This article is contributed. See the original author and article here.
By: Charlotte Maguire | Program Manager – Microsoft Endpoint Manager – Intune & Shantaram Punukollu | Sr Program Manager – Identity
Microsoft Endpoint Manager – Intune support for automatically enrolling Android Enterprise dedicated devices into Azure AD Shared device mode is now in public preview! This new feature is rolling out with the October service release and will soon be available to all Microsoft Endpoint Manager customers.
Today, Microsoft Endpoint Manager customers have the option to enroll their Android devices as Android Enterprise (AE) dedicated devices. With this public preview, customers will now be able to optionally enroll their AE dedicated devices into Azure AD Shared device mode, which will allow end-users to gain single sign-on and single sign-out across all of the participating applications on the device. For an application to participate with Azure AD Shared mode, it must integrate with Azure AD’s MSAL library. More information about Azure AD Shared Mode and its capabilities can be found here.
Here are additional capabilities included with this public preview release:
Ensure device compliance with Conditional Access – Customers using Azure AD shared mode on dedicated devices will be able to secure their corporate data on user sign-in with Conditional Access that is based on device compliance.
Customized sign-in experience – Customers will be able to leverage new Managed Home Screen customizations that were built specifically for Azure AD Shared device mode. For example, admins can allow users to define a session PIN for the duration of their shift and configure an automatic sign-out timer.
To learn more about Azure AD Shared mode, dedicated devices, and/or Managed Home Screen, please see the following articles:
To learn more about how to use the features in public preview, read on!
What steps do I need to take prior to enrolling with this scenario?
In the Microsoft Endpoint Manager admin center, follow the steps listed here to get your dedicated device enrollment profile(s) and device groups appropriately set up.
With Intune’s October release, you will notice an option to specify a “Token type” when you create an enrollment profile. You can choose “Android Enterprise dedicated device (default),” or “Android Enterprise dedicated device with Azure AD shared mode (preview).” To enroll your devices with Azure AD Shared device mode automatically set up during enrollment, choose the latter.
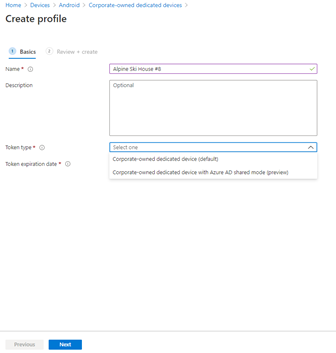
Step 2 – Select token type and expiration
Check that any applications you want users to sign into with this solution have integrated with Azure AD’s MSAL library and global sign-in and sign-out calls. If needed, read about how to add Managed Google Play apps to your devices and how to assign apps to groups.
How do I enroll my dedicated devices into Azure AD shared mode?
To enroll with Intune’s dedicated device solution, make sure that you have factory reset devices that meet the requirements found here. Identify the enrollment method you would like to use, and follow the appropriate steps listed here.
Once you begin enrollment with an “Android Enterprise dedicated device with Azure AD shared mode (preview)” you will see screens similar to the ones shared below. Follow the steps on-screen to complete enrollment.
Fig. 1 – Set up your work phone
Fig. 2 – Register shared device
Fig. 3 – Shared device registering
Fig. 4 – Shared device successfully registered
Fig. 5 – Shared device successfully registered
What are the new Managed Home Screen features and how do I use them?
In conjunction with Intune’s public preview, Microsoft’s Managed Home Screen is releasing support for Azure AD Shared device mode and offering customizations specific to this scenario. As always, Managed Home Screen can be optionally used on your dedicated devices to provide a locked-down, tailored experience for your end-users, giving them access to a curated set of apps, settings, and more. The main features Managed Home Screen is releasing alongside their support of Azure AD Shared device mode can be found below.
Sign-in screen & wallpaper for sign-in screen
This is an optional set of configurations to show a sign-in screen to end-users when Managed Home Screen is on the device and no user is signed in. Use of this feature ensures that the only action an end-user can take on a signed-out device is to sign in. Users can still access the Managed Home Screen settings pane, if configured by IT. Additionally, the debug menu is still accessible.
You can also configure a sign-in screen wallpaper that is separate from the wallpaper shown after sign-in.
Sign-in screen wallpaper
Session PIN
An optional set of configurations that allows your end-user to set IT choice of numeric or alphanumeric PIN that lasts for the duration of their signed-in session. The prompt to set a PIN appears directly after initial sign in and the PIN is completely cleared upon sign out. This PIN can be used throughout the session to access specific permissions, rather than needing to use full user credentials.
Set your session PIN
Automatic sign-out
An optional set of configurations that allows you to choose if end-users on the device should get signed-out after a specified period of inactivity. You can also choose whether or not to give user notice of the auto-sign-out with configured time frame in which they can choose to resume if they are still using the device.
Automatic sign-out prompt
Customer facing folder
This is an optional specification for any folders you create on Managed Home Screen. If you specify a folder as customer facing, then when the folder is launched it cannot be exited until the logged in user enters their session PIN. This allows the logged in user to share their device with another end-user without fear of accidentally sharing sensitive information. The logged in user also has the option to switch user when exiting the folder, which will sign out all apps on the device and return the user to the sign-in screen.
Fig 1. Home screen
Fig 2. Enter session PIN
Fig 3. Session PIN entered
Fig 4. Switch User prompt
Custom privacy statement
On the Managed Home Screen sign-in screen, notice a link to Microsoft’s privacy statement. Choose whether or not to include your organization’s privacy statement, as well, by including a link and a title for the link. If you use this feature, both privacy statement links will appear on Managed Home Screen’s sign-in screen.
Things to note:
- To recieve single sign-in and single sign-out while in Azure AD shared device mode, each app must participate. Today, Microsoft applications that participate with Azure AD shared device mode include Teams and Managed Home Screen.
- App Protection Policies (APP) are not currently supported on Intune’s Android Enterprise dedicated devices, though they are also not formally blocked. If a user targeted with APP signs into an APP-protected application, they will be prompted to install the Company Portal application, and the user’s sign in will effectively block other users from signing into the same application. It is recommended that users signing into apps on dedicated devices not be targeted with APP. With Intune’s November release, APP will be formally blocked on dedicated devices. With the November change, even if users are targeted with APP, they will not receive APP when using apps on their dedicated devices. As a result, they will be able to sign into and out of apps on their dedicated devices without blocking other users from sign-in. Users targeted with APP on non-dedicated devices will not be impacted.
How can you reach us?
Let us know if you have any additional questions on this by replying back to this post or tagging @IntuneSuppTeam out on Twitter.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments