This article is contributed. See the original author and article here.
While recently working with a customer’s Governance Risk and Compliance team (GRC) the discussion pivoted to the ability to exempt Azure resources from policies or disable the policy to reflect the Secure Score correctly for their environment. GRC teams may want on a quarterly or monthly basis to produce a report of the exemptions to review and discuss or hand over to auditors looking to see the exemption story.
The Exemption capabilities in Azure Security Center utilize Azure Policy exemptions that have been around for a bit now. @Tom Janetscheck has written quite a bit about the capability and provided some unique Workflow automations around
Submitting a exemption via Logic App
Notifying an Exemption via Logic App
Both are very great workflow automations the GRC team can adopt at an enterprise. Your GRC team may be looking for an easy to pull report they could download around the exemptions and the azure resources to quickly audit findings.
Let’s examine a few ways you can pull this information within the Azure Portal, Azure Resource Graph, and use a new PowerShell Script to download a detailed report.
Azure Portal – Policy – Assignments blade
When you want a quick view of the exemptions for a particular subscription within the Azure Portal for Policy you can leverage the Assignments blade to list those exemptions. In addition, if you have written access you can update or create new exemptions as well.
Within the Azure Portal go to Policy and click on the Assignments blade, within there, click on ASC Default assignment.
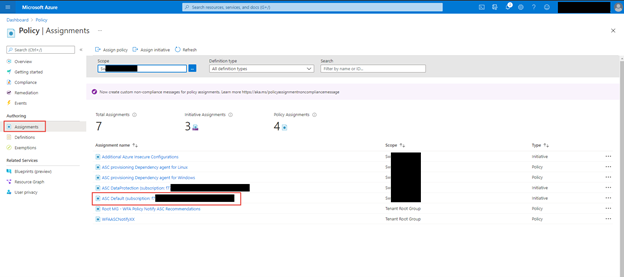
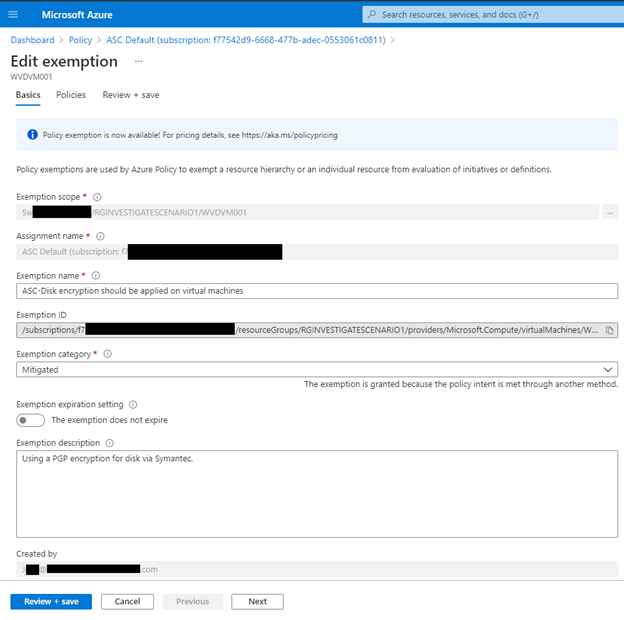
Click on the Exemptions Tab, if you have write access to policy assignments you can also click on the … and edit the exemption too see more details
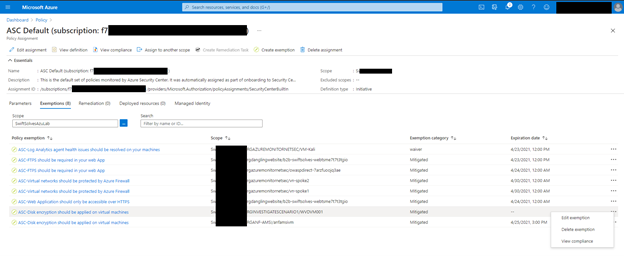
Azure Resource Graph
Some of the exemption values are stored as data in Azure Resource Graph and specifically the securityresources table. If you are unfamiliar with the Azure Resource Graph the Azure Portal’s top search bar is also powered by it and helps return fast results. It is a great way to not invoke a GET Azure Resource API call for each Azure resource details and configurations as their state and information are stored here.
Within the table Azure does store some information around the ASC recommendations and their states, including the exemptions and policies disabled.
You can now run a KQL query in Azure Resource Graph to generate a report.
securityresources
| where type == "microsoft.security/assessments"
| extend source = tostring(properties.resourceDetails.Source)
| extend resourceId =
trim(" ", tolower(tostring(case(source =~ "azure", properties.resourceDetails.Id,
source =~ "aws", properties.resourceDetails.AzureResourceId,
source =~ "gcp", properties.resourceDetails.AzureResourceId,
extract("^(.+)/providers/Microsoft.Security/assessments/.+$",1,id)))))
| extend status = trim(" ", tostring(properties.status.code))
| extend cause = trim(" ", tostring(properties.status.cause))
| extend assessmentKey = tostring(name)
| where cause == "Exempt" or cause == "OffByPolicy"
| extend ResourceName = tostring(split(resourceId,'/')[8]), RecommendationName = tostring(properties.displayName), Source = properties.resourceDetails.Source, StatusCause = tostring(properties.status.cause), StatusDescription = properties.status.description, RecommendationSeverity = tostring(properties.metadata.severity)
| project RecommendationName, RecommendationSeverity, ResourceName, StatusCause, StatusDescription, resourceGroup, Source, subscriptionId
| sort by RecommendationSeverity, RecommendationName
For a comprehensive and better visual listing experience, be sure to set the query to run on all Azure Subscriptions and Formatted Results turned on. You can then download the report to a CSV file for the auditors or for review of the exceptions and disabled policies.
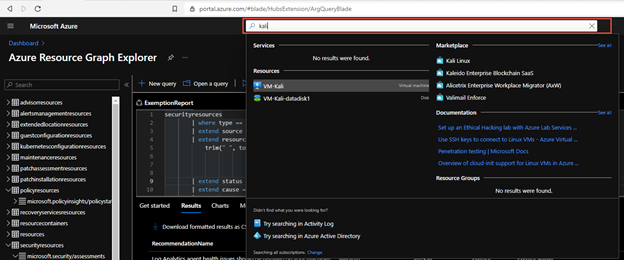
You can find the KQL query here in the Azure Security Center GitHub repo.
Generate-ExemptionReport.ps1
For a more comprehensive and detailed report that includes Notes in the exemption, expiration dates for exemptions, and who created the exemptions you can now utilize the following PowerShell script which executes across Azure Subscriptions and invokes an API to get the details:
Microsoft.Authorization/policyExemptions?api-version=2020-07-01-preview
To use the script you can download here from the GitHub Repo and open PowerShell.
Within PowerShell be sure to log into an Azure using Connect-AzAccount and using the login of someone who has a large amount of reader access across your Azure enterprises subscriptions. You may see some errors please ignore for now as the script will be tuned over time to support additional scenarios.
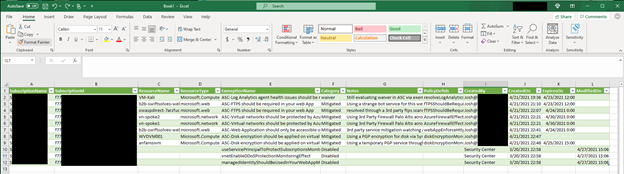
The end result is nicely generated CSV with all the details around the exemptions that can be imported into Excel, PowerBI, or other data visualization products.
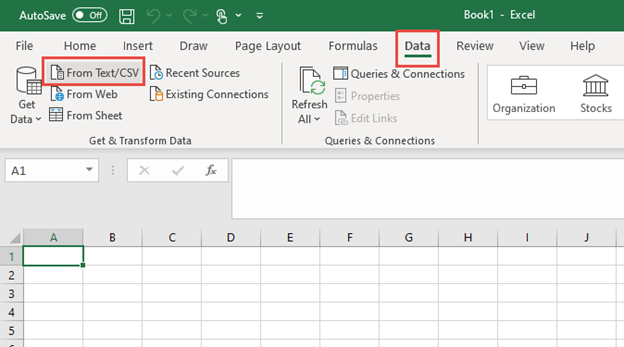
As an example you can import into into Excel, Open a new Excel sheet and got to the ‘Data’ tab and use the button ‘From Test/CSV’
Once imported you can pivot and filter as needed
In this article you explored several ways to examine and generate an exemption report. You can use the Azure Portal – Policy – Assignments blade to quickly view all the Exemptions. You can use the Azure Resource Graph and a KQL Query to generate a simplified exemption and policy disable report. Finally you can use a PowerShell script to generate a detailed exemption and policy disable report that includes notes, expiration date and time, and who created the exemption. These reports can be used in a quarterly or month basis for you GRC team to review and discuss or handed over to auditors looking to see the exemption story.
Special thanks to:
@Yuri Diogenes for reviewing this post
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments