Our Latest News
Vulnerability Summary for the Week of November 14, 2022
aiphone -- gt-dmb-n_firmware Aiphone GT-DMB-N 3-in-1 Video Entrance Station with NFC Reader 1.0.3 does not mitigate against repeated failed access attempts, which allows an attacker to gain administrative privileges. 2022-11-14 7.5 CVE-2022-40903MISCMISC amazon --...
Microsoft cloud security benchmark: Azure compute benchmark
Azure compute benchmark is now aligned with CIS Security benchmarks help organizations strengthen their security posture and meet various cloud security compliance requirements. The Microsoft cloud security benchmark announced at Ignite 2022 provides clear and...
Learning Op: Migrate Away From ADFS to Azure AD
Hello to our illustrious and awesome readers! Brandon Wilson here today with a short post just to give our readers a heads up on an excellent learning opportunity that we thought it might be helpful for many of you. Since there is already content...
Discover new ways to analyze your Customer Service data
To run a digital contact center effectively, supervisors need up-to-the-minute insights on all the activity between agents and customers. With new enhancements to Microsoft Dynamics 365 Customer Service, it’s easier than ever to find and customize the historical...
Monitoring Azure Data Factory for the Azure Well-Architected Framework
The Azure Well-Architected Framework (WAF) helps ensure that Azure workloads are reliable, stable, and secure while meeting SLAs for performance and cost. The WAF tenets are: Cost Optimization - Managing costs to maximize the value delivered....
The FBI won’t ask you for money — that’s a scam
Setup a Cosmos DB custom endpoint directly from IoT Hub
We are excited to announce the public preview support for Cosmos DB endpoint from IoT Hub in November 2022. You can now stream your data directly from IoT Hub to Cosmos DB. Many IoT solutions require extensive downstream data analysis and pushing data...
CISA, NSA, and ODNI Release Guidance for Customers on Securing the Software Supply Chain
Today, CISA, the National Security Agency (NSA), and the Office of the Director of National Intelligence (ODNI), published the third of a three-part series on securing the software supply chain: Securing Software Supply Chain Series - Recommended Practices Guide for...
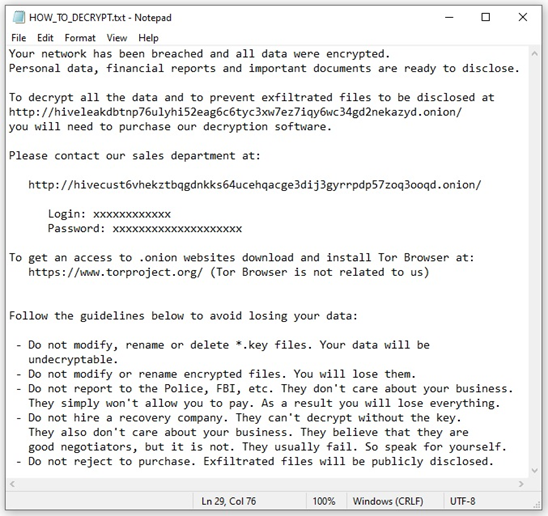
#StopRansomware: Hive Ransomware
Summary Actions to Take Today to Mitigate Cyber Threats from Ransomware:• Prioritize remediating known exploited vulnerabilities.• Enable and enforce multifactor authentication with strong passwords• Close unused ports and remove any application not deemed necessary...
#StopRansomware: Hive
Today, CISA, the Federal Bureau of Investigation (FBI), and the Department of Health and Human Services (HHS) released joint Cybersecurity Advisory (CSA) #StopRansomware: Hive Ransomware to provide network defenders tactics, techniques, and procedures (TTPs) and...
CISA Releases Two Industrial Control Systems Advisories
CISA has released two (2) Industrial Control Systems (ICS) advisories on November 17, 2022. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS.CISA encourages users and administrators to review the...
Cisco Releases Security Updates for Identity Services Engine
Official websites use .govA .gov website belongs to an official government organization in the United States. Secure .gov websites use HTTPS A lock () or https:// means you've safely connected to the .gov website. Share sensitive information only on official, secure...




Recent Comments