This article is contributed. See the original author and article here.
If you didn’t grow up in the ’90s in France like yours truly, you probably wouldn’t be familiar with the animated kids show named Petit Potam, which was based on the books of the same name by Christine Chagnoux.
While I could talk about the TV series for days, the reason Petit Potam came to the news lately is because of a vulnerability that was recently published with the same name which can potentially be used in an attack on Windows domain controllers. PetitPotam is a tool that can exploit the Encrypting File System Remote (EFSRPC) Protocol.
Exploiting the MS-EFSRPC
The EFSRPC protocol that PetitPotam exploits is typically used to maintain and manage encrypted data that is stored remotely and accessed over a network. It’s mainly used to manage Windows files that reside on remote file servers and are encrypted using the Encrypting File System (EFS).
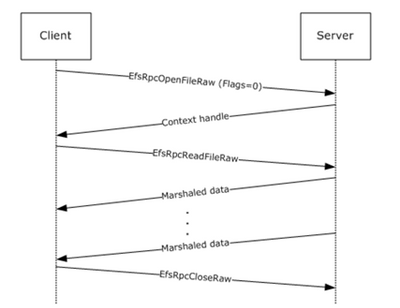
Figure 1. Message sequence for opening a file using EFS
Using the PetitPotam vector, an adversary can manipulate MS-EFSRPC API functions without authentication using the OpenEncryptedFileRaw calls. This allows the adversary to force a domain controller to authenticate to an NTLM relay server under the attacker’s control.
NTLM Relay attack
NTLM relay attacks allow the malicious actor to access services on the network by positioning themselves between the client and the server and usually intercepting the authentication traffic and then attempting to impersonate the client.
To prevent NTLM relay attacks on networks with NTLM enabled, domain administrators must ensure that services that permit NTLM authentication utilize protections such as Extended Protection for Authentication (EPA), or signing features, like SMB signing.
PetitPotam takes advantage of servers where Active Directory Certificate Services (AD CS) is not configured with protections for NTLM relay attacks.
Microsoft Defender for Identity detection
Starting from version 2.158 onwards, Microsoft Defender for Identity will trigger a security alert whenever an attacker is trying to exploit the EFS-RPC against the domain controller, which is the preliminary step of the PetitPotam attack.
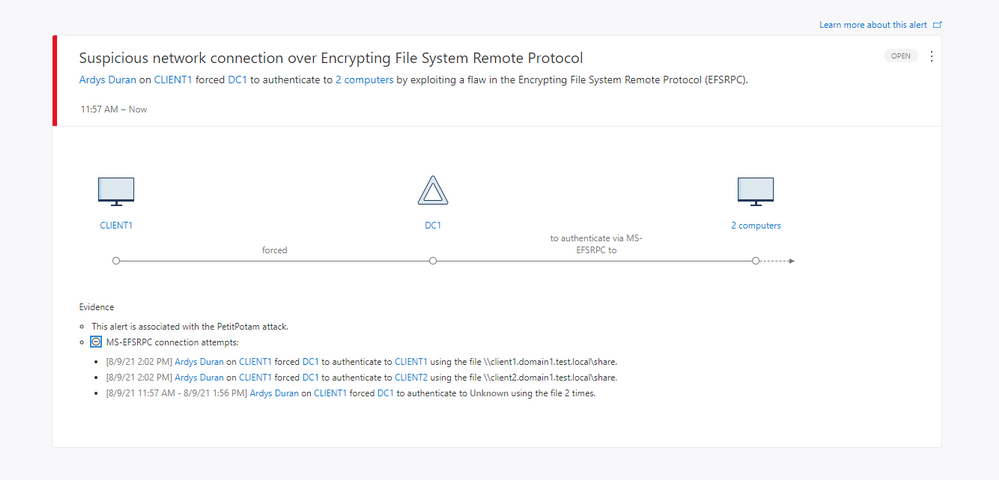
Figure 2. Suspicious Network Connection over EFS-RPC alert information
The alert provides visibility into network activity over the protocol and when an attacker is trying to force the domain controller to authenticate against a remote device. The alert will contain the following information:
- Source context – which can be the user and/or the device originating the request
- The target domain controller
- The remote device – including the file the attacker was trying to read
How to protect your organization further
On August 10, 2021, Microsoft published CVE-2021-36942 which addresses this vulnerability, named Windows LSA Spoofing Vulnerability. We highly recommend prioritizing updating the domain controllers with this CVE.
To learn more about the CVE, see the details in the MSRC portal with the following link: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-36942
What next?
If you haven’t already got access to Defender for Identity, you can start a trial using this link.
We’re always adding new capabilities to Defender for Identity and we’ll make announcements about great new features here in this blog, so check back regularly to see what the latest updates bring to your security teams.
We’re always keen on hearing your feedback, so please let us know in the comments section below if you have anything to share with us about this detection.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments