This article is contributed. See the original author and article here.
Throughout the last several months there have been many new features, updates, and happenings in the world of Information Protection at Microsoft. As we continue to build out more of this story, we wanted to use this opportunity to connect with customers, partners, and more on some of these updates to keep you informed and provide a single pane of glass on everything we have been working on for the last several months. In addition, we hope to give you some insight into the next big things being built within MIP overall. In the future, we hope to release this blog quarterly, providing you the most important and relevant updates to look for in this area and continuing to drive great customer experiences.
Microsoft Information Protection:
SharePoint Online (SPO) support for Sensitivity Labels, Co-authoring + Web-apps
- Enables SPO to process/store/index/search labeled/protected Office files
- Office web-apps support labeled/protected files and enable co-authoring
- You can now associate a sensitivity label with policies related to privacy, external user membership, and unmanaged device access.
Unified Labeling Scanner Network Discovery Feature
- New network discovery component that is now available in public preview enables you to map your file shares by scanning IP ranges and reporting on found shares and their exposure level.
- Exposure level can be used to prioritize the onboarding of this newly discovered shares to content scan job for deeper file inspections in these shares.
General availability of automatic classification with sensitivity labels in Microsoft 365 services
- You can create an auto-labeling policy with rules tailored for your organization’s sensitive data, targeting specific locations in your enterprise. A policy can either be in simulation or active mode. You can run the policy first in simulation mode and if the results satisfy your organization’s needs then you can proceed and publish the policy.
Announcing General Availability of Unified Labeling in GCC and GCC-H Environments
- GCC and GCC-H customers are now able to migrate sensitivity labels and label policies in the Azure Information Protection blade to the new label management portal, Microsoft 365 Compliance Center.
Announcing general availability of Microsoft Information Protection in Power BI
- The same sensitivity labels you use to classify and label data in Microsoft365 apps (e.g. Excel) can now be used to classify and label sensitive data in the Power BI service too.
- ***What’s Coming*** – MIP sensitivity labels in Power BI desktop (preview in December) enable creators to apply sensitivity labels and protection on PBIX files while author dataset and reports in Power BI desktop in addition to mandatory label policies in Power BI.
Announcing public preview of Microsoft Endpoint Data Loss Prevention
- Endpoint DLP is native to Windows 10 and the new Microsoft Edge browser. There is no need to install or manage additional DLP software on Windows 10 machines (Version 1809+) anymore. Endpoint DLP is managed via the cloud and the Microsoft 365 compliance center, eliminating the need to deploy and operate additional consoles, event management systems, databases, and hardware on premises.
Announcing General Availability of Double Key Encryption for Microsoft 365
- DKE Video: Protecting mission critical data using Double Key Encryption
- Github Repo: https://aka.ms/DKErepo
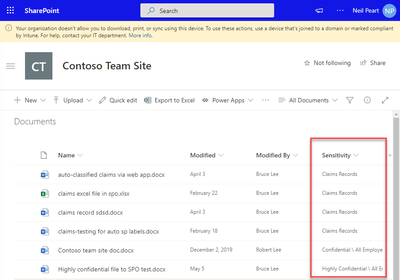
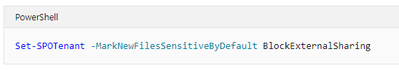
Announcing GA: Mark new files as “sensitive by default” in OneDrive & SharePoint
- When new files are added to SharePoint or OneDrive in Microsoft 365, it takes additional time for the Office Data Loss Prevention (DLP) policy to scan the content and apply rules to help protect sensitive content. If external sharing is turned on, sensitive content could be shared and accessed by guests before the Office DLP rule finishes processing.
PREVIEW – Labels as DLP condition in SPO/OD/EXO/PC
- Allows use of a label as a condition to trigger a DLP Rule
- If DLP Policy covers SPO/OD, then Teams attachments are covered
***What’s Coming*** – Per-site Azure Active Directory Conditional Access controls
- Allows AAD CA controls ‘per site’ including per-site MFA and per-site Terms of Use
- CA Policy linked to a ‘tag’ applied to Site (via PowerShell). Soon, this will be possible based on Label assigned to the Site
***What’s Coming*** – Unifying logging
- Work is being done to bring it all to the M365 Audit log, and to consume these logs from the Data classification Content and Activity explorers for unified Logging and reporting.
2020 Ignite Information Protection Related Sessions:
For more information, take a look at some of our most recent Ignite Sessions on Information Protection:
- Supercharge information protection and governance across cloud, on-premise, endpoints and remote work environments
- Be a risk management hero with intelligent data protection and compliance solutions
- Know your data, protect your data and prevent data loss with Microsoft Information Protection
- Ask the Expert: Ask anything about Microsoft Compliance: information protection & governance, insider risks, Compliance Management, and more!
- Ask the Expert: Supercharge information protection and governance across cloud, on-premise, endpoints and remote work environments
Additional Information:
- Simplifying the AIP Super User Role with Azure PIM
- eDiscovery for Teams Webinar
- MIP and Compliance V-blog part 1 – Setting up a secure collaboration environment
- Getting started with Insider Risk Management
- MIP and Compliance V-blog #2: Setting up a secure collaboration environment – End user point of view
- MIP and Compliance V-blog#3: Setting up a secure collaboration environment – Security Admin POV
- Records Management Webinar
- Protecting against insider risks in an uncertain environment
- Foster a culture of inclusion and safety with Microsoft Teams and Communication Compliance
- MIP Previews Available
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments