This article is contributed. See the original author and article here.
According to a recent study, cloud misconfigurations take an average 25 days to fix. This number can even be higher if you are managing the cloud security posture across multiple providers without having an aggregate visualization of the current security state of all cloud workloads. Not only it becomes a challenge to understand the current security state, but also to manage multiple dashboards and prioritize which issues should be resolved first.
When you upgrade Azure Security Center free tier to Azure Defender you will be able to connect to AWS and GCP using native Azure Defender connectors. Once you connect to each cloud provider, you will be able to use the Security Recommendations to quickly filter the environment and see only the recommendations that are relevant for the cloud provider that you want, as shown below:
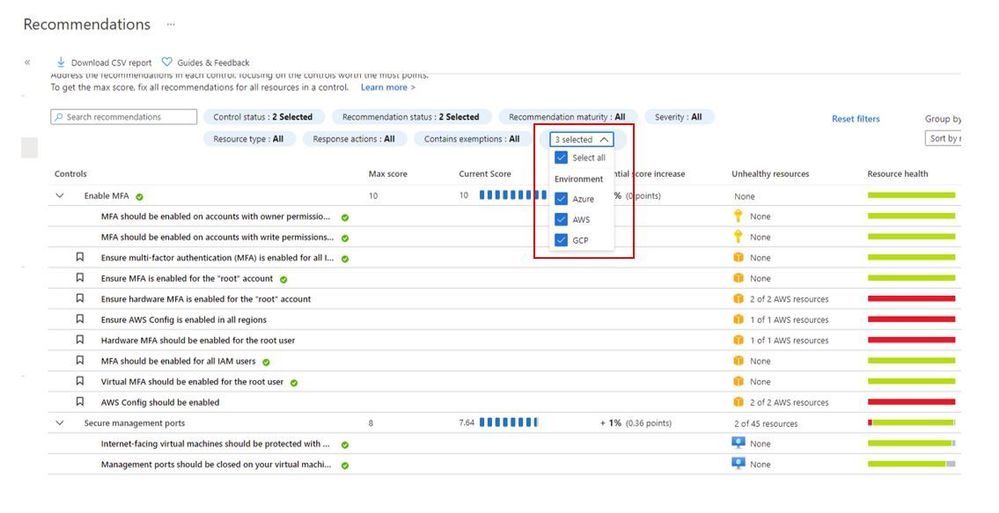
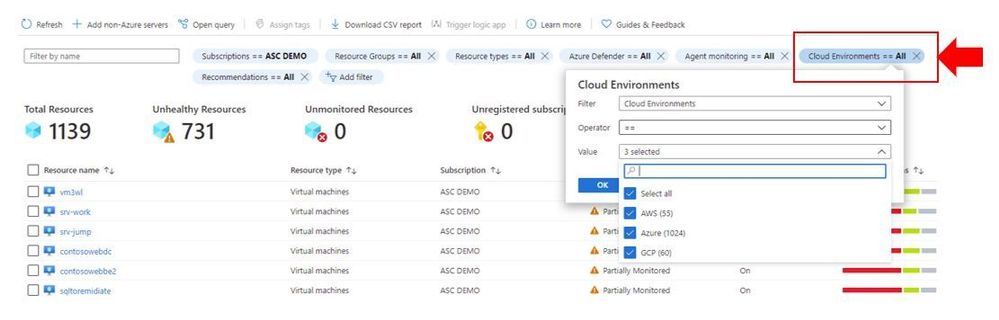
You can also quickly identify resources on each cloud provider by using the Inventory dashboard, by using the Cloud Environment filter as shown below:
In addition to all that, you can also take advantage of centralized automation by leveraging the Workflow Automation feature to automate response for security recommendations generated in Azure, AWS or GCP.
Cloud security posture management and workload protection
The security recommendations are relevant for the cloud security posture management scenario, which means that you drive the enhancement of your security posture across multiple cloud providers by remediating those recommendations. However, this is not the only scenario available for multi-cloud, you can also use the following Azure Defender plans to enhance your workload protection. When planning cloud workload protection for workloads in AWS and GCP, make sure to first enable the VMs to use Azure Arc, once you do that, the following Azure Defender plans will be available across Azure, AWS and GCP:
The potential alerts generated by workloads protected by those plans is going to be surfaced in the Security Alerts dashboard in Azure Defender. Which means that you again will have a single dashboard to visualize alerts across different cloud providers. These alerts can be streamed to your SIEM platform using Continuous Export feature in Azure Security Center.
Design considerations
Prior to implementing your multi-cloud adoption using Azure Defender, it is important to consider the following aspects:
When connecting with AWS
- An account is onboarded to a subscription, the subscription has to have Azure Defender for Servers enabled
- The VMs under this account will automatically be onboarded to Azure using Azure Arc, and will be covered by Defender (list of supported OS)
- Arc cost is inclusive with Defender (you won’t pay twice)
- To receive the security recommendations, you will need to enable AWS Security Hub on the accounts you want to onboard
- Security Hub is a paid service that can vary depending on how many accounts and regions it’s enabled on (please refer to AWS official pricing)
When connecting with GCP
- Same requirement for Defender enabled on the subscription
- Servers are not onboarded automatically, and will need to be onboarded through Arc (Arc onboarding guide)
- To receive security recommendations, you will need to enable GCP Security Command Center
- Google Security Command Center have two pricing tiers: standard (free) and premium
- Free tier includes ~12 recommendations, premium around 120
- Premium tier costs 5% of annual spending in GCP, please refer to GCP official pricing)
Additional Resources
The resources below will be useful for you to implement this multi-cloud capability in Azure Defender:
- AWS Connector (step-by-step guide to configure this integration)
- GCP Connector (step-by-step guide to configure this integration)
- Overview of Azure Defender Multi-cloud solution (video)
- Azure Defender for SQL (video)
- Azure Defender for Kubernetes (video)
- Continuous Export (video)
Reviewer
Or Serok Jeppa, Program Manager
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments