version of the Az PowerShell module. Following our release cadence, this is the second breaking change release for 2021. Because this release includes updates related to security and the switch to MS Graph, we...









Recent Comments